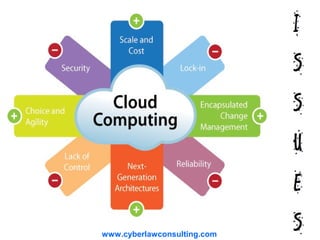
The document discusses several key legal issues related to cloud computing:
1) Compliance can be difficult when cloud services are geographically decentralized and contracts impose auditing requirements. Applicable law and jurisdiction are also unclear when services are provided across borders.
2) Cloud providers face legal liability for illegal data hosted on their services. However, laws in India and other places provide liability protection if the provider is unaware and removes illegal data upon awareness.
3) Loss of data location challenges cybercrime investigations and applying legal jurisdiction. However, conventions like the Budapest Convention on Cybercrime provide for legal access of data across borders with user consent.