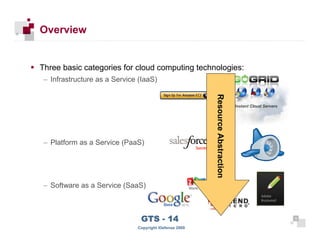
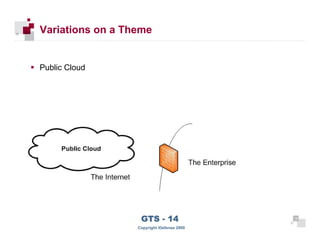
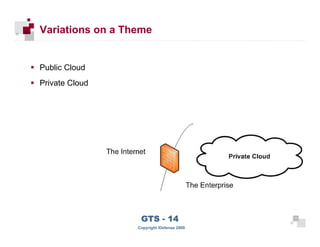
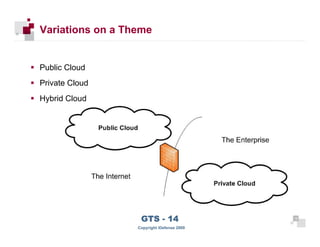
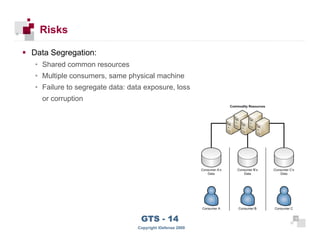
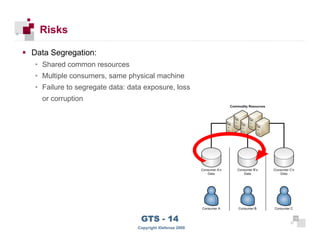
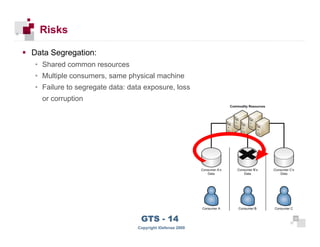
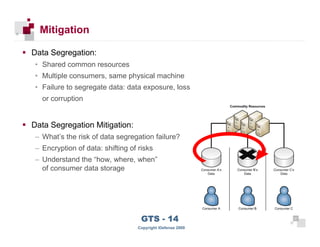
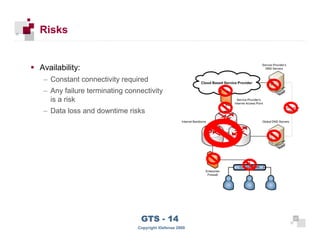
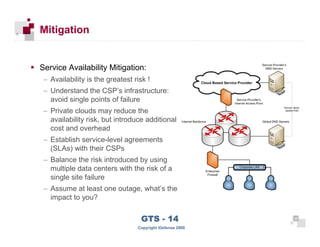
The document discusses cloud computing risks and mitigation strategies. It provides an overview of cloud computing definitions and models. It then discusses several key risks to cloud computing like privileged user access, data segregation, regulatory compliance, and the physical location of data. For each risk, it proposes potential mitigation strategies to evaluate like access controls, encryption, understanding regulatory obligations, and considering data location.