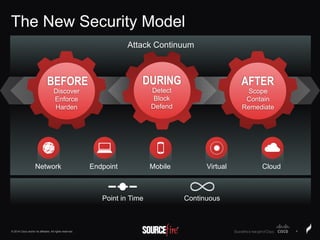
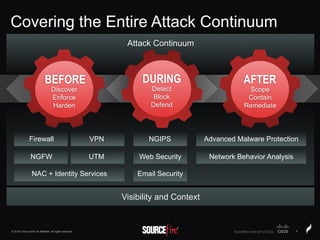
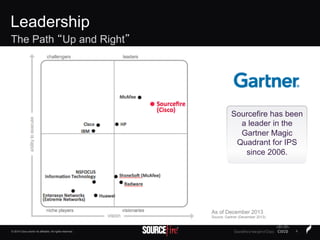
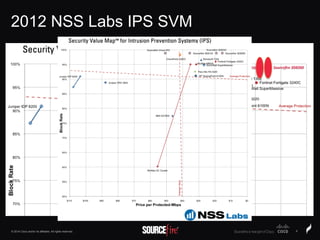
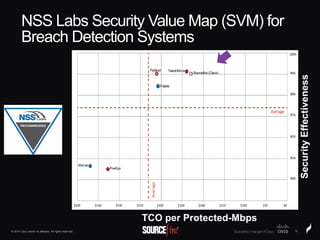
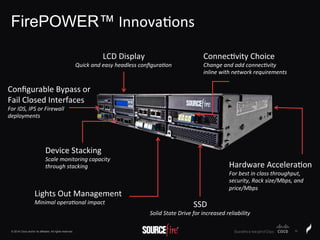
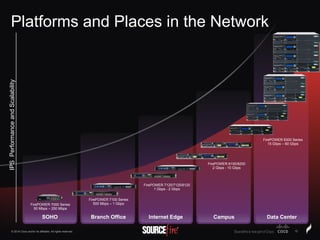
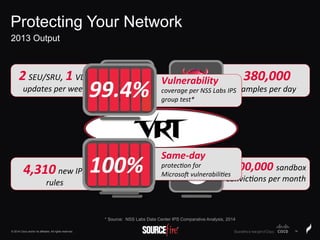
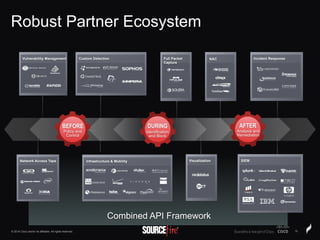
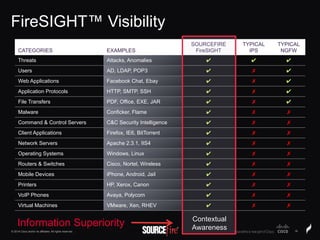
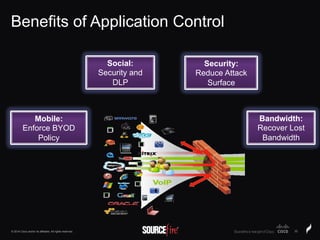
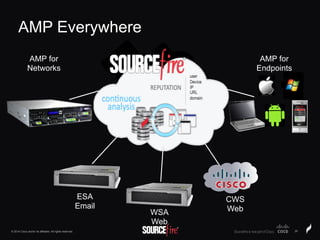
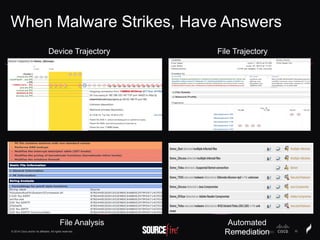
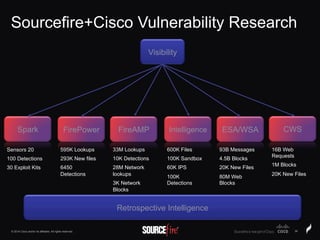
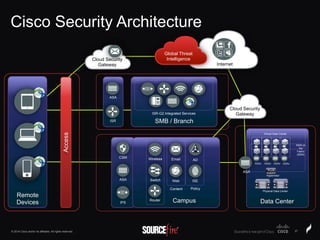
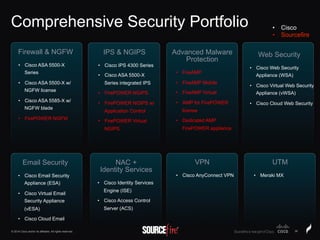
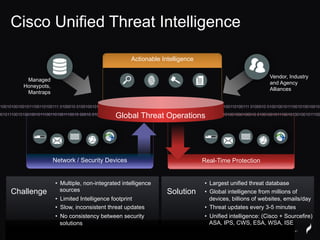
The document discusses Sourcefire's security solutions, emphasizing a comprehensive approach to network defense covering the entire attack continuum. It highlights the company's leadership in the IPS market, innovative technologies like Firepower, and the importance of real-time threat intelligence. There are also mentions of various security products, benefits of application control, and examples of operational savings for organizations.