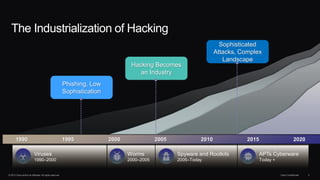
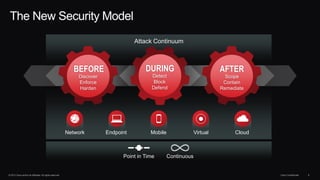
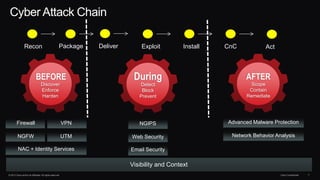
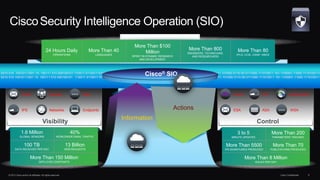
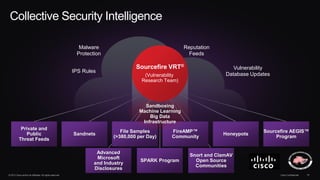
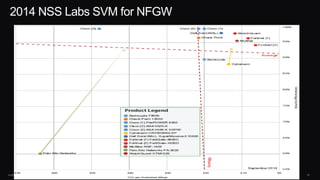
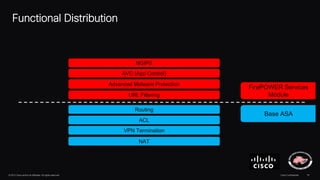
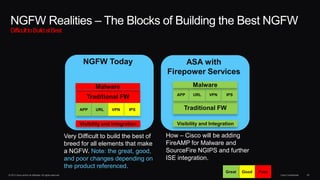
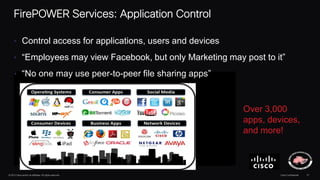
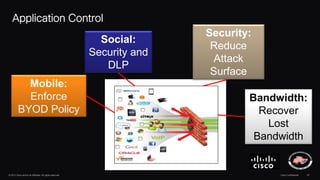
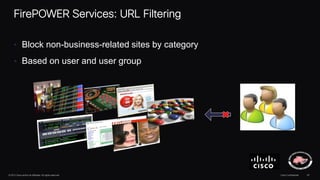
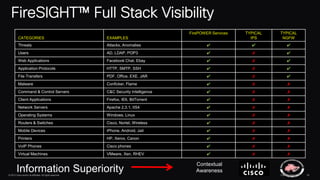
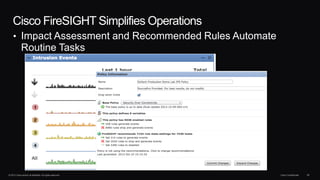
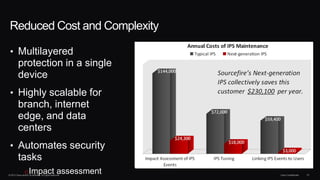
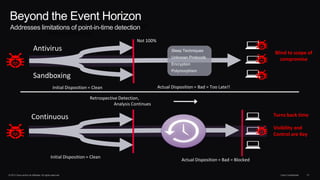
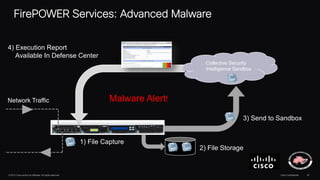
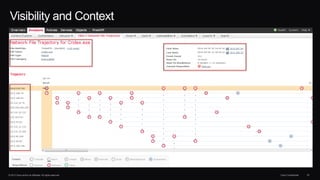
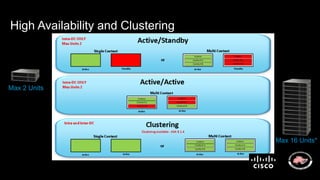
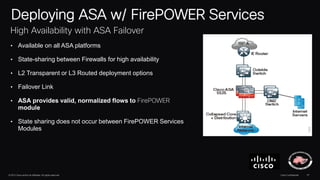
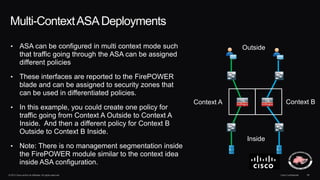
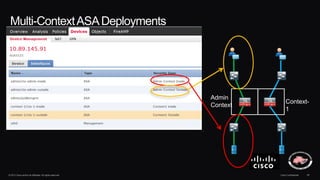
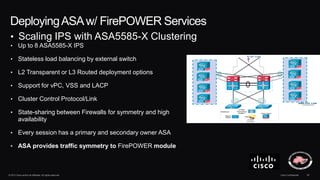
The document discusses next generation security and the Cisco FireSIGHT solution. It describes how hacking has become more sophisticated over time and now poses serious threats. Cisco FireSIGHT provides comprehensive visibility, advanced malware protection, and context-aware next generation intrusion prevention and firewall capabilities to address modern security challenges. The solution leverages collective security intelligence from Cisco's world-class security research organization.