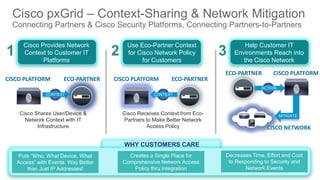
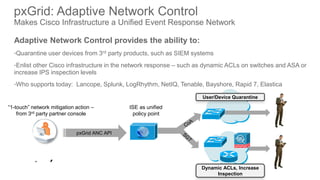
The document discusses Cisco's Platform Exchange Grid (pxGrid) and its integration with security platforms, focusing on functionality, use cases, and deployment perspectives from partners and Cisco IT. It emphasizes context sharing for improved security event response and access policy management, highlighting the ease of integration for IT departments. Additionally, it presents the benefits of using pxGrid for adaptive network control, customer implementations, and developer resources available for building integrations.