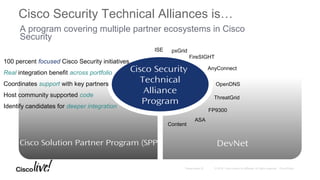
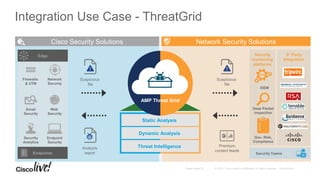
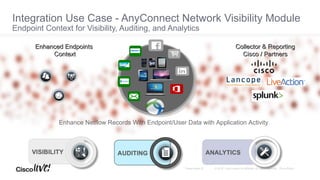
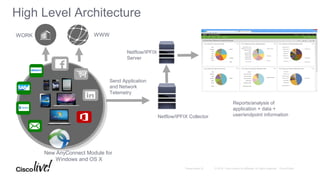
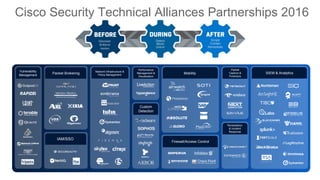
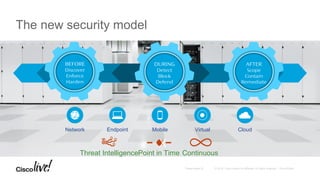
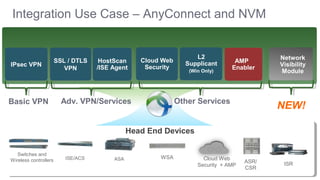
The Cisco Security Technical Alliances program coordinates integration between Cisco security products and third-party vendors. It provides APIs and frameworks to enable deeper product integration and automation. This allows for use cases like rapid threat containment by sharing context between the Cisco Firepower Management Center and Identity Services Engine, and collecting host and vulnerability data via the Host Input API. The roadmap includes expanding supported APIs and growing the ecosystem of integrated partners.