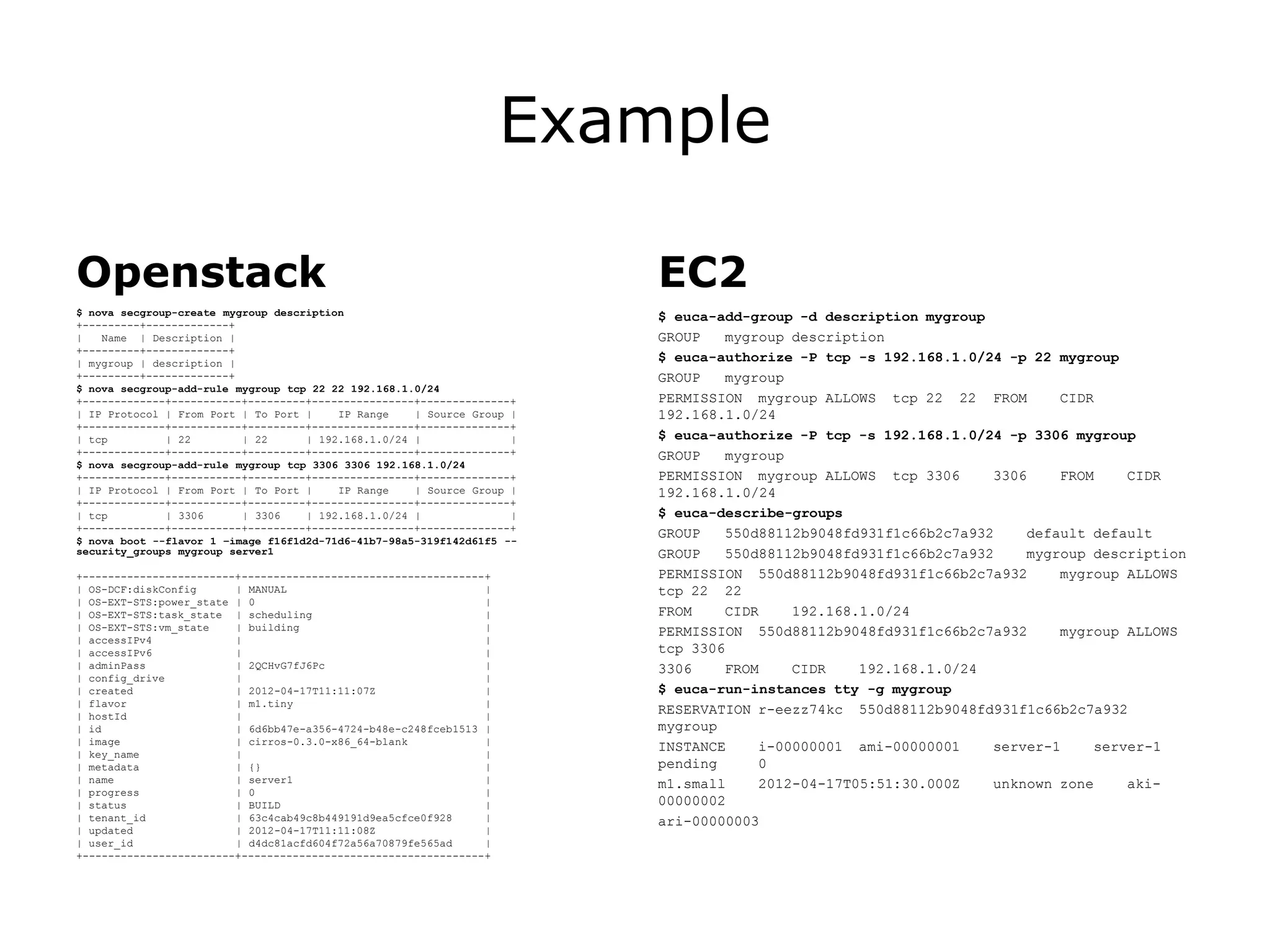
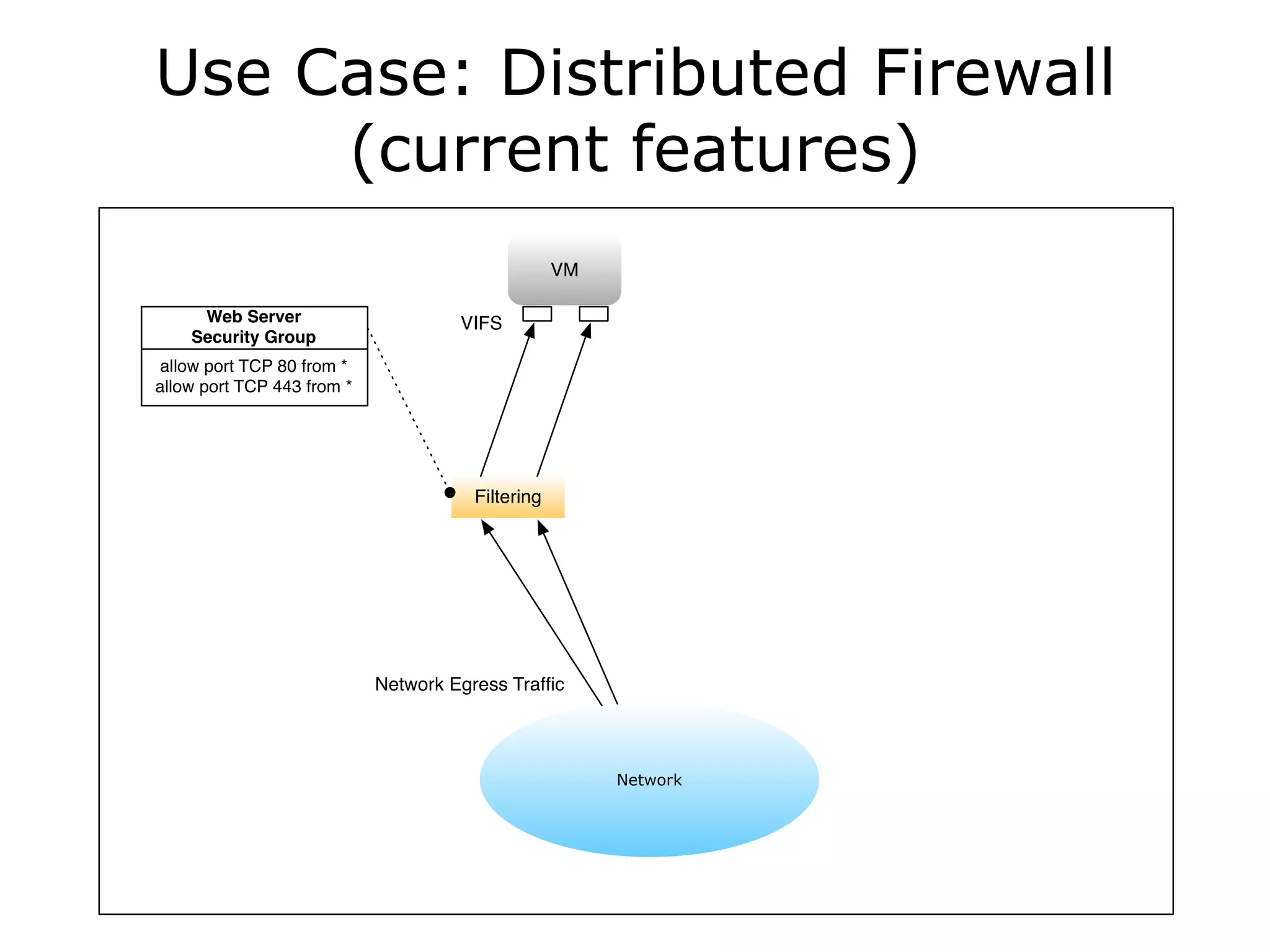
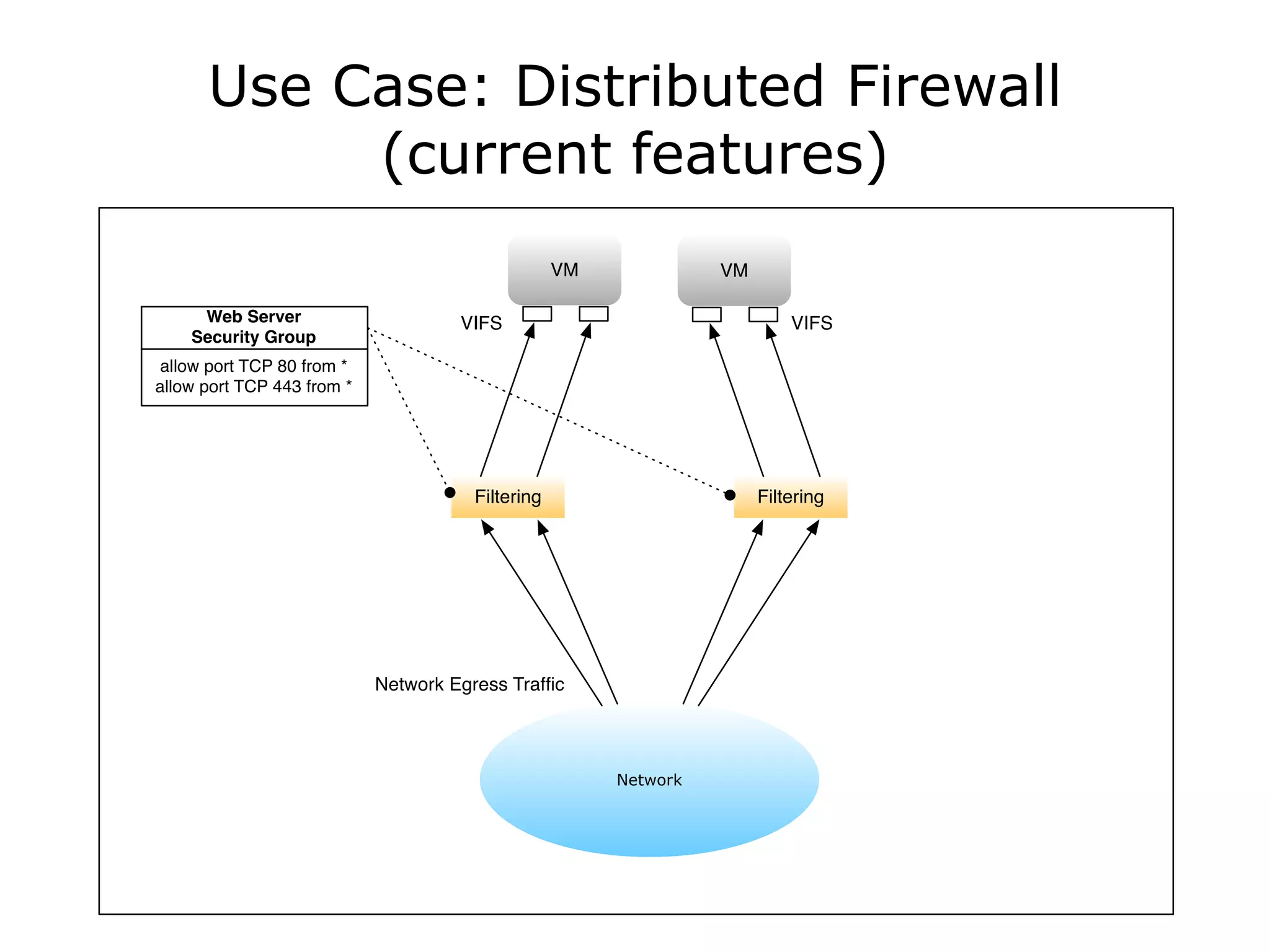
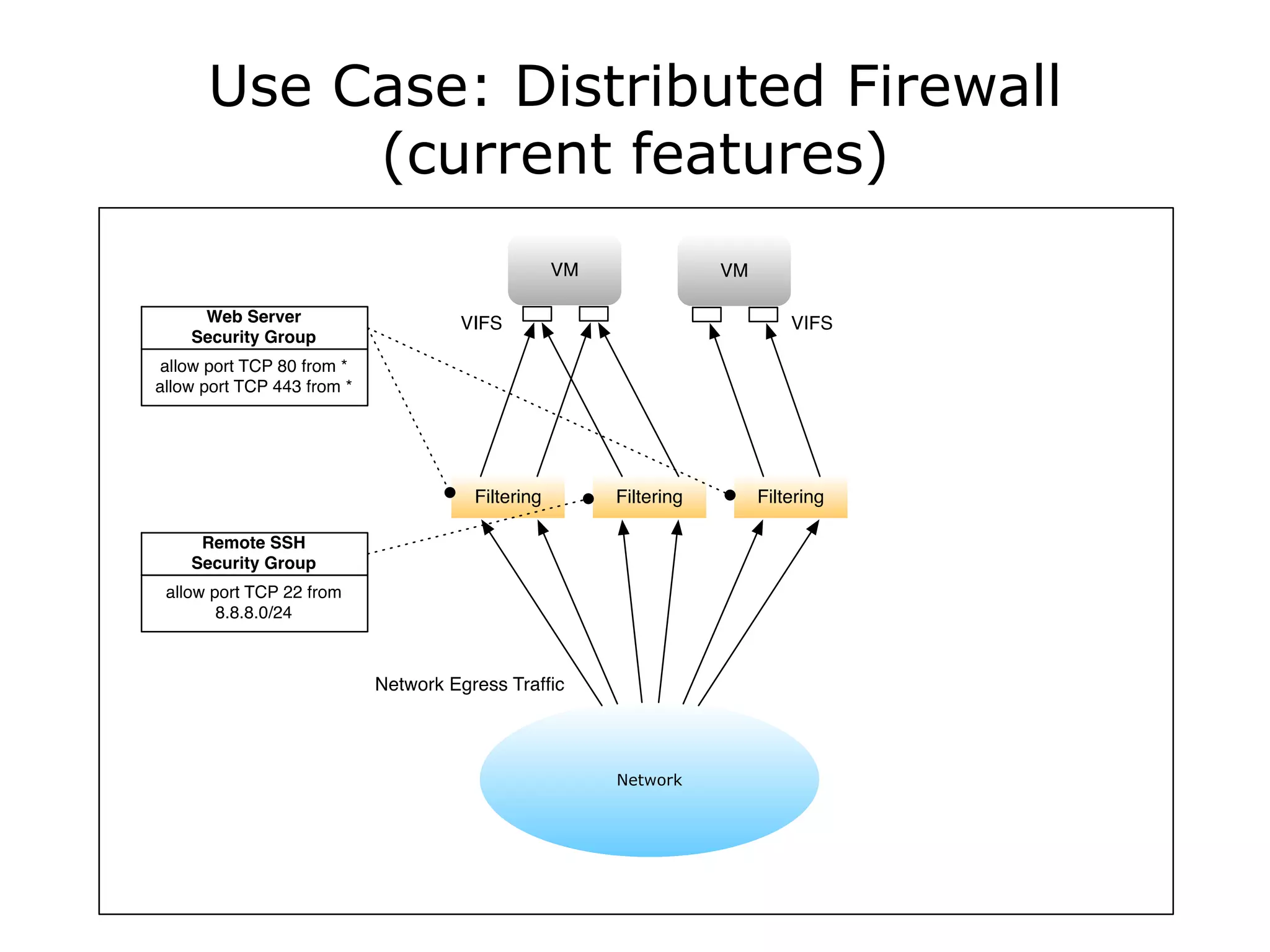
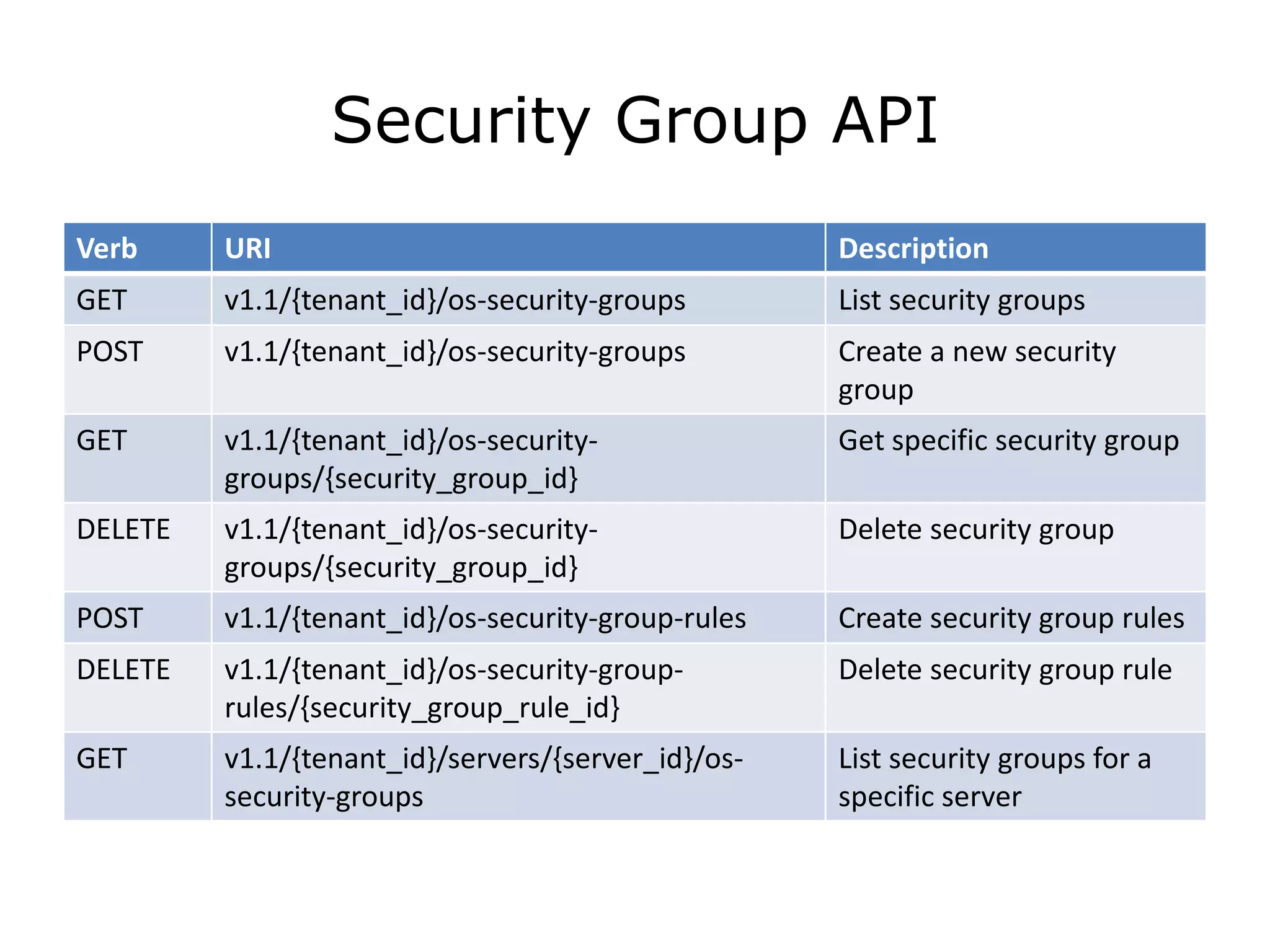
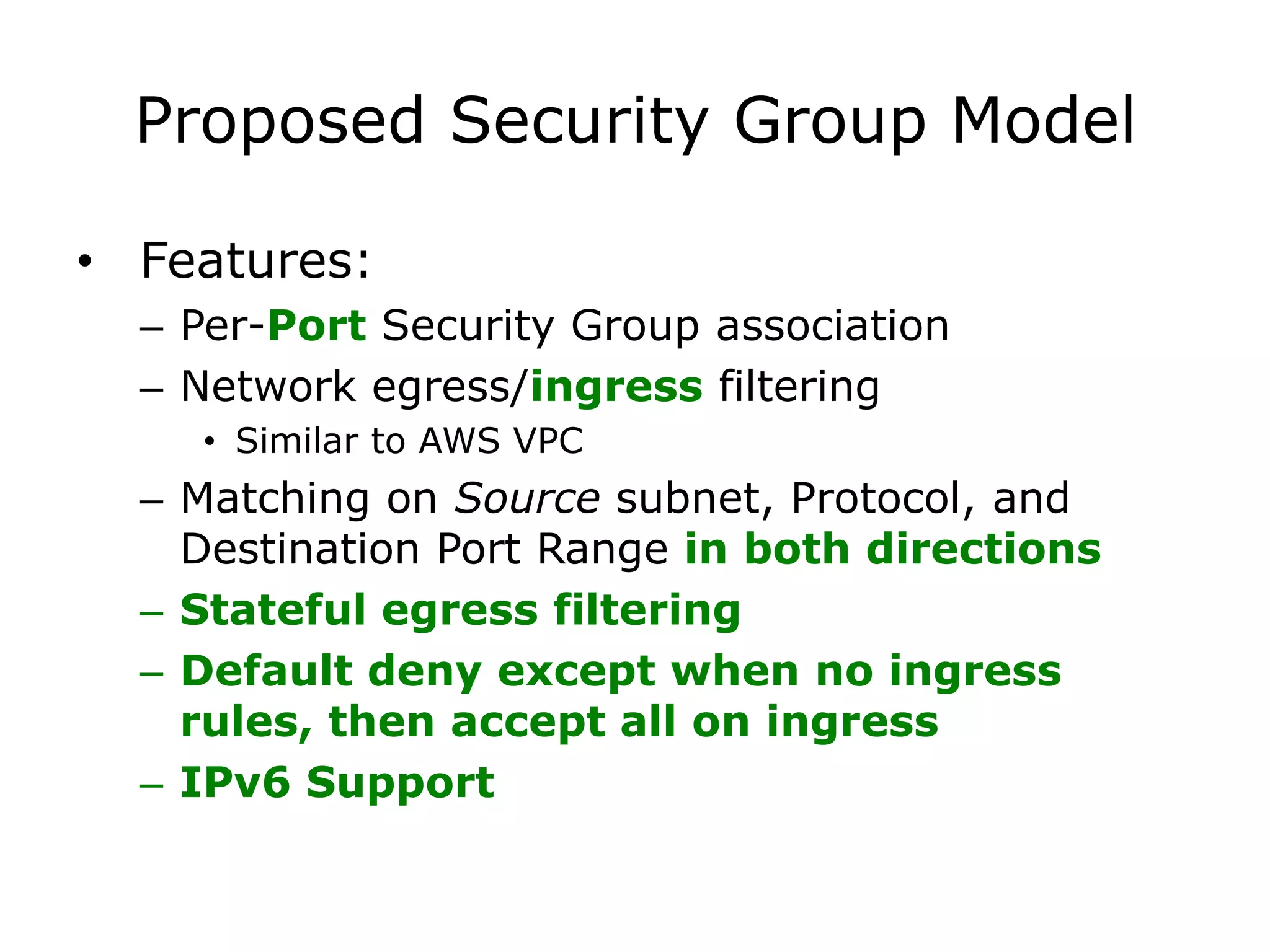
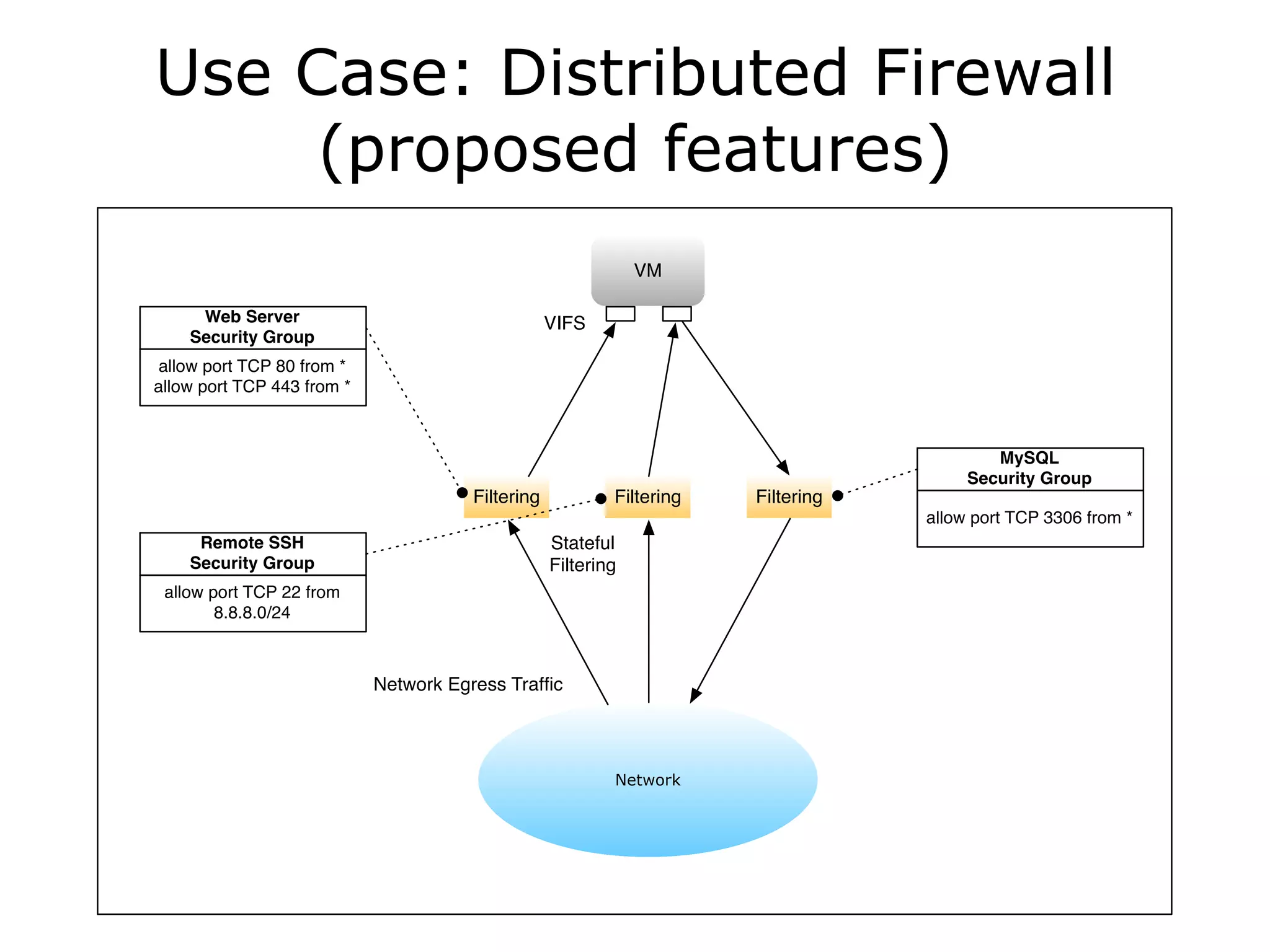
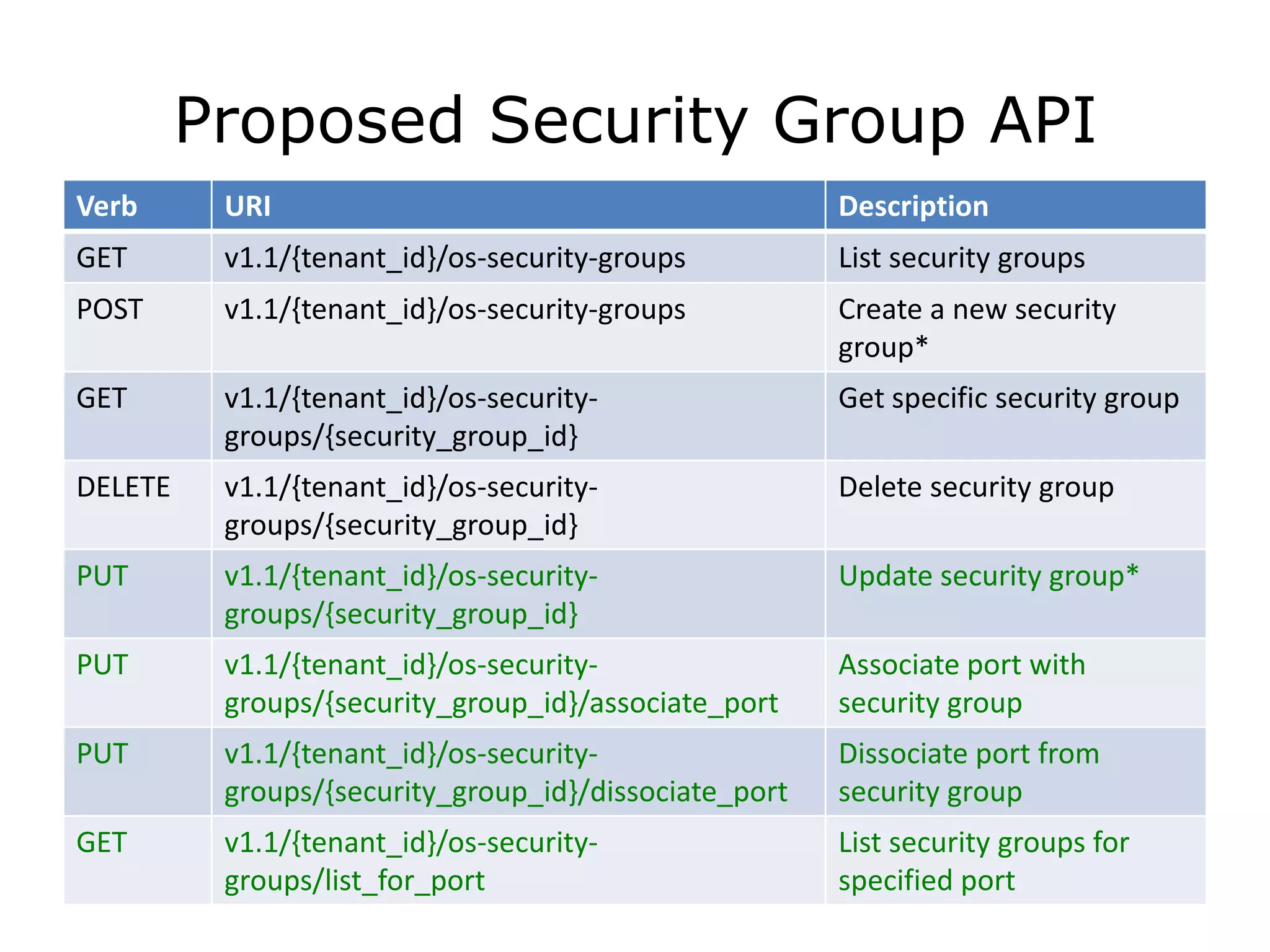
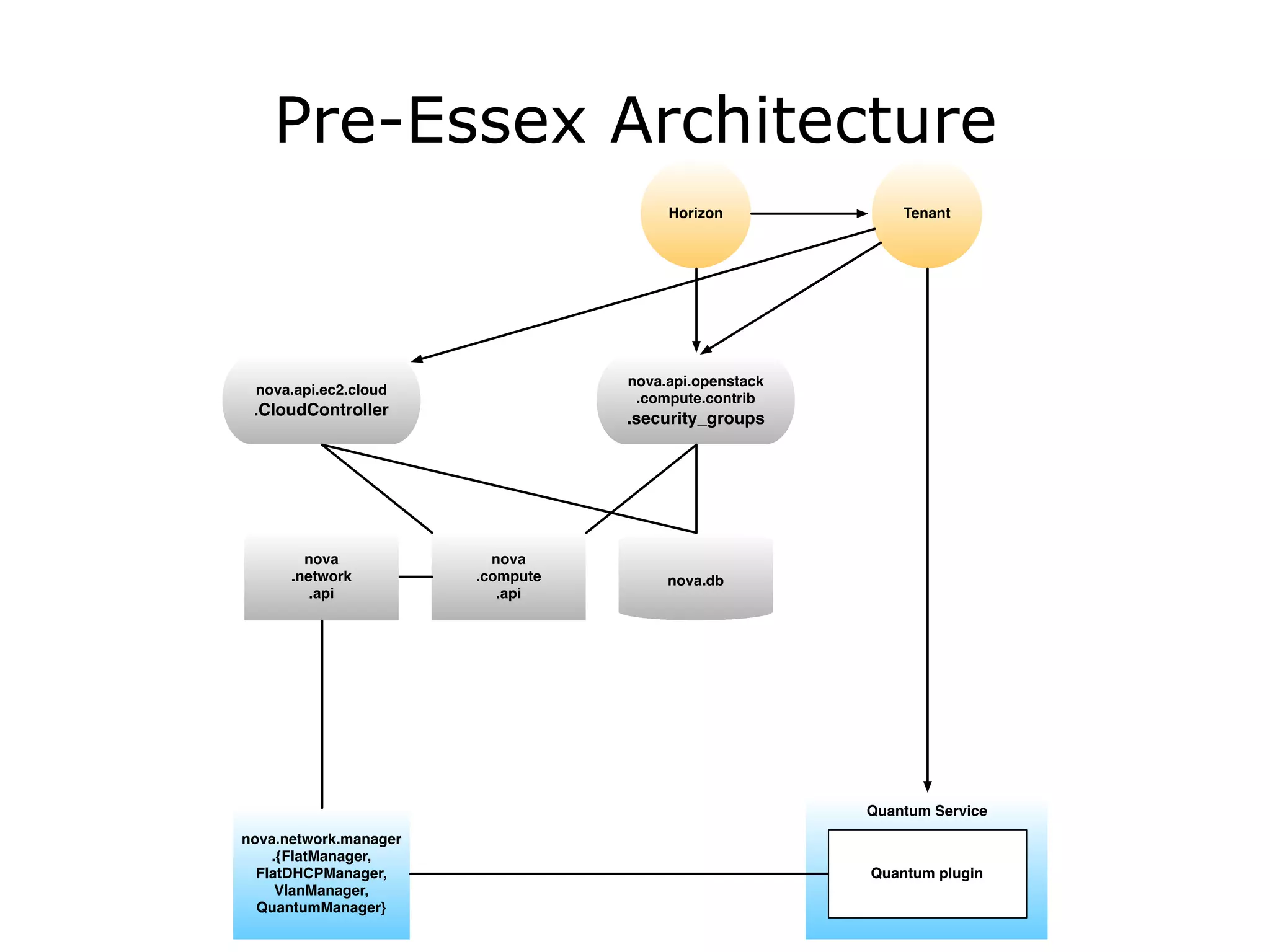
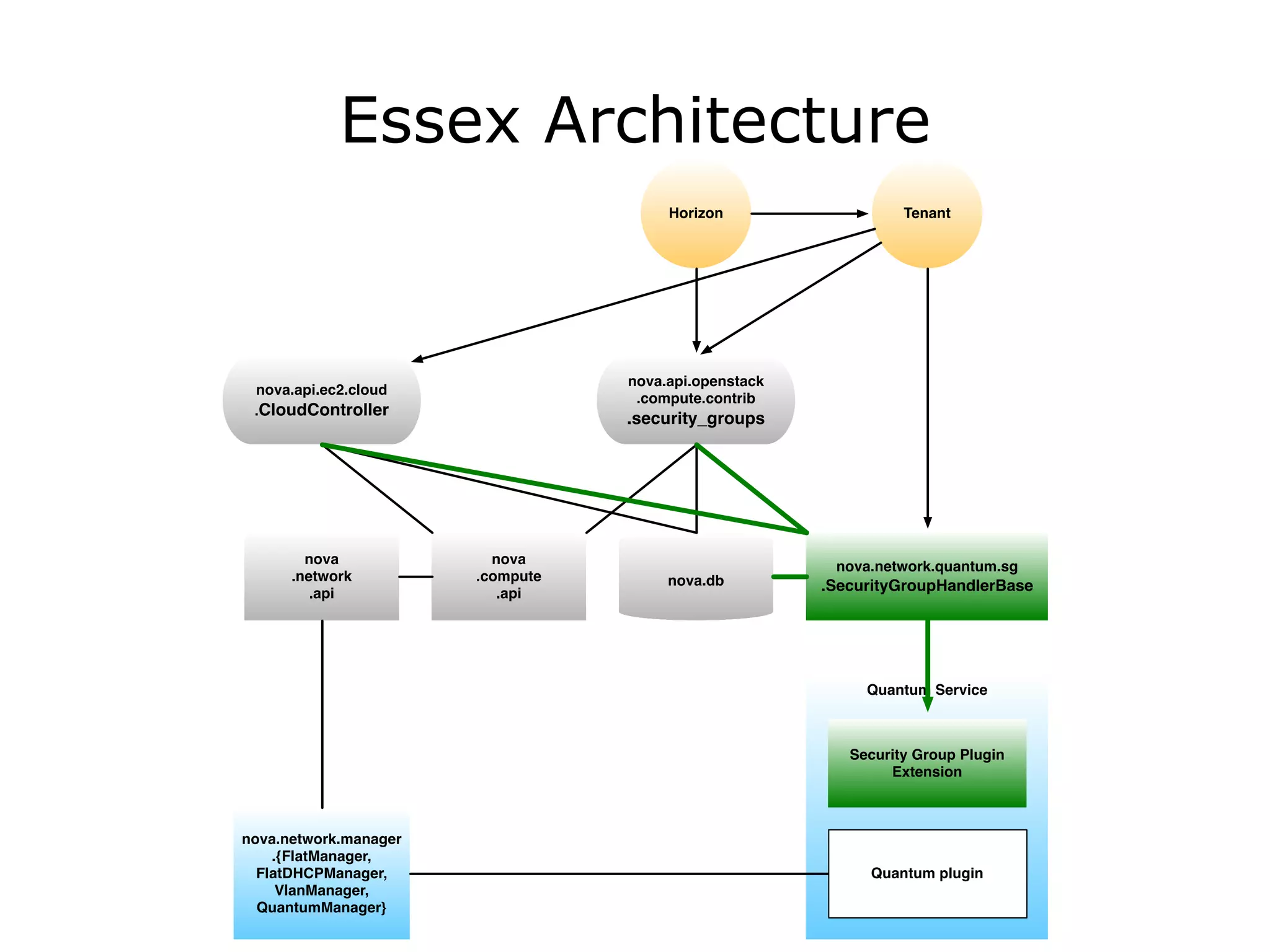
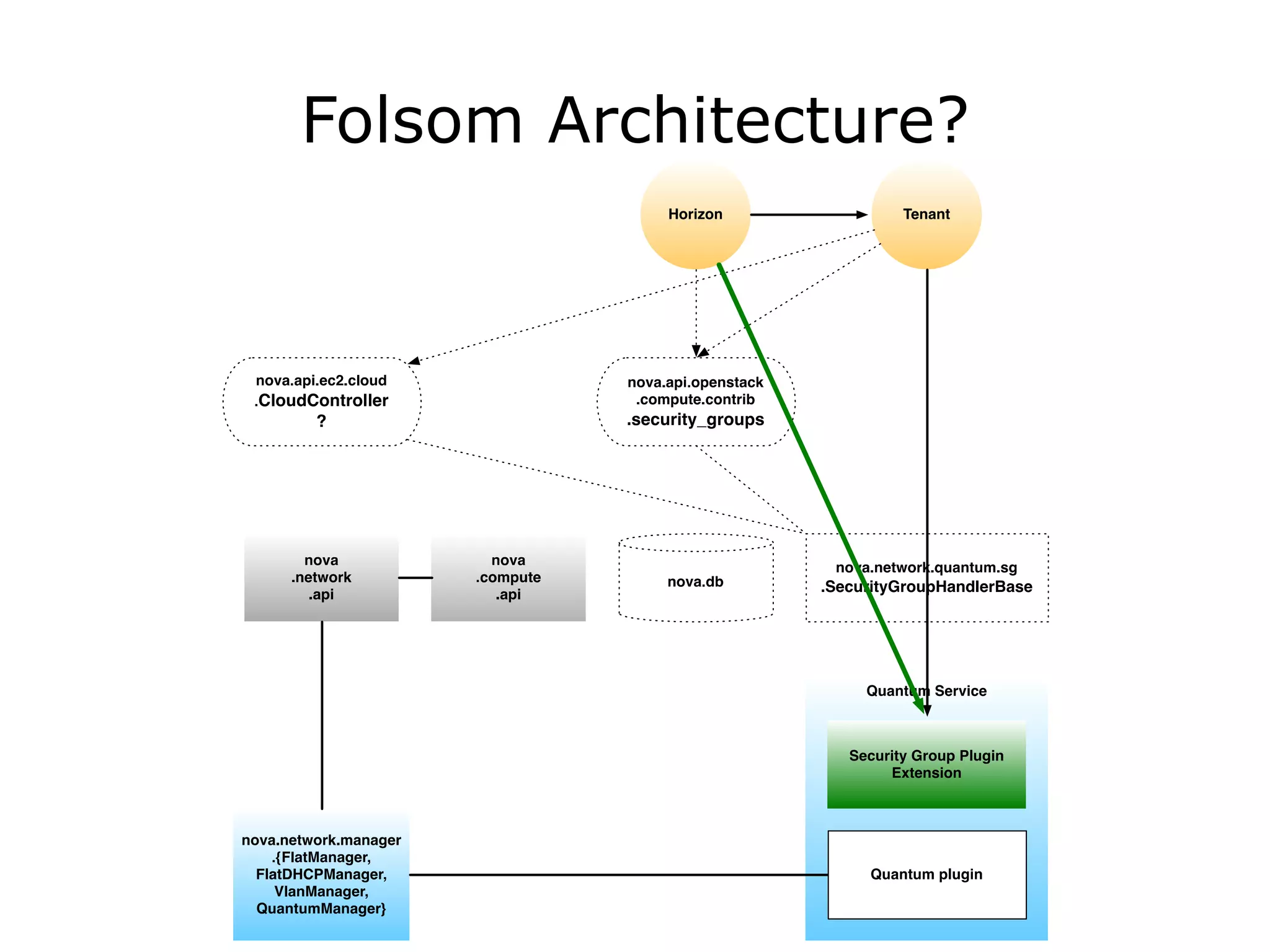
The document discusses the proposal to transition security groups from Nova to Quantum within the OpenStack framework, highlighting the differences and improvements in security group features and APIs. Key points include the current model's limitations, proposed enhancements for firewall capabilities, and the introduction of per-port security group associations. The session aims to facilitate a discussion on access control lists, provider firewalling, and user modifications to security groups.