The document discusses SAP's cloud security practices. It covers several areas:
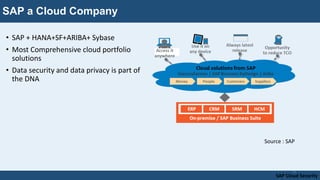
- SAP's cloud portfolio and focus on security as core to their cloud business model.
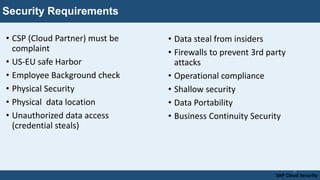
- The various security regulations and requirements SAP aims to comply with regarding things like data centers, networks, identity management and data security.
- How SAP implements logical and physical isolation of customer data through dedicated infrastructure, encryption, access controls and other means.
- SAP's backup/recovery and compliance capabilities like frequent encrypted snapshots and audit logging to support regulations.