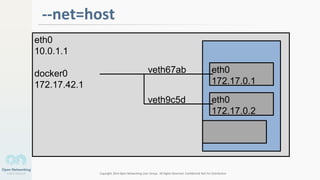
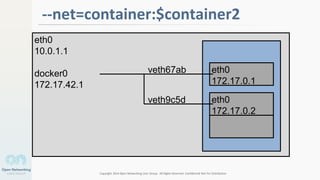
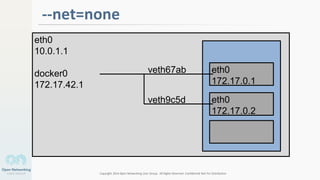
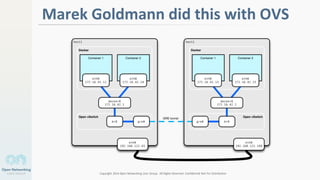
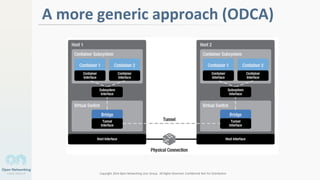
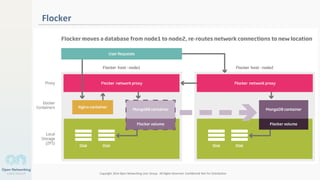
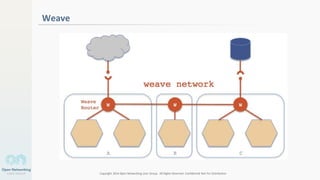
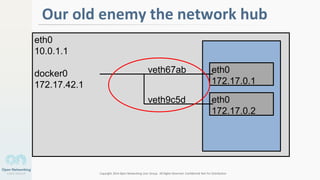
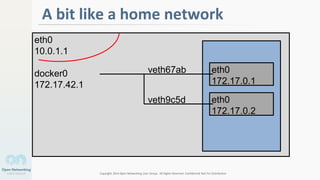
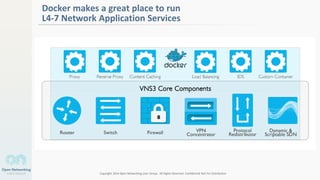
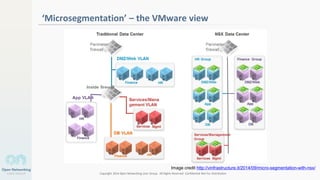
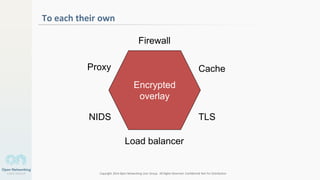
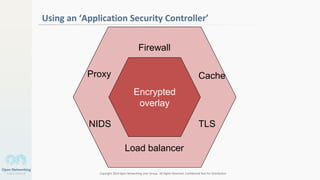
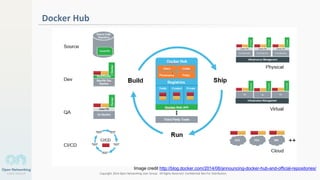
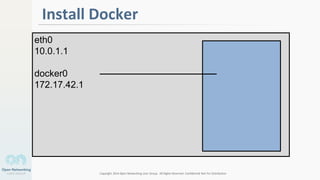
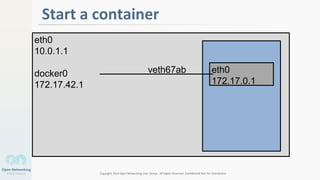
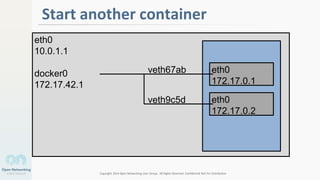
The document discusses container networking and network containment, focusing on the role of Docker and its default networking capabilities, including the docker0 bridge and iptables features. It highlights the shift towards application-centric networking for greater flexibility and cost-effectiveness in fine-grained network segregation. Additionally, it addresses the emergence of application security controllers as a means of managing network security in modern architectures.










![Copyright 2014 Open Networking User Group. All Rights Reserved Confidential Not For Distribution
2
From the docker command line
From the outside:
# start the database
sudo docker run -dp 3306:3306 --name todomvcdb
-v /data/mysql:/var/lib/mysql cpswan/todomvc.mysql
# start the app server
sudo docker run -dp 4567:4567 --name todomvcapp
--link todomvcdb:db cpswan/todomvc.sinatra
On the inside:
dburl = 'mysql://root:pa55Word@' + ENV['DB_PORT_3306_TCP_ADDR'] +
'/todomvc'
DataMapper.setup(:default, dburl)](https://image.slidesharecdn.com/onugcontainernetworks-150121105610-conversion-gate02/85/Chris-Swan-s-ONUG-NYC-talk-Container-Networks-20-320.jpg)
![Copyright 2014 Open Networking User Group. All Rights Reserved Confidential Not For Distribution
2
Simplify life with Fig
fig.yml:
todomvcdb:
image: cpswan/todomvc.mysql
expose:
- "3306"
volumes:
- /data/mysql:/var/lib/mysql
todomvcapp:
image: cpswan/todomvc.sinatra
ports:
- "4567:4567"
links:
- todomvcdb:db
I still need this on the inside:
dburl = 'mysql://root:pa55Word@' + ENV['DB_PORT_3306_TCP_ADDR'] +
'/todomvc'
DataMapper.setup(:default, dburl)](https://image.slidesharecdn.com/onugcontainernetworks-150121105610-conversion-gate02/85/Chris-Swan-s-ONUG-NYC-talk-Container-Networks-21-320.jpg)