AccessPaaS (SafePaaS)
•
0 likes•65 views
The expansion of business applications and devices is increasing data breach risk. Managing user entitlements has become more complex and traditional security systems cannot adequately monitor access across different applications. AccessPaaS is a cloud-based access management platform that uses over 200 rules covering 1,500 access points to identify access violations and risks across applications. It allows rapid remediation of issues through automated role design and access changes. Users can begin using the system within hours to identify violations and reduce access risks.
Report
Share
Report
Share
Download to read offline
Recommended
5 reasons your iam solution will fail

Recent security breaches by trusted insiders have propelled Identity and Access Management (IAM) to the top security priority of many organizations. After all, it’s clear security is only as strong as its weakest link – people – and the press is full of articles documenting the damage people can do. So it’s natural for security managers to want to shore up their IAM infrastructure to avoid similar embarrassment. But IAM needs to be approached with an eye towards the full extended environment and by taking associated risks into account. In other words, whether you are starting from scratch or taking on new IAM challenges such as cloud security, there are certain IAM tenets you should follow to build a successful, effective IAM solution.
Don’t join the Hall of Shame by having a security breach at your organization. Attend this webcast to learn five ways a typical IAM solution can fail, so you don’t make the same mistakes.
View the full on-demand webcast: http://securityintelligence.com/events/5-reasons-iam-solution-will-fail/#.VYxJ4_lVhBd
Network security in Chennai

There are many technology related companies, who project themselves as provider of network security, but few have an actual presence as Qadit has. Our skilled work force and organization presence have made us the most reliable company for providing network security in Chennai. Source: qadit.com
Need of Adaptive Authentication in defending the borderless Enterprise

ProactEye Adaptive Access & Identity Management solution can help administrators consolidate, control, and simplify access privileges. Privileges can be simplified and controlled irrespective of critical applications hosted in traditional data centres, private clouds, public clouds, or a hybrid combination of all these spaces.
Get Ahead of Cyber Attacks with Microsoft Enterprise Mobility + Security

Digital transformation with freedom and peace of mind
Holistic, identity-driven protection
Help guard your data from attacks on multiple levels using innovative, identity-driven security techniques.
Productivity without compromise
Preserve the mobile and desktop experiences your workers need to stay working with familiar apps and tools.
Flexible, comprehensive solutions
Do more with less—protect users, devices, apps, and data with intuitive mobile management on a future-ready platform.
microsoft@atidan.com
Samsung SDS IAM & EMM for Healthcare

Minimize data breaches and reduce the risks of regulatory non-compliance in addition to protecting patients, hospitals and insurance networks from fraud with Samsung SDS Identity and Access Management.
Recommended
5 reasons your iam solution will fail

Recent security breaches by trusted insiders have propelled Identity and Access Management (IAM) to the top security priority of many organizations. After all, it’s clear security is only as strong as its weakest link – people – and the press is full of articles documenting the damage people can do. So it’s natural for security managers to want to shore up their IAM infrastructure to avoid similar embarrassment. But IAM needs to be approached with an eye towards the full extended environment and by taking associated risks into account. In other words, whether you are starting from scratch or taking on new IAM challenges such as cloud security, there are certain IAM tenets you should follow to build a successful, effective IAM solution.
Don’t join the Hall of Shame by having a security breach at your organization. Attend this webcast to learn five ways a typical IAM solution can fail, so you don’t make the same mistakes.
View the full on-demand webcast: http://securityintelligence.com/events/5-reasons-iam-solution-will-fail/#.VYxJ4_lVhBd
Network security in Chennai

There are many technology related companies, who project themselves as provider of network security, but few have an actual presence as Qadit has. Our skilled work force and organization presence have made us the most reliable company for providing network security in Chennai. Source: qadit.com
Need of Adaptive Authentication in defending the borderless Enterprise

ProactEye Adaptive Access & Identity Management solution can help administrators consolidate, control, and simplify access privileges. Privileges can be simplified and controlled irrespective of critical applications hosted in traditional data centres, private clouds, public clouds, or a hybrid combination of all these spaces.
Get Ahead of Cyber Attacks with Microsoft Enterprise Mobility + Security

Digital transformation with freedom and peace of mind
Holistic, identity-driven protection
Help guard your data from attacks on multiple levels using innovative, identity-driven security techniques.
Productivity without compromise
Preserve the mobile and desktop experiences your workers need to stay working with familiar apps and tools.
Flexible, comprehensive solutions
Do more with less—protect users, devices, apps, and data with intuitive mobile management on a future-ready platform.
microsoft@atidan.com
Samsung SDS IAM & EMM for Healthcare

Minimize data breaches and reduce the risks of regulatory non-compliance in addition to protecting patients, hospitals and insurance networks from fraud with Samsung SDS Identity and Access Management.
Tools4ever identity & access management product brochure

Brochure encompassing all of the Tools4ever Identity and Password Management applications.
Identity and Access Management Playbook CISO Platform 2016

Checklist Playbook for CISO, CSO and Information Risk & Security Managers to plan and implement a successful IAM (Identity and Access Management) program. It covers Access Governance and Identity Administration, Single Sign On (SSO), Privileged Identity Management, and more.
Empower Enterprise Mobility- Maximize Mobile Control- Presented by Atidan

Identity + Mobile Management + Security
Keep your employees productive on their favorite apps and devices—and your company data protected with enterprise mobility solutions from Microsoft.
Windows 10 is better with EMS
Windows 10 is the best Windows ever and provides a foundation for protection against modern threats and continuous management while enabling your users to be more productive. To get the most out of your mobile security and productivity strategy, integrate the Microsoft Enterprise Mobility Suite (EMS) with Windows 10 for greater protection of users, devices, apps, and data.
Our enterprise-grade security
A key concern for you continues to be security, and rightly so. Identity is the control plane at the center of our solution helping you to be more secure. Only Microsoft offers cloud identity and access management solutions running at Internet scale and designed to help secure your IT environment. Microsoft Azure Active Directory has hundreds of millions of users, is available in 35 datacenters around the world, and has processed more than 1 trillion (yes, trillion) authentications. Our innovative new technology, Microsoft Advanced Threat Analytics is designed to help you identify advanced persistent threats in your organization before they cause damage.
We’re more integrated and flexible
Architecture matters. That’s why our solutions run in the cloud and work seamlessly with your on-premises investments—taking the worry out of scale, maintenance, and updates.
Our cloud-first approach provides an integrated set of solutions that are designed to work together from the ground up, avoiding the need for costly and complicated integration efforts across point capabilities. It’s the fastest and most cost-effective way to meet new business challenges and accommodate new devices, new apps, and new hires.
Nobody manages Office better
Protecting email and other corporate data on mobile devices—without bogging down workers—is one of today’s biggest IT challenges. Other vendors solve it with apps that compromise user experience and put the brakes on productivity.
Microsoft enterprise mobility solutions integrate deeply with Microsoft Office, the gold standard of productivity. We’re the only solution that brings managed mobile productivity with Microsoft Office across devices.
Webinar - How to choose the Right Compliance Management Software for your Org...

Webinar - How to choose the Right Compliance Management Software for your Org...TeamLease Regtech Pvt Ltd
Presentation on How to choose the Right Compliance Management Software for your Organization. Avantis has conducted webinar on compliance management software selection on 22th May 2020.
India’s regulatory universe is highly complex - 3,000+ possible filings - and extremely fluid - changing 2,500+ times a year. The traditional method of managing compliances breaks down in such a complex and fluid world.
Due diligence is key - the digital journey should be smooth. A good selection can be a blessing and a bad one can put you and your organization behind by several years. In this Webinar you will understand how to make the key decisions for a good Compliance Management Software:.
Topics Covered:
* Does it have all the right features?
* Is it easy to use?
* Is it quick and easy to deploy?
* Does it offer deployment options that suit you?
* Does it offer “Pay as you go” Pricing Option?
* Can the platform scale with you?
* Does it have clear terms of disengagement?
Avantis RegTech, A TeamLease Company is India's leading Compliance Management Software Company. For free personalized, real time, national and comprehensive Legal Updates, visit www.avantis.co.in and subscribe to our newsletter. Call us at 8893594595 for more details or write to us at sales@avantis.co.in to schedule a demo. Privileged identity management

Privileged IdentityManagement
Controlling access without compromising convenience
IBM Security Identity and Access Management - Portfolio

IBM Security Identity and Access Management - Products updates and what is coming
PIM, PAM, PUM: Best Practices for Unix/Linux Privileged Identity & Access Man...

PIM, PAM and PUM have different meanings, and interpretations, to different people. For the most part the concepts around these three far-ranging topics intersect, and for the most part we are talking about the same thing. PIM, privileged identity management; PUM, privileged user management; and PAM, privileged account management OR privileged access management. All three of these acronyms revolve around a few simple concepts: who can get to a server, how they can get to a server and what they can do when they get there.
Identity and Access Management (IAM): Benefits and Best Practices 

Identity and Access Management (IAM) enables more cost-effective and efficient access management, authentication, identity management, and governance across your enterprise.
Read more on How IAM benefits your business and best practices for an effective IAM implementation.
Read more: https://www.veritis.com/solutions/identity-and-access-management-services/
Windows 10 Enterprise E3 - Best in Class Security and Control - Presented by ...

Introducing Windows 10 Enterprise E3 for CSP
More than 350 million active devices are running Windows 10 and our business customers are moving faster than ever before, with more than 96% of them in active pilots. And, Windows 10 customers are already experiencing improved productivity and cost savings with an average ROI of 188% with a 13-month payback.*
In most instances, organizations are moving quickly to Windows 10 due to the heightened security risks they face and the industry-leading security features in Windows 10 that can help protect them. Companies of all sizes face real security threats from sophisticated hackers and cyber-terrorists, costing an average of $12 million an incident. In the US alone there are more than 56 million small to mid-sized businesses, in critical sectors like healthcare, legal and financial services that need strong security similar to what our large enterprise customers get through volume licensing agreements.
Partners can now offer their business customers the ‘full IT stack’ from Microsoft, including Windows 10, Office 365, Dynamics Azure and CRM as a per user, per month offering through a single channel, which businesses can scale up or down as their needs change. Key features include:
Increased Security: Offering the sophisticated security features of Windows 10 to help businesses secure sensitive data and identities, help ensure devices are protected from cybersecurity threats, give employees the freedom and flexibility to access sensitive data on a variety of devices, and help ensure controlled access to highly-sensitive data.
Simplified Licensing & Deployment: Helping businesses lower up-front costs, eliminating the need for time-consuming device counting and audits, and making it easier to stay compliant with a subscription-based, per-user licensing model. This new offering allows businesses to easily move from Windows 10 Pro to Windows 10 Enterprise E3 without rebooting.
Partner-managed IT: Configuring and managing devices by a partner experienced in Windows 10 and cloud deployments. Partners can also help businesses develop a device security and management strategy with the unique features of Windows 10. Businesses can view subscriptions and usage for Windows 10 Enterprise, and any other Microsoft cloud services purchased, in their partner portal for easier management with one contract, one user account, one support contact, and one simplified bill.
The 21 CFR Part 11 Compliance Checklist for Digital Applications

Are digital applications better than paper-based systems? Without a doubt, yes. Applications replace large cabinets of paper storage with a small computer. They not only save space and paper but also offer quick data or document search with easy updates. But there is one component where paper-based systems are better than applications and that is maintaining signatures. Physical signatures cannot be easily replicated. As a software developer, I have successfully developed complex dynamic forms with nested search queries, but it makes me ponder how can I validate a digital record or a signature that would make my developed system as reliable as a paper-based document management system?
IBM Security Portfolio - 2015

This is the product and services portfolio of IBM Security, which is one pillar of IBM CAMSS strategy. Products in portfolio are still moving during early 2015 due to re-portfolio of IBM. However, it will be categorized in 2 major parts.
1) IBM Security Products : all security software and appliance
2) IBM Security Services : all security services, including Cloud security.
Identity & Access Management - Securing Your Data in the 21st Century Enterprise

Identity & Access Management presentation at BSides Charlotte, June 13, 2015
SailPoint VS CyberArk.pdf

SailPoint is a centralized identity management solution that allows organizations to manage employee authorizations, digital identities, data security, network management, compliance, and more. CyberArk is used to access local admin accounts, domain admin accounts, service accounts, and other privileged accounts simply and safely.
Oracle Scene Safeguard your Business

Article written by Adil Khan, CEO at SafePaaS on how to use SOD to safeguard your business. Learn all about access controls to mitigate risk, cyberthreats and fraud within Oracle Applications.
More Related Content
What's hot
Tools4ever identity & access management product brochure

Brochure encompassing all of the Tools4ever Identity and Password Management applications.
Identity and Access Management Playbook CISO Platform 2016

Checklist Playbook for CISO, CSO and Information Risk & Security Managers to plan and implement a successful IAM (Identity and Access Management) program. It covers Access Governance and Identity Administration, Single Sign On (SSO), Privileged Identity Management, and more.
Empower Enterprise Mobility- Maximize Mobile Control- Presented by Atidan

Identity + Mobile Management + Security
Keep your employees productive on their favorite apps and devices—and your company data protected with enterprise mobility solutions from Microsoft.
Windows 10 is better with EMS
Windows 10 is the best Windows ever and provides a foundation for protection against modern threats and continuous management while enabling your users to be more productive. To get the most out of your mobile security and productivity strategy, integrate the Microsoft Enterprise Mobility Suite (EMS) with Windows 10 for greater protection of users, devices, apps, and data.
Our enterprise-grade security
A key concern for you continues to be security, and rightly so. Identity is the control plane at the center of our solution helping you to be more secure. Only Microsoft offers cloud identity and access management solutions running at Internet scale and designed to help secure your IT environment. Microsoft Azure Active Directory has hundreds of millions of users, is available in 35 datacenters around the world, and has processed more than 1 trillion (yes, trillion) authentications. Our innovative new technology, Microsoft Advanced Threat Analytics is designed to help you identify advanced persistent threats in your organization before they cause damage.
We’re more integrated and flexible
Architecture matters. That’s why our solutions run in the cloud and work seamlessly with your on-premises investments—taking the worry out of scale, maintenance, and updates.
Our cloud-first approach provides an integrated set of solutions that are designed to work together from the ground up, avoiding the need for costly and complicated integration efforts across point capabilities. It’s the fastest and most cost-effective way to meet new business challenges and accommodate new devices, new apps, and new hires.
Nobody manages Office better
Protecting email and other corporate data on mobile devices—without bogging down workers—is one of today’s biggest IT challenges. Other vendors solve it with apps that compromise user experience and put the brakes on productivity.
Microsoft enterprise mobility solutions integrate deeply with Microsoft Office, the gold standard of productivity. We’re the only solution that brings managed mobile productivity with Microsoft Office across devices.
Webinar - How to choose the Right Compliance Management Software for your Org...

Webinar - How to choose the Right Compliance Management Software for your Org...TeamLease Regtech Pvt Ltd
Presentation on How to choose the Right Compliance Management Software for your Organization. Avantis has conducted webinar on compliance management software selection on 22th May 2020.
India’s regulatory universe is highly complex - 3,000+ possible filings - and extremely fluid - changing 2,500+ times a year. The traditional method of managing compliances breaks down in such a complex and fluid world.
Due diligence is key - the digital journey should be smooth. A good selection can be a blessing and a bad one can put you and your organization behind by several years. In this Webinar you will understand how to make the key decisions for a good Compliance Management Software:.
Topics Covered:
* Does it have all the right features?
* Is it easy to use?
* Is it quick and easy to deploy?
* Does it offer deployment options that suit you?
* Does it offer “Pay as you go” Pricing Option?
* Can the platform scale with you?
* Does it have clear terms of disengagement?
Avantis RegTech, A TeamLease Company is India's leading Compliance Management Software Company. For free personalized, real time, national and comprehensive Legal Updates, visit www.avantis.co.in and subscribe to our newsletter. Call us at 8893594595 for more details or write to us at sales@avantis.co.in to schedule a demo. Privileged identity management

Privileged IdentityManagement
Controlling access without compromising convenience
IBM Security Identity and Access Management - Portfolio

IBM Security Identity and Access Management - Products updates and what is coming
PIM, PAM, PUM: Best Practices for Unix/Linux Privileged Identity & Access Man...

PIM, PAM and PUM have different meanings, and interpretations, to different people. For the most part the concepts around these three far-ranging topics intersect, and for the most part we are talking about the same thing. PIM, privileged identity management; PUM, privileged user management; and PAM, privileged account management OR privileged access management. All three of these acronyms revolve around a few simple concepts: who can get to a server, how they can get to a server and what they can do when they get there.
Identity and Access Management (IAM): Benefits and Best Practices 

Identity and Access Management (IAM) enables more cost-effective and efficient access management, authentication, identity management, and governance across your enterprise.
Read more on How IAM benefits your business and best practices for an effective IAM implementation.
Read more: https://www.veritis.com/solutions/identity-and-access-management-services/
Windows 10 Enterprise E3 - Best in Class Security and Control - Presented by ...

Introducing Windows 10 Enterprise E3 for CSP
More than 350 million active devices are running Windows 10 and our business customers are moving faster than ever before, with more than 96% of them in active pilots. And, Windows 10 customers are already experiencing improved productivity and cost savings with an average ROI of 188% with a 13-month payback.*
In most instances, organizations are moving quickly to Windows 10 due to the heightened security risks they face and the industry-leading security features in Windows 10 that can help protect them. Companies of all sizes face real security threats from sophisticated hackers and cyber-terrorists, costing an average of $12 million an incident. In the US alone there are more than 56 million small to mid-sized businesses, in critical sectors like healthcare, legal and financial services that need strong security similar to what our large enterprise customers get through volume licensing agreements.
Partners can now offer their business customers the ‘full IT stack’ from Microsoft, including Windows 10, Office 365, Dynamics Azure and CRM as a per user, per month offering through a single channel, which businesses can scale up or down as their needs change. Key features include:
Increased Security: Offering the sophisticated security features of Windows 10 to help businesses secure sensitive data and identities, help ensure devices are protected from cybersecurity threats, give employees the freedom and flexibility to access sensitive data on a variety of devices, and help ensure controlled access to highly-sensitive data.
Simplified Licensing & Deployment: Helping businesses lower up-front costs, eliminating the need for time-consuming device counting and audits, and making it easier to stay compliant with a subscription-based, per-user licensing model. This new offering allows businesses to easily move from Windows 10 Pro to Windows 10 Enterprise E3 without rebooting.
Partner-managed IT: Configuring and managing devices by a partner experienced in Windows 10 and cloud deployments. Partners can also help businesses develop a device security and management strategy with the unique features of Windows 10. Businesses can view subscriptions and usage for Windows 10 Enterprise, and any other Microsoft cloud services purchased, in their partner portal for easier management with one contract, one user account, one support contact, and one simplified bill.
The 21 CFR Part 11 Compliance Checklist for Digital Applications

Are digital applications better than paper-based systems? Without a doubt, yes. Applications replace large cabinets of paper storage with a small computer. They not only save space and paper but also offer quick data or document search with easy updates. But there is one component where paper-based systems are better than applications and that is maintaining signatures. Physical signatures cannot be easily replicated. As a software developer, I have successfully developed complex dynamic forms with nested search queries, but it makes me ponder how can I validate a digital record or a signature that would make my developed system as reliable as a paper-based document management system?
IBM Security Portfolio - 2015

This is the product and services portfolio of IBM Security, which is one pillar of IBM CAMSS strategy. Products in portfolio are still moving during early 2015 due to re-portfolio of IBM. However, it will be categorized in 2 major parts.
1) IBM Security Products : all security software and appliance
2) IBM Security Services : all security services, including Cloud security.
Identity & Access Management - Securing Your Data in the 21st Century Enterprise

Identity & Access Management presentation at BSides Charlotte, June 13, 2015
What's hot (19)
Tools4ever identity & access management product brochure

Tools4ever identity & access management product brochure
Identity and Access Management Playbook CISO Platform 2016

Identity and Access Management Playbook CISO Platform 2016
Empower Enterprise Mobility- Maximize Mobile Control- Presented by Atidan

Empower Enterprise Mobility- Maximize Mobile Control- Presented by Atidan
Webinar - How to choose the Right Compliance Management Software for your Org...

Webinar - How to choose the Right Compliance Management Software for your Org...
IBM Security Identity and Access Management - Portfolio

IBM Security Identity and Access Management - Portfolio
PIM, PAM, PUM: Best Practices for Unix/Linux Privileged Identity & Access Man...

PIM, PAM, PUM: Best Practices for Unix/Linux Privileged Identity & Access Man...
Identity and Access Management (IAM): Benefits and Best Practices 

Identity and Access Management (IAM): Benefits and Best Practices
Windows 10 Enterprise E3 - Best in Class Security and Control - Presented by ...

Windows 10 Enterprise E3 - Best in Class Security and Control - Presented by ...
The 21 CFR Part 11 Compliance Checklist for Digital Applications

The 21 CFR Part 11 Compliance Checklist for Digital Applications
Identity & Access Management - Securing Your Data in the 21st Century Enterprise

Identity & Access Management - Securing Your Data in the 21st Century Enterprise
Biometric - Solutions for Enterprises & Commercial banking

Biometric - Solutions for Enterprises & Commercial banking
Similar to AccessPaaS (SafePaaS)
SailPoint VS CyberArk.pdf

SailPoint is a centralized identity management solution that allows organizations to manage employee authorizations, digital identities, data security, network management, compliance, and more. CyberArk is used to access local admin accounts, domain admin accounts, service accounts, and other privileged accounts simply and safely.
Oracle Scene Safeguard your Business

Article written by Adil Khan, CEO at SafePaaS on how to use SOD to safeguard your business. Learn all about access controls to mitigate risk, cyberthreats and fraud within Oracle Applications.
Oracle Scene Oct 2017

Article "Safeguard Your Business - with access controls that mitigate the risk of cyber threats, financial misstatements and fraud in Oracle Applications." by SafePaaS CEO Adil Khan
okta | Top 8 Identity and Access Management Challenges with Your SaaS Applica...

Copyright ICMP Technologies Inc. 2017
Identity Manager & AirWatch Cloud Mobile App - Infographic

Identity Manager & AirWatch Cloud Mobile App - Infographic
Enterprise GRC for PEoplesoft

This solution brief is a guide for PeopleSoft customers to conform to evolving risk management and compliance standards
Security and Compliance

Security and compliance is an ongoing process, not a steady state. It is constantly maintained, enhanced, and verified by highly-skilled, experienced and trained personnel. We strive to keep software and hardware technologies up to date through robust processes. To help keep Office 365 security at the top of the industry, we use processes such as the Security Development Lifecycle; we also employ techniques that throttle traffic and prevent, detect, and mitigate breaches.
https://runfrictionless.com/b2b-white-paper-service/
Aplication data security compliances

Protect What Matters Most: Business Critical Apps and Data : Hackers and malicious insiders steal your data by exploiting the gaps left by traditional endpoint and network security. As many companies have painfully discovered, a breach goes far beyond the loss of data. It results in financial losses, regulatory fines, and damage to a company’s reputation. The Imperva SecureSphere, Incapsula and Skyfence product lines enable organizations to discover assets and vulnerabilities, protect information wherever it lives – in the cloud and on-premises – and comply with regulations. check this out and thanks
Intelligence Driven Identity and Access Management

This RSA white paper discusses the benefits of Intelligence Driven Identity and Access Management (IAM), and describes various RSA IAM solutions.
JDi Data Claims Management & Policy Administration System Overview

Insurance Software Solutions Created With Your Success in Mind.
Power better claims management results. JDi Data suite of claims management and policy administration solutions can help turn around your claims management and workers compensation processes.
Top Five Security Must-Haves for Office 365

Whether you’ve already deployed Office 365 or have plans to, security considerations around moving your business-critical apps to the cloud are paramount. From Exchange, Yammer, and SharePoint to OneDrive and the Administrator Portal, monitoring activity and securing access is critical to mitigating threats and protecting confidential data.
DemandTec case study

While providing applications to their employees, DemandTec was able to meet new business needs with cloud solutions and migrate existing on-premises functionality to SaaS providers.
Identity and Access Management (IAM)

Identity and Access Management (IAM) is a crucial part of living in a connected world. It involves managing multiple identities of an individual or entity, distributed across disparate portals. In an enterprise, IAM solutions serve as a mean to secure access, control user activities and manage authentication for an App or a group of software (infrastructure).
This detailed PowerPoint brings you the most fundamental concepts and ideas related to identity and access management. Plus, we have debunked some popular IAM myths, so do checkout!
Business-Driven Identity and Access Governance: Why This New Approach Matters

This white paper explains why taking a business-driven approach to identity and access governance (IAG) can enable organizations to easily prove compliance, minimize risk, and enable the business to be productive.
Similar to AccessPaaS (SafePaaS) (20)
okta | Top 8 Identity and Access Management Challenges with Your SaaS Applica...

okta | Top 8 Identity and Access Management Challenges with Your SaaS Applica...
Identity Manager & AirWatch Cloud Mobile App - Infographic

Identity Manager & AirWatch Cloud Mobile App - Infographic
Intelligence Driven Identity and Access Management

Intelligence Driven Identity and Access Management
JDi Data Claims Management & Policy Administration System Overview

JDi Data Claims Management & Policy Administration System Overview
Business-Driven Identity and Access Governance: Why This New Approach Matters

Business-Driven Identity and Access Governance: Why This New Approach Matters
Recently uploaded
Cracking the code review at SpringIO 2024

Code reviews are vital for ensuring good code quality. They serve as one of our last lines of defense against bugs and subpar code reaching production.
Yet, they often turn into annoying tasks riddled with frustration, hostility, unclear feedback and lack of standards. How can we improve this crucial process?
In this session we will cover:
- The Art of Effective Code Reviews
- Streamlining the Review Process
- Elevating Reviews with Automated Tools
By the end of this presentation, you'll have the knowledge on how to organize and improve your code review proces
WSO2Con2024 - WSO2's IAM Vision: Identity-Led Digital Transformation

WSO2Con2024 - WSO2's IAM Vision: Identity-Led Digital Transformation
SOCRadar Research Team: Latest Activities of IntelBroker

The European Union Agency for Law Enforcement Cooperation (Europol) has suffered an alleged data breach after a notorious threat actor claimed to have exfiltrated data from its systems. Infamous data leaker IntelBroker posted on the even more infamous BreachForums hacking forum, saying that Europol suffered a data breach this month.
The alleged breach affected Europol agencies CCSE, EC3, Europol Platform for Experts, Law Enforcement Forum, and SIRIUS. Infiltration of these entities can disrupt ongoing investigations and compromise sensitive intelligence shared among international law enforcement agencies.
However, this is neither the first nor the last activity of IntekBroker. We have compiled for you what happened in the last few days. To track such hacker activities on dark web sources like hacker forums, private Telegram channels, and other hidden platforms where cyber threats often originate, you can check SOCRadar’s Dark Web News.
Stay Informed on Threat Actors’ Activity on the Dark Web with SOCRadar!
Vitthal Shirke Microservices Resume Montevideo

Software Engineering, Software Consulting, Tech Lead.
Spring Boot, Spring Cloud, Spring Core, Spring JDBC, Spring Security,
Spring Transaction, Spring MVC,
Log4j, REST/SOAP WEB-SERVICES.
Gamify Your Mind; The Secret Sauce to Delivering Success, Continuously Improv...

Games are powerful teaching tools, fostering hands-on engagement and fun. But they require careful consideration to succeed. Join me to explore factors in running and selecting games, ensuring they serve as effective teaching tools. Learn to maintain focus on learning objectives while playing, and how to measure the ROI of gaming in education. Discover strategies for pitching gaming to leadership. This session offers insights, tips, and examples for coaches, team leads, and enterprise leaders seeking to teach from simple to complex concepts.
First Steps with Globus Compute Multi-User Endpoints

In this presentation we will share our experiences around getting started with the Globus Compute multi-user endpoint. Working with the Pharmacology group at the University of Auckland, we have previously written an application using Globus Compute that can offload computationally expensive steps in the researcher's workflows, which they wish to manage from their familiar Windows environments, onto the NeSI (New Zealand eScience Infrastructure) cluster. Some of the challenges we have encountered were that each researcher had to set up and manage their own single-user globus compute endpoint and that the workloads had varying resource requirements (CPUs, memory and wall time) between different runs. We hope that the multi-user endpoint will help to address these challenges and share an update on our progress here.
Why React Native as a Strategic Advantage for Startup Innovation.pdf

Do you know that React Native is being increasingly adopted by startups as well as big companies in the mobile app development industry? Big names like Facebook, Instagram, and Pinterest have already integrated this robust open-source framework.
In fact, according to a report by Statista, the number of React Native developers has been steadily increasing over the years, reaching an estimated 1.9 million by the end of 2024. This means that the demand for this framework in the job market has been growing making it a valuable skill.
But what makes React Native so popular for mobile application development? It offers excellent cross-platform capabilities among other benefits. This way, with React Native, developers can write code once and run it on both iOS and Android devices thus saving time and resources leading to shorter development cycles hence faster time-to-market for your app.
Let’s take the example of a startup, which wanted to release their app on both iOS and Android at once. Through the use of React Native they managed to create an app and bring it into the market within a very short period. This helped them gain an advantage over their competitors because they had access to a large user base who were able to generate revenue quickly for them.
How Recreation Management Software Can Streamline Your Operations.pptx

Recreation management software streamlines operations by automating key tasks such as scheduling, registration, and payment processing, reducing manual workload and errors. It provides centralized management of facilities, classes, and events, ensuring efficient resource allocation and facility usage. The software offers user-friendly online portals for easy access to bookings and program information, enhancing customer experience. Real-time reporting and data analytics deliver insights into attendance and preferences, aiding in strategic decision-making. Additionally, effective communication tools keep participants and staff informed with timely updates. Overall, recreation management software enhances efficiency, improves service delivery, and boosts customer satisfaction.
Exploring Innovations in Data Repository Solutions - Insights from the U.S. G...

The U.S. Geological Survey (USGS) has made substantial investments in meeting evolving scientific, technical, and policy driven demands on storing, managing, and delivering data. As these demands continue to grow in complexity and scale, the USGS must continue to explore innovative solutions to improve its management, curation, sharing, delivering, and preservation approaches for large-scale research data. Supporting these needs, the USGS has partnered with the University of Chicago-Globus to research and develop advanced repository components and workflows leveraging its current investment in Globus. The primary outcome of this partnership includes the development of a prototype enterprise repository, driven by USGS Data Release requirements, through exploration and implementation of the entire suite of the Globus platform offerings, including Globus Flow, Globus Auth, Globus Transfer, and Globus Search. This presentation will provide insights into this research partnership, introduce the unique requirements and challenges being addressed and provide relevant project progress.
Advanced Flow Concepts Every Developer Should Know

Tim Combridge from Sensible Giraffe and Salesforce Ben presents some important tips that all developers should know when dealing with Flows in Salesforce.
Innovating Inference - Remote Triggering of Large Language Models on HPC Clus...

Large Language Models (LLMs) are currently the center of attention in the tech world, particularly for their potential to advance research. In this presentation, we'll explore a straightforward and effective method for quickly initiating inference runs on supercomputers using the vLLM tool with Globus Compute, specifically on the Polaris system at ALCF. We'll begin by briefly discussing the popularity and applications of LLMs in various fields. Following this, we will introduce the vLLM tool, and explain how it integrates with Globus Compute to efficiently manage LLM operations on Polaris. Attendees will learn the practical aspects of setting up and remotely triggering LLMs from local machines, focusing on ease of use and efficiency. This talk is ideal for researchers and practitioners looking to leverage the power of LLMs in their work, offering a clear guide to harnessing supercomputing resources for quick and effective LLM inference.
Climate Science Flows: Enabling Petabyte-Scale Climate Analysis with the Eart...

The Earth System Grid Federation (ESGF) is a global network of data servers that archives and distributes the planet’s largest collection of Earth system model output for thousands of climate and environmental scientists worldwide. Many of these petabyte-scale data archives are located in proximity to large high-performance computing (HPC) or cloud computing resources, but the primary workflow for data users consists of transferring data, and applying computations on a different system. As a part of the ESGF 2.0 US project (funded by the United States Department of Energy Office of Science), we developed pre-defined data workflows, which can be run on-demand, capable of applying many data reduction and data analysis to the large ESGF data archives, transferring only the resultant analysis (ex. visualizations, smaller data files). In this talk, we will showcase a few of these workflows, highlighting how Globus Flows can be used for petabyte-scale climate analysis.
Enhancing Research Orchestration Capabilities at ORNL.pdf

Cross-facility research orchestration comes with ever-changing constraints regarding the availability and suitability of various compute and data resources. In short, a flexible data and processing fabric is needed to enable the dynamic redirection of data and compute tasks throughout the lifecycle of an experiment. In this talk, we illustrate how we easily leveraged Globus services to instrument the ACE research testbed at the Oak Ridge Leadership Computing Facility with flexible data and task orchestration capabilities.
Prosigns: Transforming Business with Tailored Technology Solutions

Unlocking Business Potential: Tailored Technology Solutions by Prosigns
Discover how Prosigns, a leading technology solutions provider, partners with businesses to drive innovation and success. Our presentation showcases our comprehensive range of services, including custom software development, web and mobile app development, AI & ML solutions, blockchain integration, DevOps services, and Microsoft Dynamics 365 support.
Custom Software Development: Prosigns specializes in creating bespoke software solutions that cater to your unique business needs. Our team of experts works closely with you to understand your requirements and deliver tailor-made software that enhances efficiency and drives growth.
Web and Mobile App Development: From responsive websites to intuitive mobile applications, Prosigns develops cutting-edge solutions that engage users and deliver seamless experiences across devices.
AI & ML Solutions: Harnessing the power of Artificial Intelligence and Machine Learning, Prosigns provides smart solutions that automate processes, provide valuable insights, and drive informed decision-making.
Blockchain Integration: Prosigns offers comprehensive blockchain solutions, including development, integration, and consulting services, enabling businesses to leverage blockchain technology for enhanced security, transparency, and efficiency.
DevOps Services: Prosigns' DevOps services streamline development and operations processes, ensuring faster and more reliable software delivery through automation and continuous integration.
Microsoft Dynamics 365 Support: Prosigns provides comprehensive support and maintenance services for Microsoft Dynamics 365, ensuring your system is always up-to-date, secure, and running smoothly.
Learn how our collaborative approach and dedication to excellence help businesses achieve their goals and stay ahead in today's digital landscape. From concept to deployment, Prosigns is your trusted partner for transforming ideas into reality and unlocking the full potential of your business.
Join us on a journey of innovation and growth. Let's partner for success with Prosigns.
Designing for Privacy in Amazon Web Services

Data privacy is one of the most critical issues that businesses face. This presentation shares insights on the principles and best practices for ensuring the resilience and security of your workload.
Drawing on a real-life project from the HR industry, the various challenges will be demonstrated: data protection, self-healing, business continuity, security, and transparency of data processing. This systematized approach allowed to create a secure AWS cloud infrastructure that not only met strict compliance rules but also exceeded the client's expectations.
Developing Distributed High-performance Computing Capabilities of an Open Sci...

COVID-19 had an unprecedented impact on scientific collaboration. The pandemic and its broad response from the scientific community has forged new relationships among public health practitioners, mathematical modelers, and scientific computing specialists, while revealing critical gaps in exploiting advanced computing systems to support urgent decision making. Informed by our team’s work in applying high-performance computing in support of public health decision makers during the COVID-19 pandemic, we present how Globus technologies are enabling the development of an open science platform for robust epidemic analysis, with the goal of collaborative, secure, distributed, on-demand, and fast time-to-solution analyses to support public health.
Explore Modern SharePoint Templates for 2024

Modern design is crucial in today's digital environment, and this is especially true for SharePoint intranets. The design of these digital hubs is critical to user engagement and productivity enhancement. They are the cornerstone of internal collaboration and interaction within enterprises.
Webinar: Salesforce Document Management 2.0 - Smarter, Faster, Better

Check out the webinar slides to learn more about how XfilesPro transforms Salesforce document management by leveraging its world-class applications. For more details, please connect with sales@xfilespro.com
If you want to watch the on-demand webinar, please click here: https://www.xfilespro.com/webinars/salesforce-document-management-2-0-smarter-faster-better/
top nidhi software solution freedownload

This presentation emphasizes the importance of data security and legal compliance for Nidhi companies in India. It highlights how online Nidhi software solutions, like Vector Nidhi Software, offer advanced features tailored to these needs. Key aspects include encryption, access controls, and audit trails to ensure data security. The software complies with regulatory guidelines from the MCA and RBI and adheres to Nidhi Rules, 2014. With customizable, user-friendly interfaces and real-time features, these Nidhi software solutions enhance efficiency, support growth, and provide exceptional member services. The presentation concludes with contact information for further inquiries.
Cyaniclab : Software Development Agency Portfolio.pdf

CyanicLab, an offshore custom software development company based in Sweden,India, Finland, is your go-to partner for startup development and innovative web design solutions. Our expert team specializes in crafting cutting-edge software tailored to meet the unique needs of startups and established enterprises alike. From conceptualization to execution, we offer comprehensive services including web and mobile app development, UI/UX design, and ongoing software maintenance. Ready to elevate your business? Contact CyanicLab today and let us propel your vision to success with our top-notch IT solutions.
Recently uploaded (20)
WSO2Con2024 - WSO2's IAM Vision: Identity-Led Digital Transformation

WSO2Con2024 - WSO2's IAM Vision: Identity-Led Digital Transformation
SOCRadar Research Team: Latest Activities of IntelBroker

SOCRadar Research Team: Latest Activities of IntelBroker
Gamify Your Mind; The Secret Sauce to Delivering Success, Continuously Improv...

Gamify Your Mind; The Secret Sauce to Delivering Success, Continuously Improv...
First Steps with Globus Compute Multi-User Endpoints

First Steps with Globus Compute Multi-User Endpoints
Why React Native as a Strategic Advantage for Startup Innovation.pdf

Why React Native as a Strategic Advantage for Startup Innovation.pdf
How Recreation Management Software Can Streamline Your Operations.pptx

How Recreation Management Software Can Streamline Your Operations.pptx
Exploring Innovations in Data Repository Solutions - Insights from the U.S. G...

Exploring Innovations in Data Repository Solutions - Insights from the U.S. G...
Advanced Flow Concepts Every Developer Should Know

Advanced Flow Concepts Every Developer Should Know
Innovating Inference - Remote Triggering of Large Language Models on HPC Clus...

Innovating Inference - Remote Triggering of Large Language Models on HPC Clus...
Climate Science Flows: Enabling Petabyte-Scale Climate Analysis with the Eart...

Climate Science Flows: Enabling Petabyte-Scale Climate Analysis with the Eart...
Enhancing Research Orchestration Capabilities at ORNL.pdf

Enhancing Research Orchestration Capabilities at ORNL.pdf
Prosigns: Transforming Business with Tailored Technology Solutions

Prosigns: Transforming Business with Tailored Technology Solutions
Developing Distributed High-performance Computing Capabilities of an Open Sci...

Developing Distributed High-performance Computing Capabilities of an Open Sci...
Webinar: Salesforce Document Management 2.0 - Smarter, Faster, Better

Webinar: Salesforce Document Management 2.0 - Smarter, Faster, Better
Cyaniclab : Software Development Agency Portfolio.pdf

Cyaniclab : Software Development Agency Portfolio.pdf
AccessPaaS (SafePaaS)
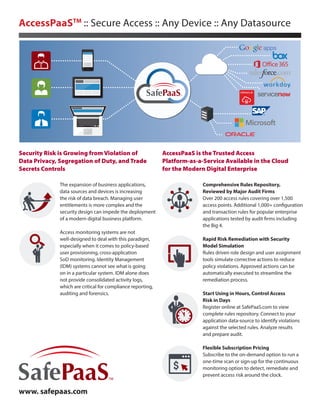
- 1. Security Risk is Growing from Violation of Data Privacy, Segregation of Duty, and Trade Secrets Controls The expansion of business applications, data sources and devices is increasing the risk of data breach. Managing user entitlements is more complex and the security design can impede the deployment of a modern digital business platform. Access monitoring systems are not well-designed to deal with this paradigm, especially when it comes to policy-based user provisioning, cross-application SoD monitoring. Identity Management (IDM) systems cannot see what is going on in a particular system. IDM alone does not provide consolidated activity logs, which are critical for compliance reporting, auditing and forensics. AccessPaaS is the Trusted Access Platform-as-a-Service Available in the Cloud for the Modern Digital Enterprise Comprehensive Rules Repository, Reviewed by Major Audit Firms Over 200 access rules covering over 1,500 access points. Additional 1,000+ configuration and transaction rules for popular enterprise applications tested by audit firms including the Big 4. Rapid Risk Remediation with Security Model Simulation Rules driven role design and user assignment tools simulate corrective actions to reduce policy violations. Approved actions can be automatically executed to streamline the remediation process. Start Using in Hours, Control Access Risk in Days Register online at SafePaaS.com to view complete rules repository. Connect to your application data-source to identify violations against the selected rules. Analyze results and prepare audit. Flexible Subscription Pricing Subscribe to the on-demand option to run a one-time scan or sign-up for the continuous monitoring option to detect, remediate and prevent access risk around the clock. AccessPaaSTM :: Secure Access :: Any Device :: Any Datasource www. safepaas.com
- 2. Access Management for Cloud and On-Premise Applications Self Service Identity Based Access Provisioning • Safeguard your most important business information against cybersecurity risks with policy-based centralized orchestration of user identity management and access control. • Improve productivity and reduce costs by enforcing access policies, such as segregation of duty (SoD) rules, before violations get introduced into the ERP environment, controlling sensitive business information to potential threats and vulnerabilities. Role Based Access Controls • Discover instant access insight and user access risks within your business applications to correct Roles that improve user productivity and mitigate enterprise information risks. • Automate change controls over the Roles to ensure that the process owners can review and approve Roles based on responsibilities, organization structure, data security rules and job position. Segregation of Duties (SoD) Policy Management • Jump start your top down risk-based SoD analysis with hundreds of SoD Rules based on thousands of application functions, included in our rules repository. • Rapidly reduce SoD risks with workflow enabled collaboration among process owners, application managers, IS security and Auditors. Periodic User Certification • Automate periodic user access review to comply with access policies and maintain audit trail to support IT General Controls. • Enable managers to detect dormant user and unauthorized system access. Identify Governance - #1 area requiring remedial action: • User access is a top focus for IT auditors because it is a common source of internal abuse • Gartner Survey: 44% of IT audit deficiencies are access related • Ernst & Young: 7 of Top 10 control deficiencies relate to user access control Access Management for Any App, Any Data Source Configure the security model for any application data source to enable central access management. The security snapshot is extracted and analyzed for access policy compliance. The solution includes pre-configured security model for popular enterprise applications including Oracle E-Business Suite, PeopleSoft, J D Edwards, SAP, Salesforce and Workday. Secure Single Sign-on with Active Directory Integration Fast access to all cloud apps as well as on premise apps behind the firewall – via desktops, smartphones and tablets. Our policy-driven security and multi-factor authentication ensure that only authorized users get access to sensitive data. Changes in active directory are synchronized to downstream applications continuously, providing you with an effective enterprise wide access control to minimize cybersecurity risks. Unique Profile based Device Management AccessPaaS allows the user to enroll an access device such as laptop, desktop, mobile phone and tablet with a Cloud Directory and creates a secure profile on the device that can only be accessed with individual AccessPaaS Cloud Directory credentials. Once in the new secure profile, the user can access web and desktop apps at will without entering credentials again. In other words, once the user is logged in to their device, they won’t need to log in again to access AccessPaaS and SAMLenabled cloud and on-premise apps. Centralized Audit Trail A key benefit of identity and access management is the centralized recording of all user management and log in activities. AccessPaaS audit trail records all user changes and activities, which can be used for powerful statistics or retroactive forensics. Orphan Accounts • Poor de-provisioning • High risk of sabotage, t heft and fraud Rogue Accounts • Fake accounts created by criminals • Undetected access and activity • Data theft, fraud and abuse Entitlement Creep • Accumulated privileges • Potential toxic combinations • Increased risk of fraud Privileged Users • Users with “keys to kingdom” • Poor visibility due to shared a ccounts