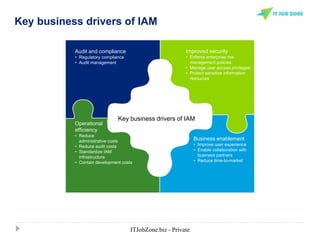
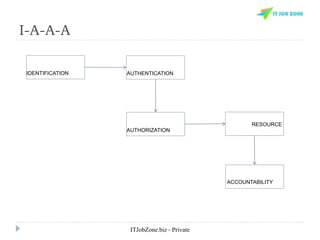
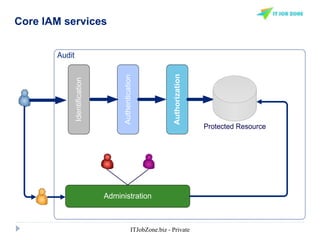
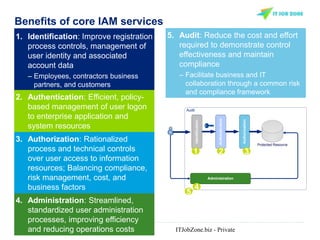
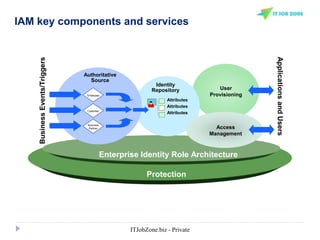
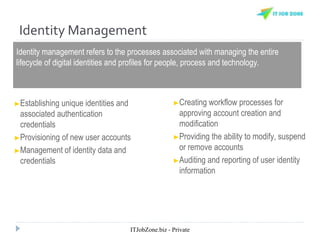
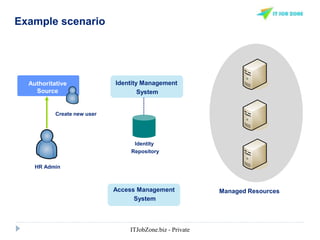
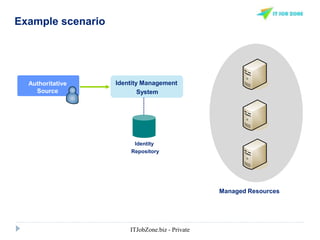
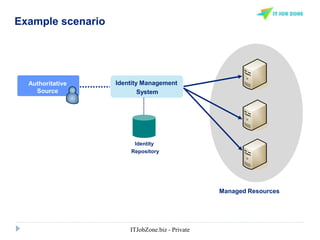
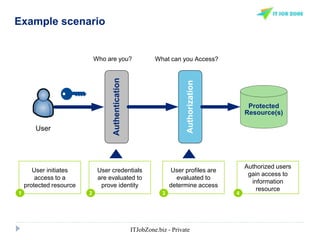
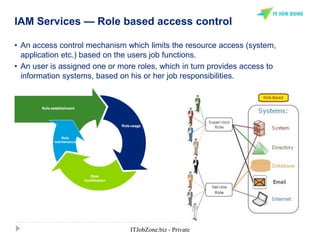
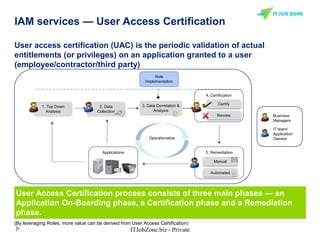
The document provides an overview of Identity and Access Management (IAM) and its importance in managing digital identities, access privileges, and compliance. It highlights key business drivers, such as improved security and operational efficiency, along with core IAM services and components. Additionally, it discusses processes like user access certification and role-based access control to ensure effective management of user identities and their access to resources.