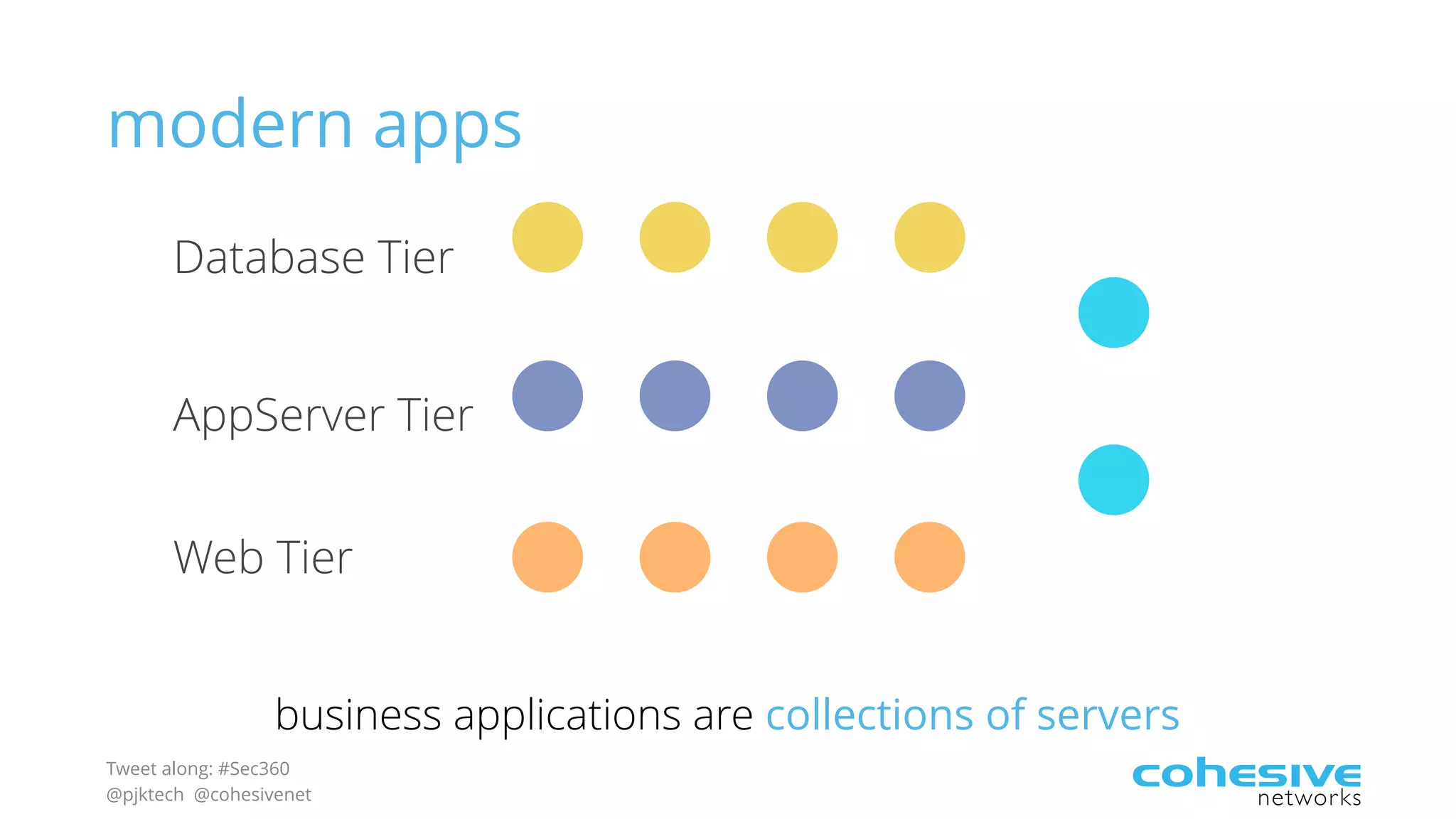
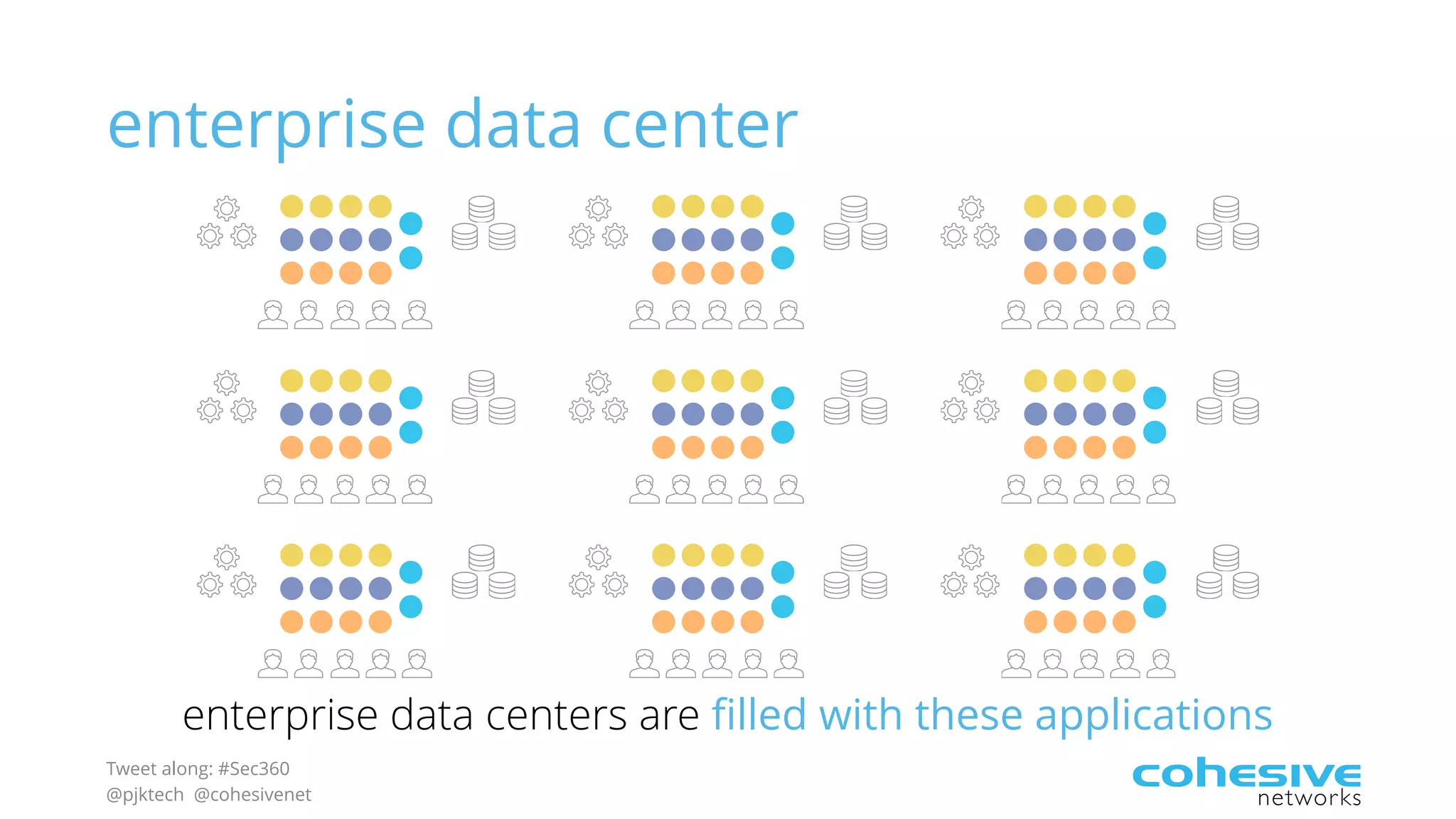
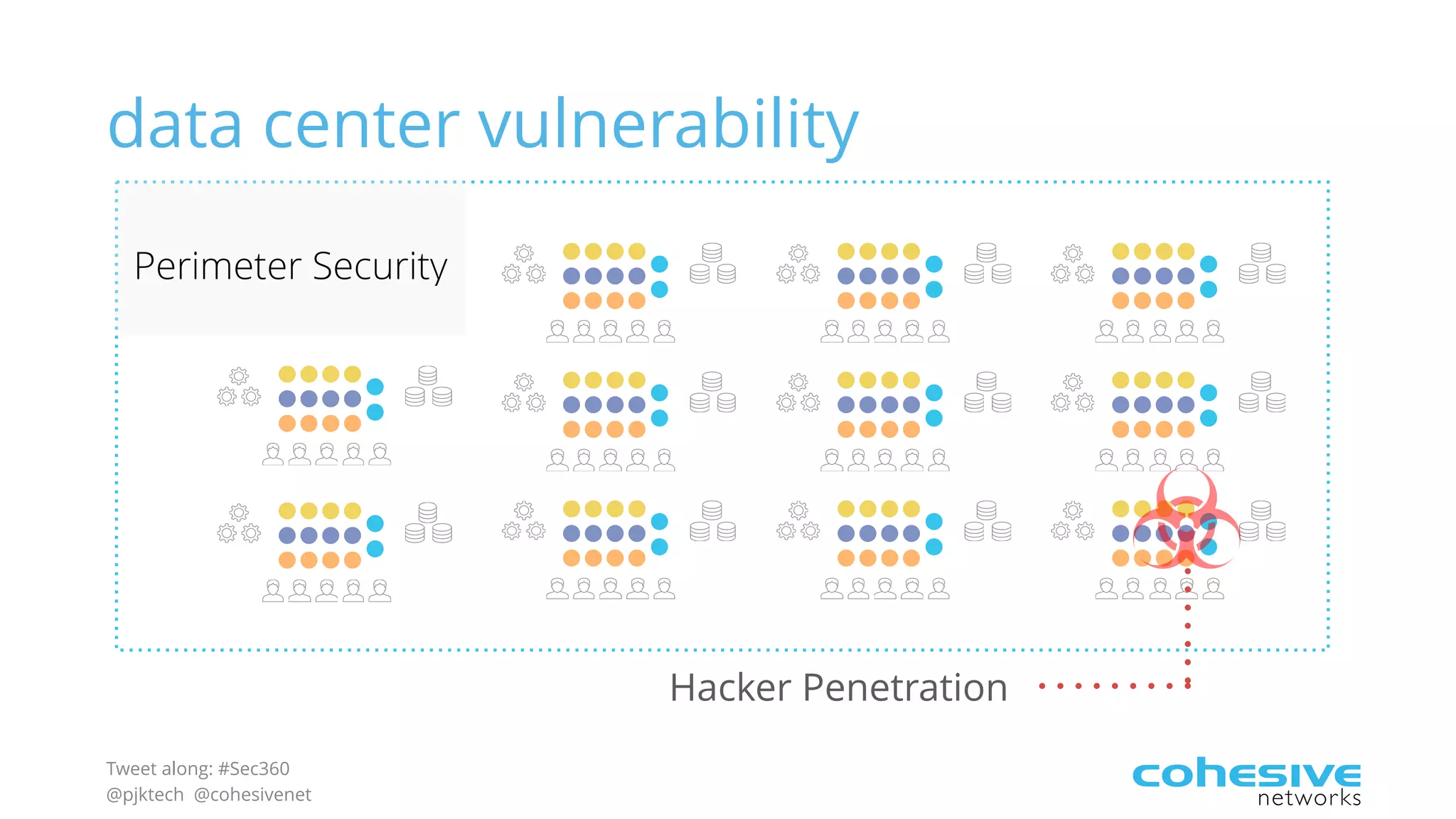
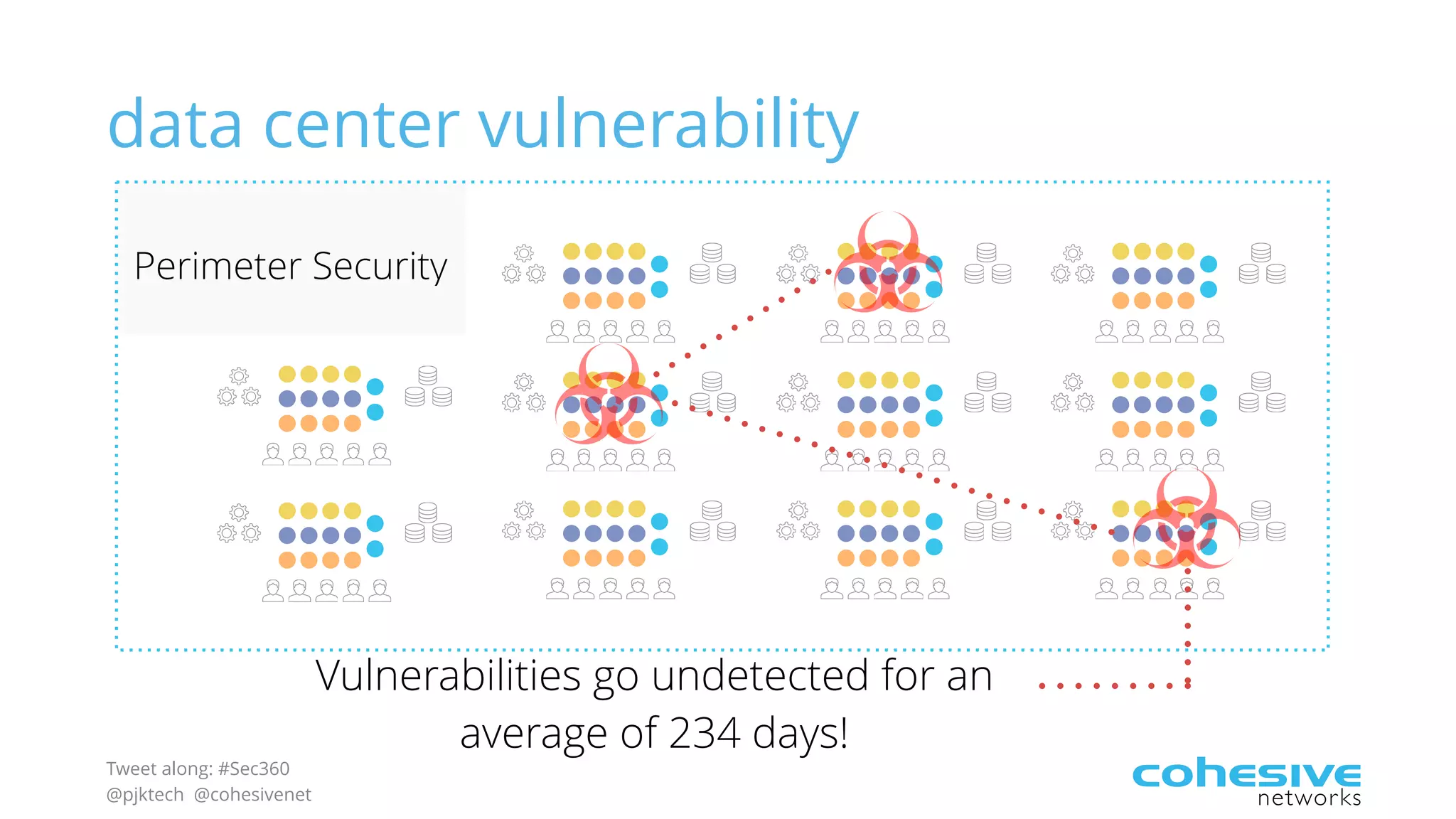
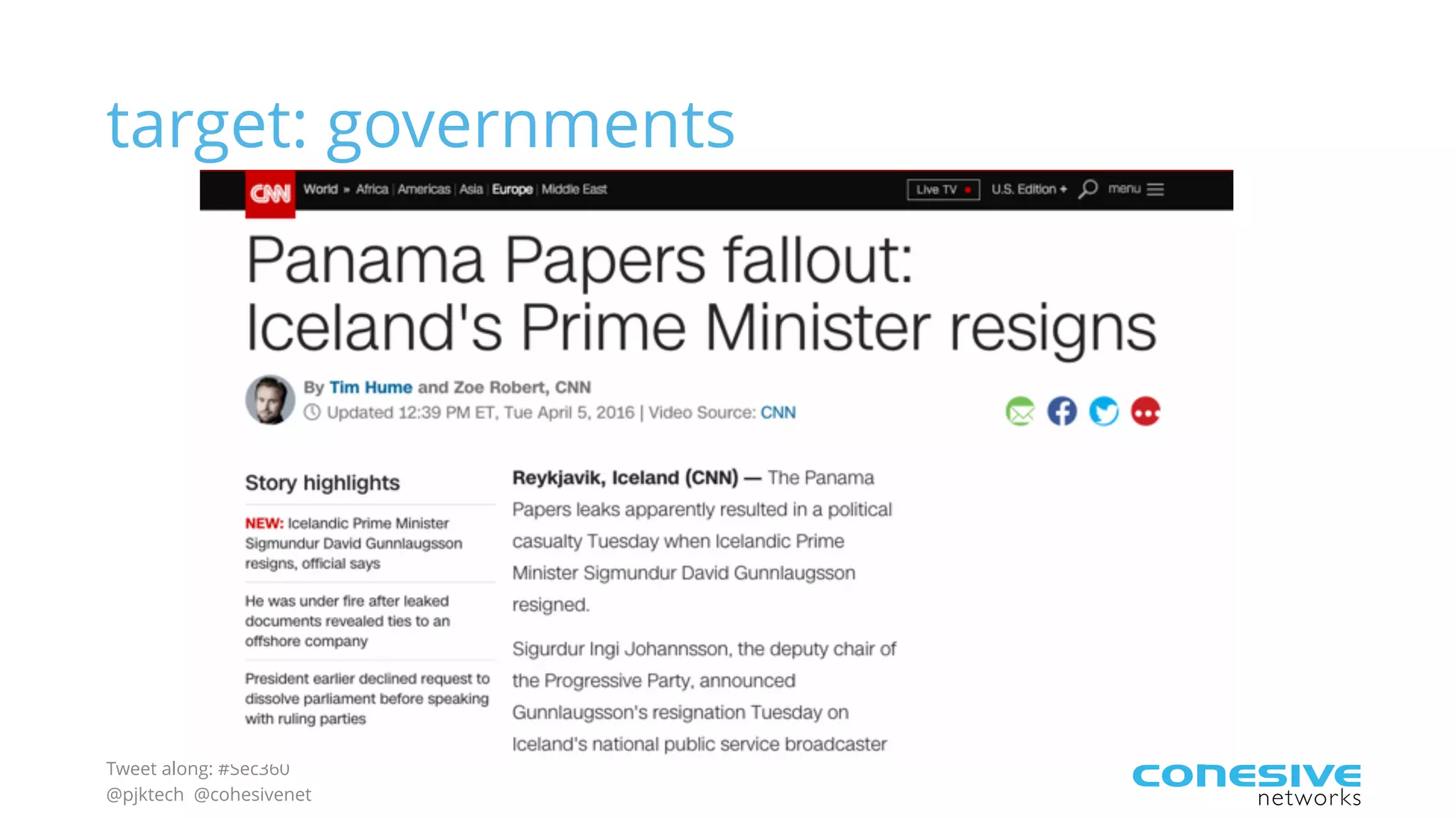
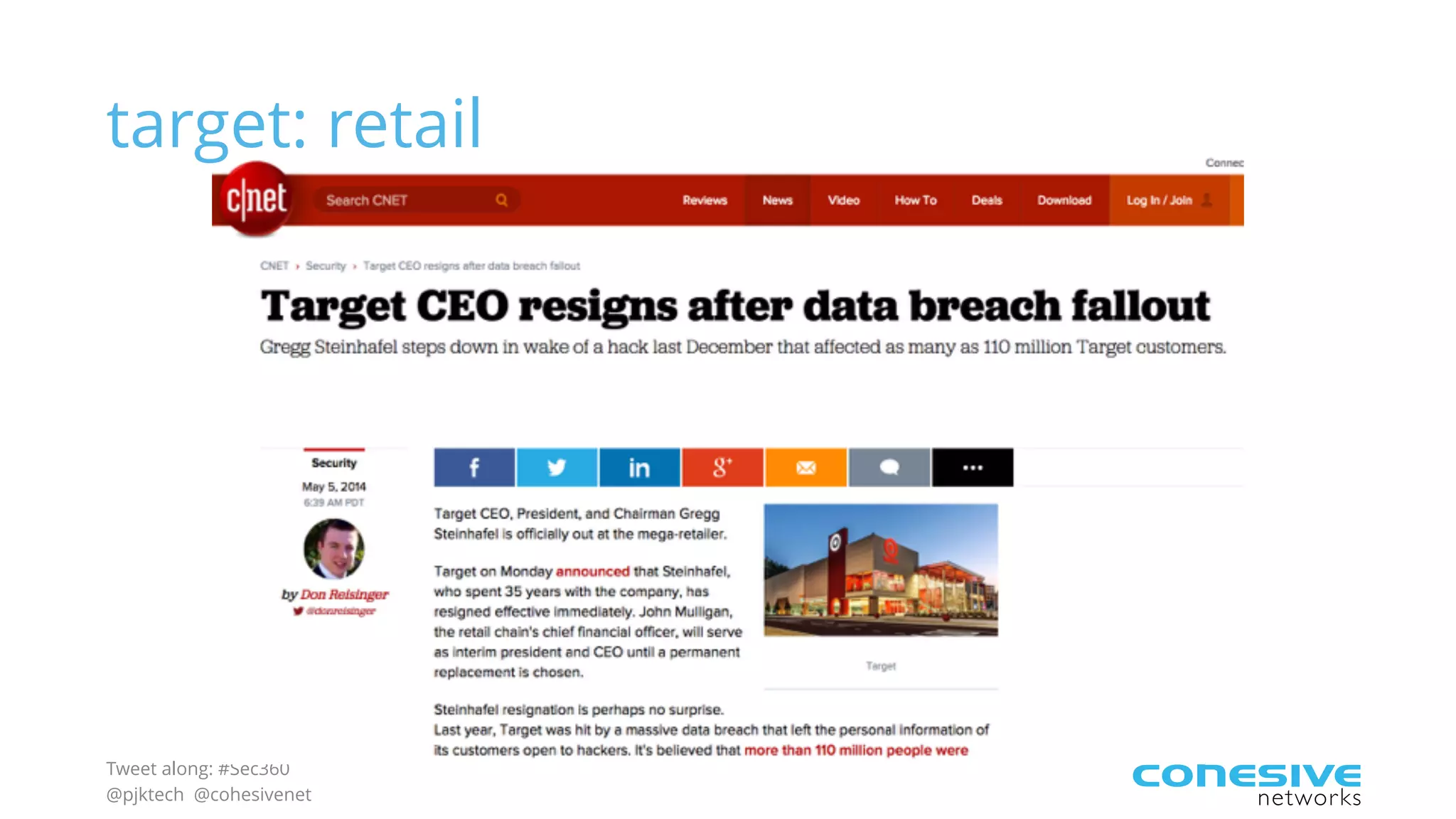
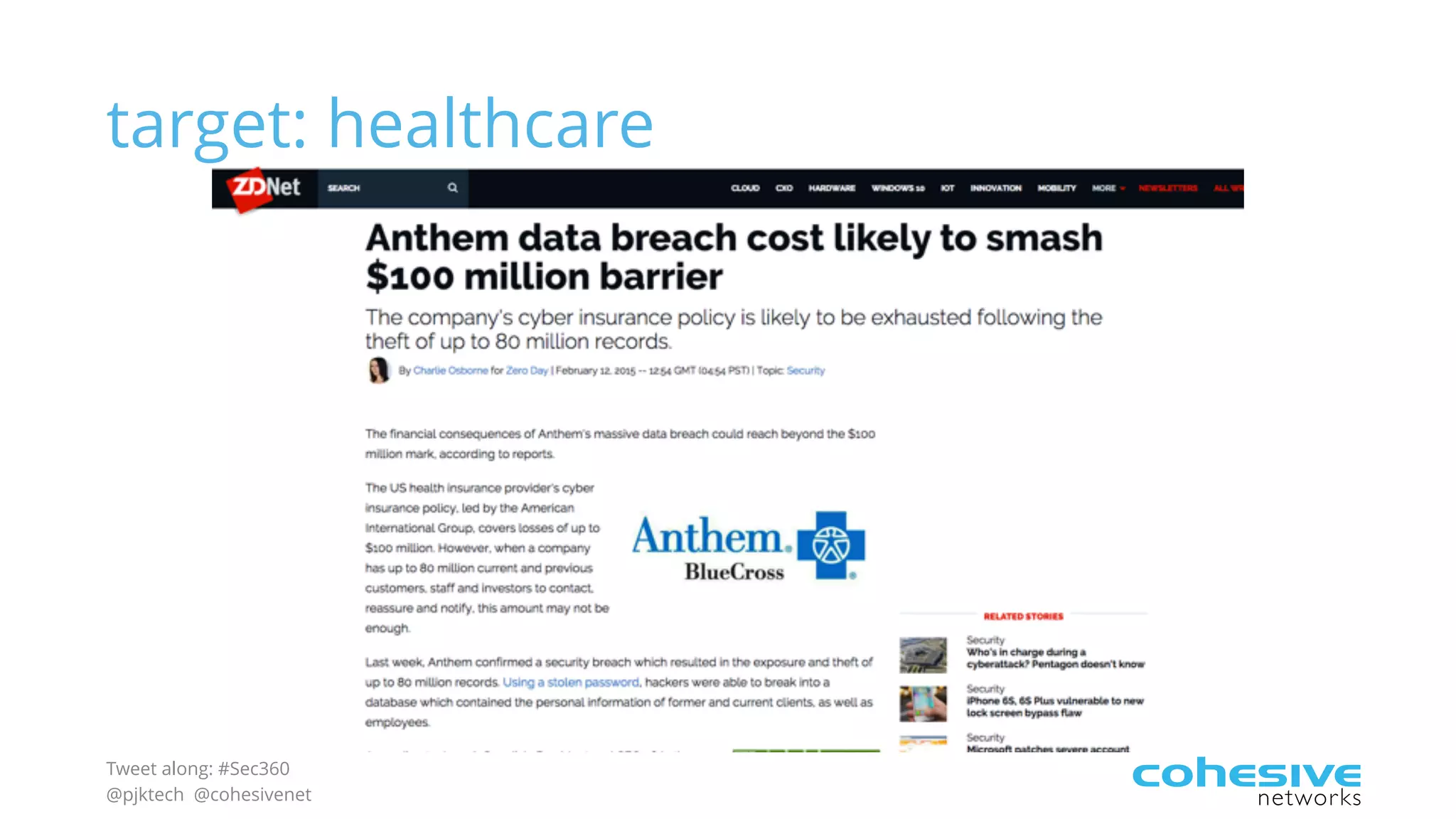
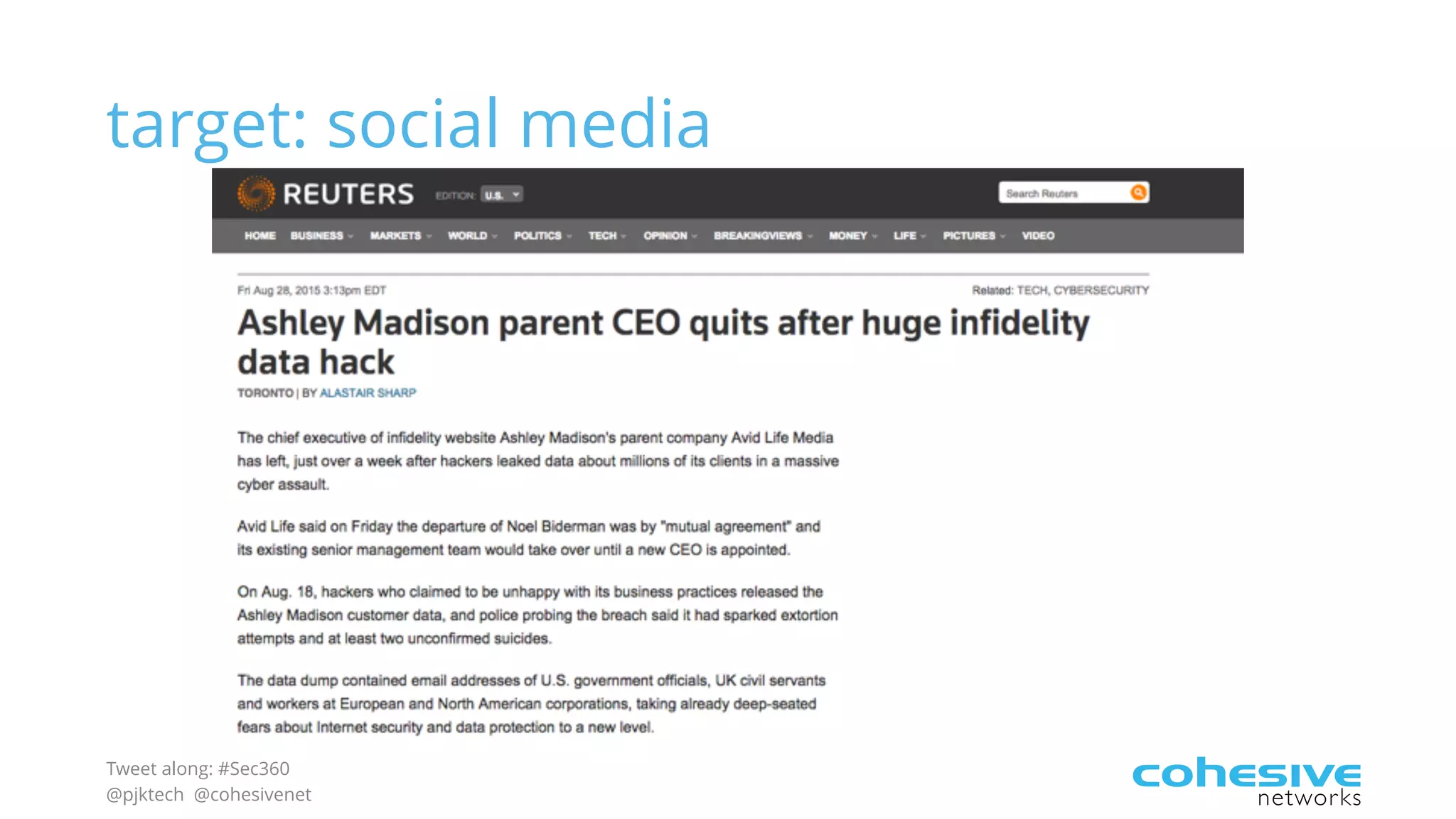
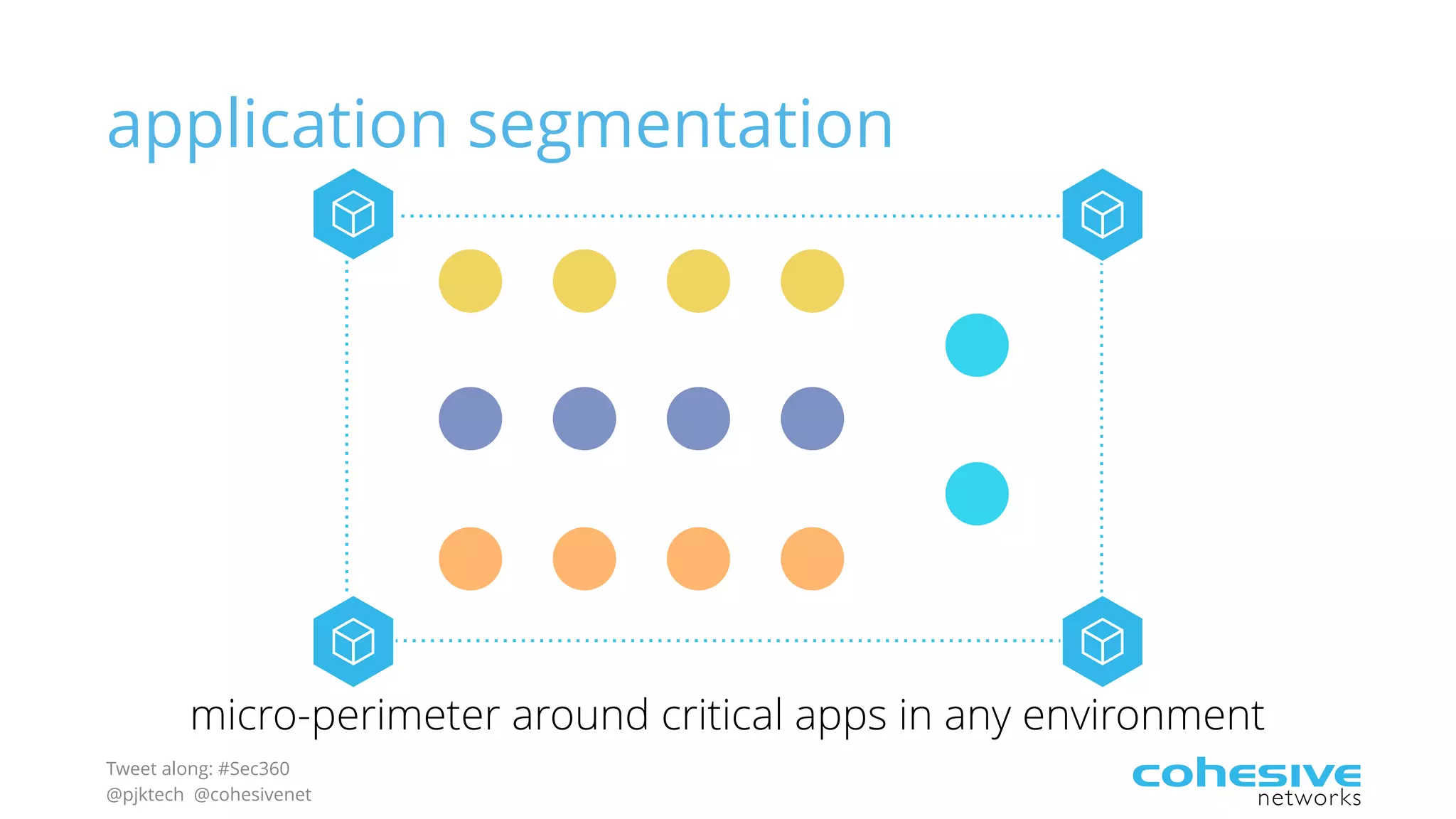
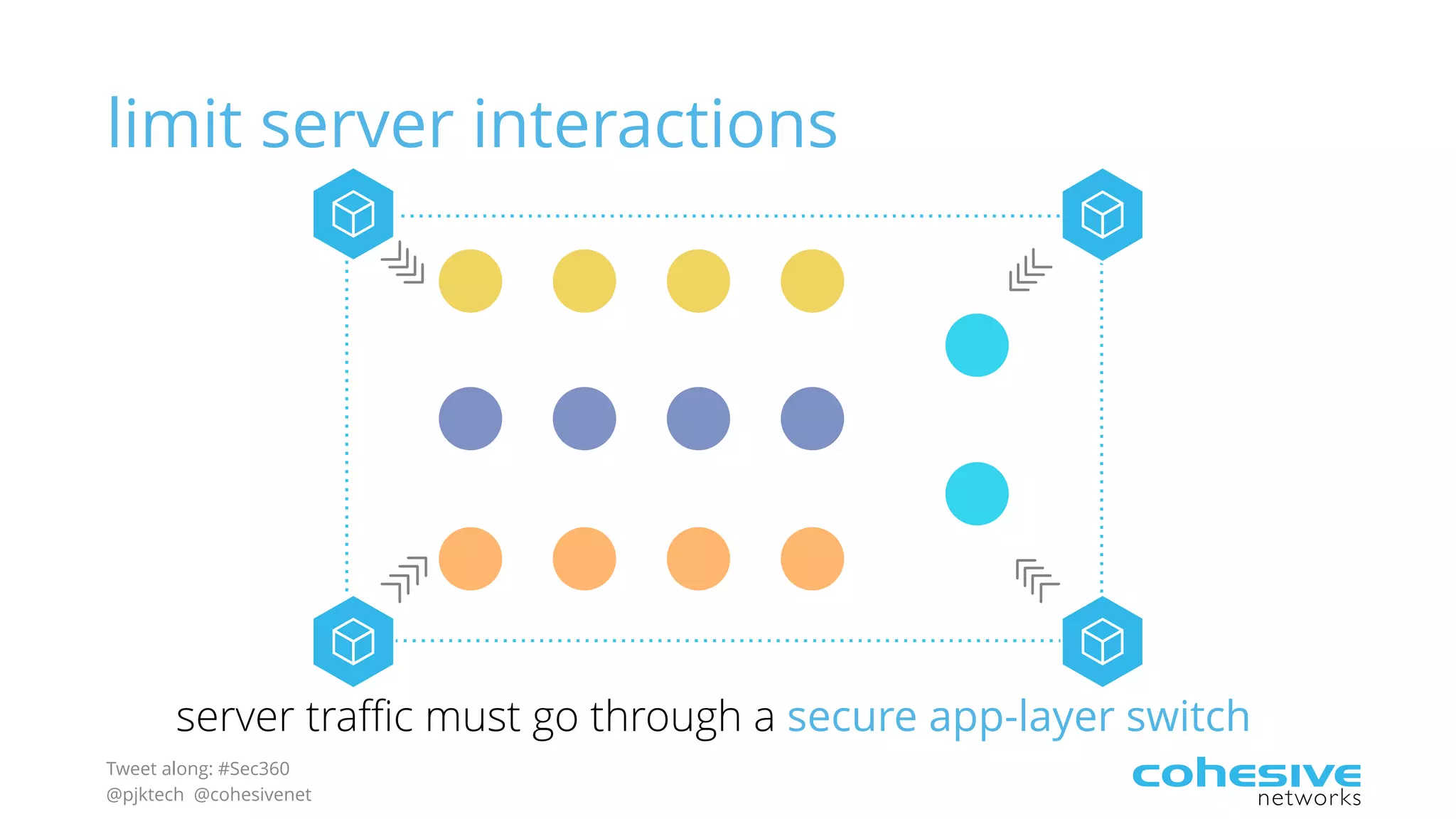
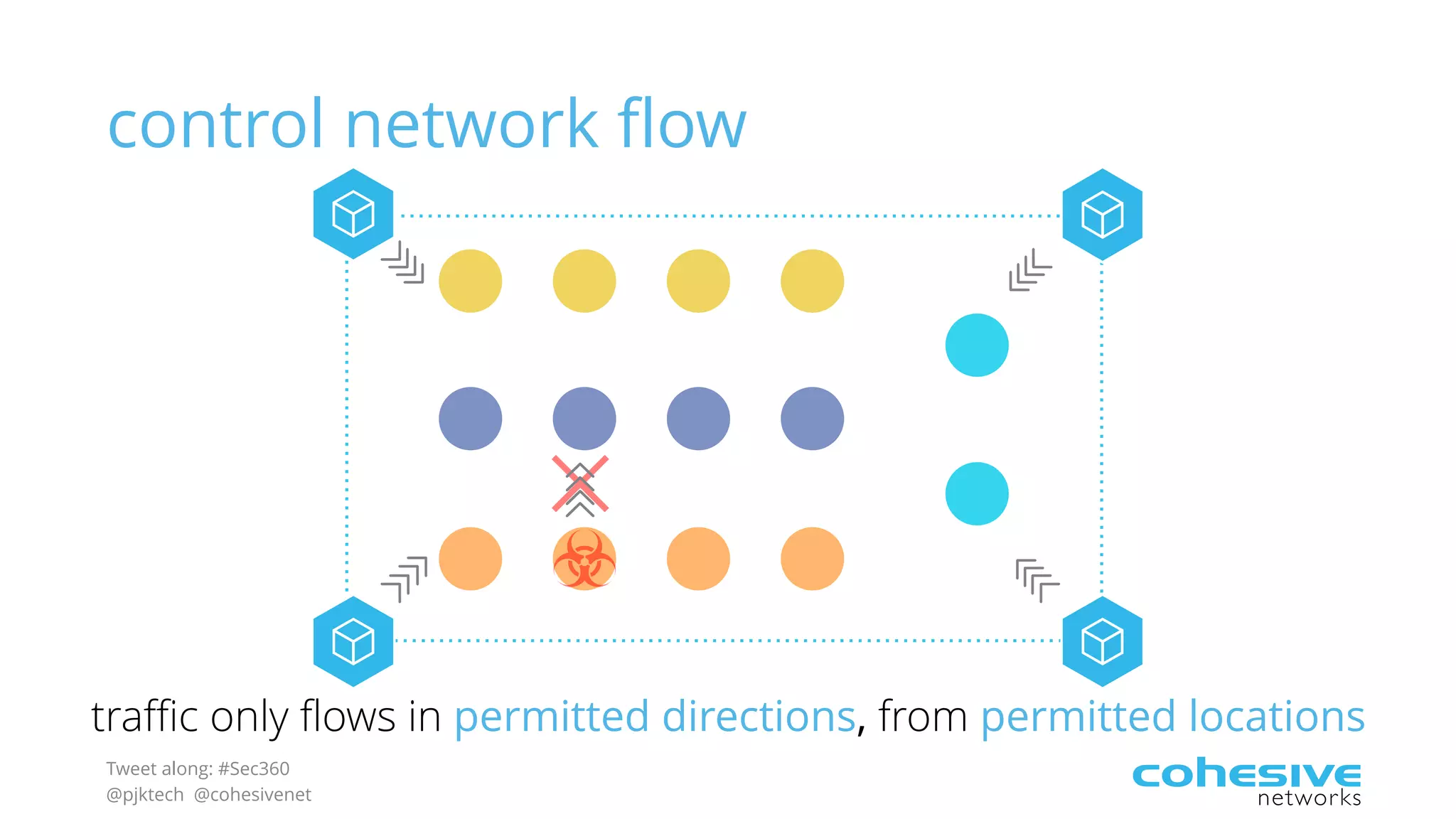
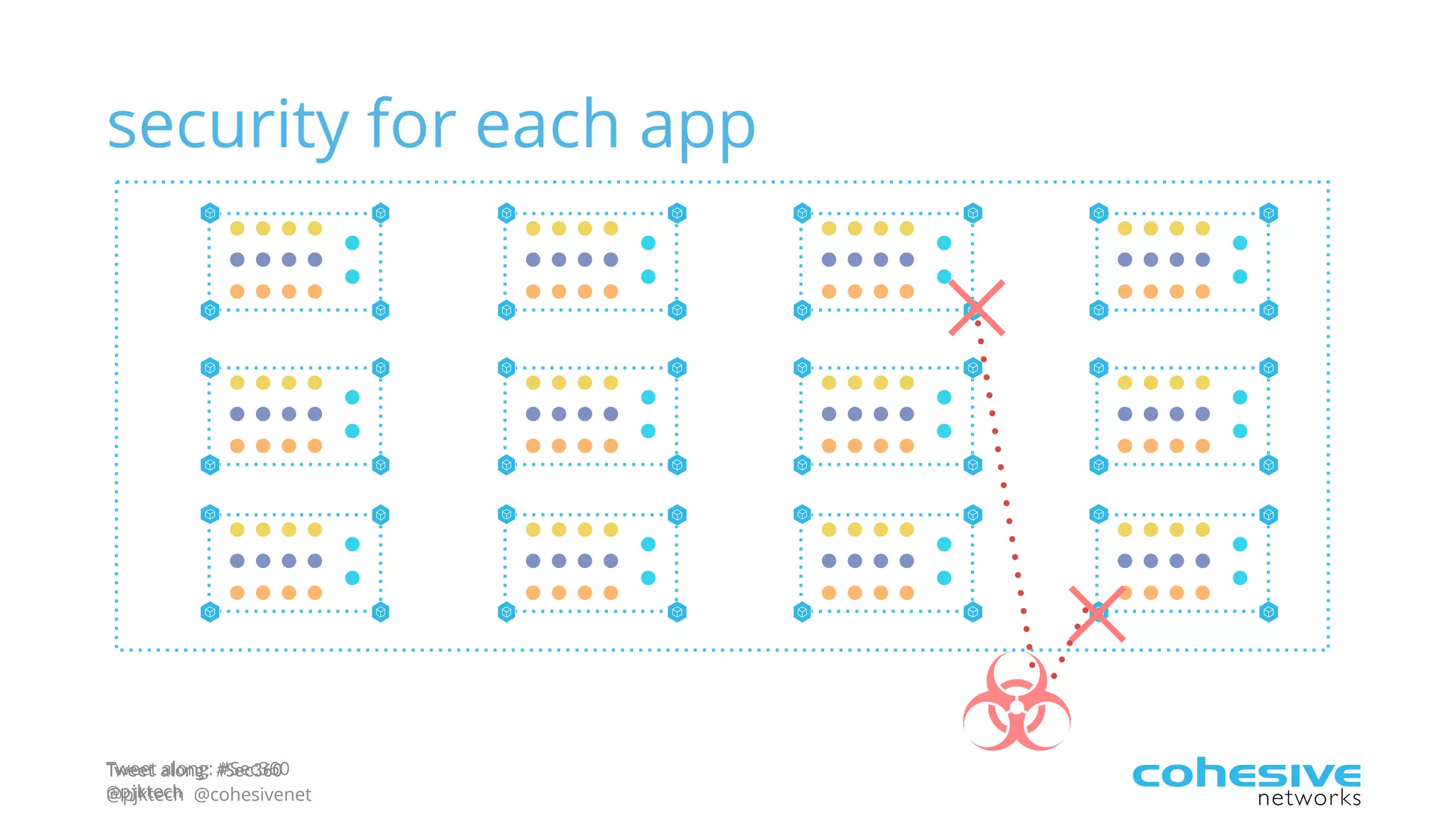
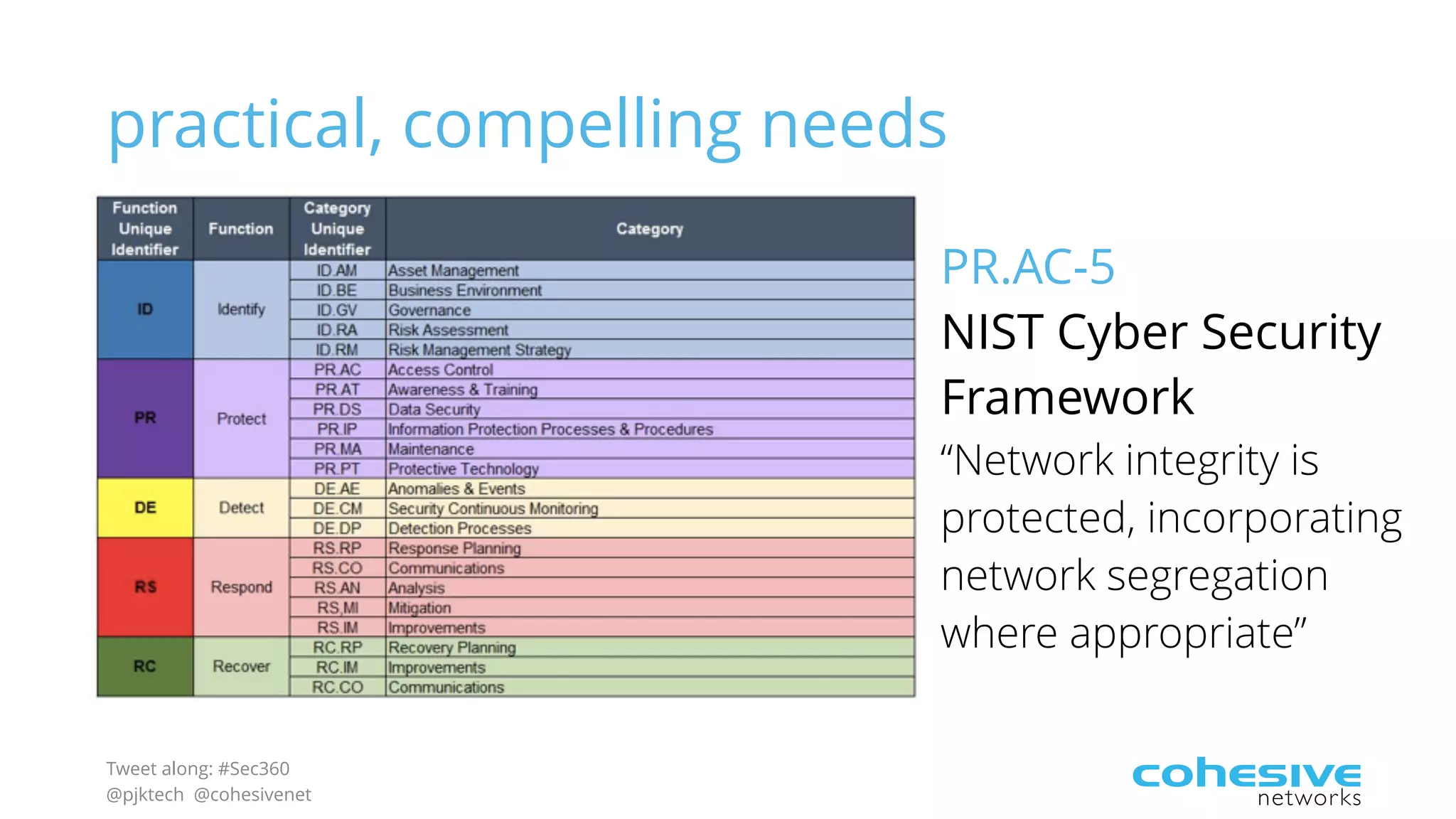
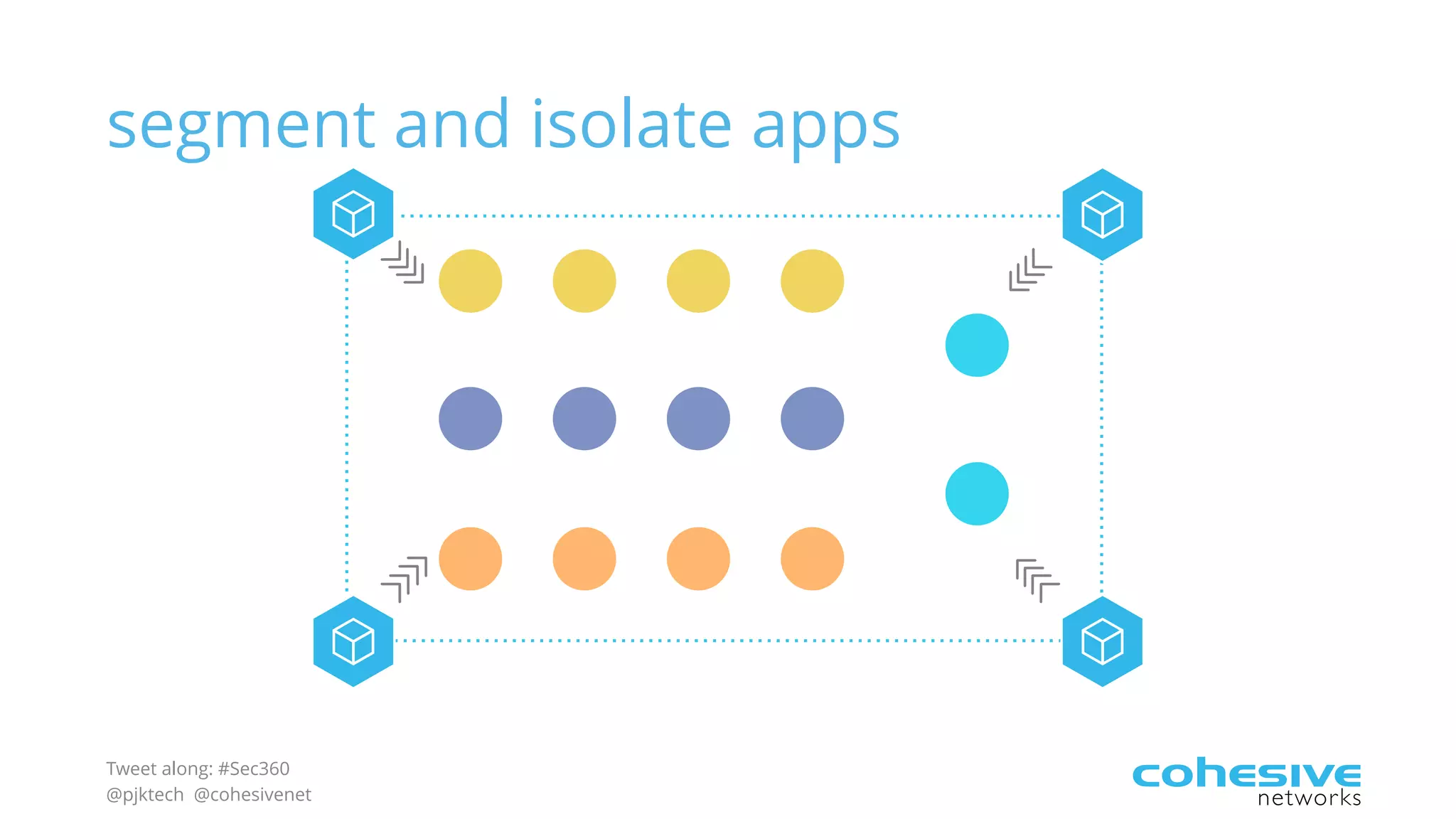
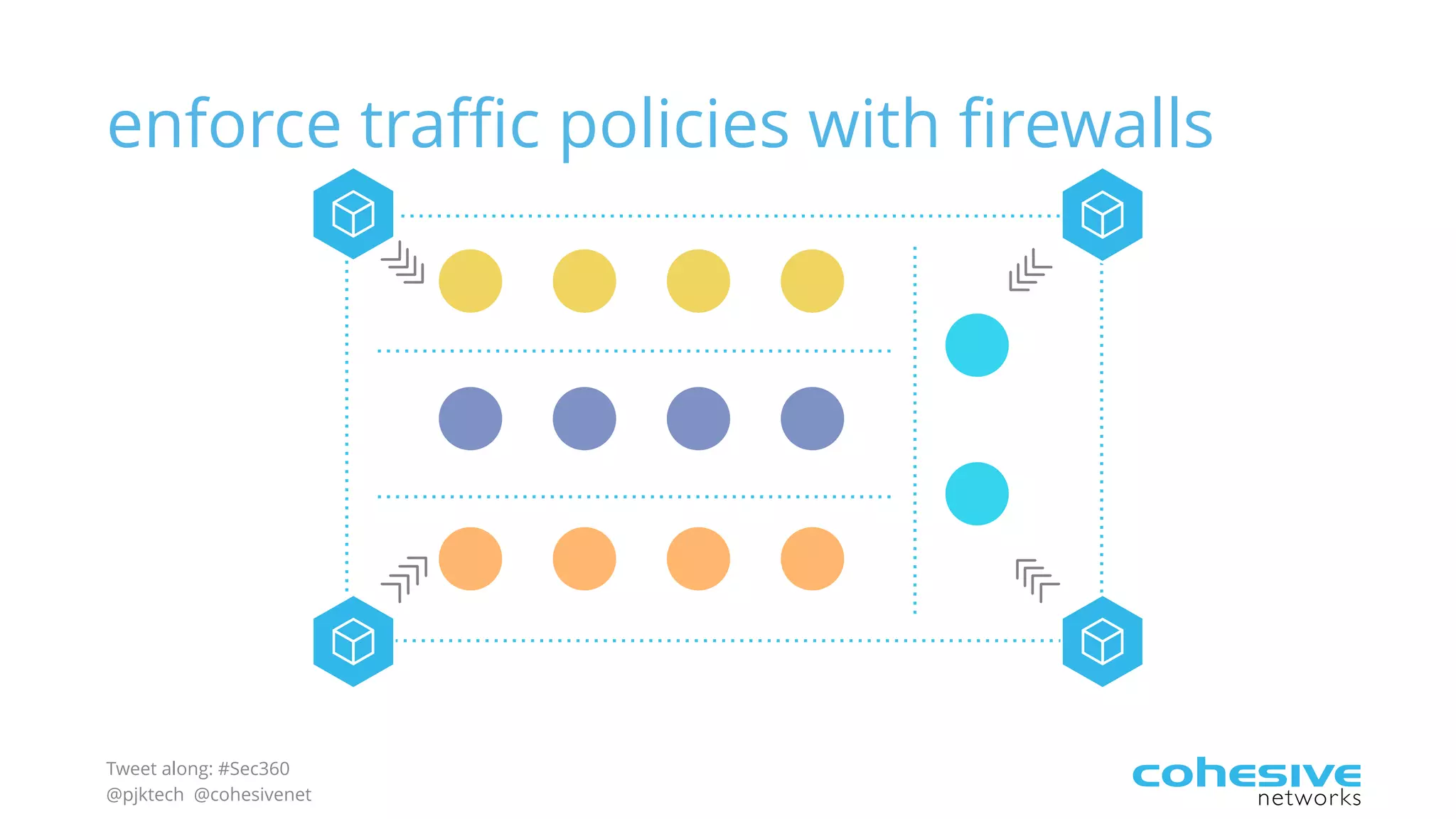
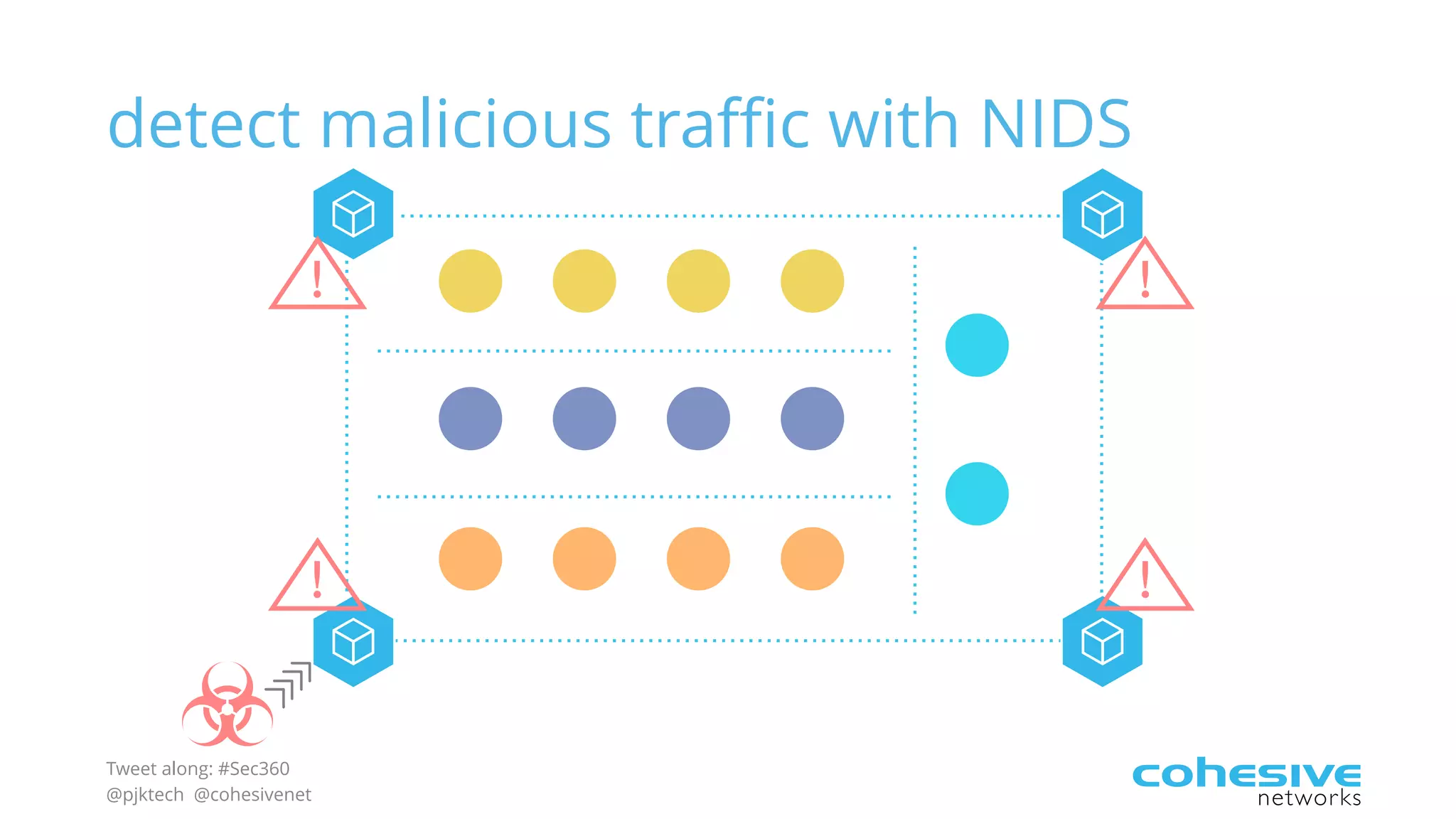
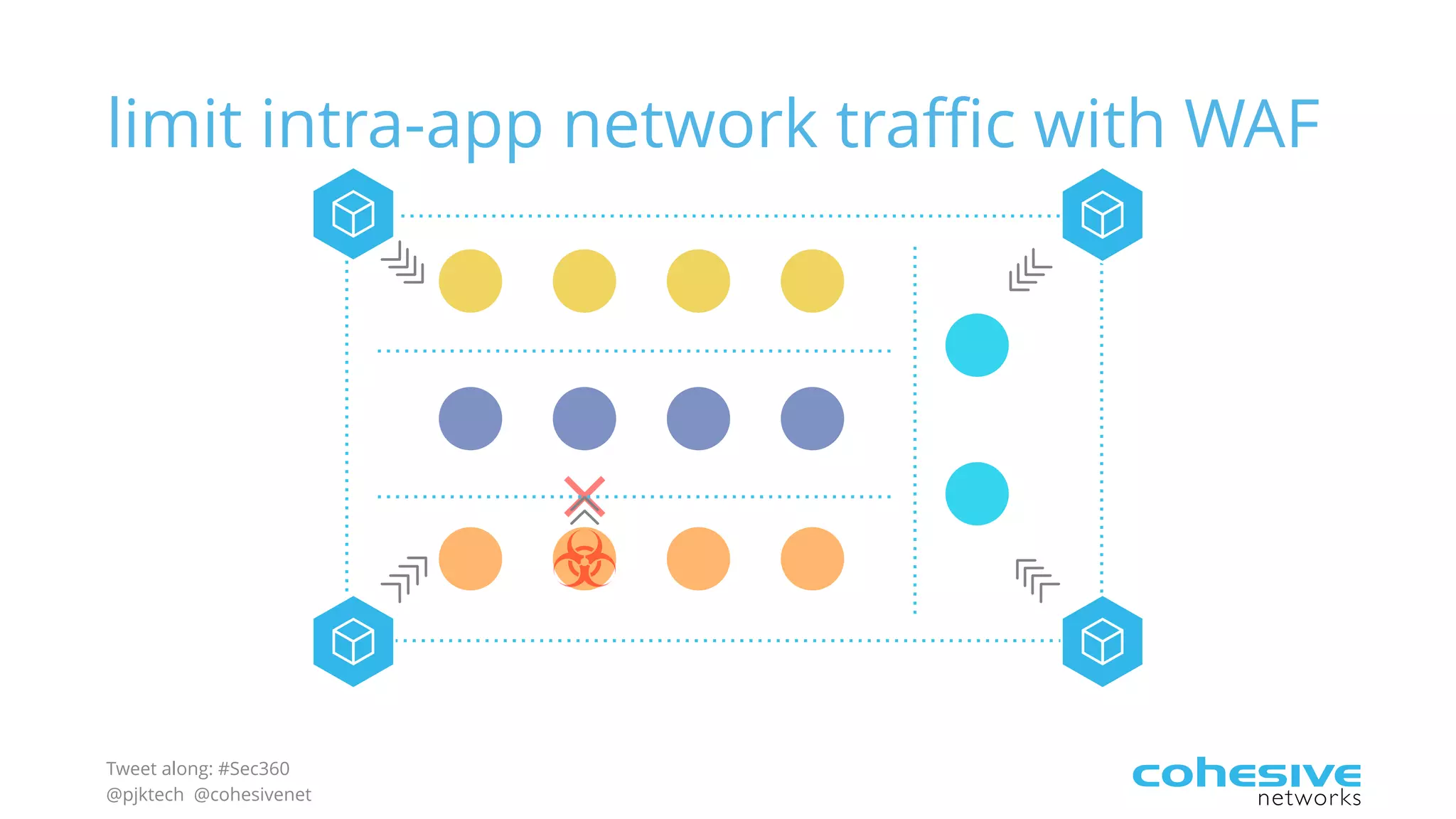
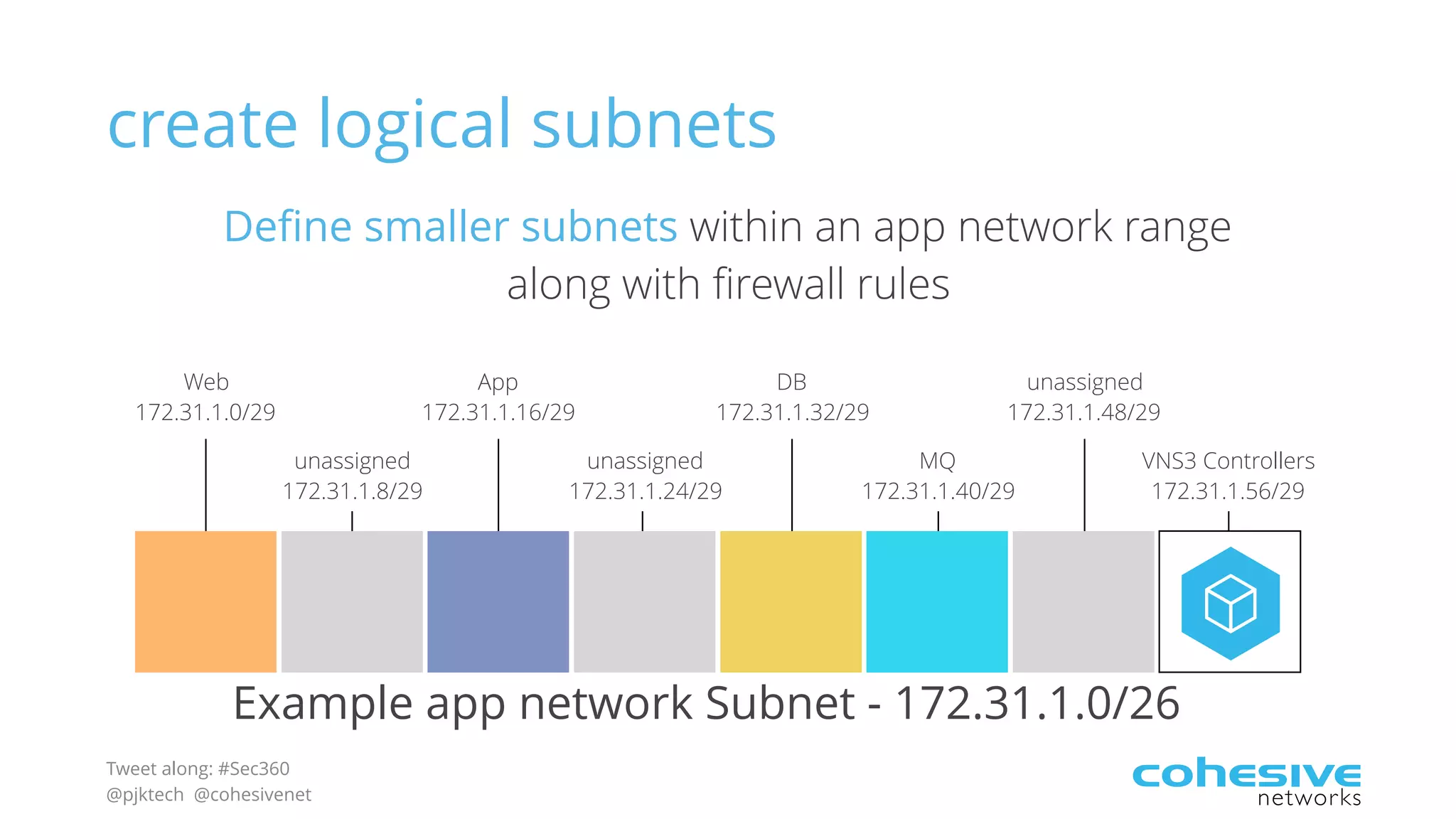
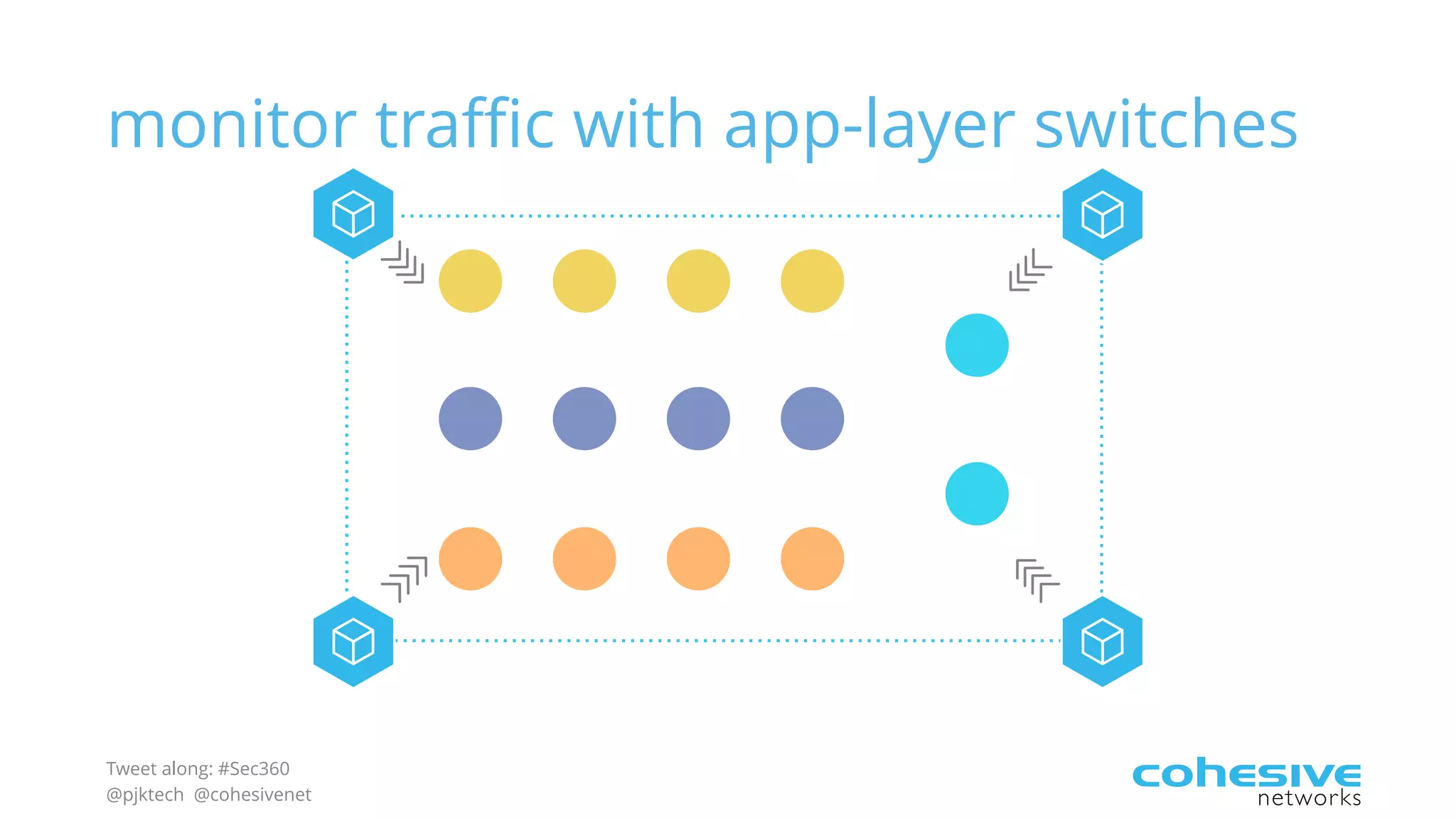
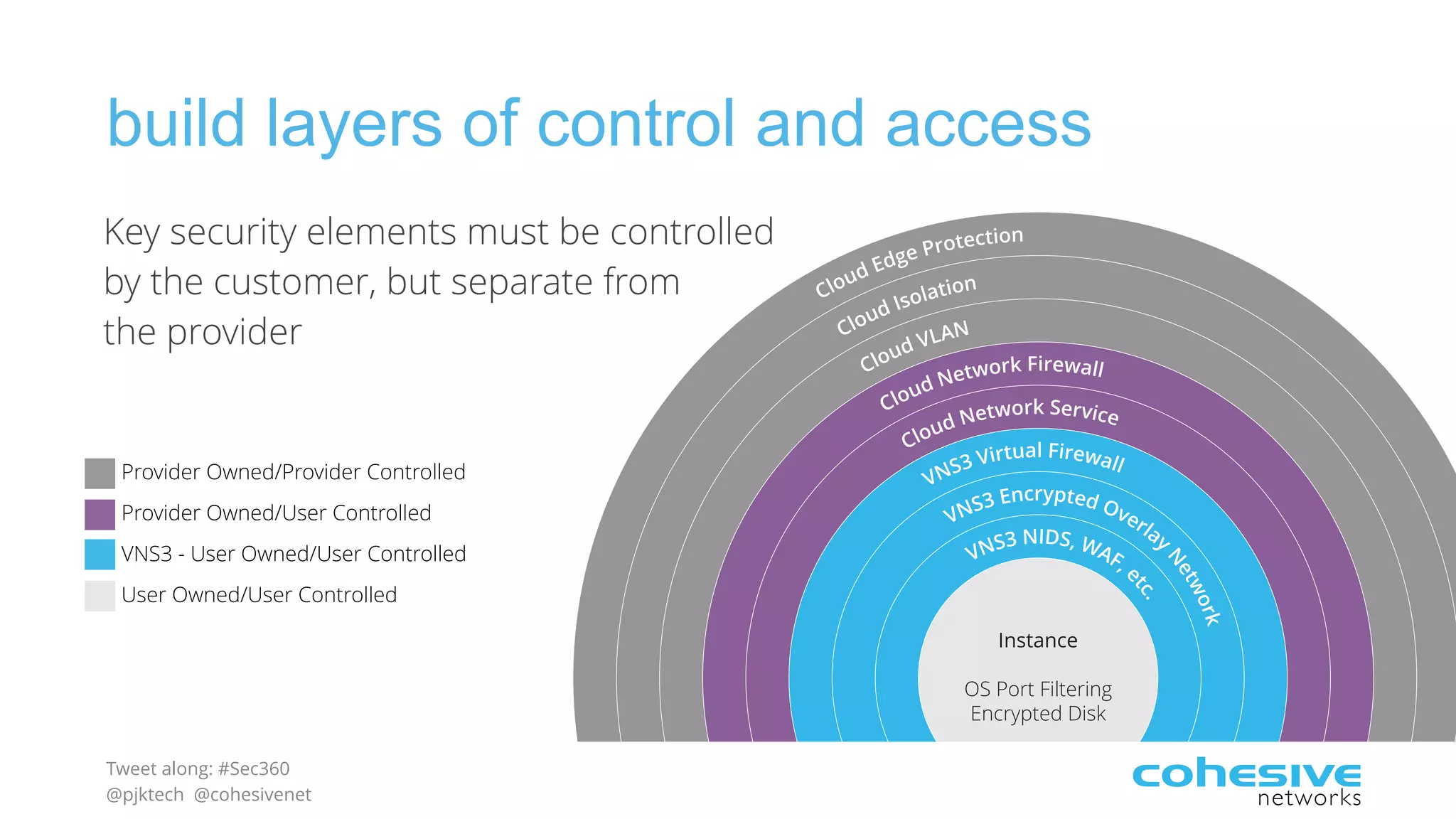
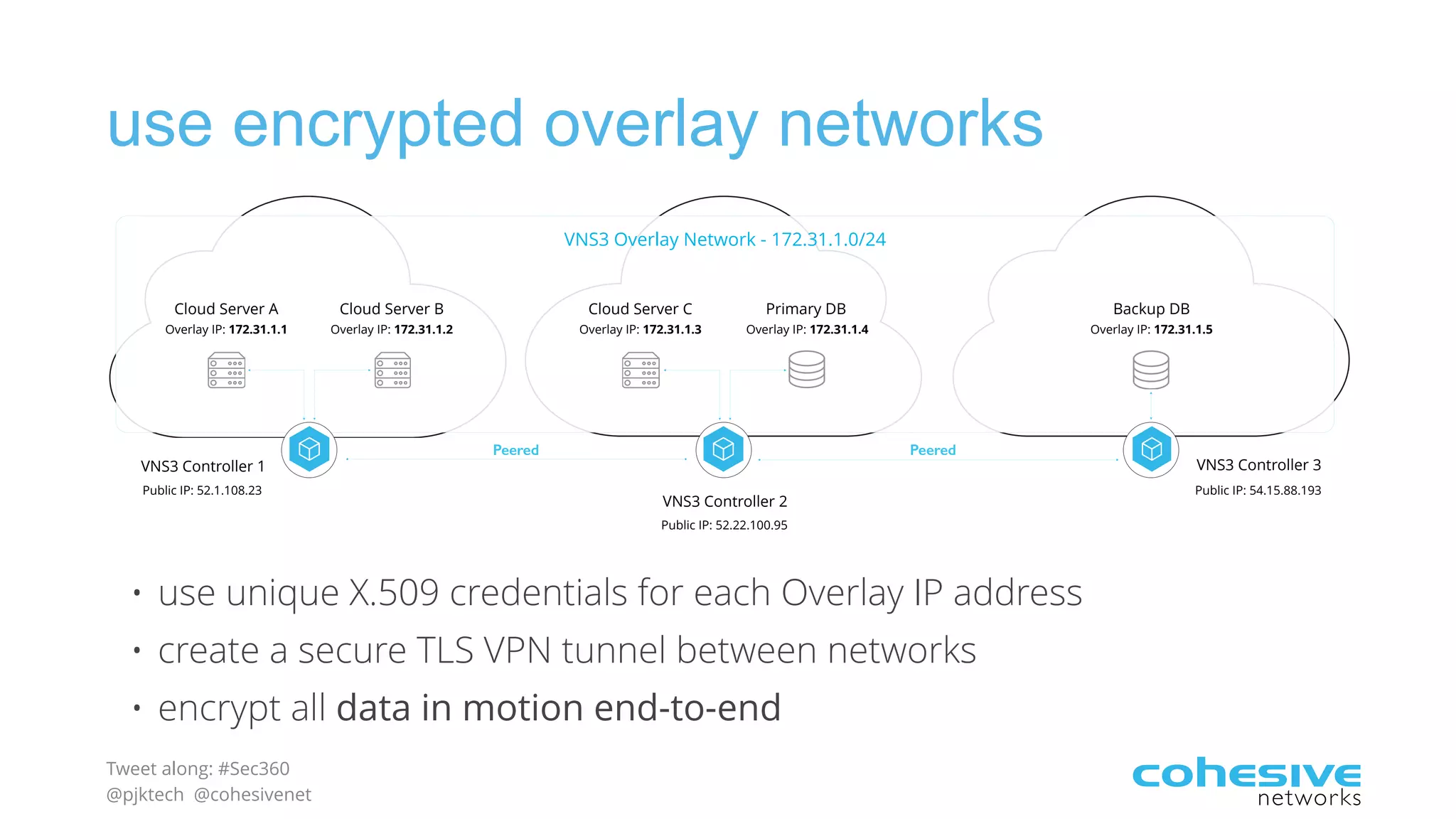
The document discusses rethinking cloud application security in 2016. It argues that data center security models do not work for cloud security and that applications need security through network virtualization. Upcoming compliance regulations will emphasize network segmentation, application security, and isolation. The document recommends using application layer switches and network controls like micro-perimeters, encrypted overlays and traffic policies to build secure layers of access and control for cloud applications. This will help make 2016 a more secure year.