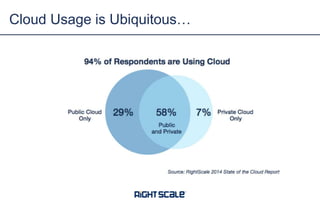
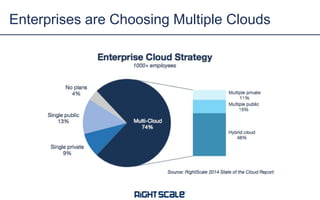
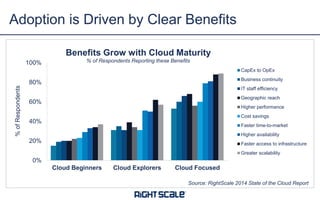
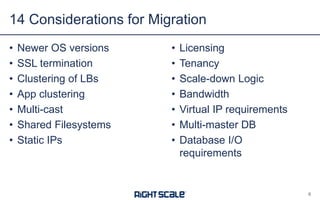
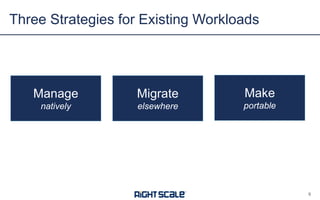
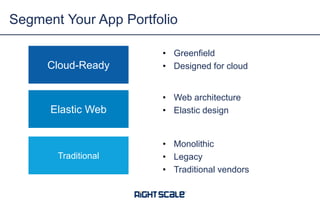
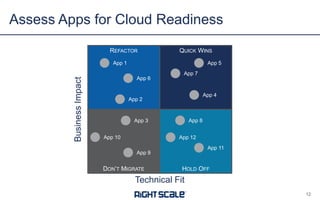
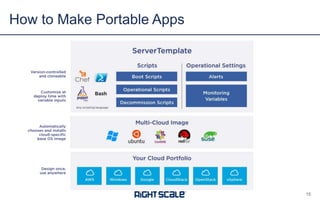
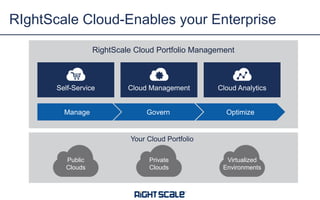
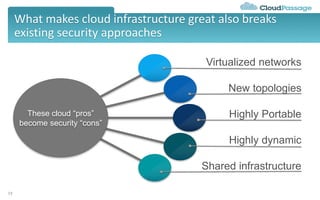
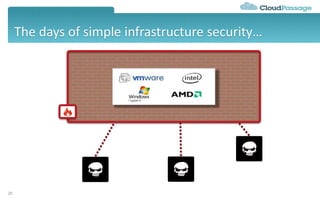
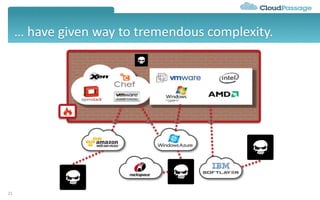
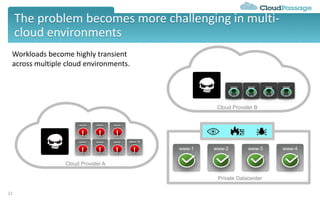
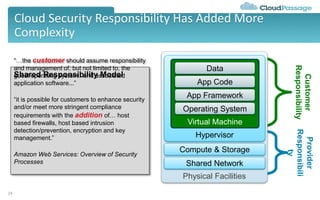
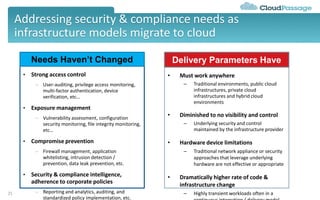
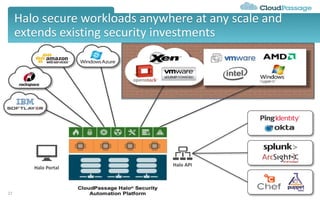
The document discusses best practices and security considerations for cloud migration, highlighting the increasing adoption of hybrid cloud solutions among enterprises. Key strategies include understanding existing workload realities, planning for portability, and accounting for security challenges that arise in multi-cloud environments. It emphasizes the need for strong access control, exposure management, and the use of automated security platforms to manage compliance and security across different cloud infrastructures.