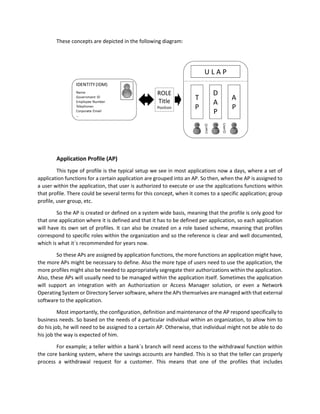
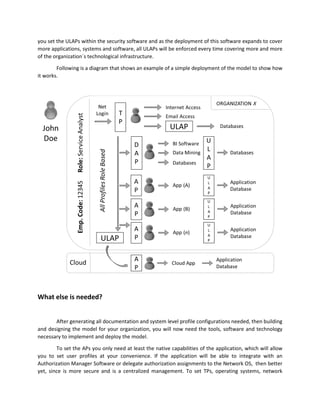
This document outlines a user access profiling model aimed at improving data protection and authorization management within organizations. It addresses the complexities of managing user access across various applications, technologies, and data types, while proposing a structured approach involving identities and roles for better security. The model emphasizes the need for centralized access control to mitigate risks associated with data proliferation, particularly in cloud computing environments.