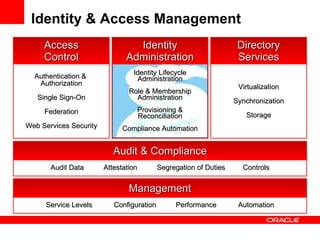
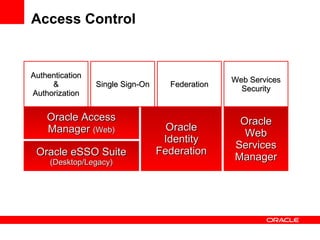
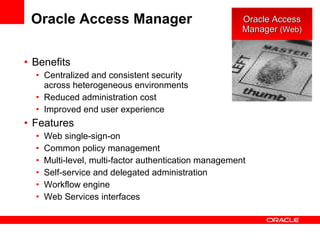
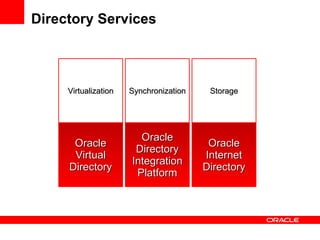
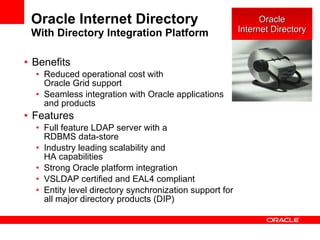
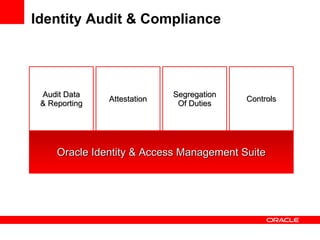
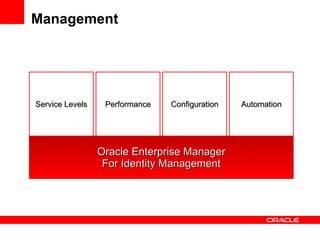
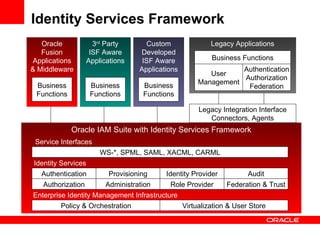
- The document introduces Oracle Identity and Access Management (IAM) solutions including Access Control, Directory Services, Identity Administration, Authentication & Authorization, Single Sign-On, Federation, Web Services Security, Identity Lifecycle Administration, Role & Membership Administration, Provisioning & Reconciliation, Compliance Automation, Virtualization, Synchronization, Storage, Audit & Compliance, and Management.
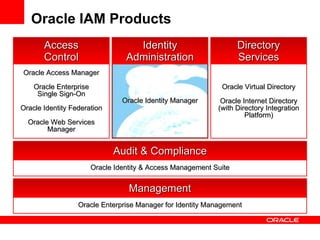
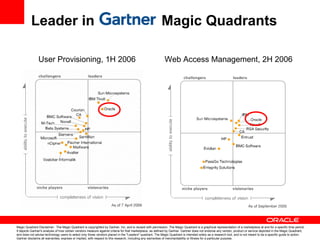
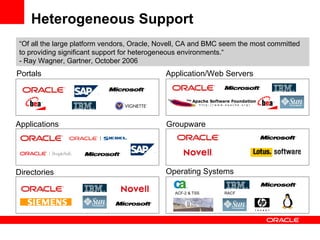
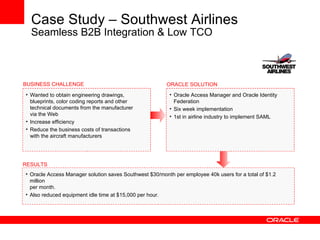
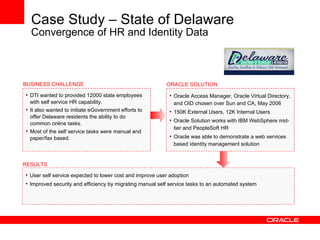
- It discusses Oracle IAM products that address these solutions and how Oracle has been a leader in industry evaluations. Customer examples are provided that demonstrate cost savings, improved security and compliance, and consolidated identity management.
- The future of Oracle IAM is discussed in terms of expanding the product portfolio, building security into databases and middleware,