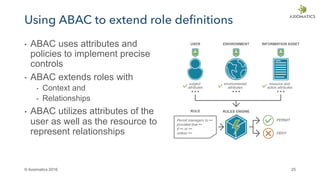
This document discusses the increasing complexity of access control and the need for next generation access control solutions. It outlines 7 trends driving this complexity, including increased data sharing and regulation, identity management for many types of users, and big data analytics. It argues that traditional static access control models are no longer sufficient and that attribute-based access control (ABAC) is needed to enable fine-grained, dynamic access decisions based on multiple attributes. The document provides an overview of how ABAC works and how Axiomatics provides software to implement ABAC for applications, databases, and policy management and review.