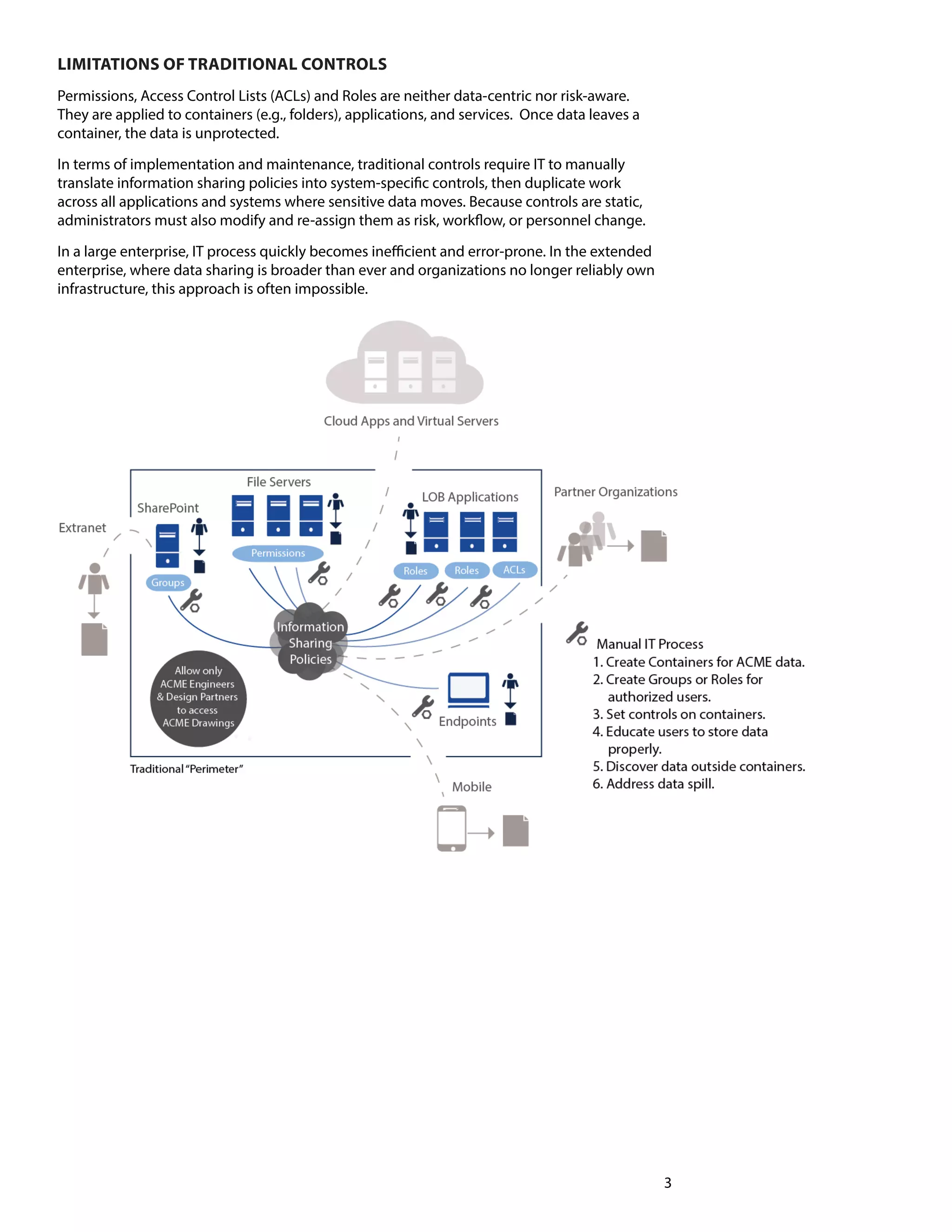
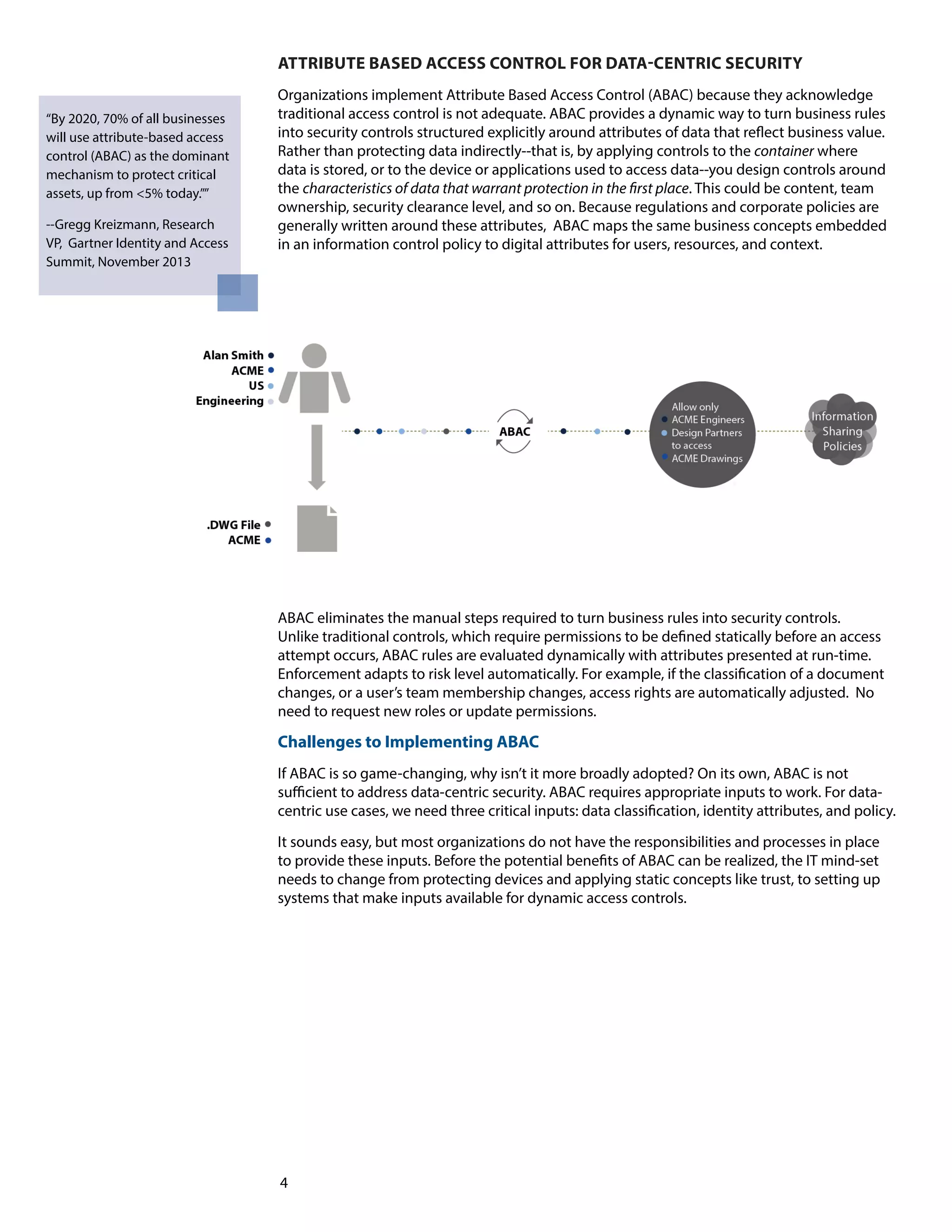
This white paper discusses the necessity for organizations to shift towards data-centric security to protect sensitive information in the evolving landscape of the extended enterprise. It outlines four fundamental changes needed to implement this approach, emphasizing the limitations of traditional security measures and the benefits of attribute-based access control (ABAC). Additionally, the paper highlights the challenges organizations face in adopting ABAC and the importance of dynamic risk management.