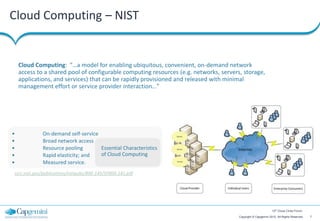
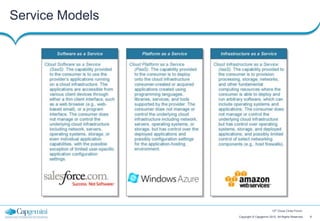
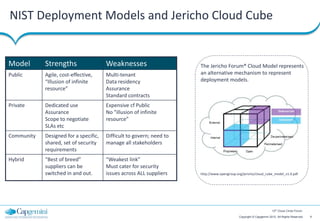
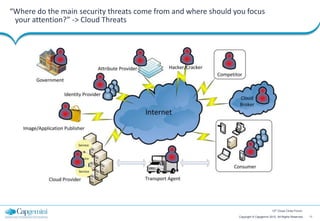
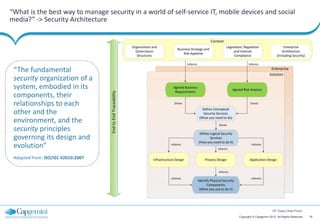
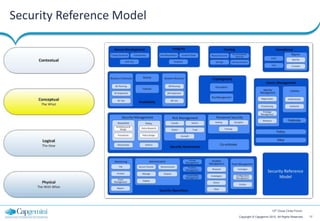
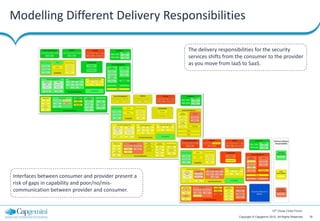
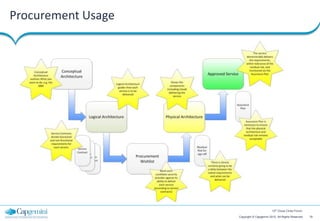
The document discusses cloud security strategies, focusing on the risks and genuine security issues that impede cloud adoption. It emphasizes the human element in threats, compliance challenges, and the need for an architectural approach to manage security effectively in cloud environments. The presentation aims to guide organizations in understanding the security landscape of cloud services compared to on-premise solutions.