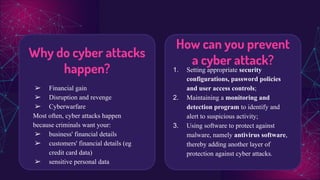
The document discusses the implications of computer misuse and cybersecurity. It begins with an introduction from the presentation group and defines key terms like computer misuse, cybersecurity, vulnerabilities, threats, attacks, and countermeasures. It then covers various types of threats like malware, password attacks, DDoS attacks, and vulnerabilities from both internal and external sources. Specific examples of countermeasures and how to prevent cyber attacks are provided. The document concludes by discussing the impact of computer misuse related to cyberbullying and ways to mitigate cyberbullying.