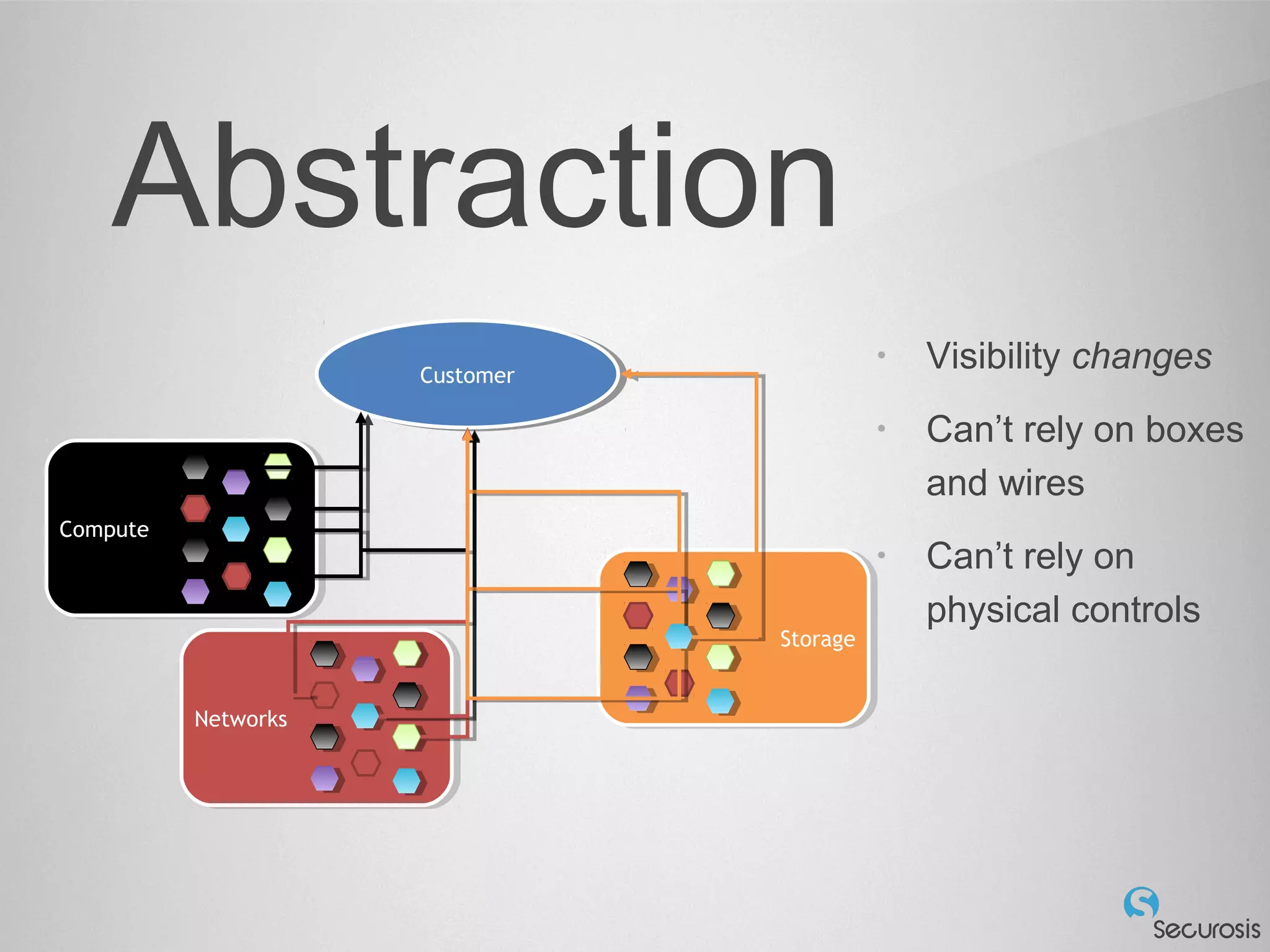
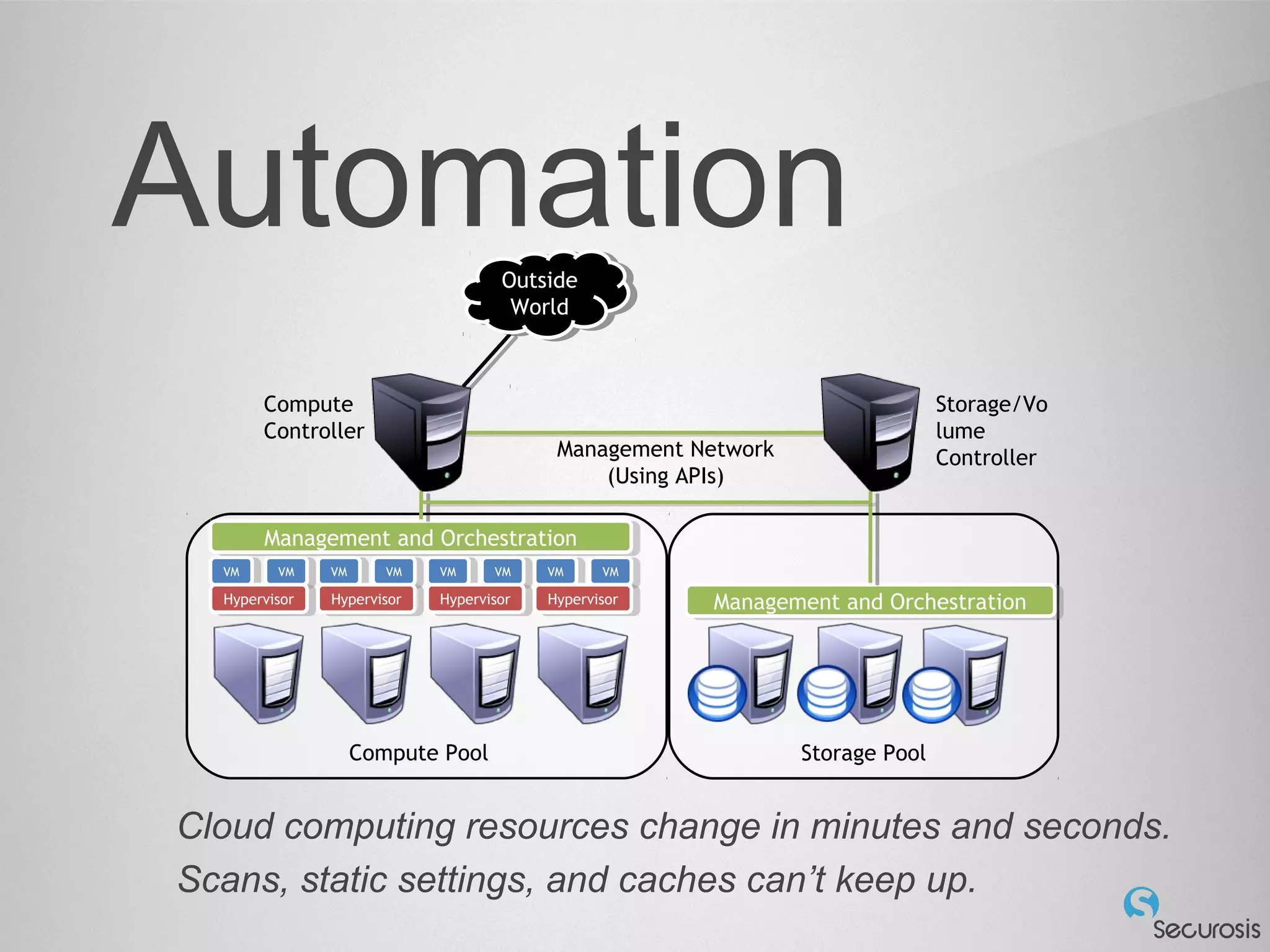
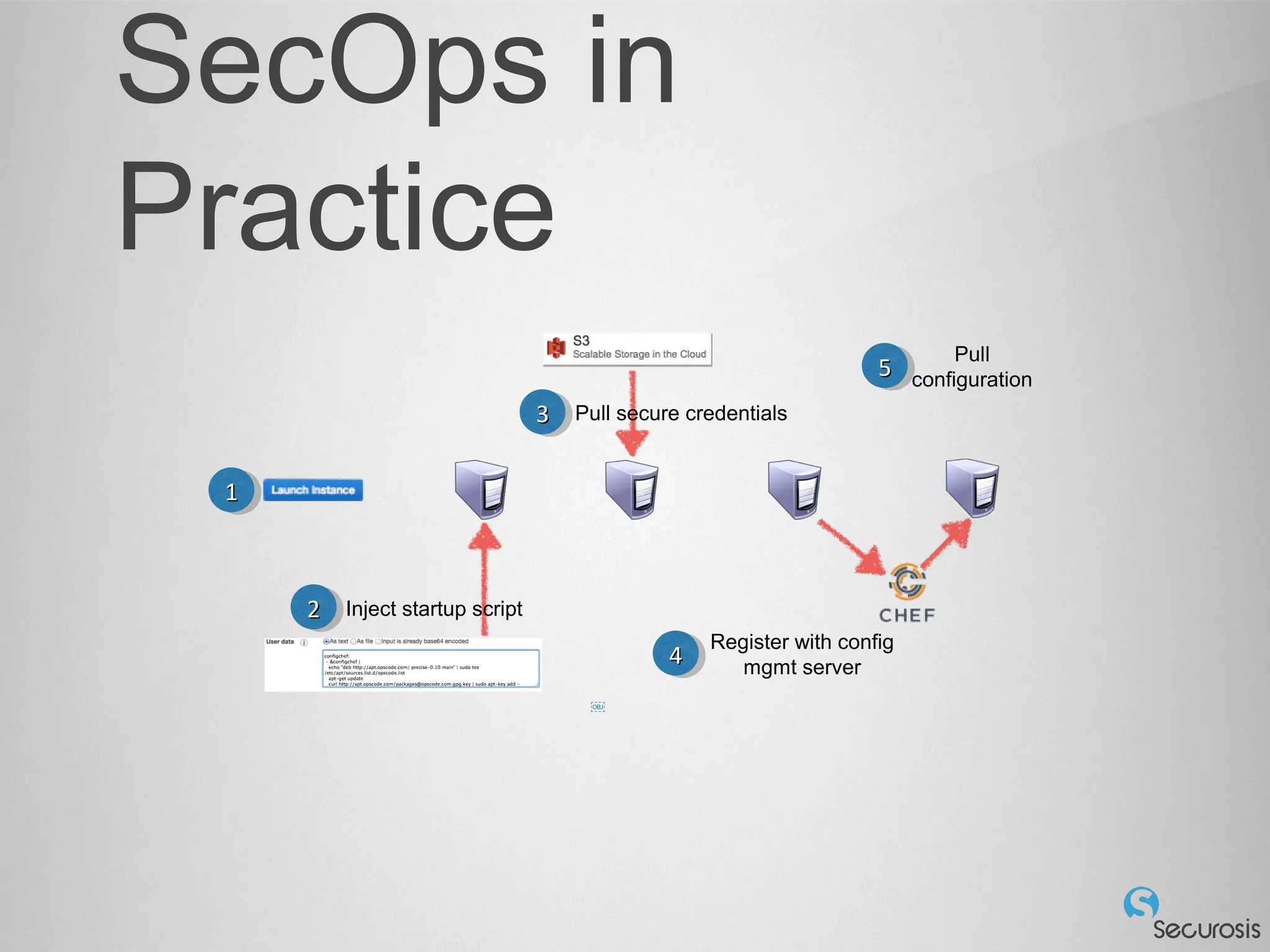
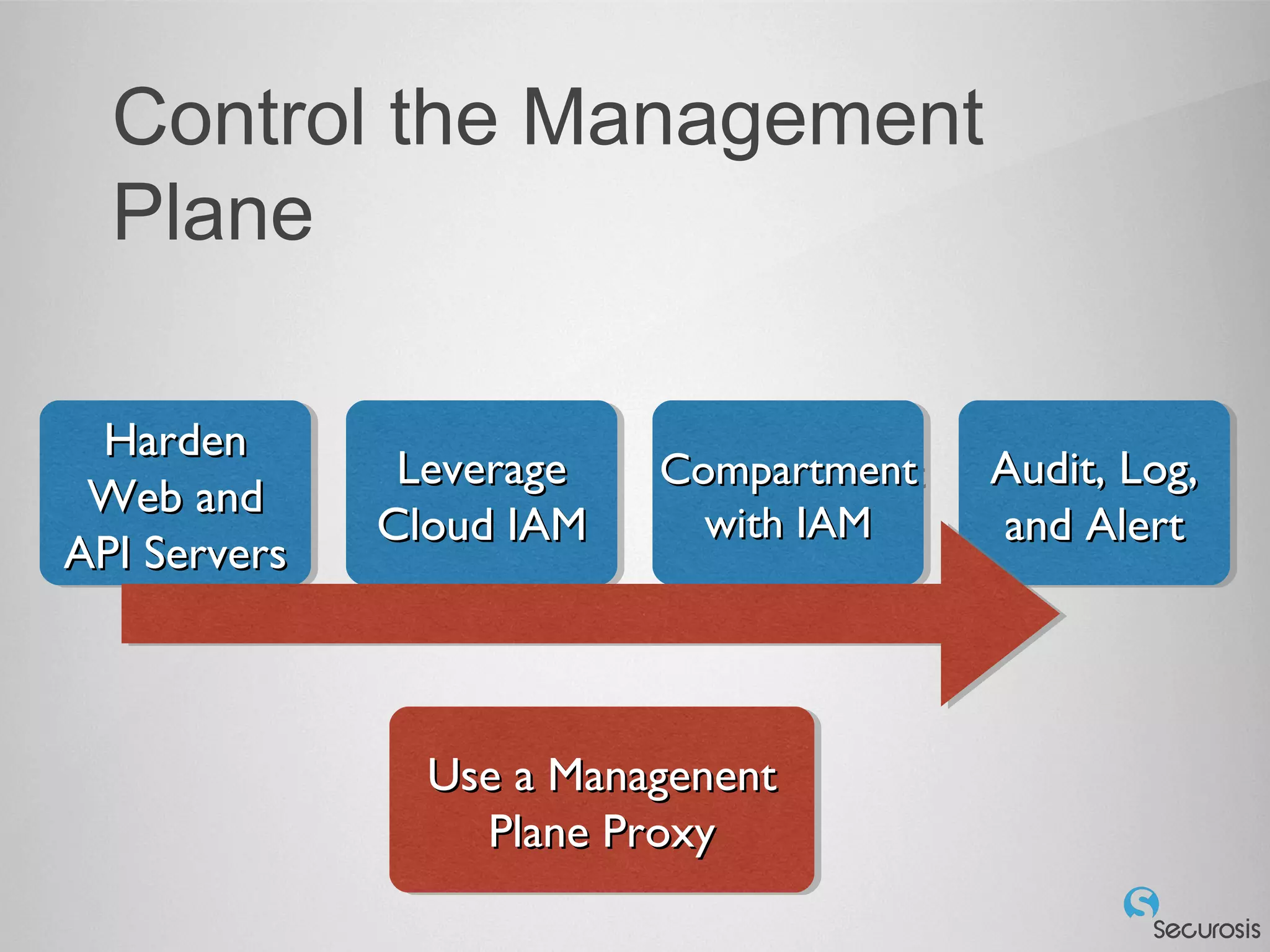
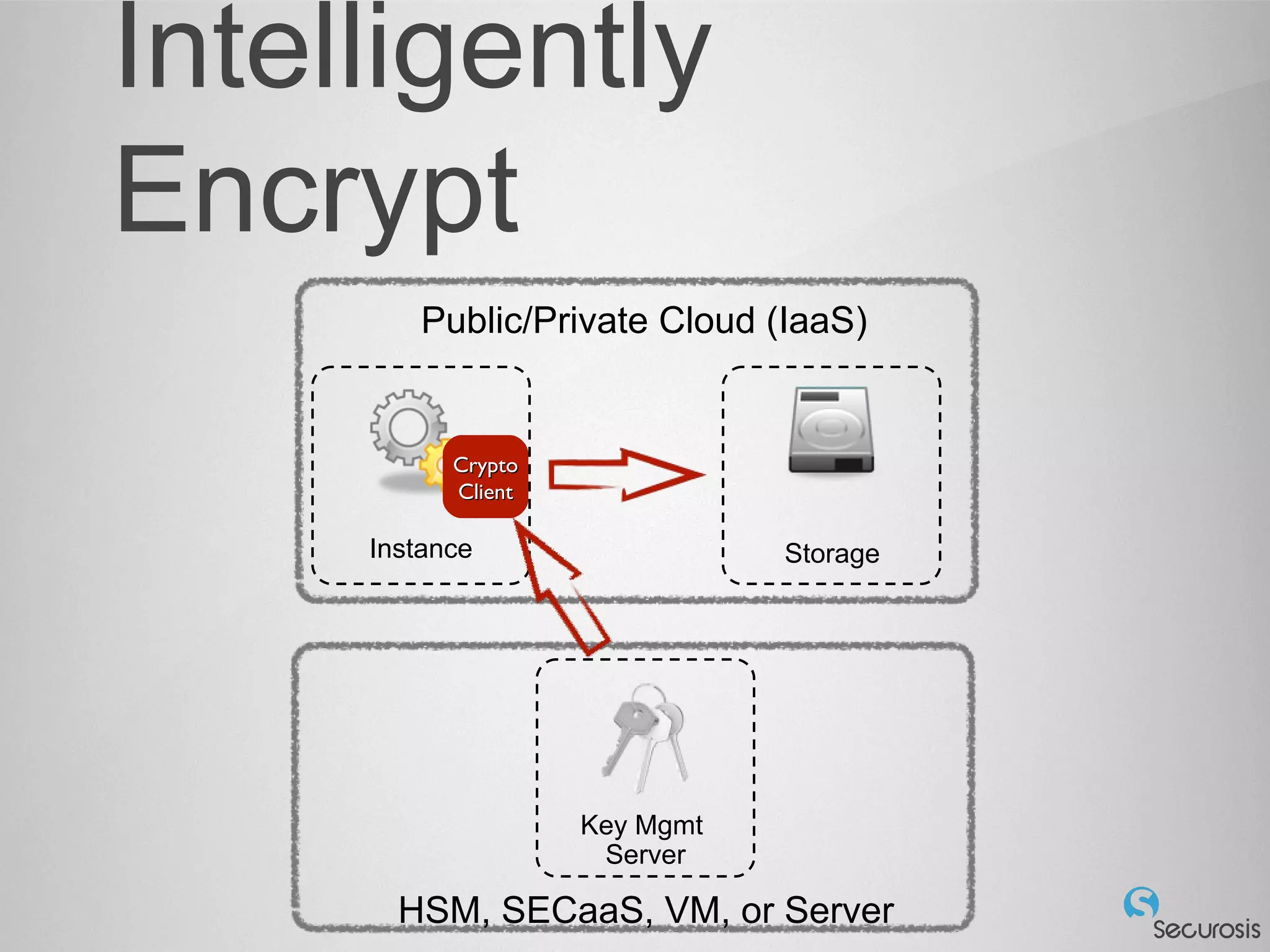
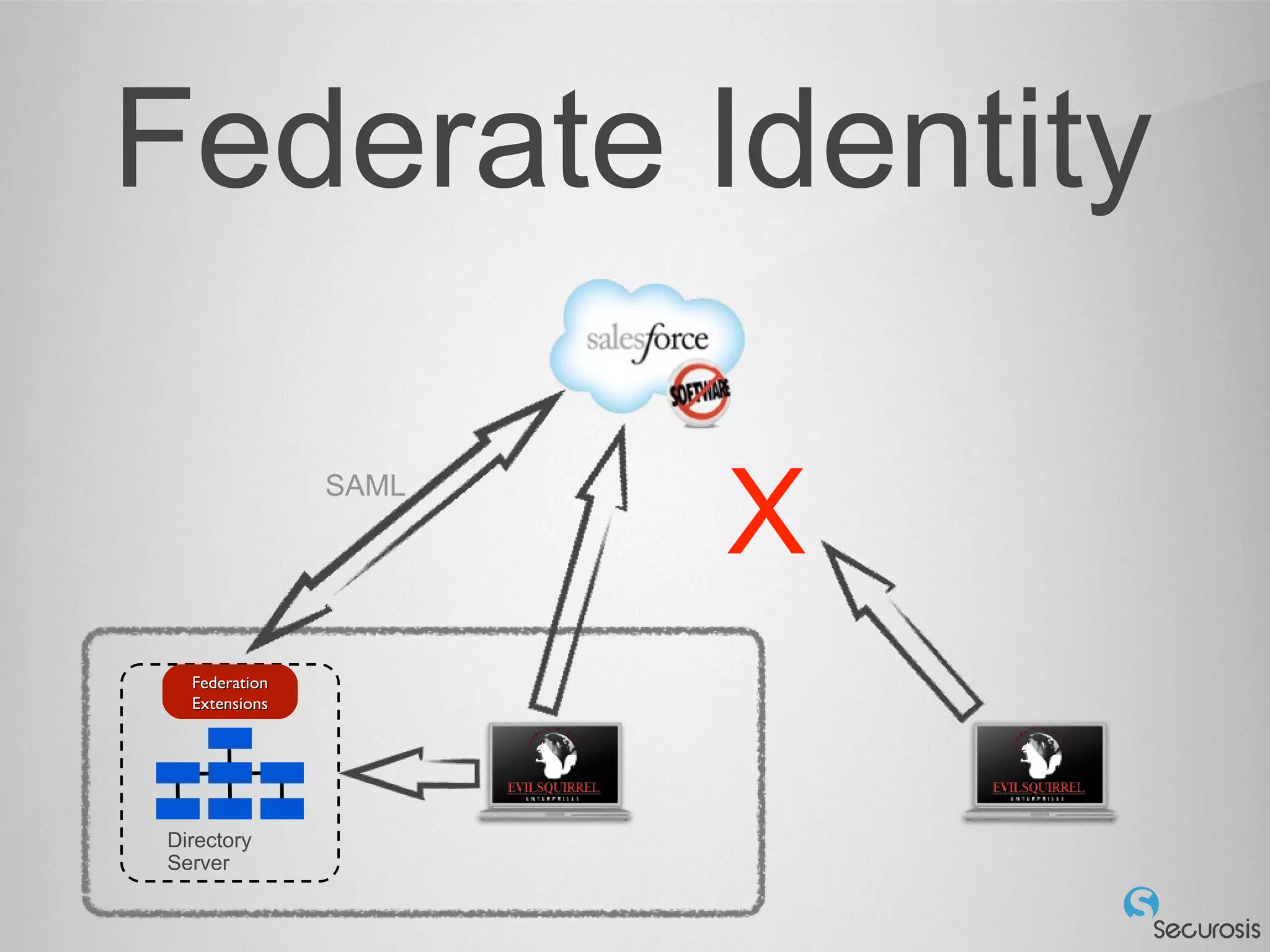
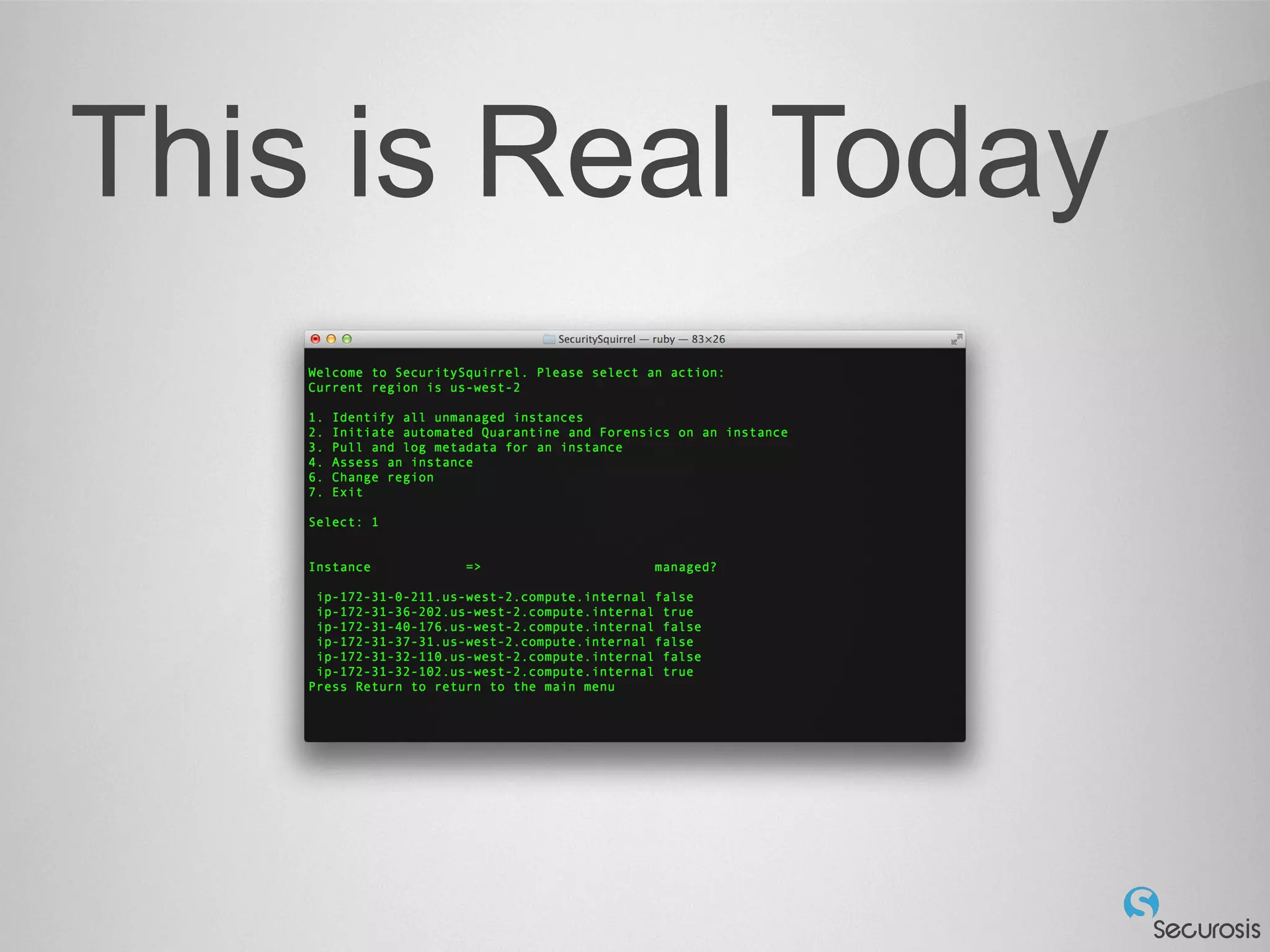
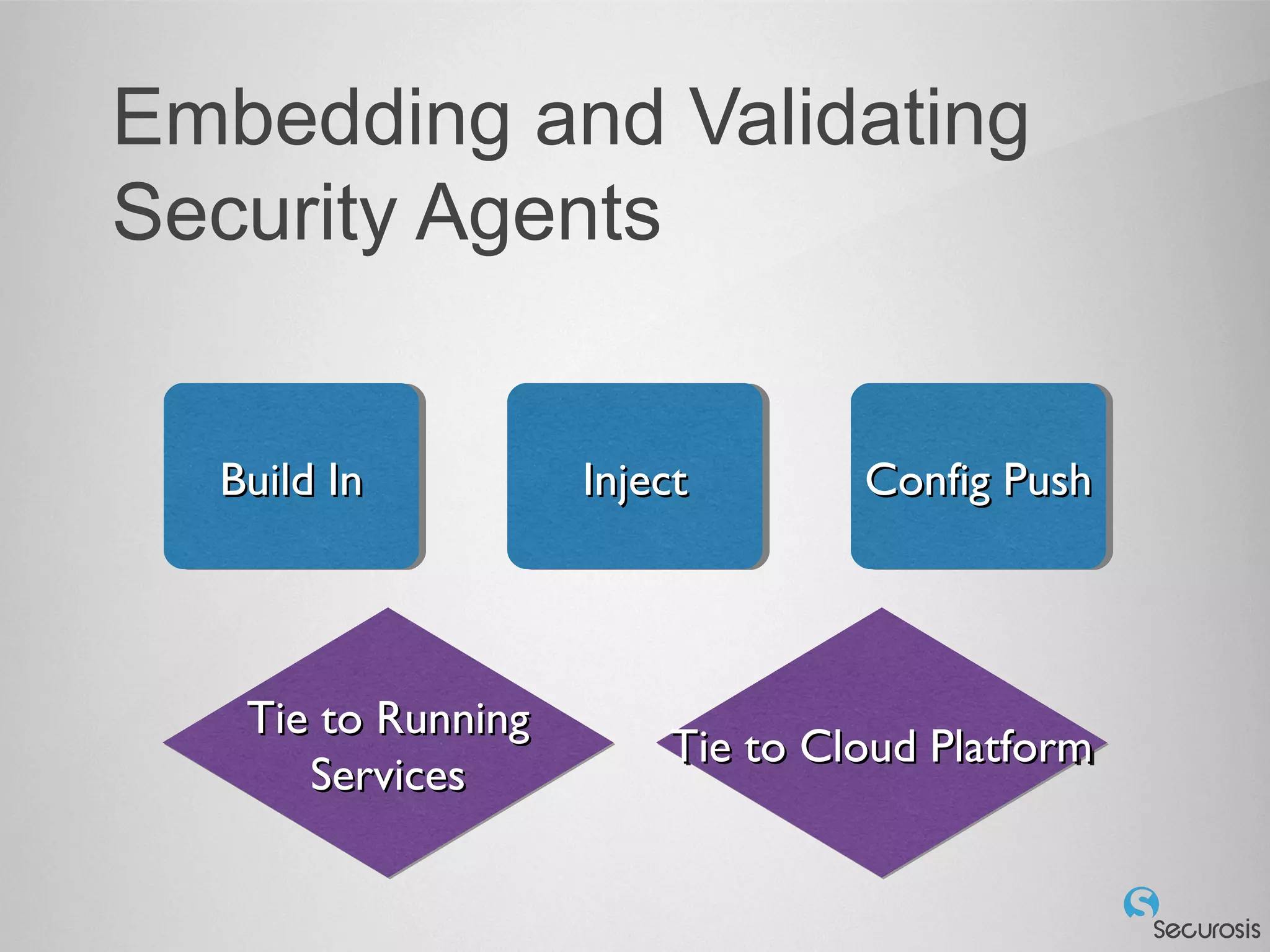
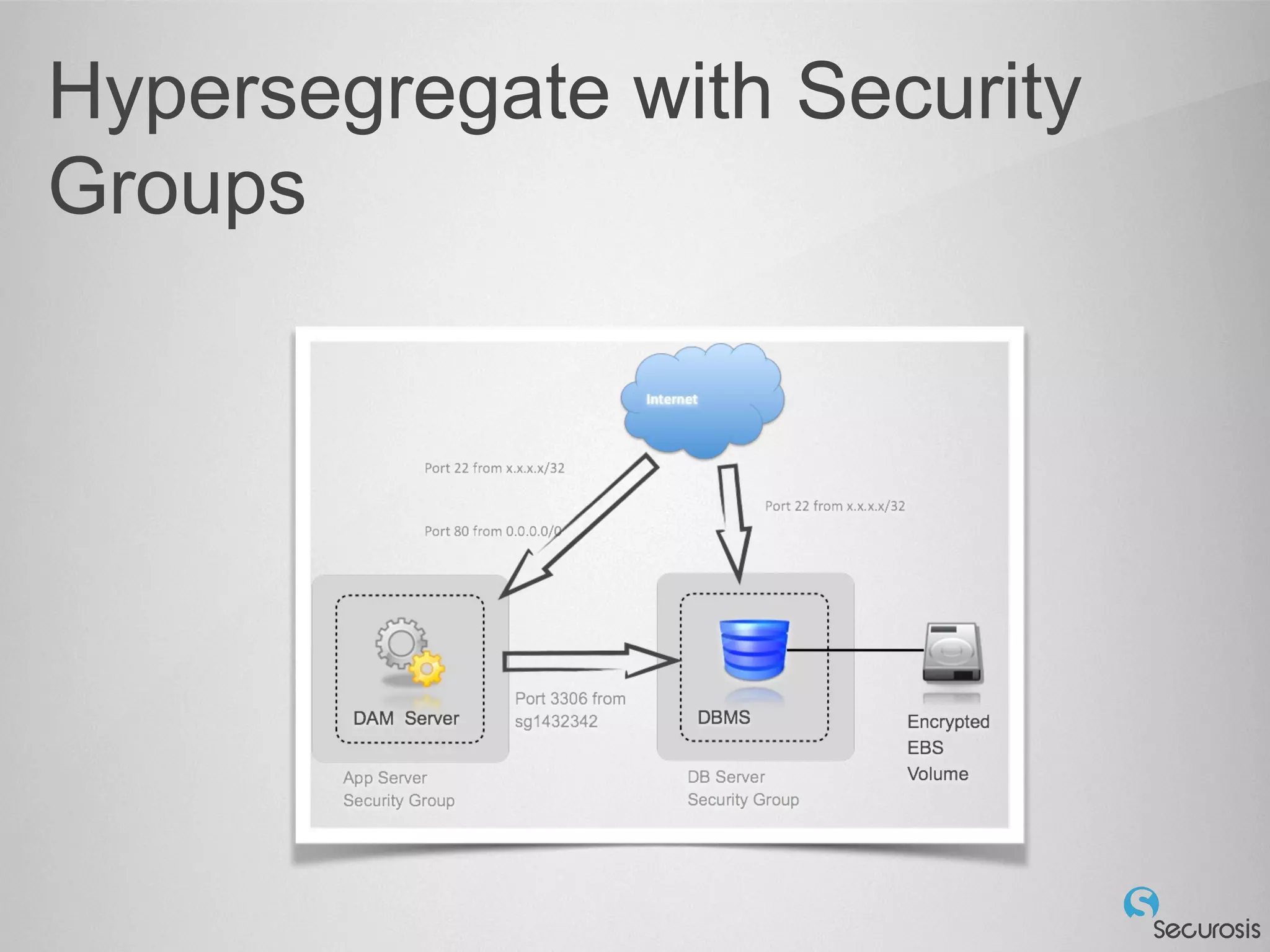
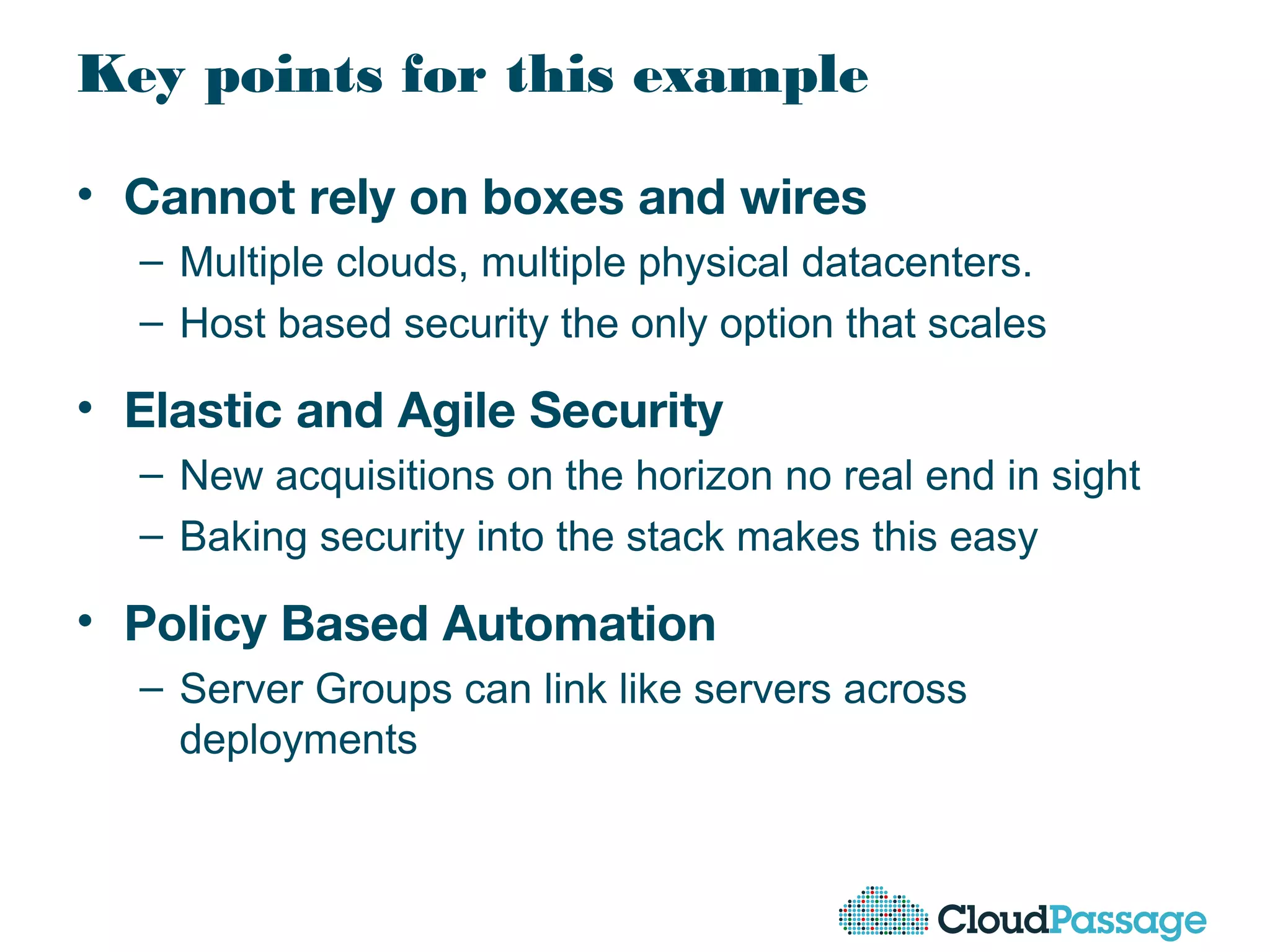
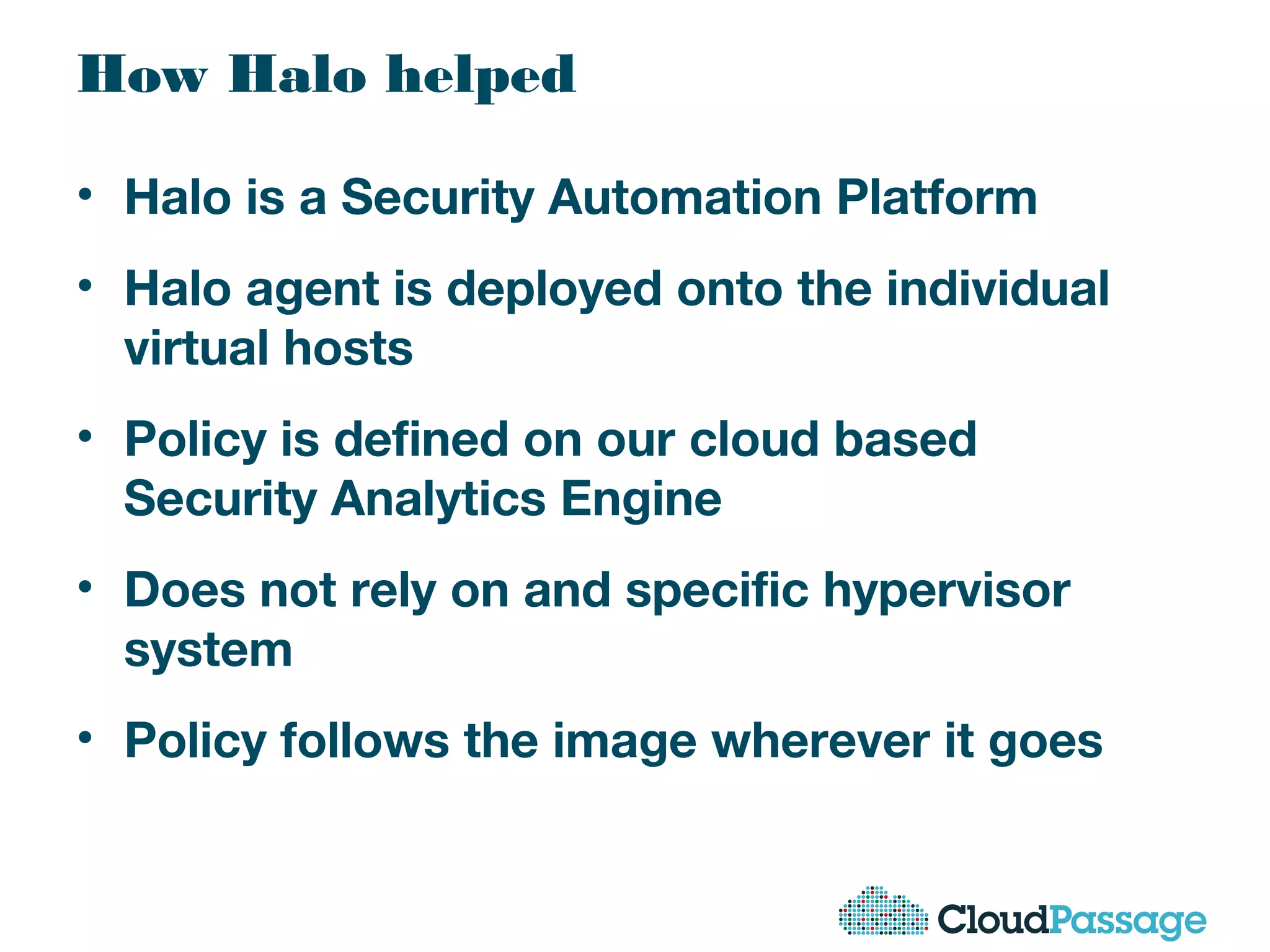
The document discusses essential security considerations for cloud computing, emphasizing the importance of adapting to its elastic and automated nature rather than relying on traditional physical controls. It advocates for policy-based automation, integration with DevOps, and the use of host-based security solutions to manage diverse environments effectively. Additionally, it highlights security automation tools, like Halo, which allow policies to follow images across different deployments.