Infographic: Security for Mobile Service Providers
•
3 likes•4,612 views
This infographic offers an operator's view on mobile security trends, such as the technology innovations driving business gowth and security threats. It also suggests how you can protect customers.
Report
Share
Report
Share
Download to read offline
Recommended
Midsize Business Solutions: Cybersecurity

You face unprecedented challenges to protect your midsize business from cybersecurity threats. New trends such as mobility and cloud are changing how you need to secure devices, data and your network.
To deal with these challenges, you need a smart, scalable threat-centric security model. This model needs to provide cost-effective threat remediation and support standard security policies and controls.
Cisco can help. We deliver intelligent cybersecurity for the real world. Our threat-centric approach reduces complexity while delivering superior visibility and control—saving you time and reducing costs.
With Cisco, you gain advanced threat protection across the entire attack continuum—before, during, and after an attack. To learn more, visit http://cs.co/mmigvepg
3 Tips for Choosing a Next Generation Firewall

Discover the top three tips when choosing a NGFW to protect your business from attacks. Learn more: http://cs.co/9001BD8k1
Pervasive Security Across Your Extended Network

There are many ways attackers can access your network. Keep yours safe before, during, and after an attack with best-in-class Cisco Security designed to protect your business data. Learn more at http://cs.co/9009BJ8o3
Data Center Security Challenges

More than a technology issue - it's a human problem. Learn more at www.cisco.com/go/acisecurity.
Cisco 2015 Midyear Security Report Slide Deck

Download the full Midyear Security Report >> http://cs.co/MSR15SL
Cisco has released its Midyear Security Report. In this report, Cisco provides industry insights and key findings taken from threat intelligence and cybersecurity trends for the first half of 2015.
Desafíos de la Ciberseguridad en un ecosistema digitalmente transformado

Para trabajar en un ecosistema digitalmente transformado, los directores de sistemas de información y otros líderes empresariales tienen que navegar en un entorno de amenazas a la seguridad en constante cambio. Las soluciones de Next Gen Security (NGS) son soluciones de seguridad optimizadas para trabajar mejor con la escala masiva y cobertura expansiva de la Tercera Plataforma. Aunque 7 de cada 10 empresas afirman estar en el proceso de implementar una solución más de seguridad de nueva generación, 3 de esos 7 no tendrá éxito por la falta de competencia interna, por lo que el tema de seguridad es cada día más crítico”. Akamai ofrece un rendimiento a escala con la solución de distribución en la nube más grande y confiable del mundo. Sus recursos se escalan de forma que sus clientes no tengan que hacerlo. Akamai tiene una visibilidad sin igual de las propiedades más atacadas en la web y obtiene inteligencia ante amenazas continuamente a partir de inspecciones avanzadas tanto del tráfico bueno como del malo.
Recommended
Midsize Business Solutions: Cybersecurity

You face unprecedented challenges to protect your midsize business from cybersecurity threats. New trends such as mobility and cloud are changing how you need to secure devices, data and your network.
To deal with these challenges, you need a smart, scalable threat-centric security model. This model needs to provide cost-effective threat remediation and support standard security policies and controls.
Cisco can help. We deliver intelligent cybersecurity for the real world. Our threat-centric approach reduces complexity while delivering superior visibility and control—saving you time and reducing costs.
With Cisco, you gain advanced threat protection across the entire attack continuum—before, during, and after an attack. To learn more, visit http://cs.co/mmigvepg
3 Tips for Choosing a Next Generation Firewall

Discover the top three tips when choosing a NGFW to protect your business from attacks. Learn more: http://cs.co/9001BD8k1
Pervasive Security Across Your Extended Network

There are many ways attackers can access your network. Keep yours safe before, during, and after an attack with best-in-class Cisco Security designed to protect your business data. Learn more at http://cs.co/9009BJ8o3
Data Center Security Challenges

More than a technology issue - it's a human problem. Learn more at www.cisco.com/go/acisecurity.
Cisco 2015 Midyear Security Report Slide Deck

Download the full Midyear Security Report >> http://cs.co/MSR15SL
Cisco has released its Midyear Security Report. In this report, Cisco provides industry insights and key findings taken from threat intelligence and cybersecurity trends for the first half of 2015.
Desafíos de la Ciberseguridad en un ecosistema digitalmente transformado

Para trabajar en un ecosistema digitalmente transformado, los directores de sistemas de información y otros líderes empresariales tienen que navegar en un entorno de amenazas a la seguridad en constante cambio. Las soluciones de Next Gen Security (NGS) son soluciones de seguridad optimizadas para trabajar mejor con la escala masiva y cobertura expansiva de la Tercera Plataforma. Aunque 7 de cada 10 empresas afirman estar en el proceso de implementar una solución más de seguridad de nueva generación, 3 de esos 7 no tendrá éxito por la falta de competencia interna, por lo que el tema de seguridad es cada día más crítico”. Akamai ofrece un rendimiento a escala con la solución de distribución en la nube más grande y confiable del mundo. Sus recursos se escalan de forma que sus clientes no tengan que hacerlo. Akamai tiene una visibilidad sin igual de las propiedades más atacadas en la web y obtiene inteligencia ante amenazas continuamente a partir de inspecciones avanzadas tanto del tráfico bueno como del malo.
Challenges and Solution to Mitigate the cyber-attack on Critical Infrastruct...

SCADA systems control some of the most vital infrastructure in industrial and energy sectors, from oil and gas pipelines to nuclear facilities to water treatment plants.
Critical infrastructure is defined as the physical and IT assets, networks and services that if disrupted or destroyed would have a serious impact on the health, security, or economic wellbeing of citizens and the efficient functioning of a country’s government.
Introduction to Cloud Security

Cloud has changed the way we use computing and can yield significant economic, collaborative and efficiency benefits. But with this increased adoption, at both the personal & business level, comes increased exposure to potential risks, threats and attacks. This talk will introduce the fundamentals of cloud security, how cloud service and deployment models influence security, and practices that we can all undertake for threat and risk protection.
eSentinel™ – 360° Cybersecurity Platform Simplified

No matter how good your multiple cybersecurity tools are, an attacker will eventually find a way into your network through vulnerabilities.
Once cybercriminals acquire unauthorised access, you can only depend on the speed and performance of your IT team, to identify the threats, to manage multiple platforms to mitigate the attack. However, the time to respond and mitigate could last for hours or even days.
How Zero Trust Makes the Mission Simple & Secure

Dug Song, VP & GM, Cisco & Co-Founder, Duo Security
Zero Trust Security Summit 2020
01.28.2020 International Spy Museum
Addressing Healthcare Challenges Today

Ivanti's own healthcare vertical expert will interview an IT leader from William Osler Health System about the unique service management challenges facing healthcare providers today and share the latest on Ivanti Neurons for Healthcare.
Strategy Cloud and Security as a Service

Hans-Peter Bauer, Vice President Central and Eastern Europe, McAfee
What is zero trust model (ztm)

The Zero Trust Model of information #security simplifies how #information security is conceptualized by assuming there are no longer “trusted” interfaces, applications, traffic, networks, or users. It takes the old model— “trust but verify”—and inverts it, because recent breaches have proven that when an organization trusts, it doesn’t verify
Cyber Ethics: Cyber Security Services | VAPT and WAPT

Cyber Ethics is a Cyber Security Services for Analyzing the Vulnerability Assessment and Penetration Testing of your Network Infrastructure.
Symantec Webinar | Implementing a Zero Trust Framework to Secure Modern Workf...

Symantec cloud security experts discuss implementing Zero Trust security policies across Web, email, and cloud application access. Watch recording here: https://symc.ly/2J3Htkf.
Zero Trust Framework for Network Security

Forrester Privacy & Security 2018
September 25-26 2018, Washington DC
Zymr Cybersecurity 

Enhance Defences, Minimize The Risk, Drive Innovation with Zymr Cybersecurity Services.
Navigating the Zero Trust Journey for Today's Everywhere Workplace

Join Ivanti cybersecurity experts as they share best practices for implementing an effective zero trust security strategy at the user, device and network-access levels to ensure the optimal security posture for your organization. Learn how you can implement a multi-tiered approach to mobile phishing protection to best protect against data breaches.
Defend your Everywhere Workplace through adaptive zero trust security and adapt to modern threats faster and experience better outcomes.
Business Continuity and app Security 

Mediante el uso del marco de perímetro digital seguro, implementando un modelo “defense-in depth” se logrará la continuidad de las operaciones para evitar que los ataques maliciosos afecten las mismas y proporcionar resiliencia de acceso seguro y de red durante interrupciones, desastres naturales y calamidades. Esto permite a la fuerza de trabajo reanudar rápidamente industrias de actividades críticas y esenciales.
Zero Trust Network Access 

The above PPT explains the working of the ZTNA model for Network Security,
Cyber Security Services & Solutions - Zymr

Premium cyber security services to help minimize the risk of your business falling victim to online vulnerability and malicious cyber-attacks.
What is Zero Trust

Zero Trust: the idea that all access to corporate resources should be restricted until the user has proven their identity and access permissions, and the device has passed a security profile check. A core concept for Okta.
Micro segmentation and zero trust for security and compliance - Guardicore an...

Micro Segmentation for Zero trust security and compliance
1) What is Zero Trust?
2) How does zero trust relate to compliance?
3) Guardicore and Micro Segmentation,
4) YouAttest and Compliance
5) Short Demo and Q&A session
What is zero trust model of information security?

The Zero Trust Model of information security simplifies how information security is conceptualized by assuming there are no longer “trusted” interfaces, applications, traffic, networks, or users. It takes the old model—“trust but verify”—and inverts it, because recent breaches have proven that when an organization trusts, it doesn’t verify. (Forrester)
Proteja sus datos en cualquier servicio Cloud y Web de forma unificada

Hoy en día, una media de más de 1000 aplicaciones Cloud se está utilizando en cada empresa, de las cuales, el 98% se categoriza como «Shadow IT», lo cual significa que la dirección IT no las controla.
Además, 80% de la información que sale afuera de las empresas se comparte utilizando aplicaciones Cloud. Y más de 50% del acceso y uso de las aplicaciones Cloud se realiza desde fuera de las redes corporativas.
Debunked: 5 Myths About Zero Trust Security

In 2018, Zero Trust Security gained popularity due to its simplicity and effectiveness. Yet despite a rise in awareness, many organizations still don’t know where to start or are slow to adopt a Zero Trust approach.
The result? Breaches affected as many as 66% of companies just last year. And as hackers become more sophisticated and resourceful, the number of breaches will continue to rise.
Unless organizations adopt Zero Trust Security. In 2019, take some time to assess your company’s risk factors and learn how to implement Zero Trust Security in your organization.
Malware and the Cost of Inactivity

Breaches happen every day. The culprit? Malware. It’s no longer a question of “if” you’ll be breached, but “when”. Don’t become another statistic. Protect your organization today. Learn more here >> http://cs.co/ampvodvepg
Cisco ISE Reduces the Attack Surface by Controlling Access

Cisco ISE reduces the attack surface by controlling access and preventing unauthorized lateral movement on the network. Learn more at http://cs.co/9007BRFbW
More Related Content
What's hot
Challenges and Solution to Mitigate the cyber-attack on Critical Infrastruct...

SCADA systems control some of the most vital infrastructure in industrial and energy sectors, from oil and gas pipelines to nuclear facilities to water treatment plants.
Critical infrastructure is defined as the physical and IT assets, networks and services that if disrupted or destroyed would have a serious impact on the health, security, or economic wellbeing of citizens and the efficient functioning of a country’s government.
Introduction to Cloud Security

Cloud has changed the way we use computing and can yield significant economic, collaborative and efficiency benefits. But with this increased adoption, at both the personal & business level, comes increased exposure to potential risks, threats and attacks. This talk will introduce the fundamentals of cloud security, how cloud service and deployment models influence security, and practices that we can all undertake for threat and risk protection.
eSentinel™ – 360° Cybersecurity Platform Simplified

No matter how good your multiple cybersecurity tools are, an attacker will eventually find a way into your network through vulnerabilities.
Once cybercriminals acquire unauthorised access, you can only depend on the speed and performance of your IT team, to identify the threats, to manage multiple platforms to mitigate the attack. However, the time to respond and mitigate could last for hours or even days.
How Zero Trust Makes the Mission Simple & Secure

Dug Song, VP & GM, Cisco & Co-Founder, Duo Security
Zero Trust Security Summit 2020
01.28.2020 International Spy Museum
Addressing Healthcare Challenges Today

Ivanti's own healthcare vertical expert will interview an IT leader from William Osler Health System about the unique service management challenges facing healthcare providers today and share the latest on Ivanti Neurons for Healthcare.
Strategy Cloud and Security as a Service

Hans-Peter Bauer, Vice President Central and Eastern Europe, McAfee
What is zero trust model (ztm)

The Zero Trust Model of information #security simplifies how #information security is conceptualized by assuming there are no longer “trusted” interfaces, applications, traffic, networks, or users. It takes the old model— “trust but verify”—and inverts it, because recent breaches have proven that when an organization trusts, it doesn’t verify
Cyber Ethics: Cyber Security Services | VAPT and WAPT

Cyber Ethics is a Cyber Security Services for Analyzing the Vulnerability Assessment and Penetration Testing of your Network Infrastructure.
Symantec Webinar | Implementing a Zero Trust Framework to Secure Modern Workf...

Symantec cloud security experts discuss implementing Zero Trust security policies across Web, email, and cloud application access. Watch recording here: https://symc.ly/2J3Htkf.
Zero Trust Framework for Network Security

Forrester Privacy & Security 2018
September 25-26 2018, Washington DC
Zymr Cybersecurity 

Enhance Defences, Minimize The Risk, Drive Innovation with Zymr Cybersecurity Services.
Navigating the Zero Trust Journey for Today's Everywhere Workplace

Join Ivanti cybersecurity experts as they share best practices for implementing an effective zero trust security strategy at the user, device and network-access levels to ensure the optimal security posture for your organization. Learn how you can implement a multi-tiered approach to mobile phishing protection to best protect against data breaches.
Defend your Everywhere Workplace through adaptive zero trust security and adapt to modern threats faster and experience better outcomes.
Business Continuity and app Security 

Mediante el uso del marco de perímetro digital seguro, implementando un modelo “defense-in depth” se logrará la continuidad de las operaciones para evitar que los ataques maliciosos afecten las mismas y proporcionar resiliencia de acceso seguro y de red durante interrupciones, desastres naturales y calamidades. Esto permite a la fuerza de trabajo reanudar rápidamente industrias de actividades críticas y esenciales.
Zero Trust Network Access 

The above PPT explains the working of the ZTNA model for Network Security,
Cyber Security Services & Solutions - Zymr

Premium cyber security services to help minimize the risk of your business falling victim to online vulnerability and malicious cyber-attacks.
What is Zero Trust

Zero Trust: the idea that all access to corporate resources should be restricted until the user has proven their identity and access permissions, and the device has passed a security profile check. A core concept for Okta.
Micro segmentation and zero trust for security and compliance - Guardicore an...

Micro Segmentation for Zero trust security and compliance
1) What is Zero Trust?
2) How does zero trust relate to compliance?
3) Guardicore and Micro Segmentation,
4) YouAttest and Compliance
5) Short Demo and Q&A session
What is zero trust model of information security?

The Zero Trust Model of information security simplifies how information security is conceptualized by assuming there are no longer “trusted” interfaces, applications, traffic, networks, or users. It takes the old model—“trust but verify”—and inverts it, because recent breaches have proven that when an organization trusts, it doesn’t verify. (Forrester)
Proteja sus datos en cualquier servicio Cloud y Web de forma unificada

Hoy en día, una media de más de 1000 aplicaciones Cloud se está utilizando en cada empresa, de las cuales, el 98% se categoriza como «Shadow IT», lo cual significa que la dirección IT no las controla.
Además, 80% de la información que sale afuera de las empresas se comparte utilizando aplicaciones Cloud. Y más de 50% del acceso y uso de las aplicaciones Cloud se realiza desde fuera de las redes corporativas.
Debunked: 5 Myths About Zero Trust Security

In 2018, Zero Trust Security gained popularity due to its simplicity and effectiveness. Yet despite a rise in awareness, many organizations still don’t know where to start or are slow to adopt a Zero Trust approach.
The result? Breaches affected as many as 66% of companies just last year. And as hackers become more sophisticated and resourceful, the number of breaches will continue to rise.
Unless organizations adopt Zero Trust Security. In 2019, take some time to assess your company’s risk factors and learn how to implement Zero Trust Security in your organization.
What's hot (20)
Challenges and Solution to Mitigate the cyber-attack on Critical Infrastruct...

Challenges and Solution to Mitigate the cyber-attack on Critical Infrastruct...
eSentinel™ – 360° Cybersecurity Platform Simplified

eSentinel™ – 360° Cybersecurity Platform Simplified
Cyber Ethics: Cyber Security Services | VAPT and WAPT

Cyber Ethics: Cyber Security Services | VAPT and WAPT
Symantec Webinar | Implementing a Zero Trust Framework to Secure Modern Workf...

Symantec Webinar | Implementing a Zero Trust Framework to Secure Modern Workf...
Navigating the Zero Trust Journey for Today's Everywhere Workplace

Navigating the Zero Trust Journey for Today's Everywhere Workplace
Micro segmentation and zero trust for security and compliance - Guardicore an...

Micro segmentation and zero trust for security and compliance - Guardicore an...
Proteja sus datos en cualquier servicio Cloud y Web de forma unificada

Proteja sus datos en cualquier servicio Cloud y Web de forma unificada
Viewers also liked
Malware and the Cost of Inactivity

Breaches happen every day. The culprit? Malware. It’s no longer a question of “if” you’ll be breached, but “when”. Don’t become another statistic. Protect your organization today. Learn more here >> http://cs.co/ampvodvepg
Cisco ISE Reduces the Attack Surface by Controlling Access

Cisco ISE reduces the attack surface by controlling access and preventing unauthorized lateral movement on the network. Learn more at http://cs.co/9007BRFbW
A Reality Check on the State of Cybersecurity

In 2015, companies need to challenge the perception of security versus the reality of a connected world of people, process, data and things in the Internet of Everything. Learn more at cisco.com/go/securityservices
Identify Zero-Day Breaches with Cognitive Threat Analytics on Cisco Web Secur...

Cognitive Threat Analytics is a technology that analyzes web requests to identify Command & Control traffic, identifying threats that are currently present in a network. It is currently available across the entire Cisco Web Security portfolio, including Cloud Web Security (CWS) and the Web Security Appliance (WSA). To learn more, watch this webinar: http://cs.co/9000BuggO
Cisco Web and Email Security Overview

The top two attack vectors for malware are email and web browsers. Watering-hole attacks conceal malware on member-based sites and phishing scams can target individuals with personal details. This PPT describes a different security approach to protect against these threats while achieving business growth, efficiency and lowered expenses. The presentation features Cisco Email, Web and Cloud Web Security and covers basic features, offers, benefits, newest features and product integrations. Watch the webinar: http://cs.co/9004BGqvy
Balance Data Center Security and Performance

Today's data centers require an approach to security that does not compromise performance or functionality. Identify where you may have gaps in your data center security, and learn what solutions are available to close or mitigate those gaps. Take action to secure your data center. Download our white paper >> http://cs.co/9000BBV22
2013 Cisco Annual Security Report

Expanding connectivity from any device to many clouds is having a significant impact on the threat landscape. As more people embrace multiple devices that connect to various networks and services through a wide range of applications, more vulnerabilities are exposed. Delve into the security threats and challenges of 2012 with analysis from Cisco's global threat intelligence. Download the report: http://www.cisco.com/go/securityreport.
Enterprise Strategy Group: Security Survey

Understand what your organization is up against and where security is needed.
Defending the Data Center: Managing Users from the Edge to the Application

Simplify your network security and engineering through Cisco’s TrustSec for the Data Center.
From Physical to Virtual to Cloud

Take a deep dive into 3 important deployment types for Cisco Security.
McAllen Intermediate School District

Migrated to Cisco Identity Services Engine (ISE) 1.2 as best solution to level academic environment with secure network access: Transforming Learning in Campus, Classroom & Community.
Data Center Security Now and into the Future

Understand all the latest Data Center trends and Data Center security requirements. Take a deep dive on Cisco’s value-added integrated approach on Data Center Security Strategy.
Inside NetQin Mobile Inc. (NYSE: NQ) - By iChinaStock

China-based NetQin Mobile Inc. (NYSE: NQ) sells mobile security services via freemium model. Its primary users are feature phone and low-end smartphones, mostly to Chinese customers but also some internationally. Qihoo (NYSE: QIHU) is a key competitor.
andrew milroy - top security trends and takeaways for 2013

Andrew Milroy presentation at recent Trend Micro Evolve Security Conference
Viewers also liked (14)
Cisco ISE Reduces the Attack Surface by Controlling Access

Cisco ISE Reduces the Attack Surface by Controlling Access
Identify Zero-Day Breaches with Cognitive Threat Analytics on Cisco Web Secur...

Identify Zero-Day Breaches with Cognitive Threat Analytics on Cisco Web Secur...
Defending the Data Center: Managing Users from the Edge to the Application

Defending the Data Center: Managing Users from the Edge to the Application
Inside NetQin Mobile Inc. (NYSE: NQ) - By iChinaStock

Inside NetQin Mobile Inc. (NYSE: NQ) - By iChinaStock
andrew milroy - top security trends and takeaways for 2013

andrew milroy - top security trends and takeaways for 2013
Similar to Infographic: Security for Mobile Service Providers
5G mission diary: Houston, we have a problem

In 2020, many telecommunication companies will debut their first commercial 5G networks. The 5G mission has become a hot-button topic for the entire telecom community. But these networks have inherited many threats from their 3G and 4G forebears. Long-known weaknesses in security protocols and algorithms have been baked into new 5G systems. This creates a perfect storm for threat actors to target 5G security weaknesses using their old tricks.
Watch the webinar recording, where PT experts Paolo Emiliani, Head of Pre-Sales Engineering team, and Jun Kim, Managing Director, Korea, help you to navigate the tricky path to 5G deployment and:
explain new 5G trust and service delivery models
assess the evolving 5G threat landscape and privacy issues
explore realms of 5G protection with a focus on real-life cases
discuss new and emerging 5G threats affecting telecom infrastructure and end devices
explain why roaming protection in 5G is a game-changer
underline essential mitigation techniques for 5G security
Follow us on LinkedIn to keep up with our upcoming webinars and events: https://www.linkedin.com/company/positive-tech/
Transform your enterprise branch with secure sd-wan

Timo Lohenoja, Systems engineer Finland and the Baltics, Fortinet, https://dssitsec.eu
Security course: exclusive 5G SA pitfalls and new changes to legislation

5G will mark the transition to an entirely new era in connectivity. It will link together critical infrastructure elements, making security an absolute imperative. This comes as no surprise — regulators have been enhancing their control over telecom security for some time already, as seen in the UK and Europe. We believe that this growth in regulative powers is part of a global tendency — one that is forcing change on all MNOs with regards to network security.
Our webinar covers:
- Types of threats in the 5G standalone core that you should be aware of (based on our exclusive research)
- Building appropriate guidelines to maintain reliability and resilience
- Reinforcing security strategy as a new global tendency in telecommunications, including an overview of recent changes to legislation in the UK and Europe
Telecom Security in the Era of 5G and IoT

CTO at Positive Technologies, Dmitry Kurbatov discusses what kind of security risks are associated with 5G telecommunications networks and to what extent thеse risks could be managed. Topics include:
• How the 5G core network will work, and how it differs from the current telecom infrastructure.
• Benefits that the innovative 5G slicing technology can bring, and what its security risks will be.
• What new protocols, interfaces, and infrastructure-enhancing technologies like network functions virtualization will take off in the near future.
• Compatibility concerns with 4G, 3G, and 2G networks. What does this mean for 5G?
Scaling Mobile Network Security for LTE: A Multi-Layer Approach

Service providers know they need to protect the network, maintain stability, and manage millions of real-time sessions without costs spiraling out of control. In this paper, Patrick Donegan, Senior Analyst at Heavy Reading, outlines the new challenges introduced by LTE and the security architecture in the service provider network. He stresses the importance of implementing a dynamic, multi-layered security approach that makes use of virtualization, service chaining, and real-time subscriber awareness.
Security is a top priority for service providers, who must deliver superior network quality and customer experiences without adding complexity or cost. F5 Networks offers a suite of dynamic, multi-layered solutions that simplify delivery architectures, boost service availability, and enhance application awareness and control
A Different Approach to Securing Your Cloud Journey

Whether you are just exploring moving workloads to the cloud, or are fully cloud-enabled, one thing is certain: security has changed from a purely on-premise environment.
As cybersecurity risks continue to grow with more advanced attackers and more digital surface area, how you think about staying secure without compromising user experience must adapt.
During this talk, you will:
- Hear how global consistency, agile controls, and predictable costs are goals and principles that matter in this new environment
- Be able to evaluate your current plans against a "customer security model"
Cisco Connect 2018 Thailand - Cisco SD-WAN next generation wan to power your ...

Cisco Connect 2018 Thailand - Cisco SD-WAN next generation wan to power your ...NetworkCollaborators
Cisco Connect 2018 Thailand How to deal with the impact of digital transformation on networks 

Digital transformation has increased the importance of the network, particularly the edge, where customers, employees, cloud applications and IoT devices connect to the enterprise. The legacy static and non-dierentiated network edge of years past is no longer suicient for many reasons, so as companies embark on digital-transformation plans, their networks must evolve.
SP 5G: Unified Enablement Platform 

Redefining the Network and realizing opportunities with Cisco 5G.
Data Center Trends And Network Security Impact

Perimeter firewall
Core network segmentation
Virtualization
Cloud computing (infrastructure-as-a-service)
Software-defined networking (SDN)
Network Function Virtualization (NFV)
WatchGuard: Bring Your Own Device or Bring Your Own Danger

The BYOD Trend. Find out how to embrace employee devices while protecting your network from threats. Review top strategies for embracing BYOD while managing risks, compliance, and end-user needs.
Roeing Corporation & WatchGuard presentation, September 2013.
Best 5G Security Solutions - SecurityGen

The world is looking forward to the 5G age. A huge digital shift will shape our society, and MNOs are
working hard to make it happen. They are building completely new infrastructure, rethinking
traditional practices, and creating new business models to recoup all these expenses. New Service
offerings will be a key ROI strategy for telcos. Market leadership will depend on delivering diverse
and top-quality services in which security is a value-add.
5G Security Program Datasheet (2).pdf

Secure your 5G future with SecGen's advanced 5G Security Solutions. Contact us at or visit our website to schedule a consultation and fortify your network against emerging threats. Trust SecGen for unmatched expertise in 5G security and protect your network with confidence.
5G Security Program -Case Studies 

The world is looking forward to the 5G age. A huge digital shift will shape our society, and MNOs are
working hard to make it happen. They are building completely new infrastructure, rethinking
traditional practices, and creating new business models to recoup all these expenses. New Service
offerings will be a key ROI strategy for telcos. Market leadership will depend on delivering diverse
and top-quality services in which security is a value-add.
SecurityGen's OSS/BSS Solutions: Navigating the Complexity of Modern Operations

In the complex landscape of modern business operations, SecurityGen stands as a beacon of clarity with its OSS/BSS solutions. Tailored to meet the diverse needs of businesses, SecurityGen's approach to Operations Support System (OSS) and Business Support System (BSS) is both intuitive and comprehensive. From network optimization to customer engagement, our solutions provide a unified platform for managing the intricacies of daily operations. SecurityGen's commitment to user-friendly interfaces ensures that organizations can navigate the complexities with ease, driving efficiency and innovation across all facets of their operations.
Similar to Infographic: Security for Mobile Service Providers (20)
Transform your enterprise branch with secure sd-wan

Transform your enterprise branch with secure sd-wan
Security course: exclusive 5G SA pitfalls and new changes to legislation

Security course: exclusive 5G SA pitfalls and new changes to legislation
Scaling Mobile Network Security for LTE: A Multi-Layer Approach

Scaling Mobile Network Security for LTE: A Multi-Layer Approach
A Different Approach to Securing Your Cloud Journey

A Different Approach to Securing Your Cloud Journey
Cisco Connect 2018 Thailand - Cisco SD-WAN next generation wan to power your ...

Cisco Connect 2018 Thailand - Cisco SD-WAN next generation wan to power your ...
How to deal with the impact of digital transformation on networks 

How to deal with the impact of digital transformation on networks
Cisco Connect 2018 Malaysia - Secure data center and mobility solutions

Cisco Connect 2018 Malaysia - Secure data center and mobility solutions
WatchGuard: Bring Your Own Device or Bring Your Own Danger

WatchGuard: Bring Your Own Device or Bring Your Own Danger
SecurityGen's OSS/BSS Solutions: Navigating the Complexity of Modern Operations

SecurityGen's OSS/BSS Solutions: Navigating the Complexity of Modern Operations
More from Cisco Security
Incident Response Services Template - Cisco Security

When responding to a security incident, communication is perhaps one of the most important, and yet, most overlooked aspects. This Cisco Security Incident Response Services Template has been used and refined for a number of years now in both Fortune 100 companies as well as with all of our Cisco Security Incident Response Services customers.
Learn more about incident response communications here: https://blogs.cisco.com/security/incident-response-fundamentals-communication
AMP Helps Cisco IT Catch 50% More Malware threats

These statistics show how the Email Security Appliance with Advanced Malware Protection allows Cisco IT to realize its comprehensive threat-centric email security strategy. Learn more: http://cs.co/9000BD620
The Cost of Inactivity: Malware Infographic

As the cost and likelihood of a breach grows you can't afford "good enough" protection before, during, AND after an attack. Protect your brand and data with Cisco email and web security.
Learn more: http://cs.co/9003hKu3, http://cs.co/9003hKu9
Cisco Addresses the Full Attack Continuum

Learn key capabilities to improve protection from advanced attacks. Featuring research from Gartner.
Infonetics Network and Content Security Vendor Scorecard

Profiles, analyzes and ranks the 8 largest global vendors of network and content security solutions.
Gartner Newsletter: Cisco TrustSec Deployed Across Enterprise Campus, Branch ...

Gartner report on Cisco TrustSec assessing technical components, interoperability considerations, Cisco’s progress in implementing support across product lines and customer deployment experiences.
Cisco 2014 Midyear Security Report

Download now to learn the latest industry trends and how to identify weak links in the security chain.
String of Paerls Infographic

String of Paerls –> Learn how an integrated threat defense can both detect and protect against socially engineered exploits. https://communities.cisco.com/docs/DOC-54686
Midyear Security Report Infographic

Get more details from the Cisco Midyear Security Report >> http://cs.co/MSR14_S
Cisco Annual Security Report Infographic

Growing Attacks Against the Internet Infrastructure. Learn more from the Cisco Annual Security Report: http://cs.co/CASR14_L
City of Tomorrow Builds in Next-Generation Security

City of El Paso relies on Cisco ASA 5585-X Series to secure network to best deliver municipality’s services.
Laser Pioneer Secures Network End-to-End to Protect Assets

Coherent mitigates against global cyber threats with Cisco Cloud Web Security.
Leveraging Context-Aware Security to Safeguard Patient Data

Texas Heart Institute controls network access to meet regulatory compliance needs for its locations located in the world’s largest medical complex.
William Paterson University

Transitioned to Cisco Identity Services Engine (ISE) 1.2 to facilitate consistent, secure wireless network access by students bringing range of devices on campus, broadening reach of bring- your-own-device (BYOD) policy.
Secure, Automated Network Access for Any Device on Campus

Trinity University relies on Cisco ISE to enable students, faculty, and guests easy network onboarding.
More from Cisco Security (16)
Incident Response Services Template - Cisco Security

Incident Response Services Template - Cisco Security
Infonetics Network and Content Security Vendor Scorecard

Infonetics Network and Content Security Vendor Scorecard
Gartner Newsletter: Cisco TrustSec Deployed Across Enterprise Campus, Branch ...

Gartner Newsletter: Cisco TrustSec Deployed Across Enterprise Campus, Branch ...
The Evolution of and Need for Secure Network Access

The Evolution of and Need for Secure Network Access
City of Tomorrow Builds in Next-Generation Security

City of Tomorrow Builds in Next-Generation Security
Laser Pioneer Secures Network End-to-End to Protect Assets

Laser Pioneer Secures Network End-to-End to Protect Assets
Leveraging Context-Aware Security to Safeguard Patient Data

Leveraging Context-Aware Security to Safeguard Patient Data
Secure, Automated Network Access for Any Device on Campus

Secure, Automated Network Access for Any Device on Campus
Recently uploaded
Unsubscribed: Combat Subscription Fatigue With a Membership Mentality by Head...

Unsubscribed: Combat Subscription Fatigue With a Membership Mentality by Head of Product, Amazon Games
FIDO Alliance Osaka Seminar: The WebAuthn API and Discoverable Credentials.pdf

FIDO Alliance Osaka Seminar
The Art of the Pitch: WordPress Relationships and Sales

Clients don’t know what they don’t know. What web solutions are right for them? How does WordPress come into the picture? How do you make sure you understand scope and timeline? What do you do if sometime changes?
All these questions and more will be explored as we talk about matching clients’ needs with what your agency offers without pulling teeth or pulling your hair out. Practical tips, and strategies for successful relationship building that leads to closing the deal.
JMeter webinar - integration with InfluxDB and Grafana

Watch this recorded webinar about real-time monitoring of application performance. See how to integrate Apache JMeter, the open-source leader in performance testing, with InfluxDB, the open-source time-series database, and Grafana, the open-source analytics and visualization application.
In this webinar, we will review the benefits of leveraging InfluxDB and Grafana when executing load tests and demonstrate how these tools are used to visualize performance metrics.
Length: 30 minutes
Session Overview
-------------------------------------------
During this webinar, we will cover the following topics while demonstrating the integrations of JMeter, InfluxDB and Grafana:
- What out-of-the-box solutions are available for real-time monitoring JMeter tests?
- What are the benefits of integrating InfluxDB and Grafana into the load testing stack?
- Which features are provided by Grafana?
- Demonstration of InfluxDB and Grafana using a practice web application
To view the webinar recording, go to:
https://www.rttsweb.com/jmeter-integration-webinar
Generating a custom Ruby SDK for your web service or Rails API using Smithy

Have you ever wanted a Ruby client API to communicate with your web service? Smithy is a protocol-agnostic language for defining services and SDKs. Smithy Ruby is an implementation of Smithy that generates a Ruby SDK using a Smithy model. In this talk, we will explore Smithy and Smithy Ruby to learn how to generate custom feature-rich SDKs that can communicate with any web service, such as a Rails JSON API.
LF Energy Webinar: Electrical Grid Modelling and Simulation Through PowSyBl -...

Do you want to learn how to model and simulate an electrical network from scratch in under an hour?
Then welcome to this PowSyBl workshop, hosted by Rte, the French Transmission System Operator (TSO)!
During the webinar, you will discover the PowSyBl ecosystem as well as handle and study an electrical network through an interactive Python notebook.
PowSyBl is an open source project hosted by LF Energy, which offers a comprehensive set of features for electrical grid modelling and simulation. Among other advanced features, PowSyBl provides:
- A fully editable and extendable library for grid component modelling;
- Visualization tools to display your network;
- Grid simulation tools, such as power flows, security analyses (with or without remedial actions) and sensitivity analyses;
The framework is mostly written in Java, with a Python binding so that Python developers can access PowSyBl functionalities as well.
What you will learn during the webinar:
- For beginners: discover PowSyBl's functionalities through a quick general presentation and the notebook, without needing any expert coding skills;
- For advanced developers: master the skills to efficiently apply PowSyBl functionalities to your real-world scenarios.
Software Delivery At the Speed of AI: Inflectra Invests In AI-Powered Quality

In this insightful webinar, Inflectra explores how artificial intelligence (AI) is transforming software development and testing. Discover how AI-powered tools are revolutionizing every stage of the software development lifecycle (SDLC), from design and prototyping to testing, deployment, and monitoring.
Learn about:
• The Future of Testing: How AI is shifting testing towards verification, analysis, and higher-level skills, while reducing repetitive tasks.
• Test Automation: How AI-powered test case generation, optimization, and self-healing tests are making testing more efficient and effective.
• Visual Testing: Explore the emerging capabilities of AI in visual testing and how it's set to revolutionize UI verification.
• Inflectra's AI Solutions: See demonstrations of Inflectra's cutting-edge AI tools like the ChatGPT plugin and Azure Open AI platform, designed to streamline your testing process.
Whether you're a developer, tester, or QA professional, this webinar will give you valuable insights into how AI is shaping the future of software delivery.
Assuring Contact Center Experiences for Your Customers With ThousandEyes

Presented by Suzanne Phillips and Alex Marcotte
Knowledge engineering: from people to machines and back

Keynote at the 21st European Semantic Web Conference
Kubernetes & AI - Beauty and the Beast !?! @KCD Istanbul 2024

As AI technology is pushing into IT I was wondering myself, as an “infrastructure container kubernetes guy”, how get this fancy AI technology get managed from an infrastructure operational view? Is it possible to apply our lovely cloud native principals as well? What benefit’s both technologies could bring to each other?
Let me take this questions and provide you a short journey through existing deployment models and use cases for AI software. On practical examples, we discuss what cloud/on-premise strategy we may need for applying it to our own infrastructure to get it to work from an enterprise perspective. I want to give an overview about infrastructure requirements and technologies, what could be beneficial or limiting your AI use cases in an enterprise environment. An interactive Demo will give you some insides, what approaches I got already working for real.
DevOps and Testing slides at DASA Connect

My and Rik Marselis slides at 30.5.2024 DASA Connect conference. We discuss about what is testing, then what is agile testing and finally what is Testing in DevOps. Finally we had lovely workshop with the participants trying to find out different ways to think about quality and testing in different parts of the DevOps infinity loop.
Empowering NextGen Mobility via Large Action Model Infrastructure (LAMI): pav...

Empowering NextGen Mobility via Large Action Model Infrastructure (LAMI)
Bits & Pixels using AI for Good.........

A whirlwind tour of tech & AI for socio-environmental impact.
Key Trends Shaping the Future of Infrastructure.pdf

Keynote at DIGIT West Expo, Glasgow on 29 May 2024.
Cheryl Hung, ochery.com
Sr Director, Infrastructure Ecosystem, Arm.
The key trends across hardware, cloud and open-source; exploring how these areas are likely to mature and develop over the short and long-term, and then considering how organisations can position themselves to adapt and thrive.
Designing Great Products: The Power of Design and Leadership by Chief Designe...

Designing Great Products: The Power of Design and Leadership by Chief Designer, Beats by Dr Dre
To Graph or Not to Graph Knowledge Graph Architectures and LLMs

Reflecting on new architectures for knowledge based systems in light of generative ai
Recently uploaded (20)
Unsubscribed: Combat Subscription Fatigue With a Membership Mentality by Head...

Unsubscribed: Combat Subscription Fatigue With a Membership Mentality by Head...
FIDO Alliance Osaka Seminar: The WebAuthn API and Discoverable Credentials.pdf

FIDO Alliance Osaka Seminar: The WebAuthn API and Discoverable Credentials.pdf
The Art of the Pitch: WordPress Relationships and Sales

The Art of the Pitch: WordPress Relationships and Sales
JMeter webinar - integration with InfluxDB and Grafana

JMeter webinar - integration with InfluxDB and Grafana
Generating a custom Ruby SDK for your web service or Rails API using Smithy

Generating a custom Ruby SDK for your web service or Rails API using Smithy
LF Energy Webinar: Electrical Grid Modelling and Simulation Through PowSyBl -...

LF Energy Webinar: Electrical Grid Modelling and Simulation Through PowSyBl -...
FIDO Alliance Osaka Seminar: Passkeys at Amazon.pdf

FIDO Alliance Osaka Seminar: Passkeys at Amazon.pdf
Software Delivery At the Speed of AI: Inflectra Invests In AI-Powered Quality

Software Delivery At the Speed of AI: Inflectra Invests In AI-Powered Quality
Assuring Contact Center Experiences for Your Customers With ThousandEyes

Assuring Contact Center Experiences for Your Customers With ThousandEyes
Knowledge engineering: from people to machines and back

Knowledge engineering: from people to machines and back
Kubernetes & AI - Beauty and the Beast !?! @KCD Istanbul 2024

Kubernetes & AI - Beauty and the Beast !?! @KCD Istanbul 2024
FIDO Alliance Osaka Seminar: FIDO Security Aspects.pdf

FIDO Alliance Osaka Seminar: FIDO Security Aspects.pdf
FIDO Alliance Osaka Seminar: Passkeys and the Road Ahead.pdf

FIDO Alliance Osaka Seminar: Passkeys and the Road Ahead.pdf
Empowering NextGen Mobility via Large Action Model Infrastructure (LAMI): pav...

Empowering NextGen Mobility via Large Action Model Infrastructure (LAMI): pav...
Key Trends Shaping the Future of Infrastructure.pdf

Key Trends Shaping the Future of Infrastructure.pdf
Designing Great Products: The Power of Design and Leadership by Chief Designe...

Designing Great Products: The Power of Design and Leadership by Chief Designe...
To Graph or Not to Graph Knowledge Graph Architectures and LLMs

To Graph or Not to Graph Knowledge Graph Architectures and LLMs
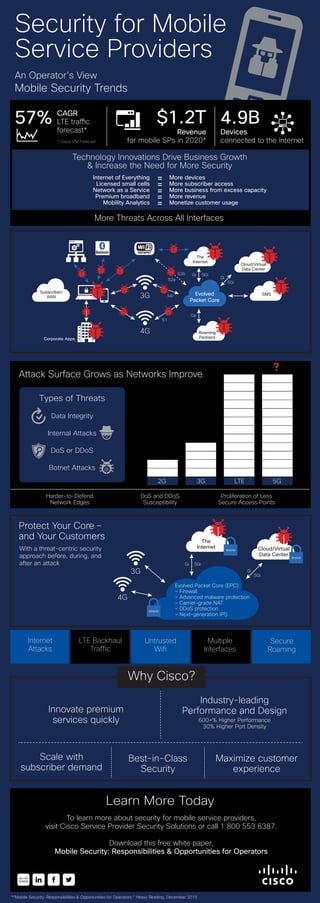
Infographic: Security for Mobile Service Providers
- 1. Security for Mobile Service Providers An Operator’s View Mobile Security Trends Evolved Packet Core Roaming Partners SMS The Internet Cloud/Virtual Data Center 4G 3G Corporate Apps Subscriber/ RAN SGi Gi SGi Gi Gp S2b S2a lub S1 57% CAGR LTE traffic forecast* * Cisco VNI Forecast $1.2T Revenue for mobile SPs in 2020* 4.9B Devices connected to the internet More Threats Across All Interfaces 2G 3G LTE 5G ? Attack Surface Grows as Networks Improve More devices More subscriber access More business from excess capacity More revenue Monetize customer usage Internet of Everything Licensed small cells Network as a Service Premium broadband Mobility Analytics = = = = = Types of Threats Data Integrity Internal Attacks DoS or DDoS Botnet Attacks Harder-to-Defend Network Edges DoS and DDoS Susceptibility Proliferation of Less Secure Access Points 4G 3G Evolved Packet Core (EPC) - Firewall - Advanced malware protection - Carrier-grade NAT - DDoS protection - Next-generation IPS Cloud/Virtual Data Center SGi Gi SGi Gi www www The Internet www Protect Your Core – and Your Customers With a threat-centric security approach before, during, and after an attack Industry-leading Performance and Design 600+% Higher Performance 30% Higher Port Density Technology Innovations Drive Business Growth & Increase the Need for More Security Innovate premium services quickly Maximize customer experience Best-in-Class Security Scale with subscriber demand *“Mobile Security: Responsibilities & Opportunities for Operators,” Heavy Reading, December 2015 Learn More Today To learn more about security for mobile service providers, visit Cisco Service Provider Security Solutions or call 1 800 553 6387. Download this free white paper, Mobile Security: Responsibilities & Opportunities for Operators Why Cisco? Internet Attacks LTE Backhaul Traffic Untrusted Wifi Multiple Interfaces Secure Roaming
