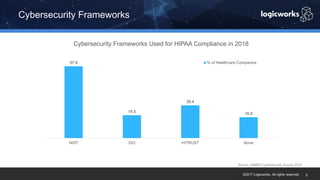
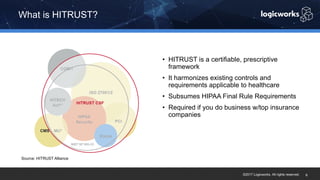
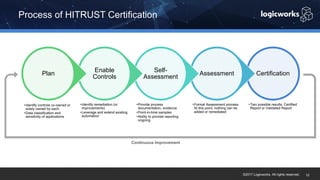
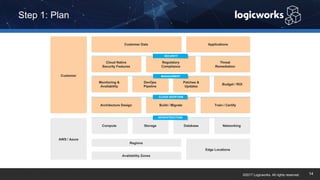
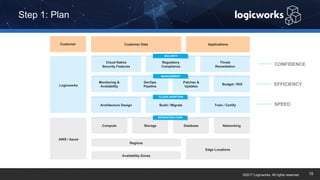
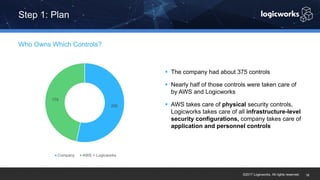
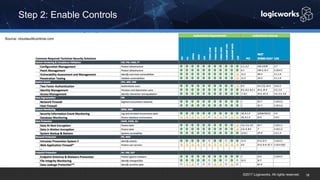
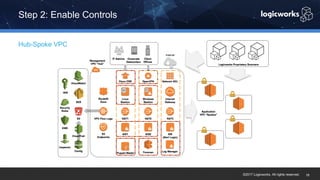
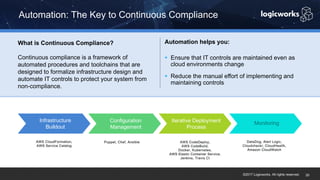
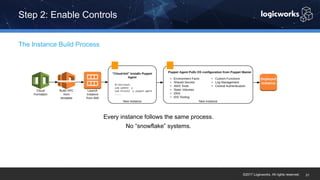
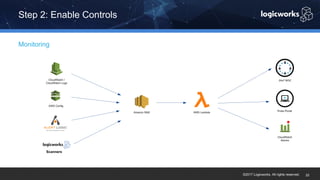
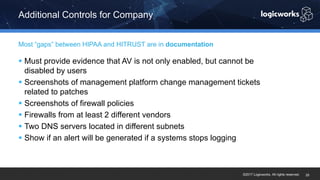
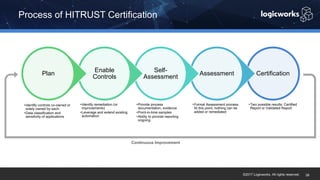
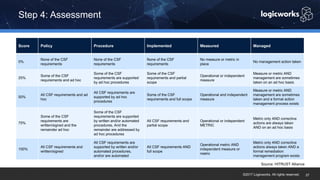
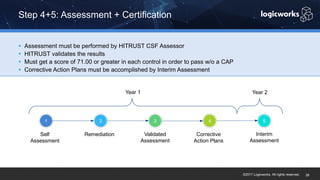
§ The company had to achieve HITRUST certification due to a new requirement from their parent organization. They worked with Logicworks and AWS to rearchitect their existing HIPAA-compliant AWS environment to meet HITRUST standards within 6 months. Logicworks and AWS provided evidence for 175 of the 400 required controls, reducing the company's time and effort for compliance. After enabling controls, undergoing assessment, and completing corrective action plans, the company achieved HITRUST certification within the 6 month deadline at a cost that was approximately 20% higher than their previous HIPAA-compliant environment.