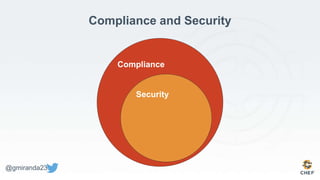
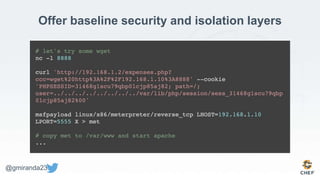
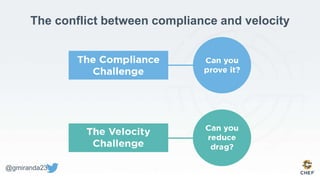
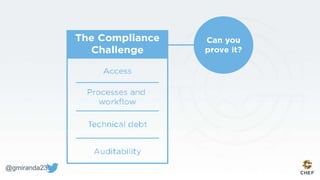
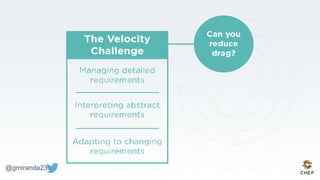
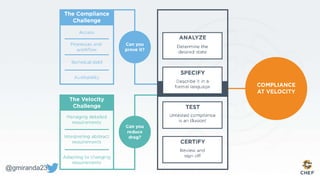
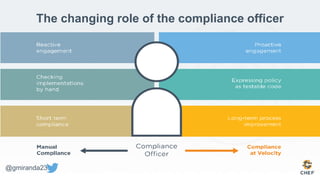
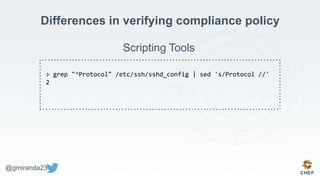
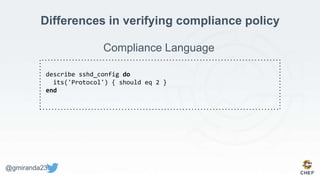
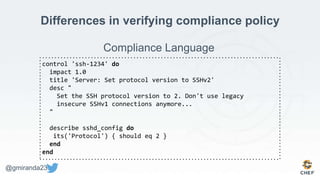
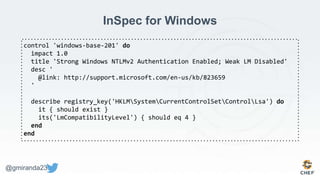
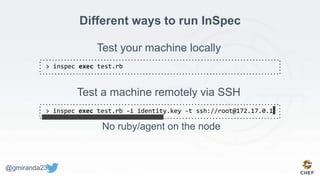
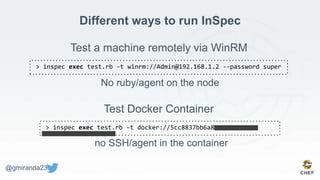
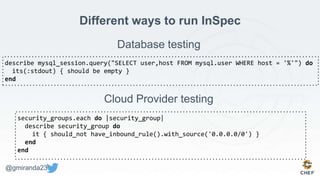
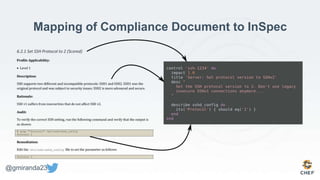
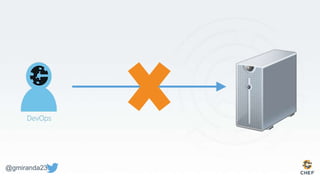
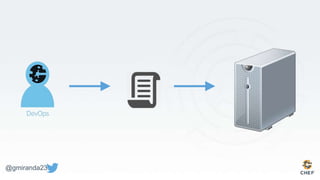
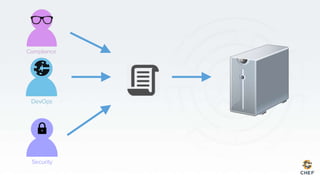
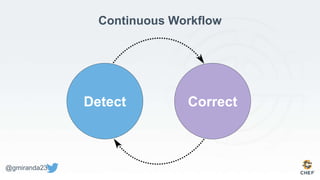
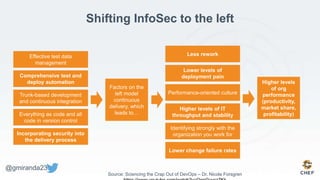
The document discusses the concept of 'Compliance as Code' using InSpec, presented by George Miranda, emphasizing the importance of integrating compliance into the development workflow to enhance security and operational velocity. It covers the historical context of IT compliance, common regulatory requirements, and how InSpec transforms compliance and security requirements into code for efficient testing and validation. Additionally, it highlights the evolving role of the compliance officer and the collaborative nature of security within development teams.