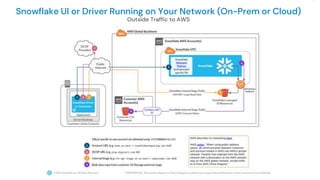
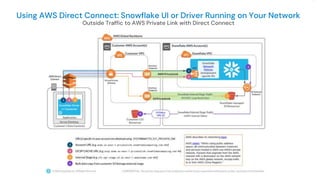
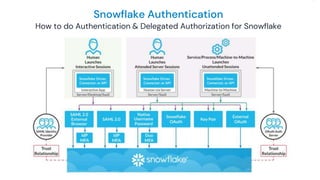
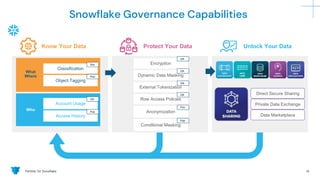
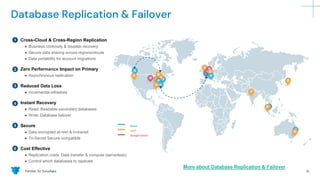
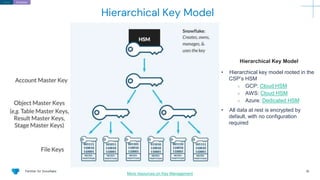
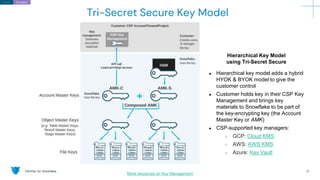
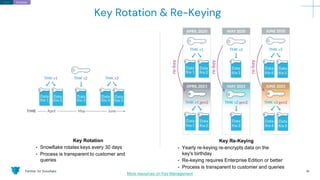
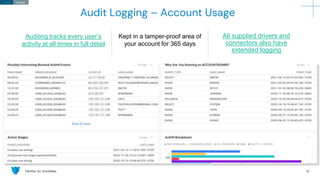
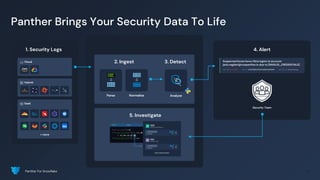
The document outlines how Panther integrates with Snowflake to enhance security and compliance for Snowflake's data cloud. It covers security best practices, continuous monitoring, authentication methods, and features such as encryption, auditing, and data governance. Additionally, it describes the functionality of Panther for detecting unauthorized access and configuration changes through built-in detection rules.