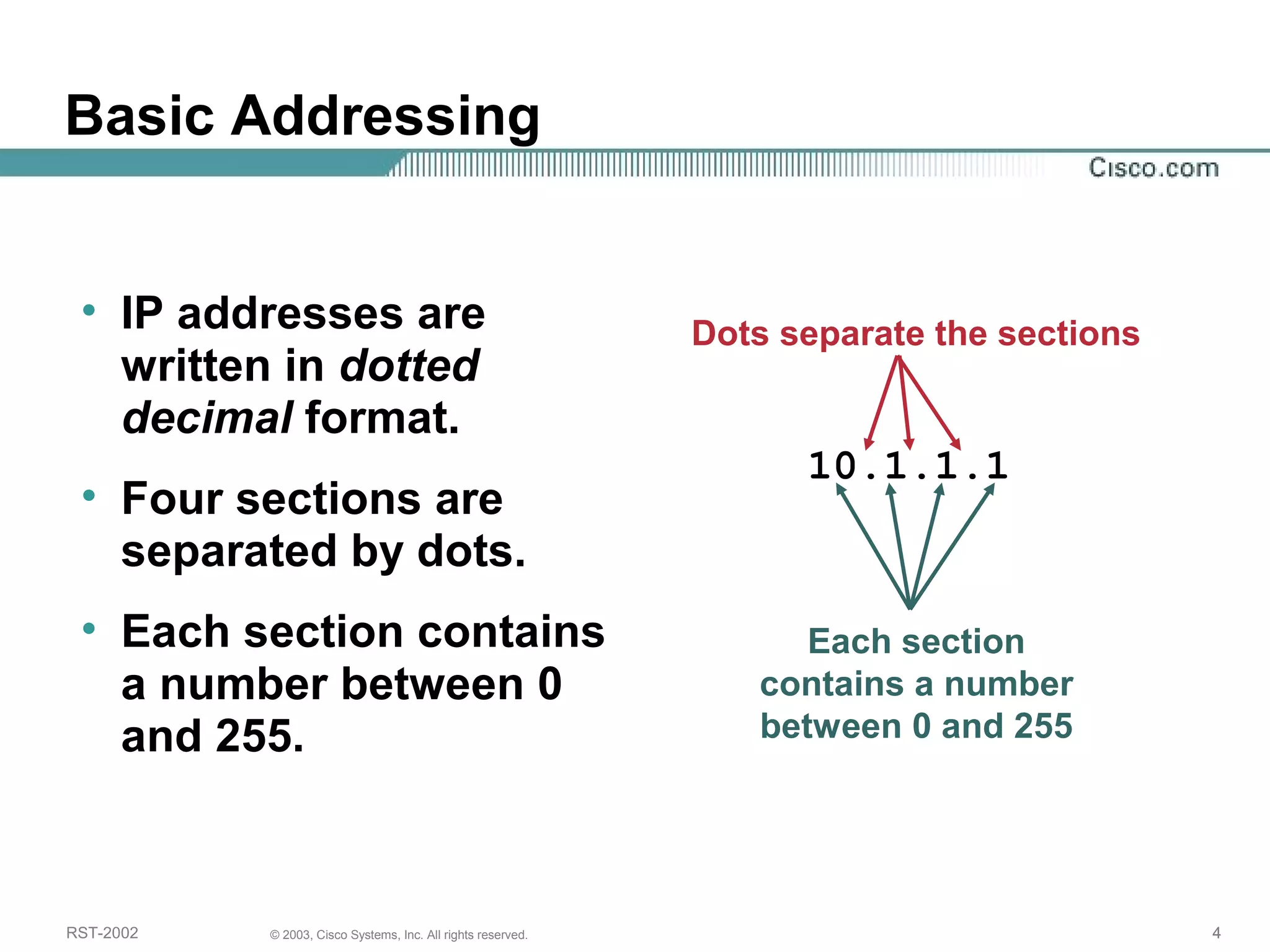
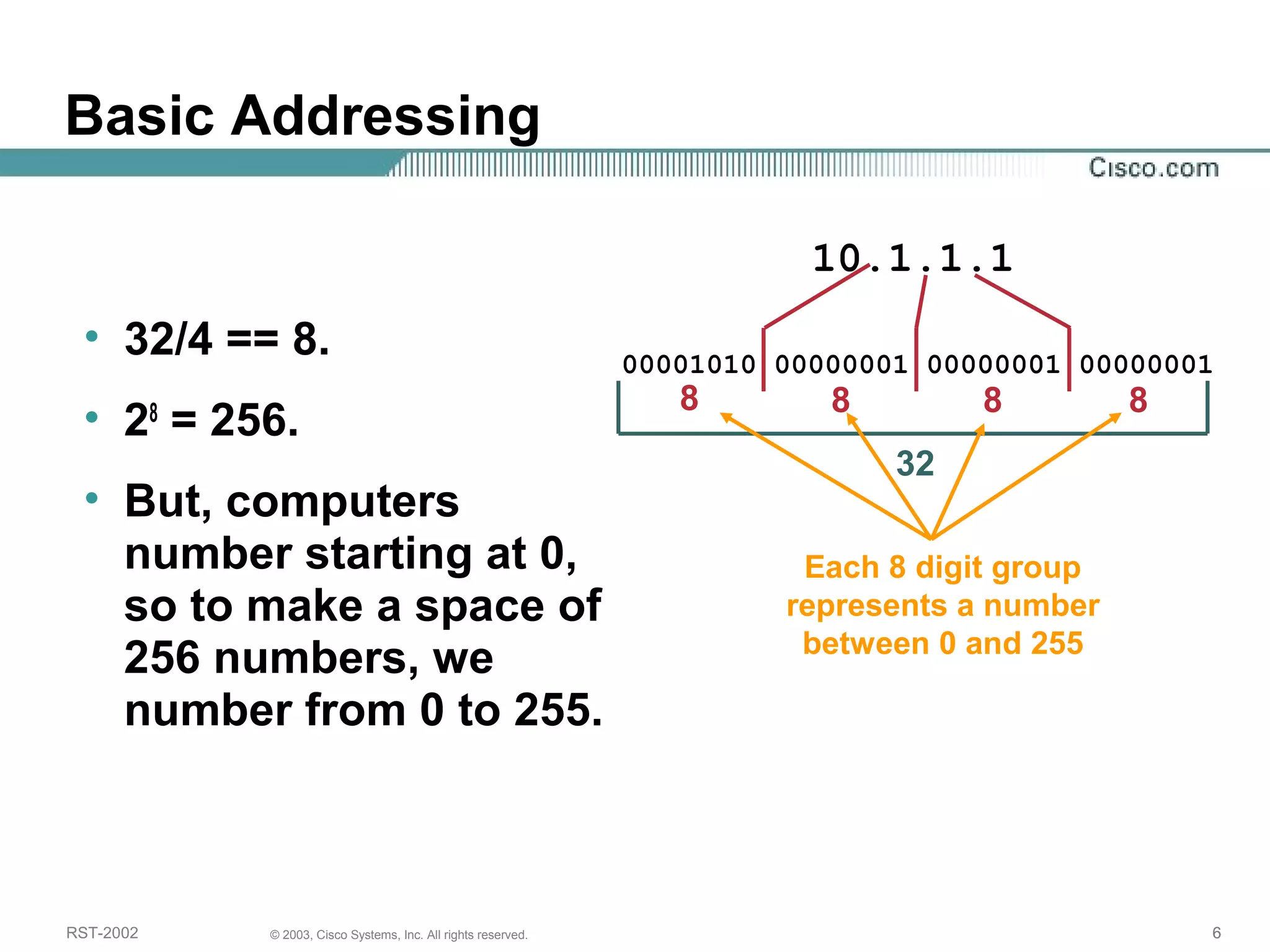
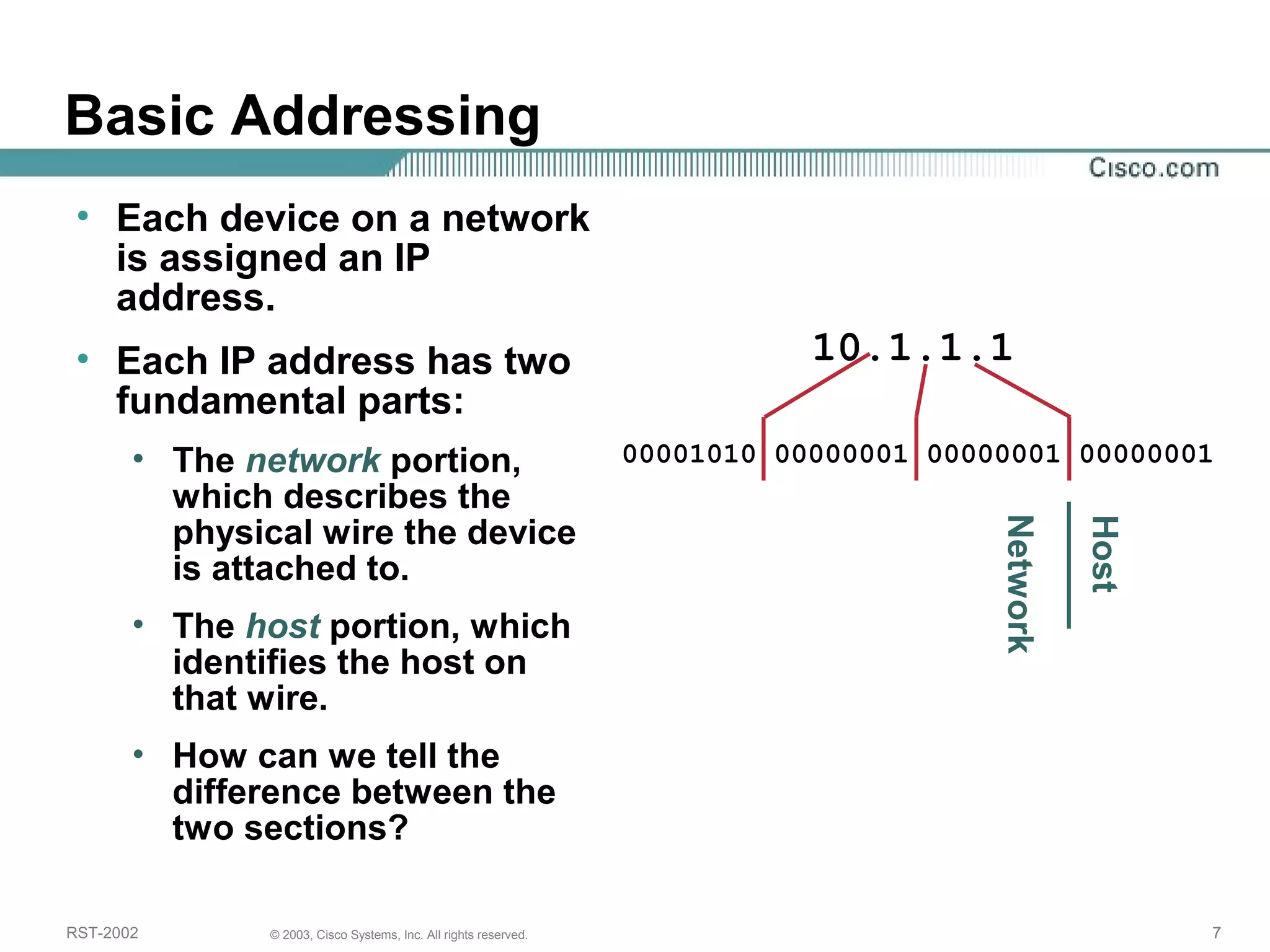
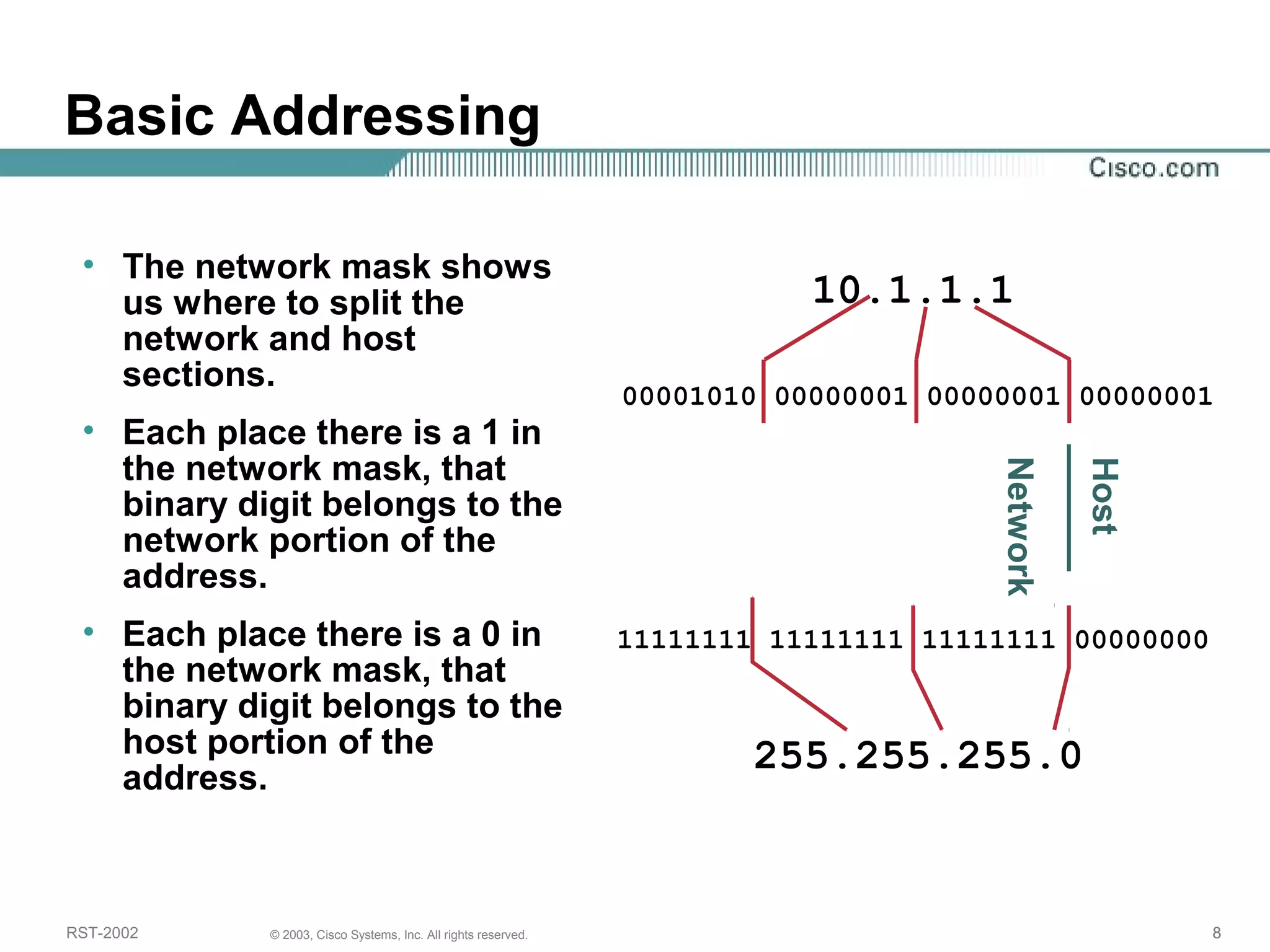
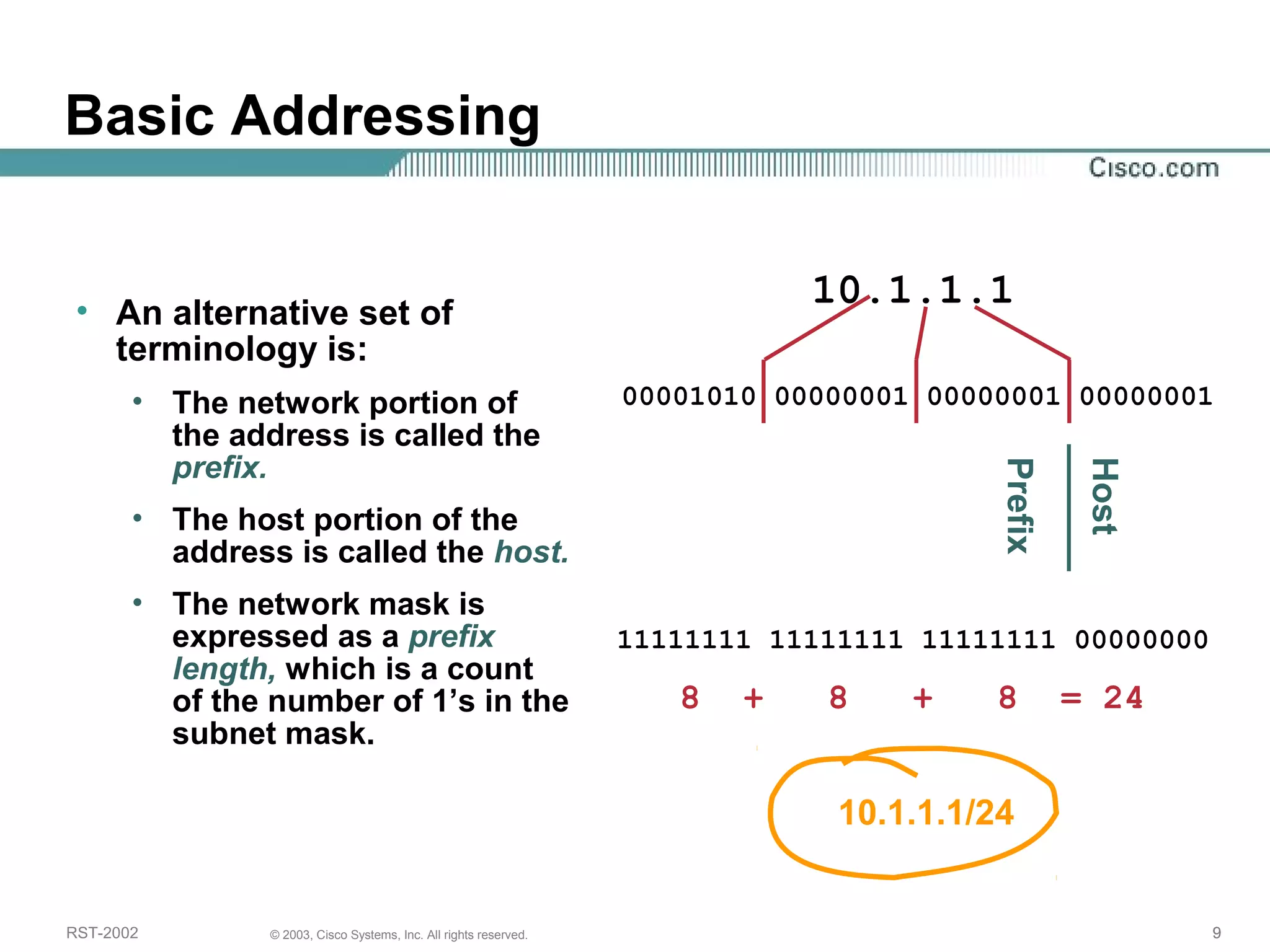
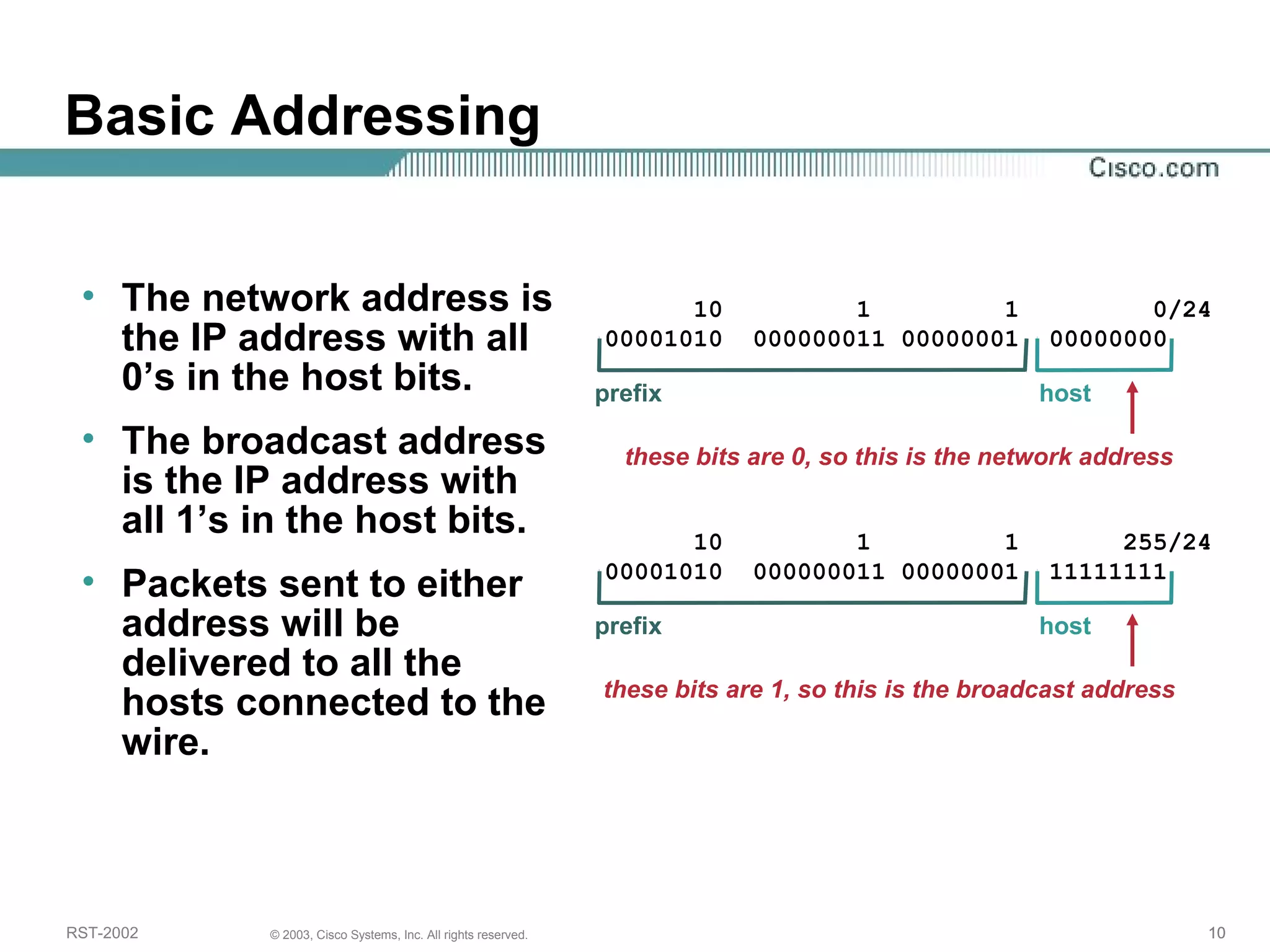
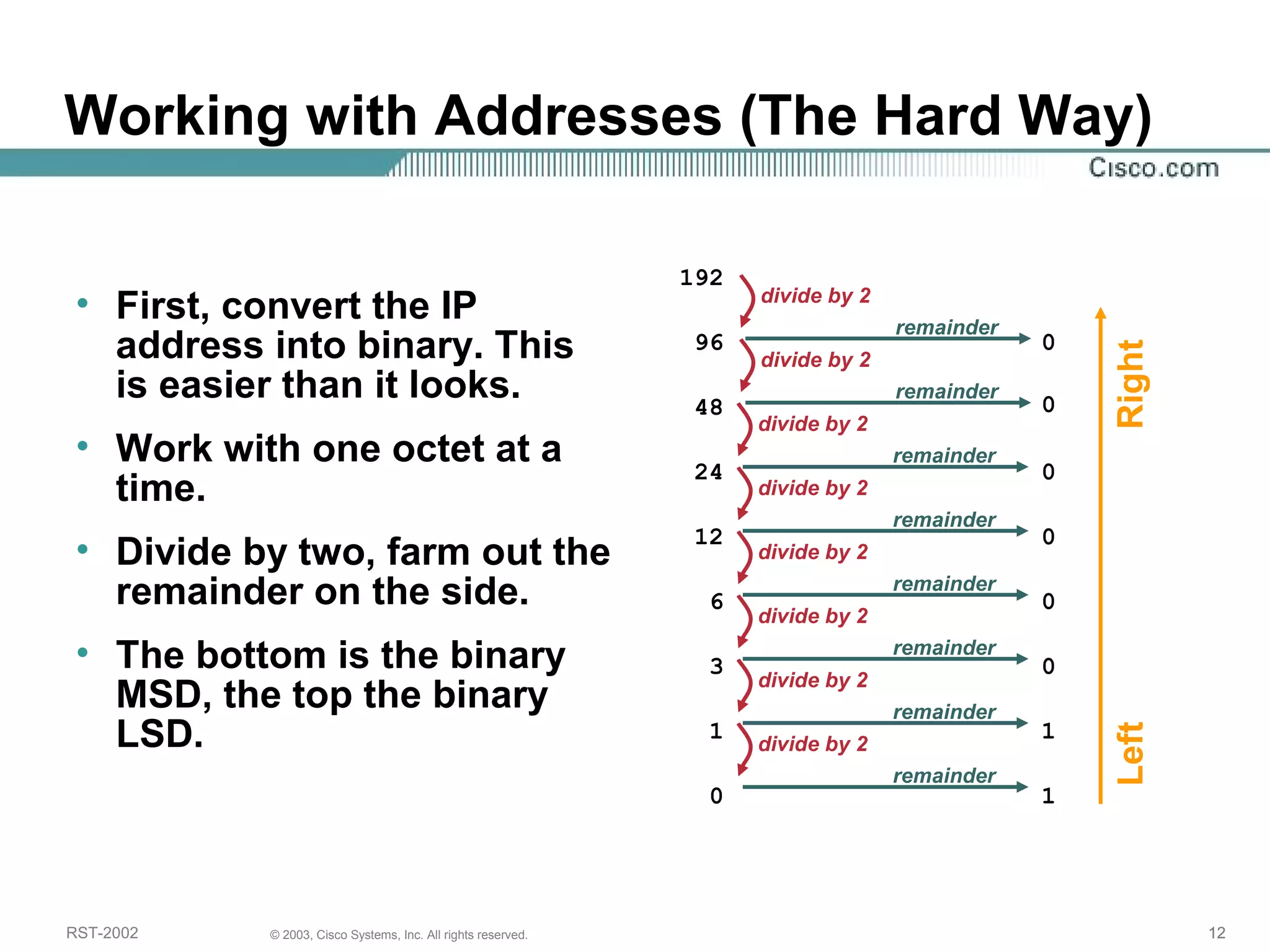
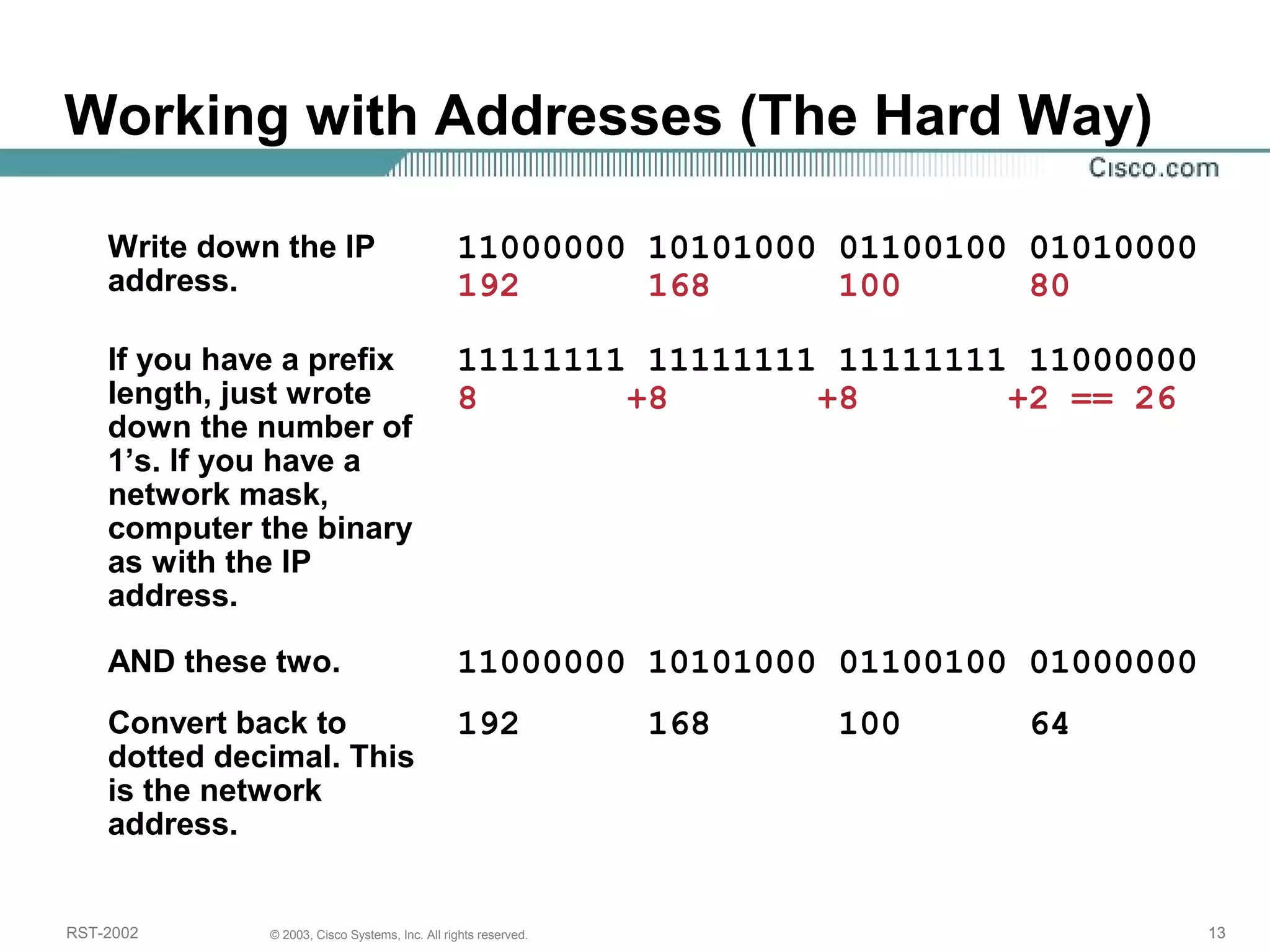
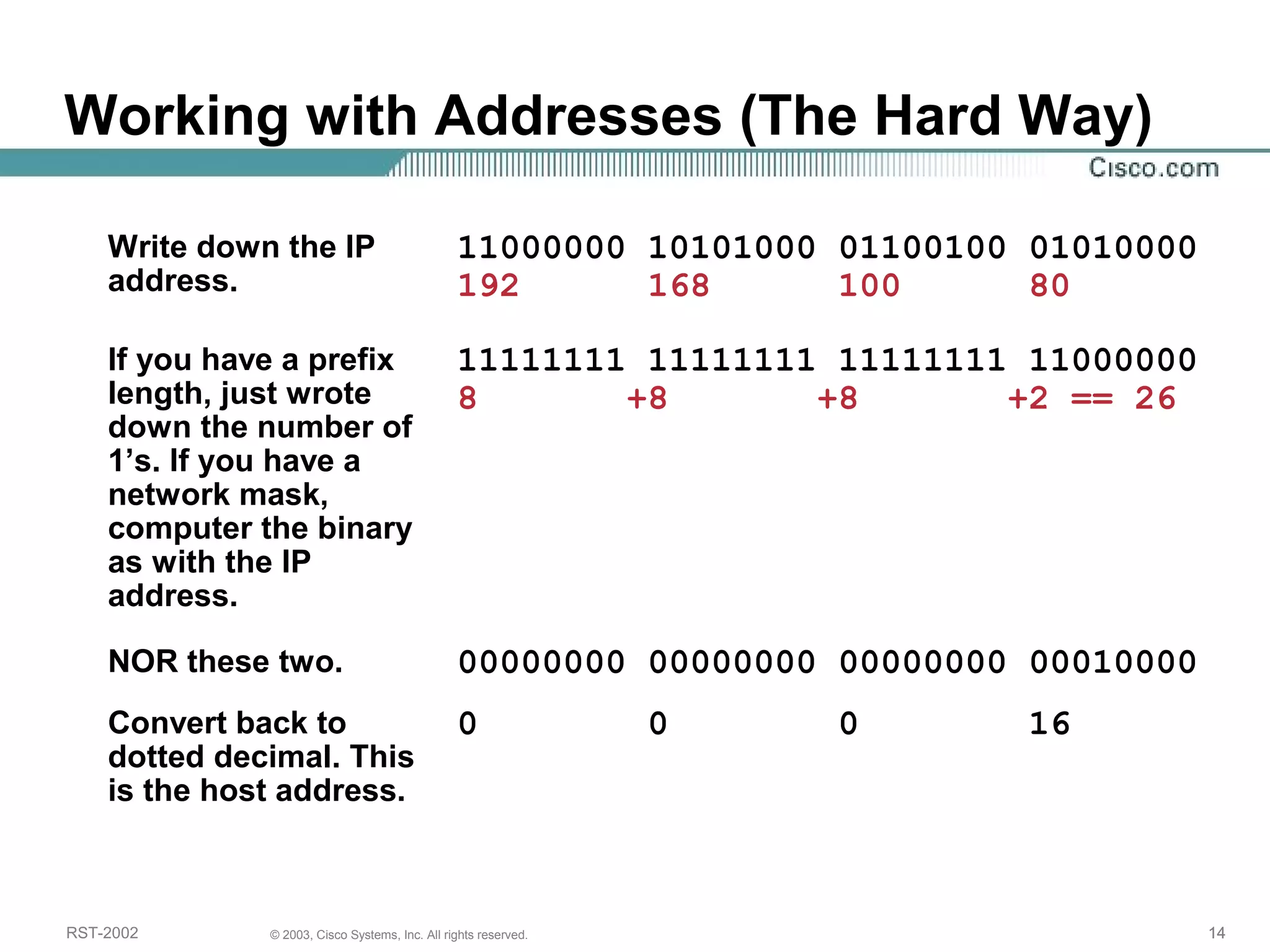
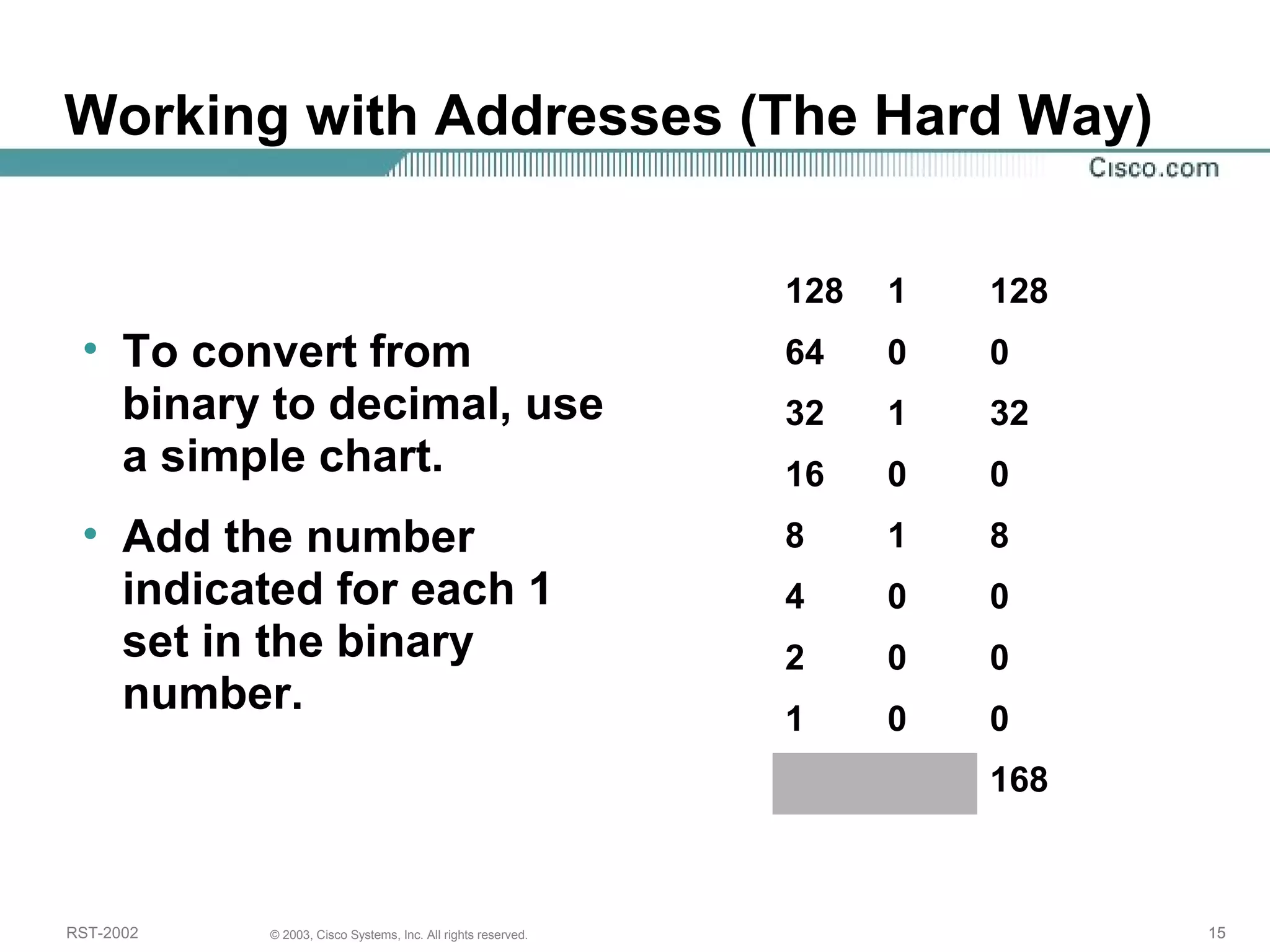
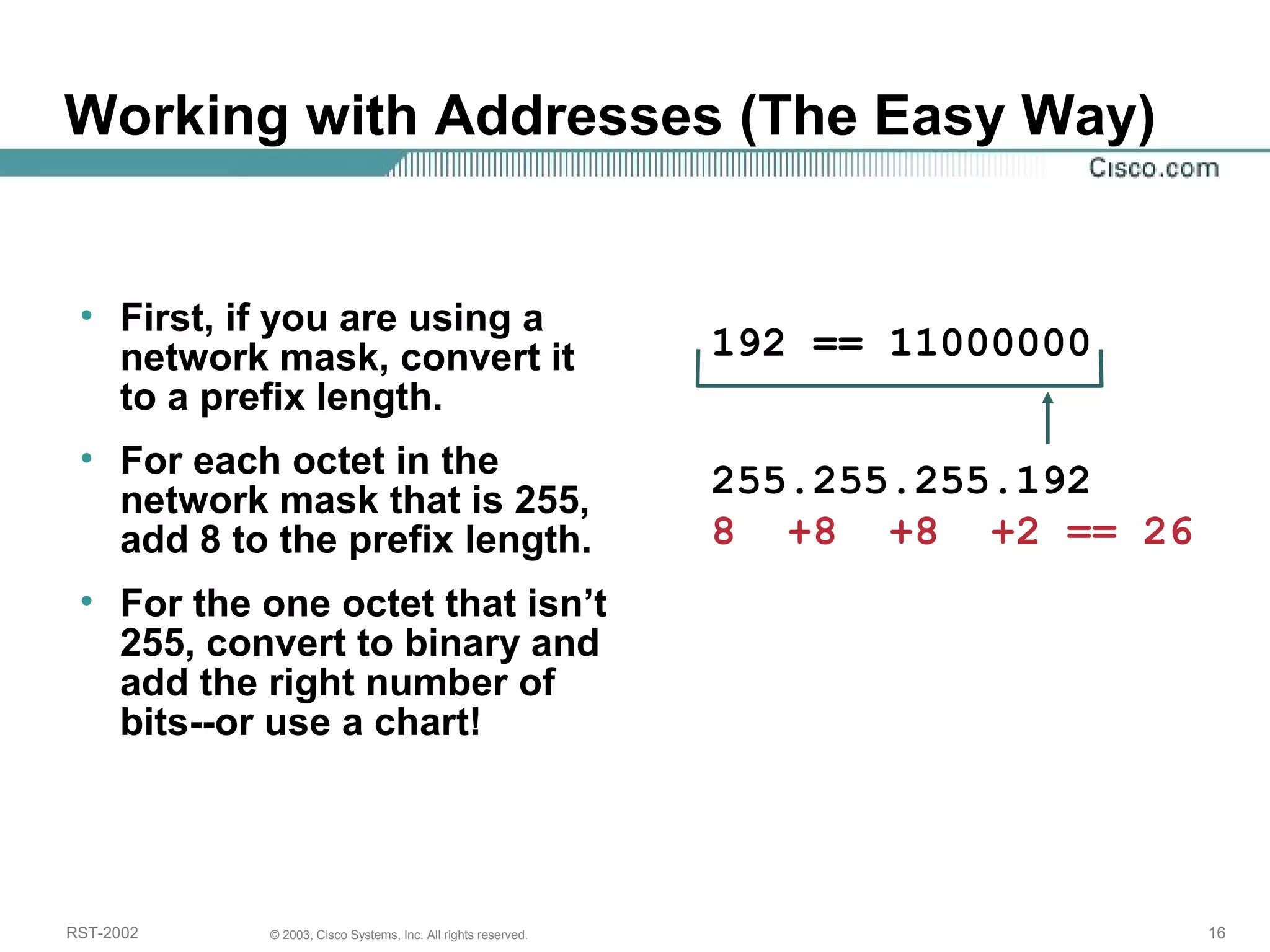
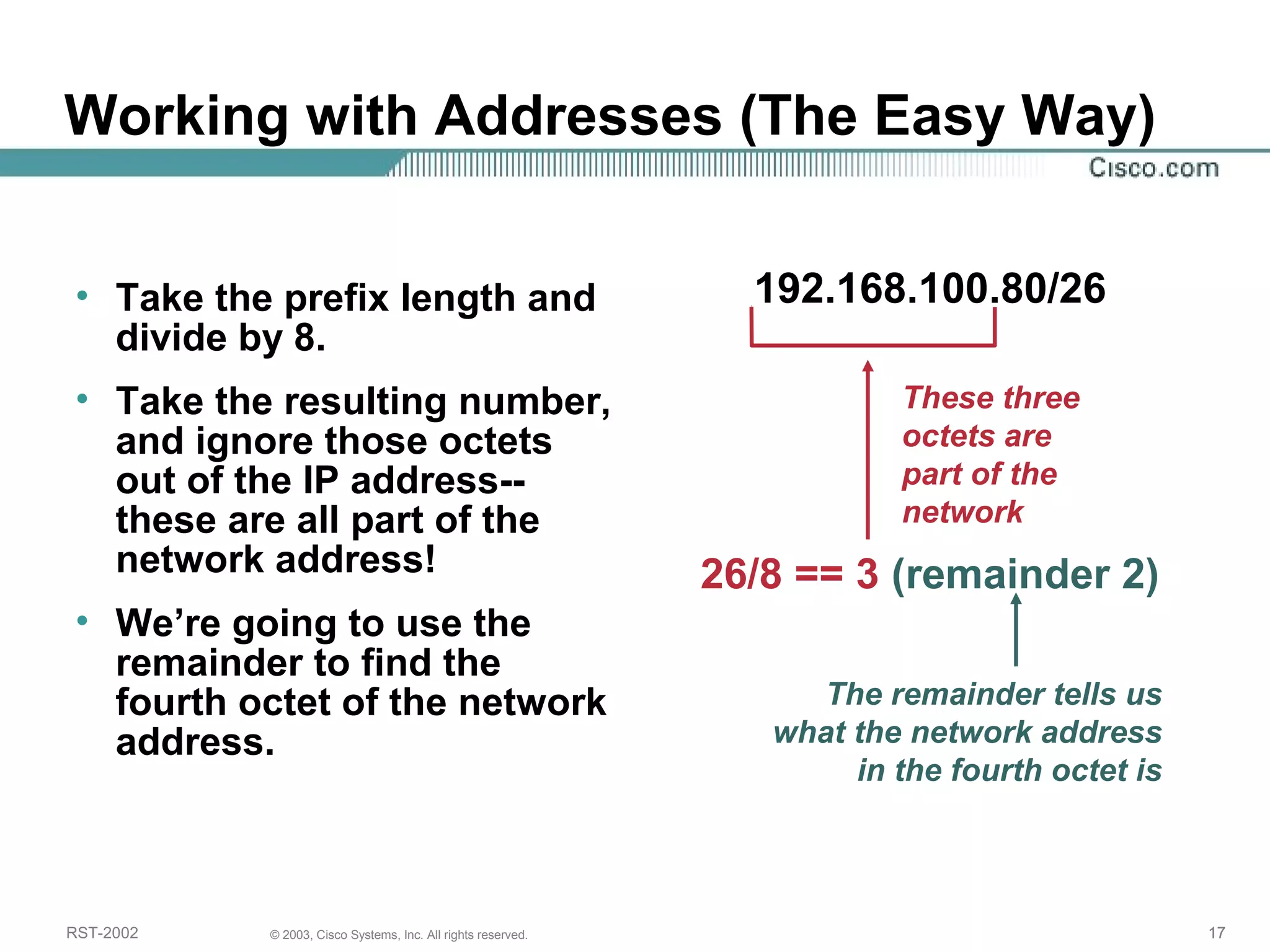
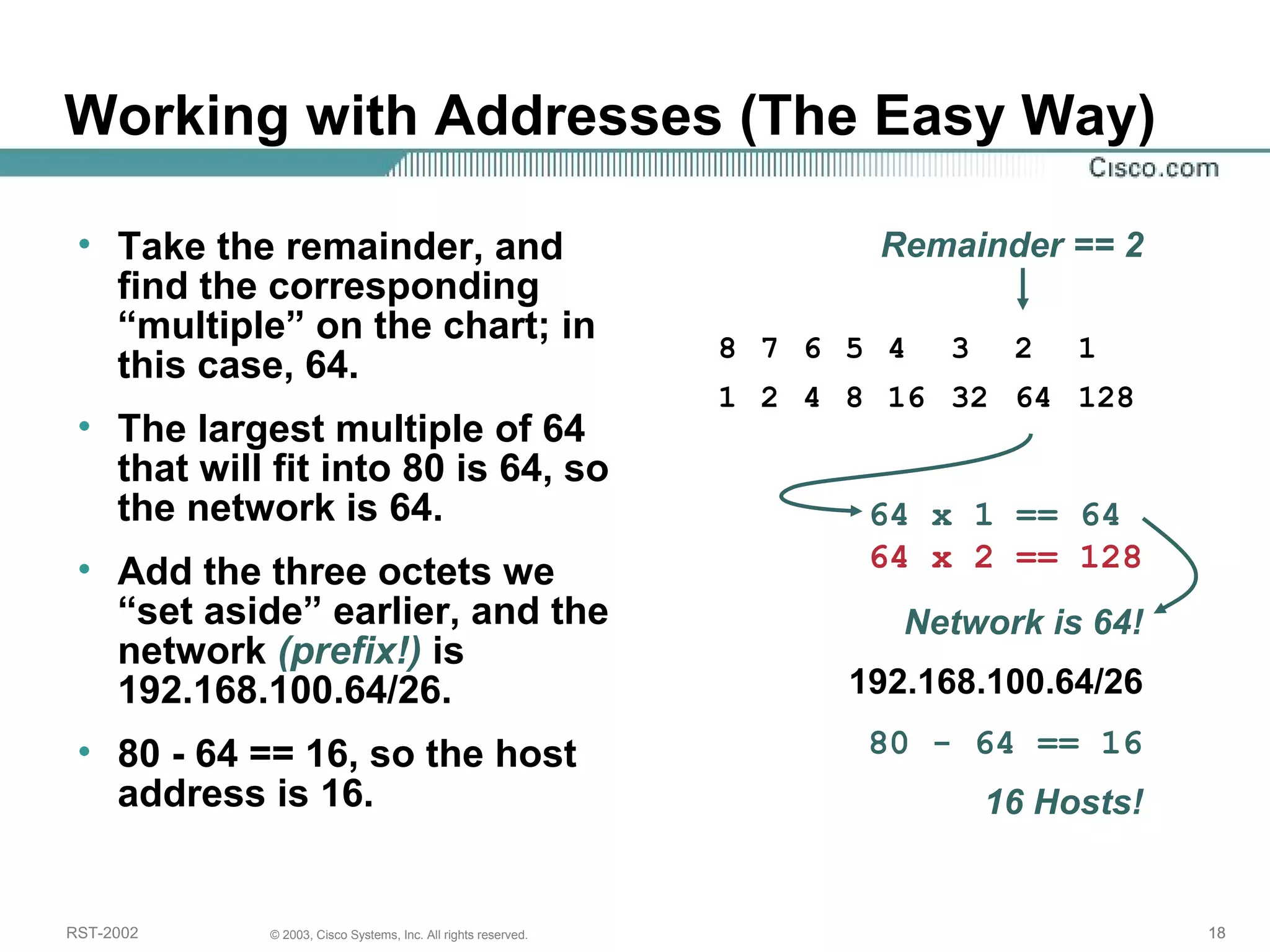
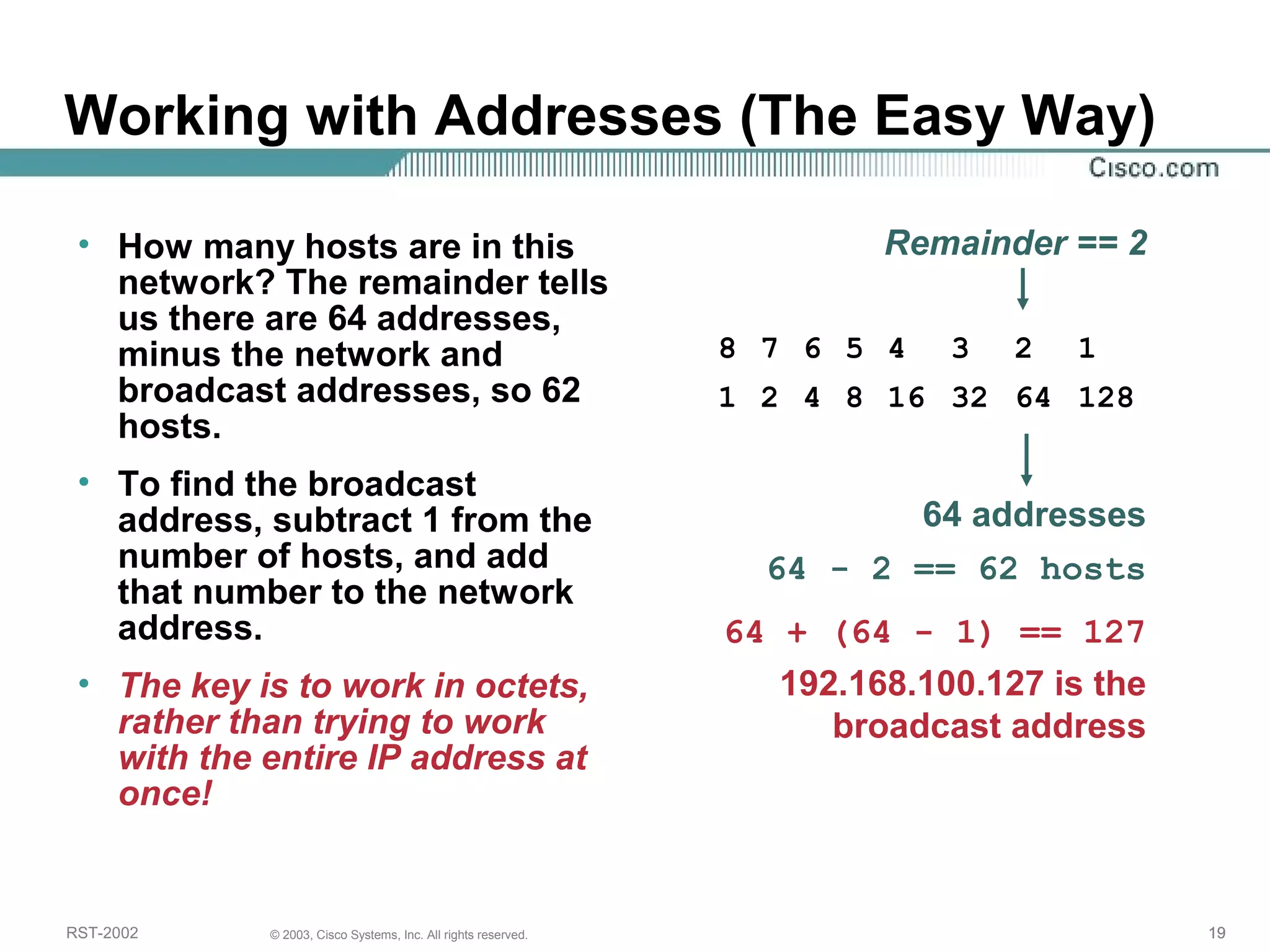
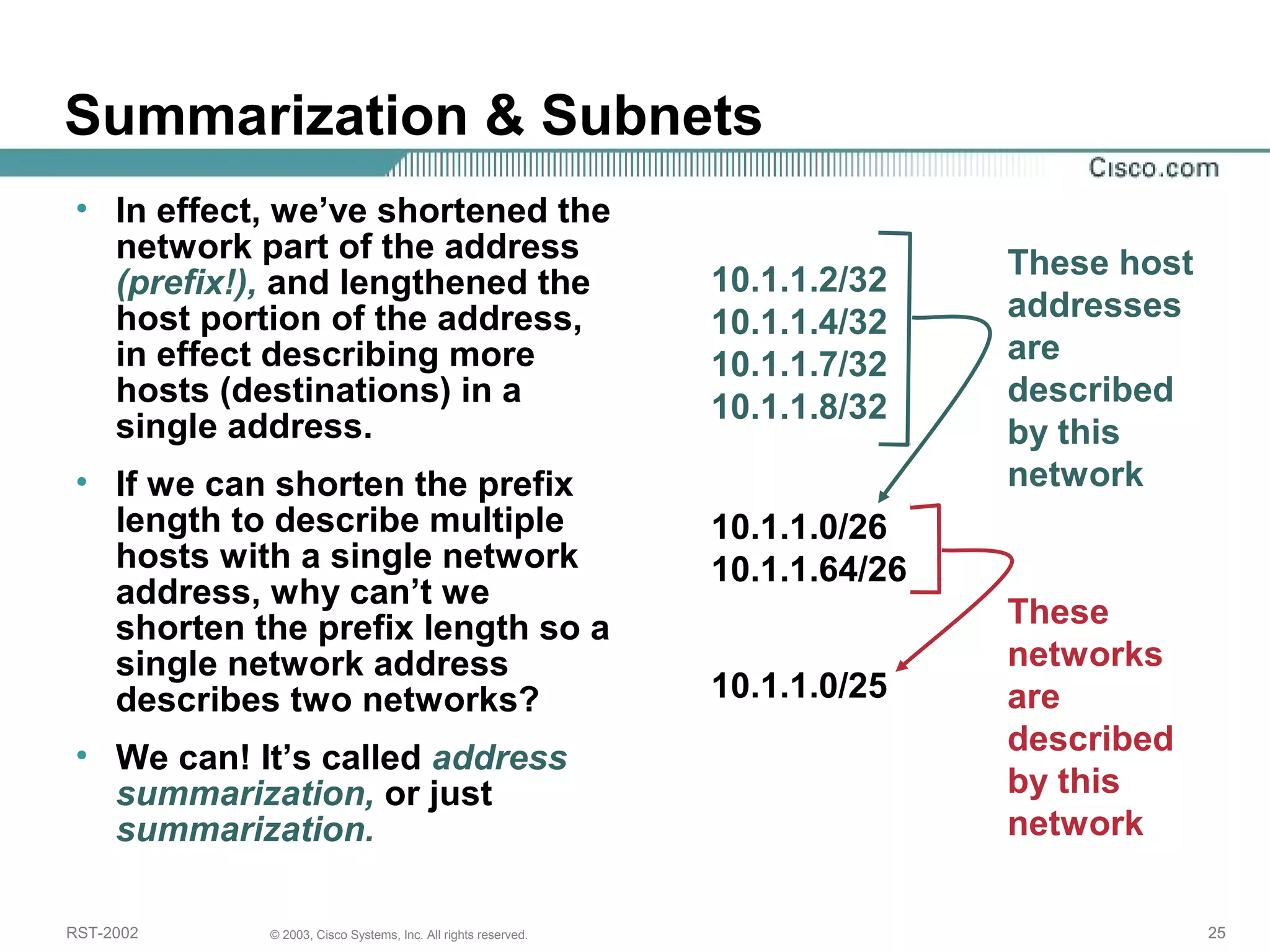
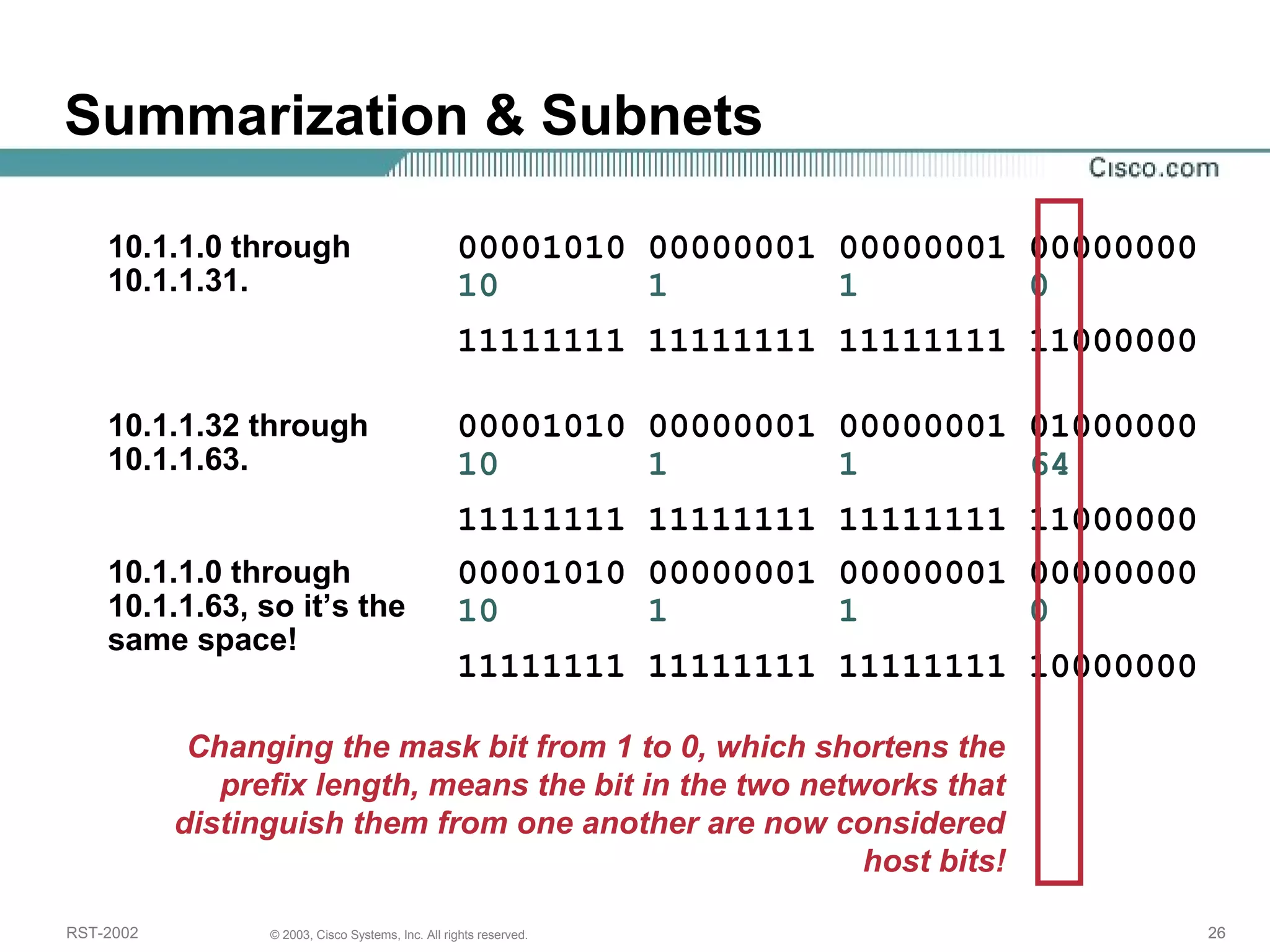
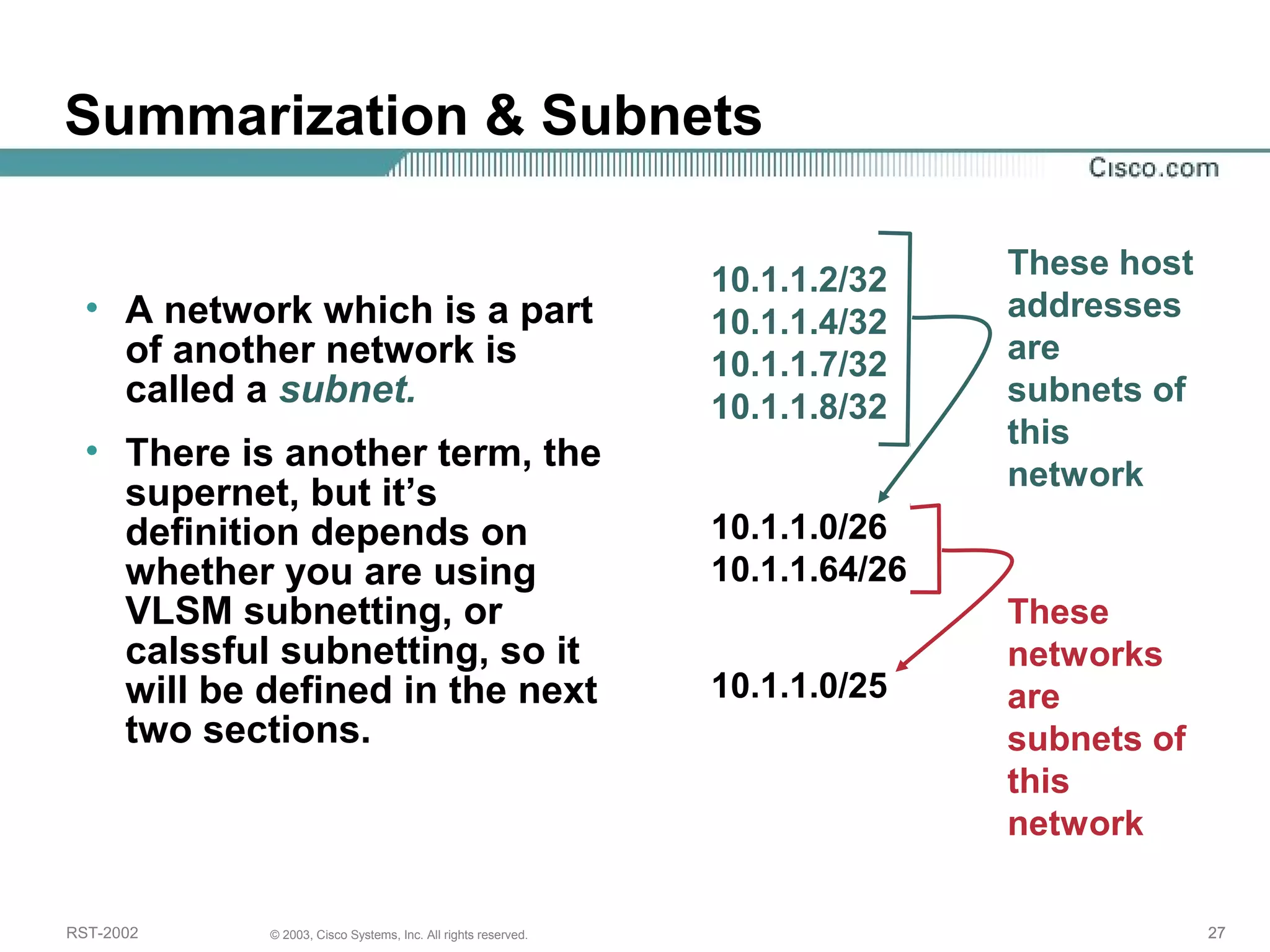
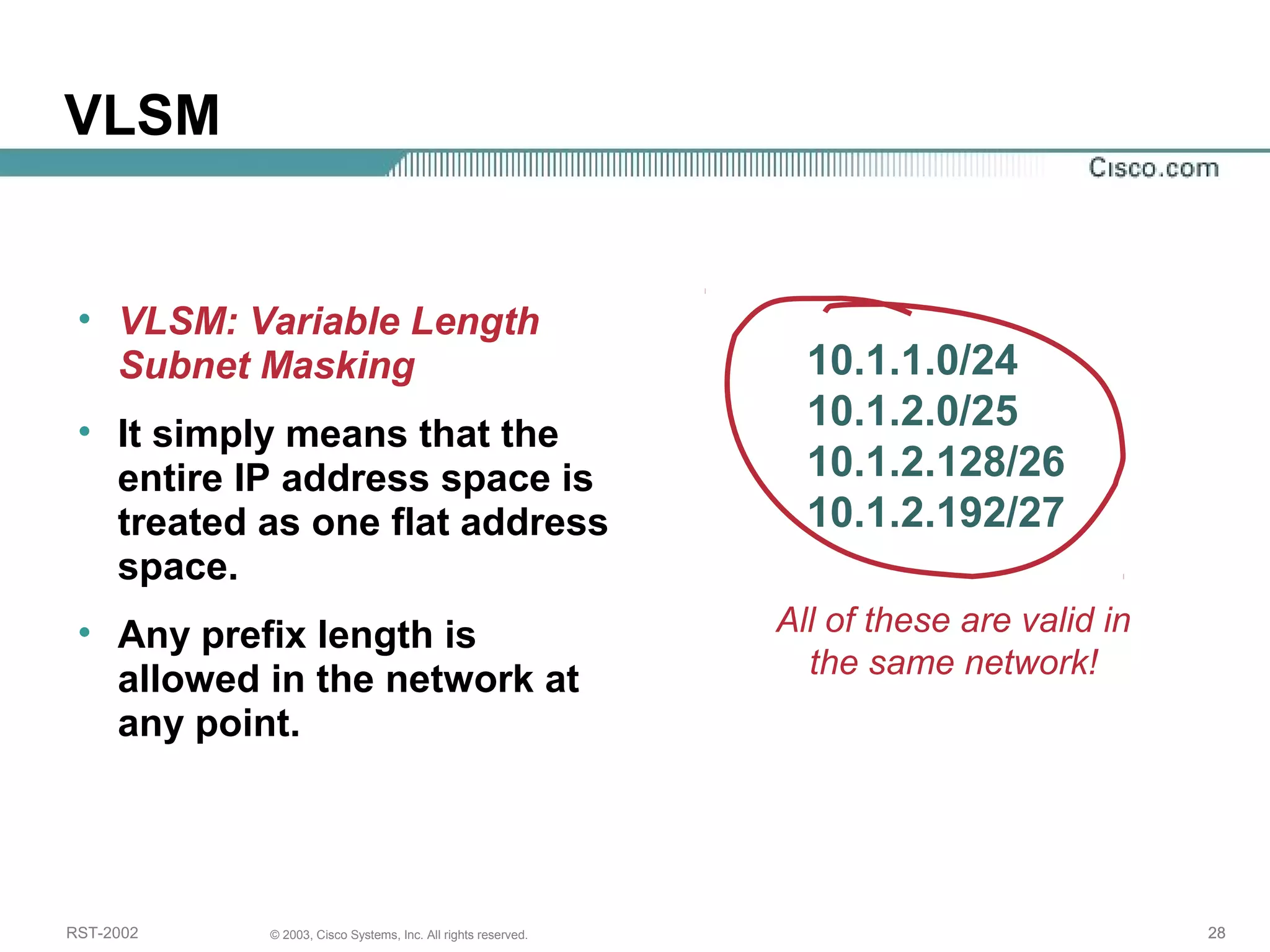
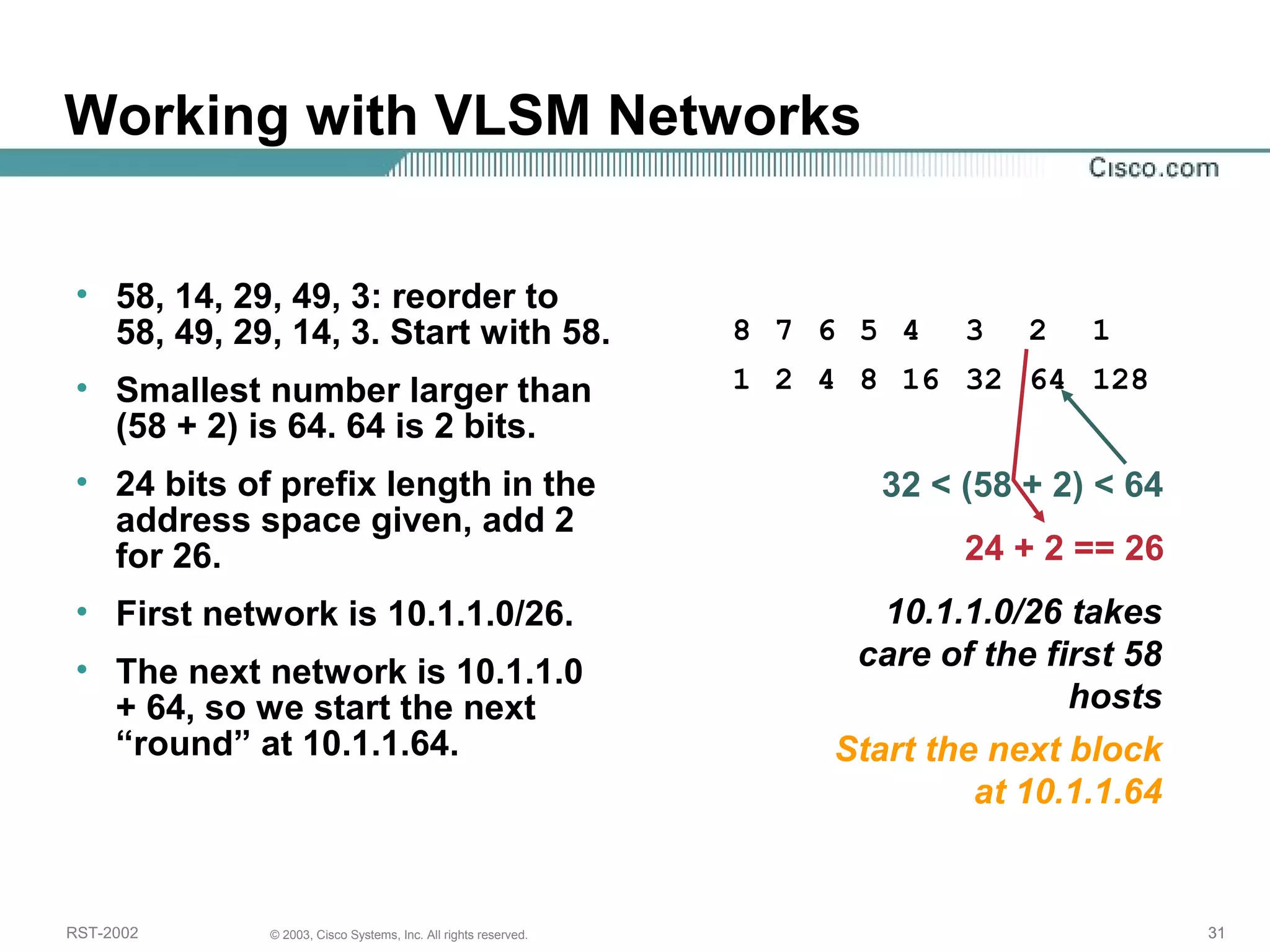
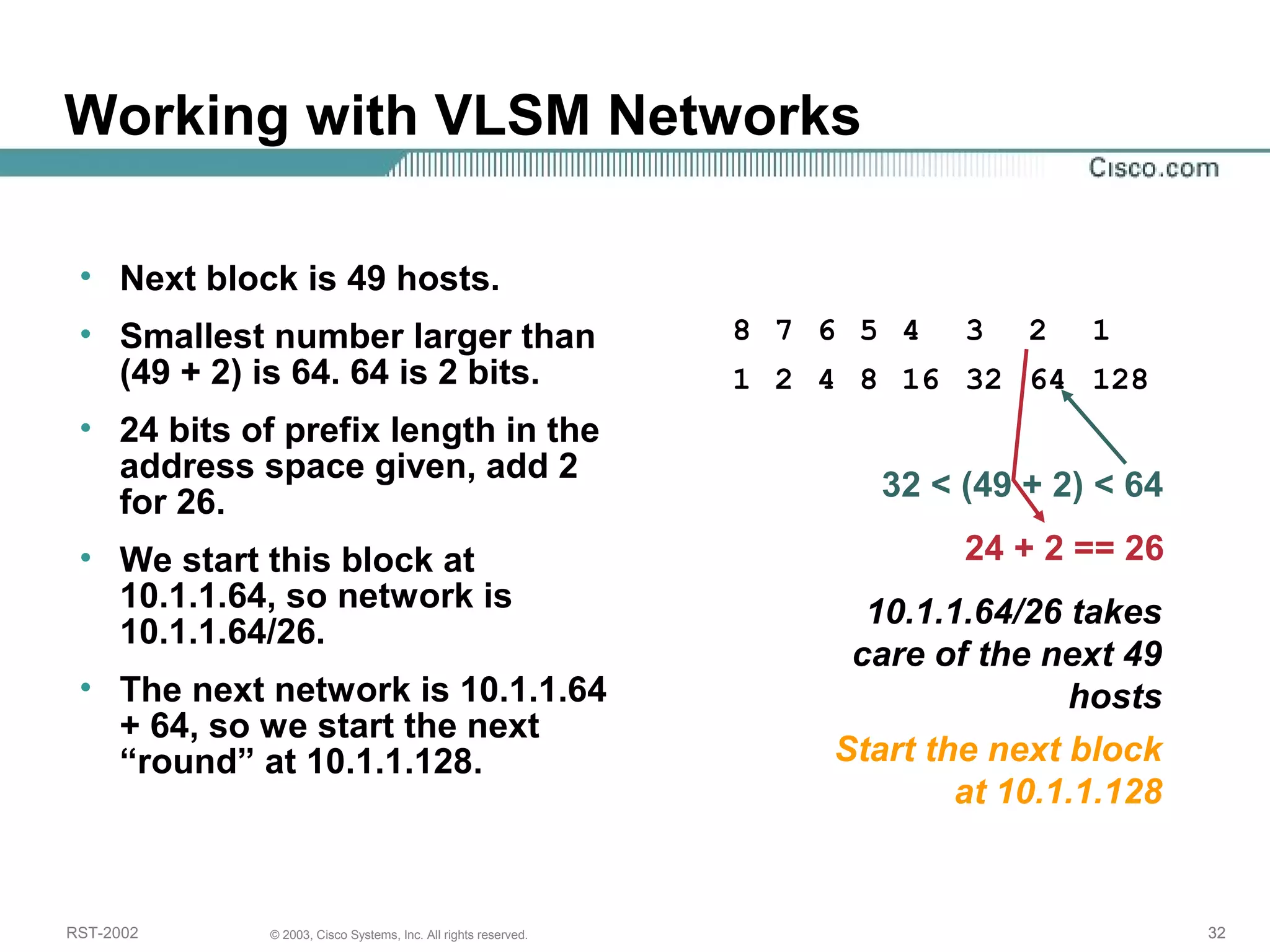
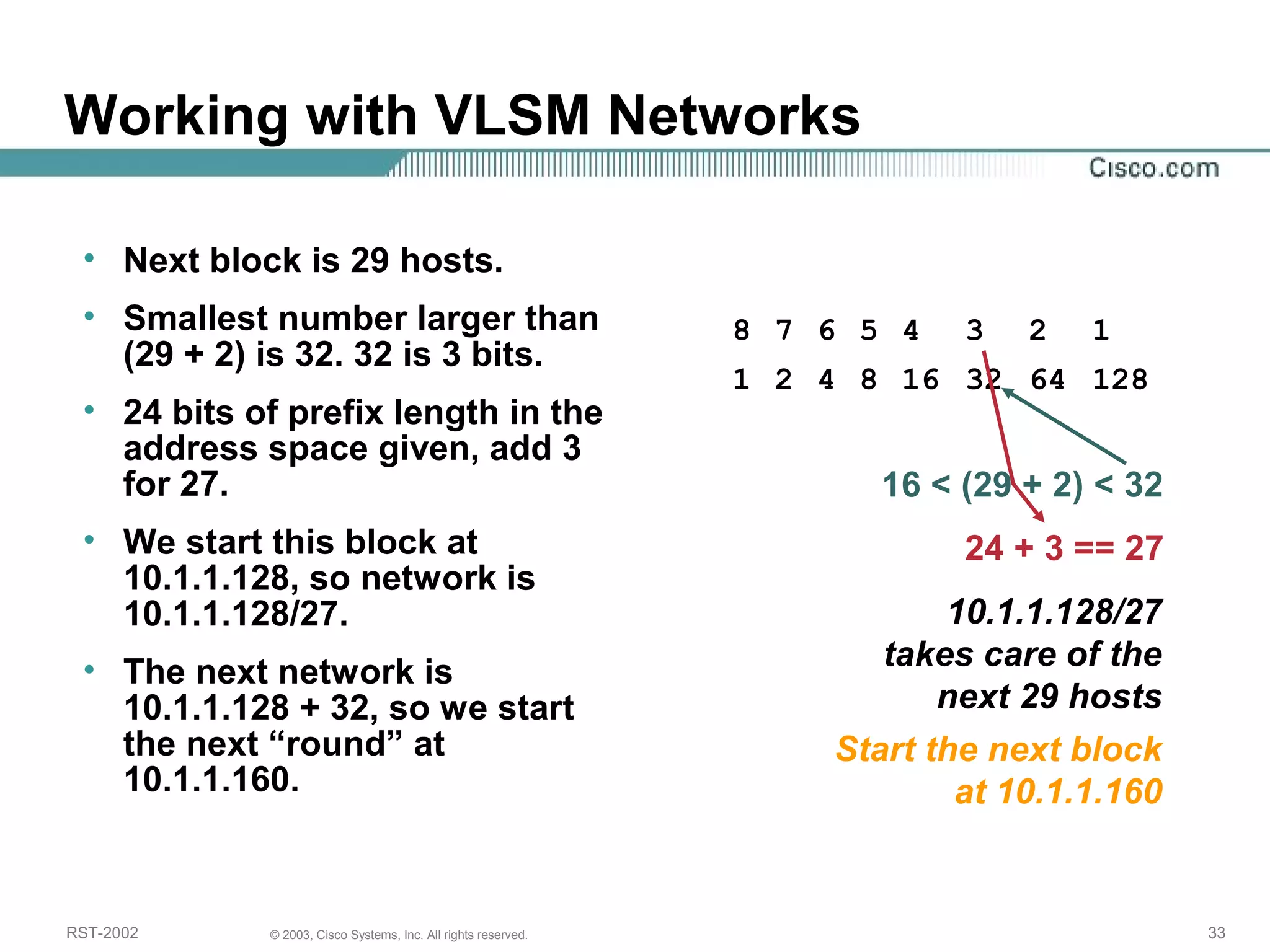
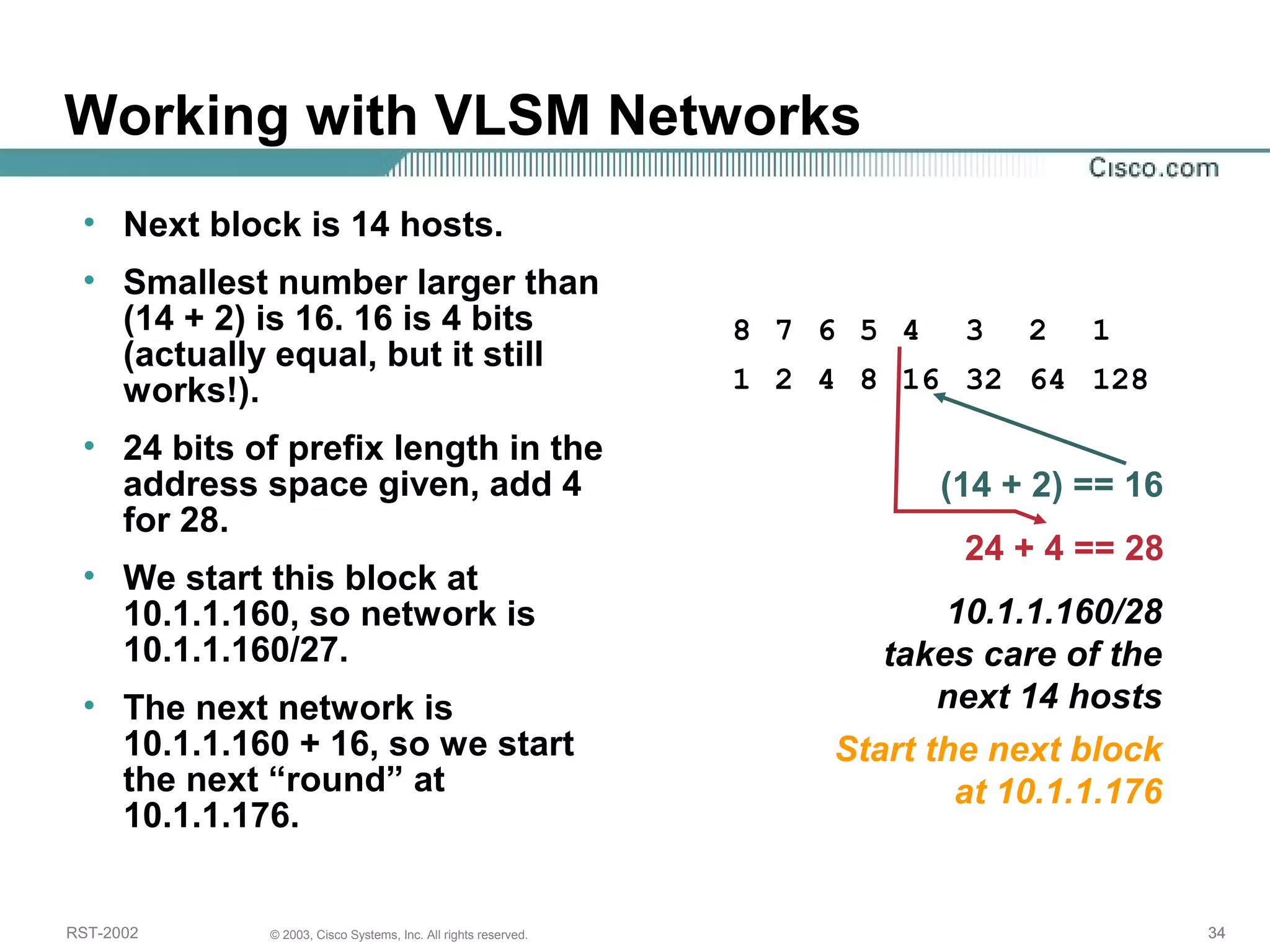
The document discusses IP addressing and subnetting. It begins with an overview of basic IP addressing concepts like dotted decimal notation, network masks, prefixes, and how to determine the network and host portions of an IP address. It then covers techniques for working with IP addresses and prefixes, including how to calculate the number of hosts in a subnet. The goal is to make these IP addressing concepts easier to understand and work with.








![Cisco IOS Show IP Route
2651A#sho ip route
....
Gateway of last resort is not set
two different prefix
lengths under the
same major
network
C 208.0.12.0/24 is directly connected, Serial0/2
....
S 208.1.10.0/24 [1/0] via 208.0.12.11
....
144.2.0.0/16 is variably subnetted, 2 subnets, 2 masks
S 144.2.2.0/24 [1/0] via 208.0.12.11
S 144.2.3.0/29 [1/0] via 208.0.12.11
C 208.0.7.0/24 is directly connected, Serial0/0
C 208.0.6.0/24 is directly connected, FastEthernet0/0
C 208.0.0.0/24 is directly connected, FastEthernet0/1
S 208.1.0.0/16 [1/0] via 208.0.12.11
a supernet and natural
mask in the same
network address space
RST-2002 © 2003, Cisco Systems, Inc. All rights reserved. 48](https://image.slidesharecdn.com/cisco-ip-addressing-141110161109-conversion-gate02/75/Cisco-ip-addressing-48-2048.jpg)