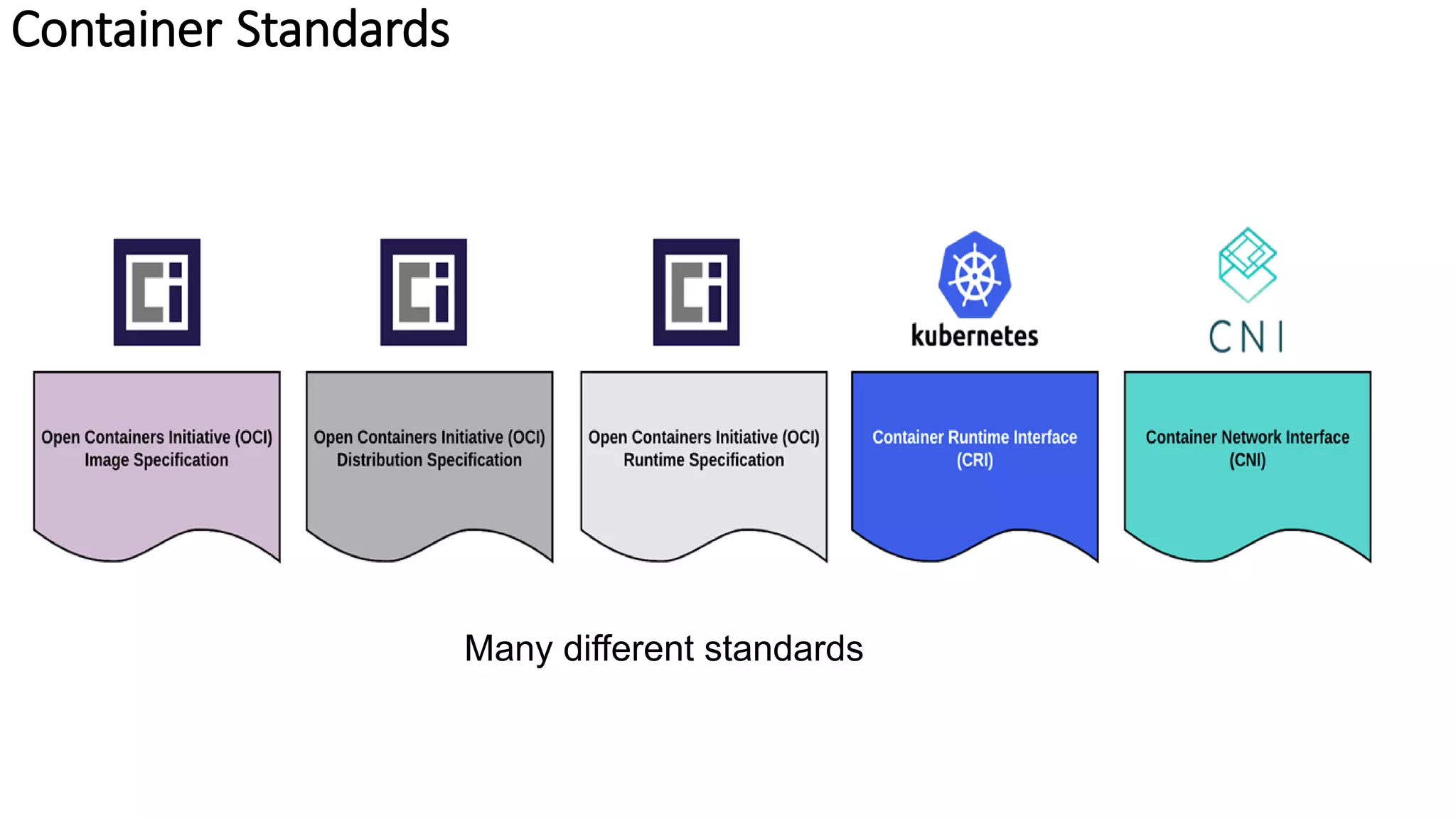
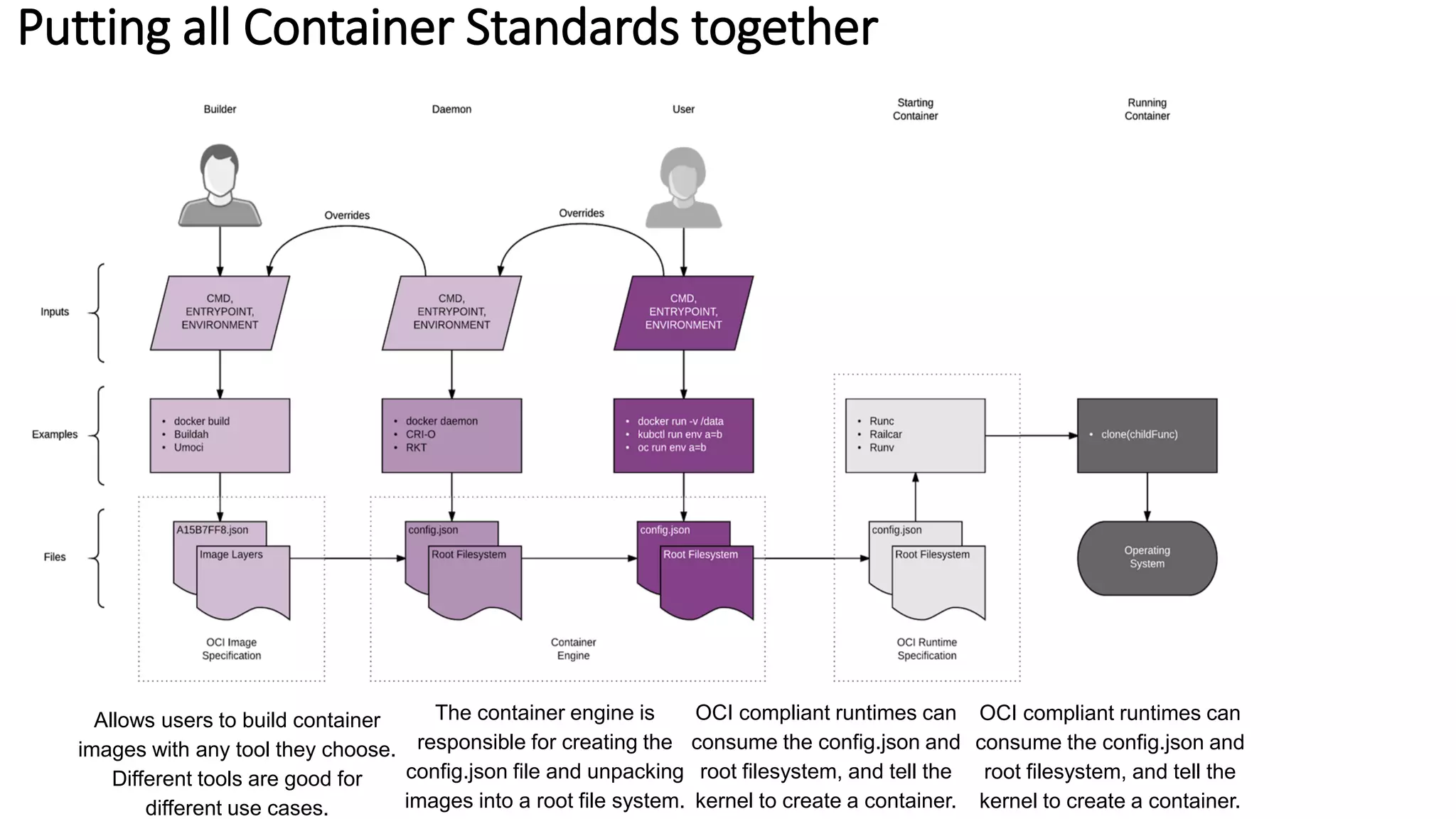
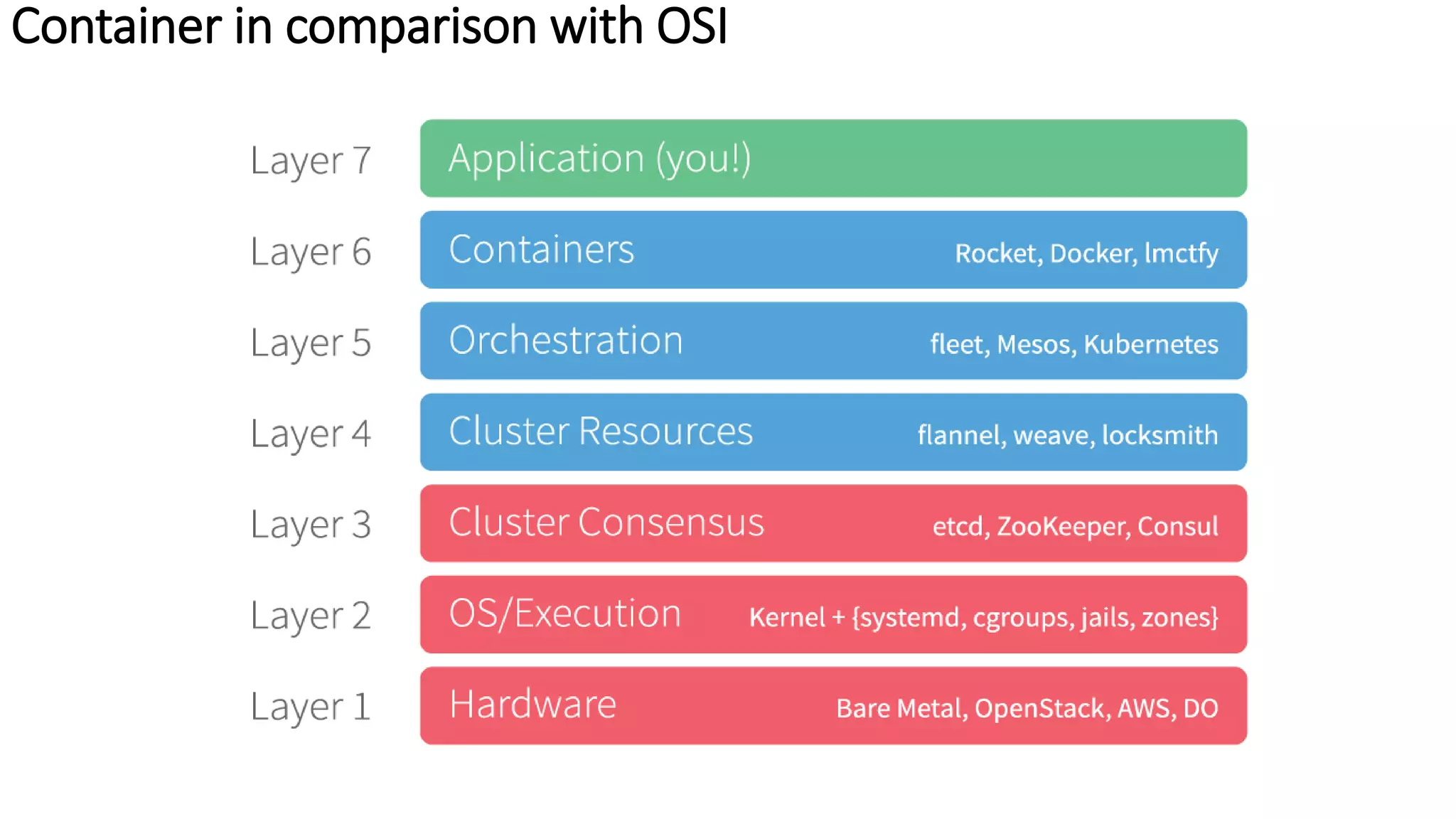
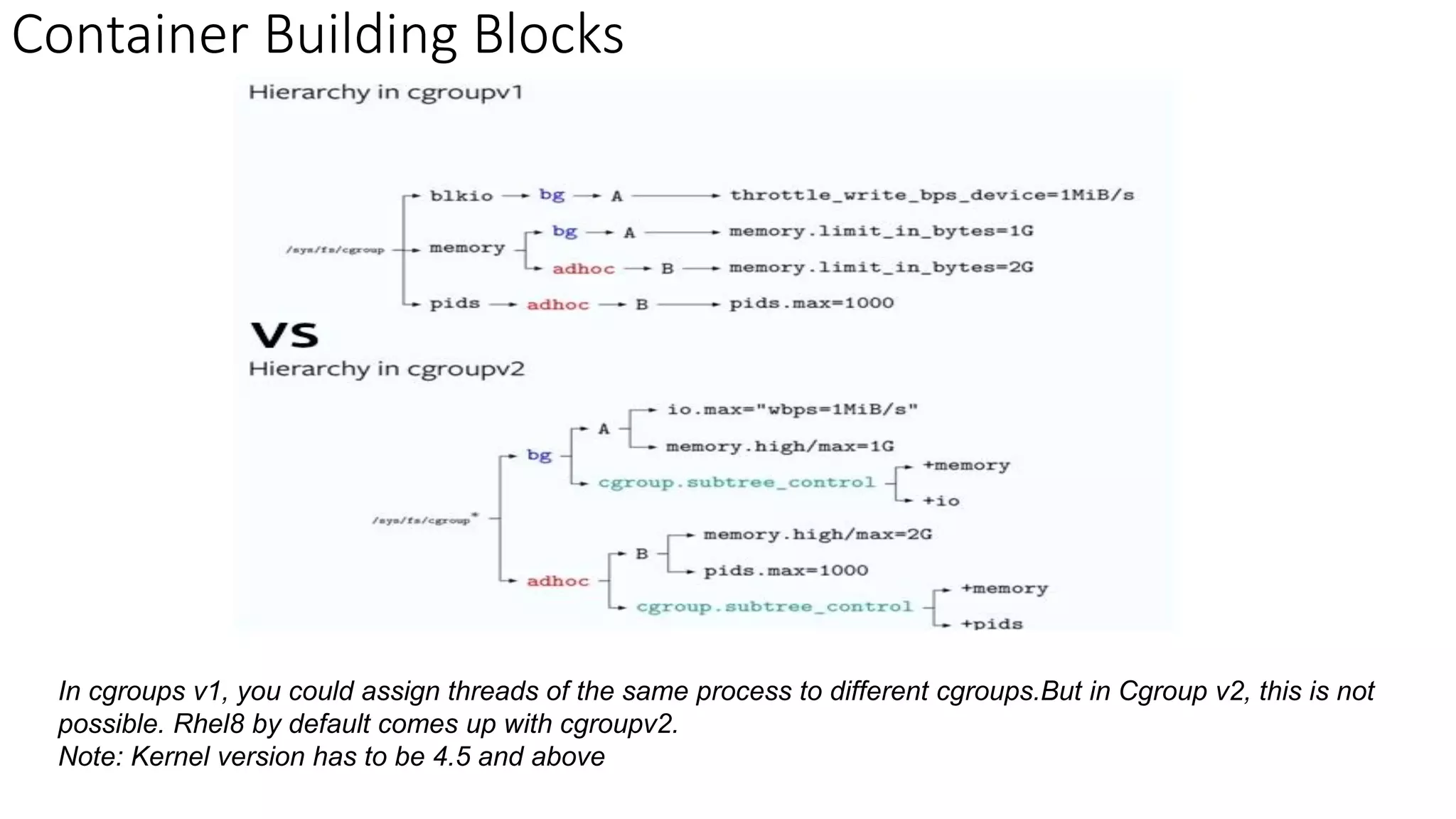
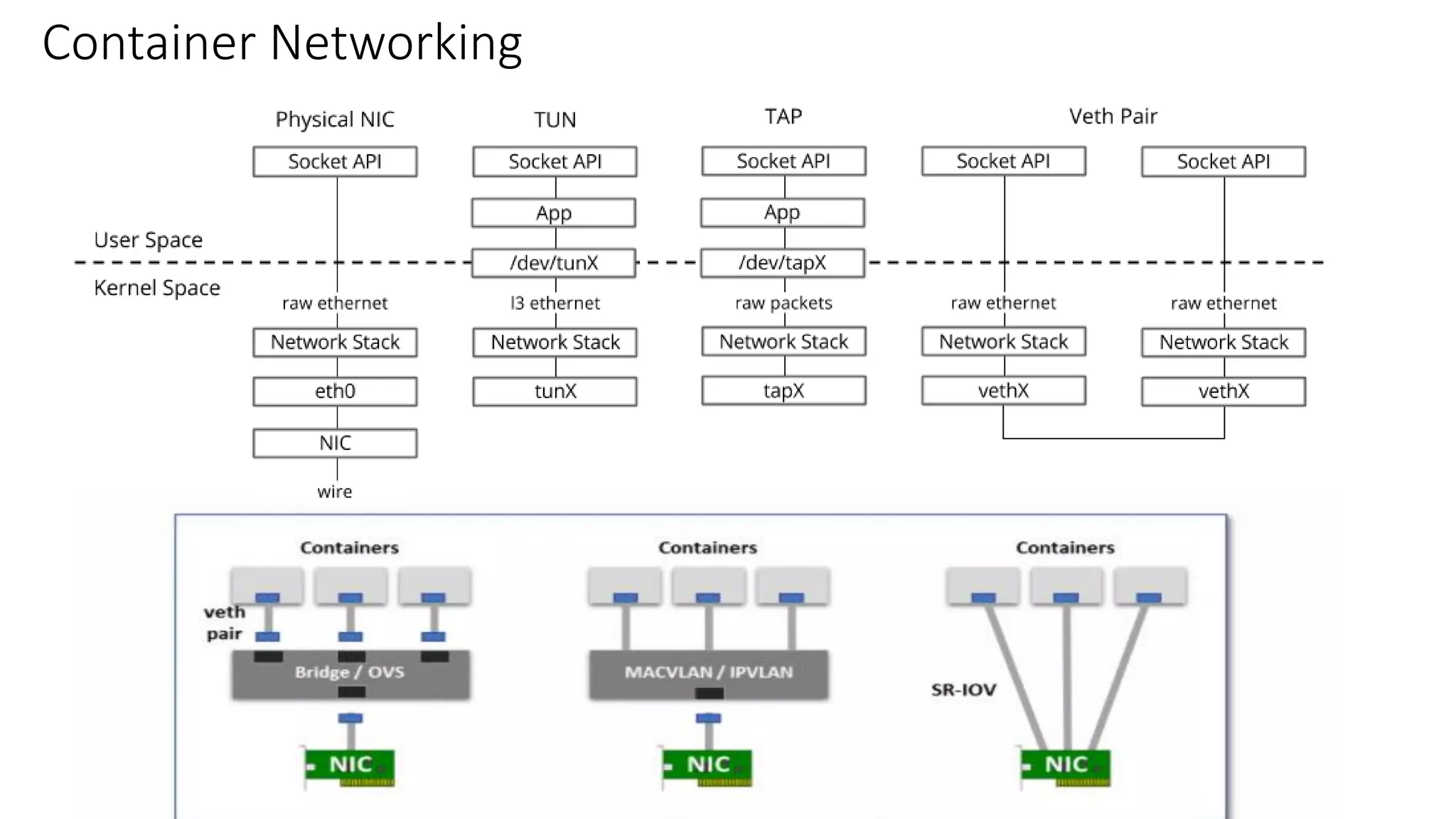
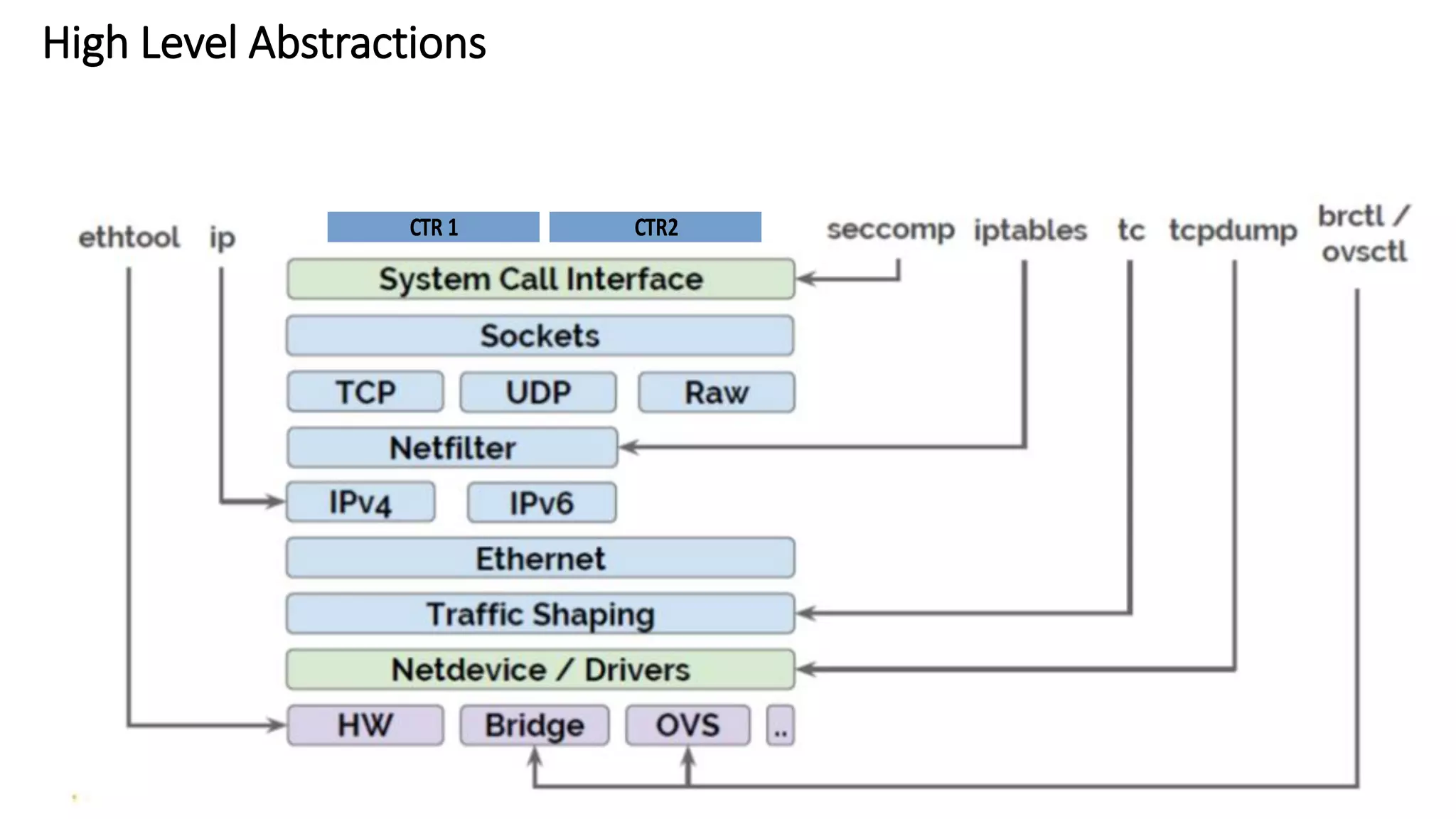
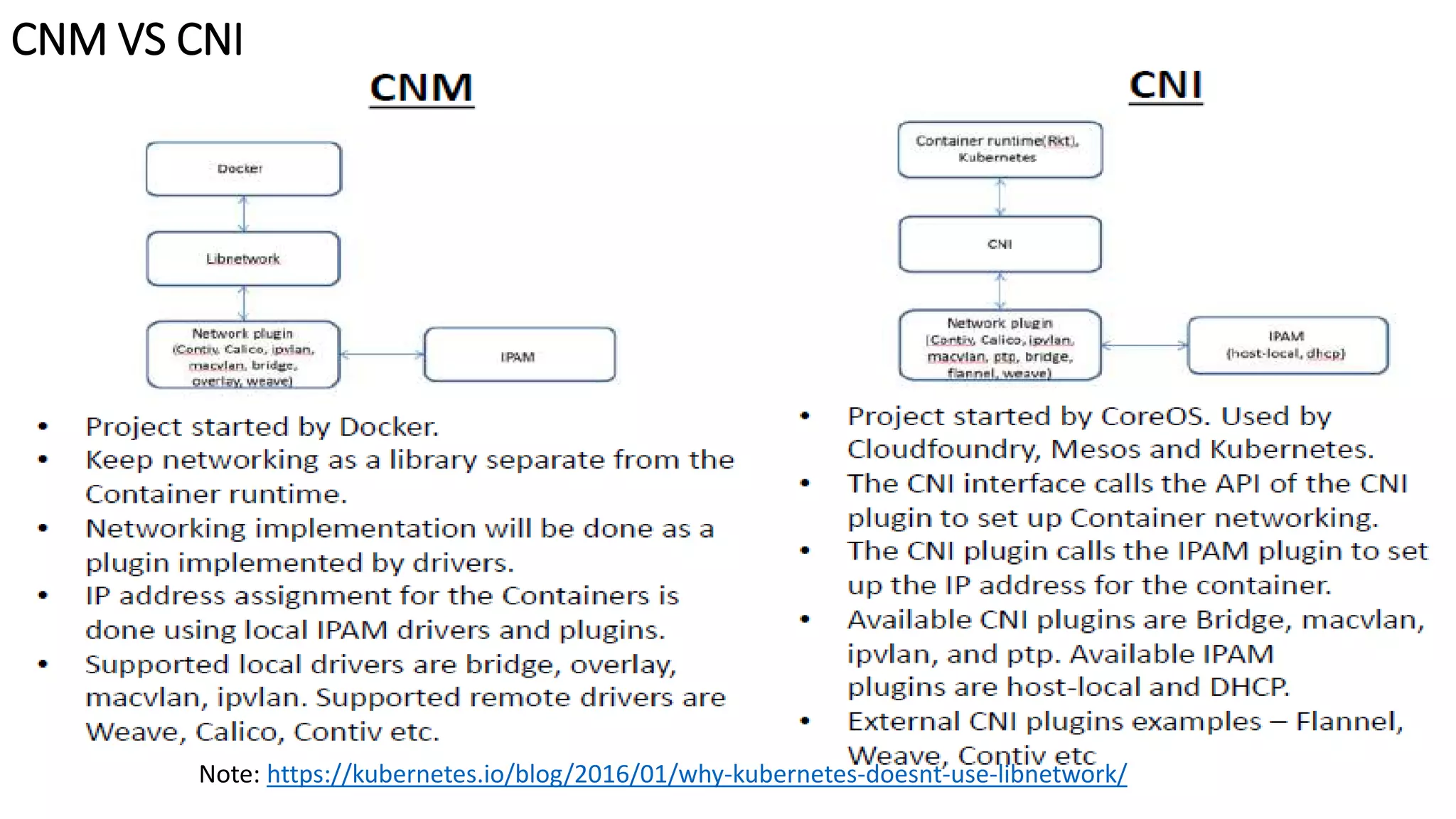
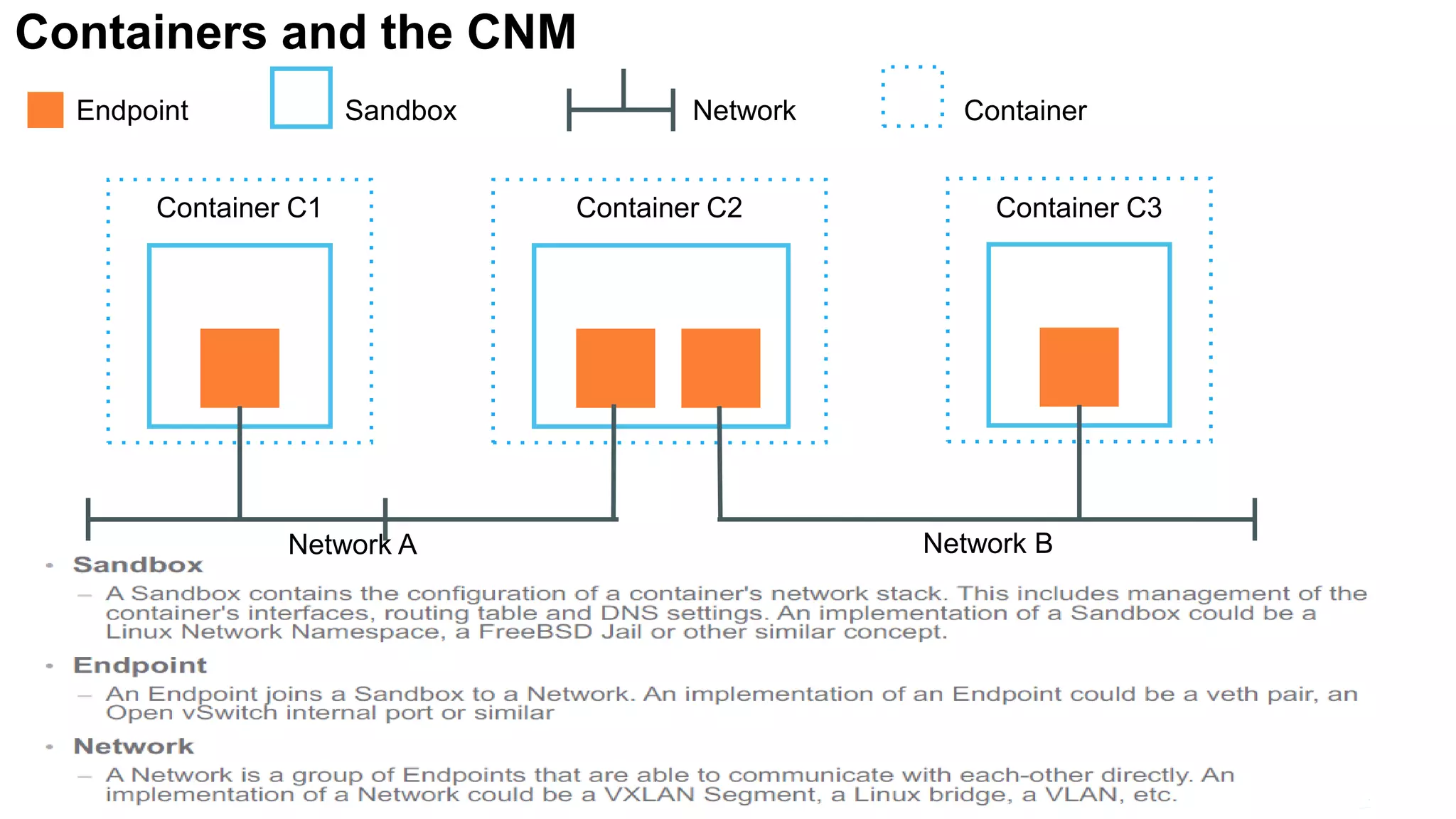
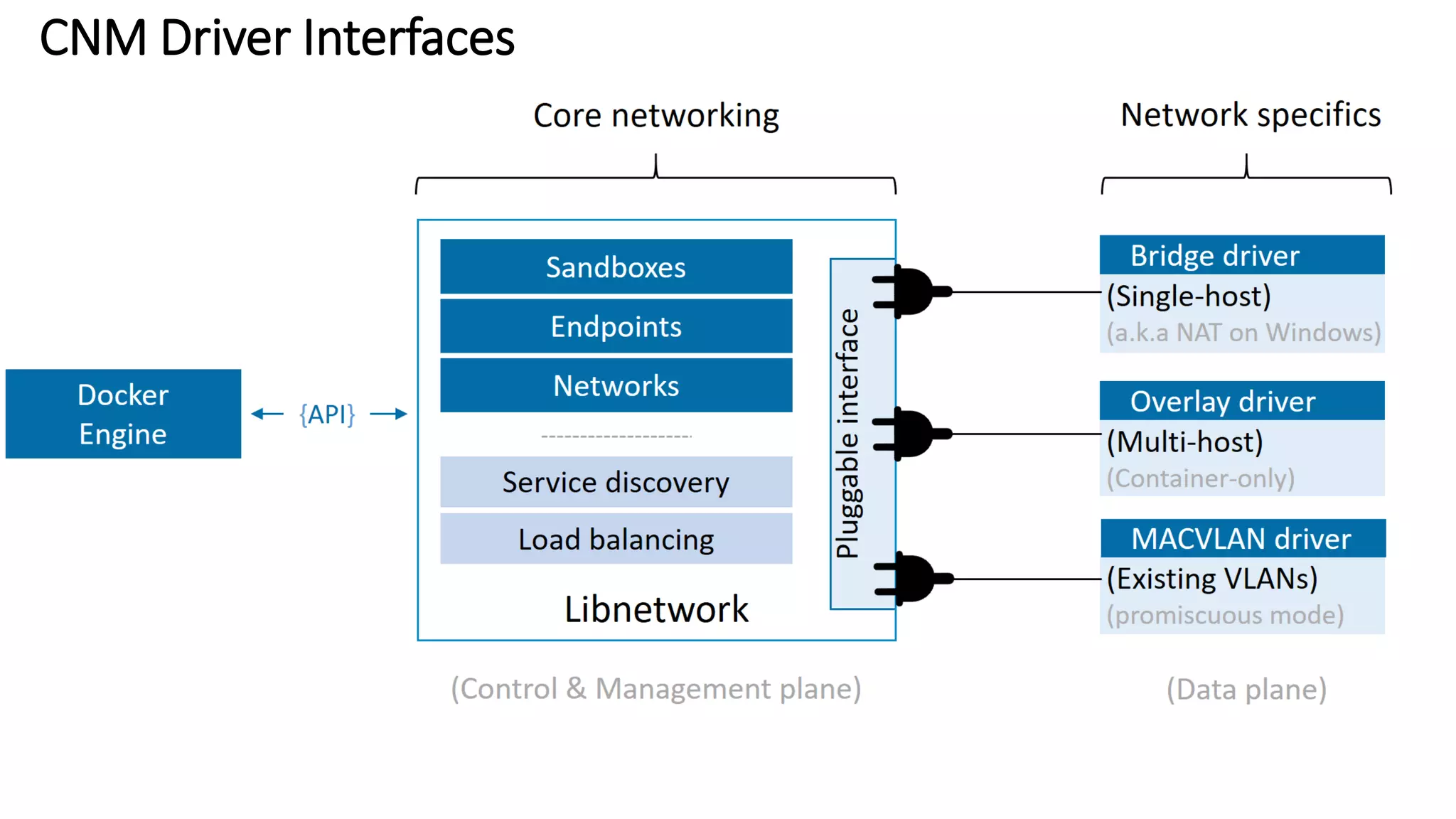
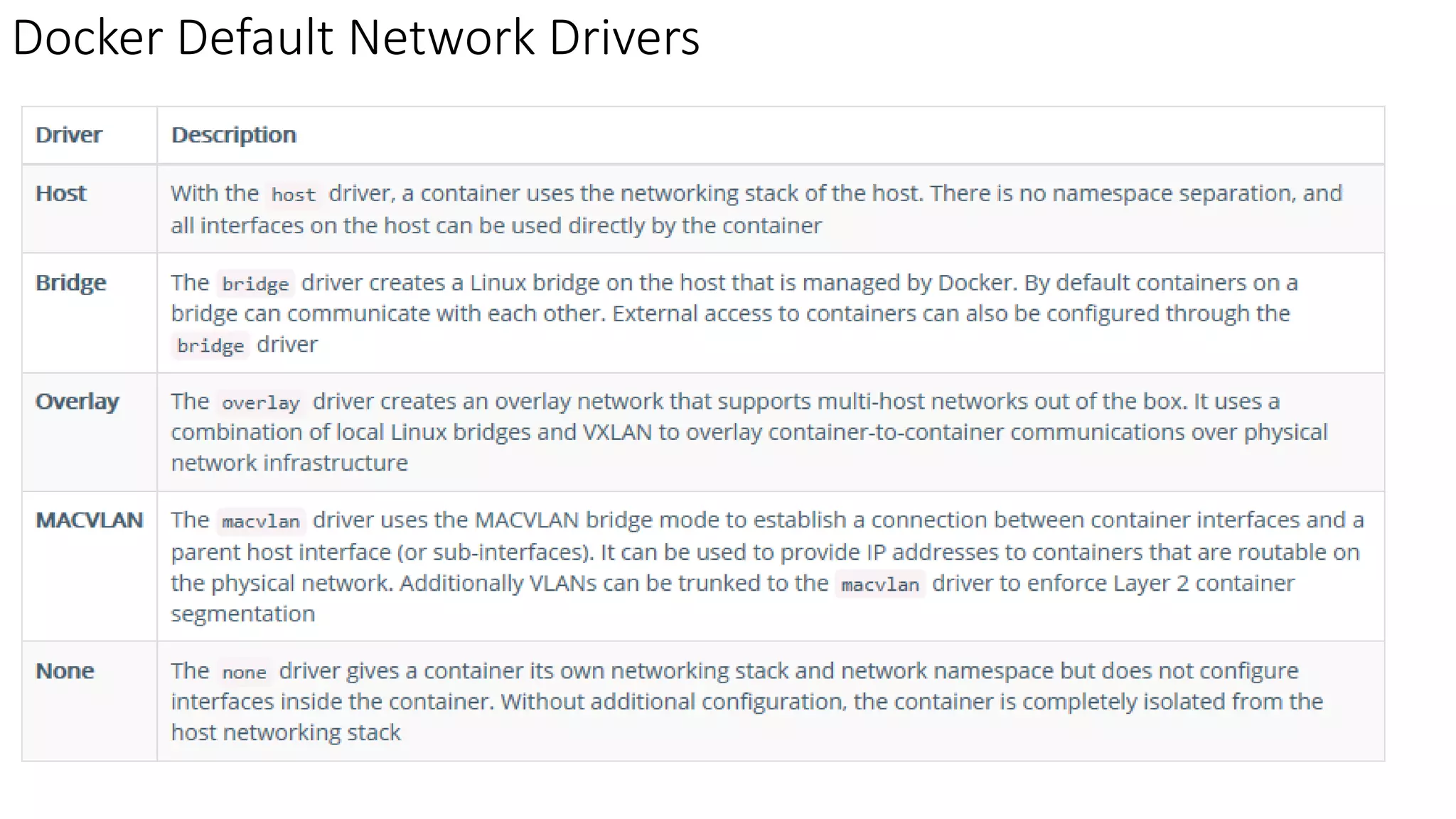
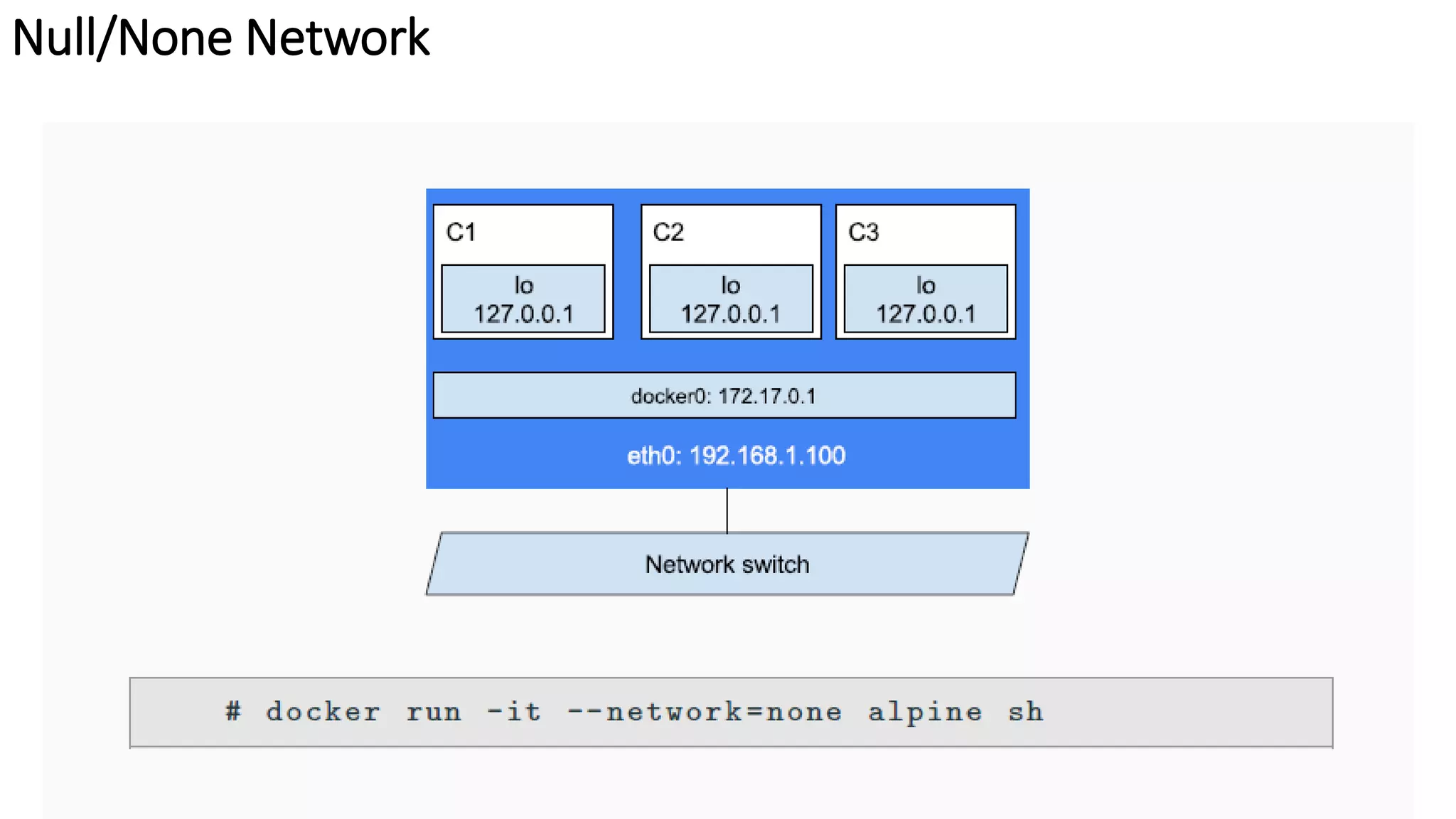
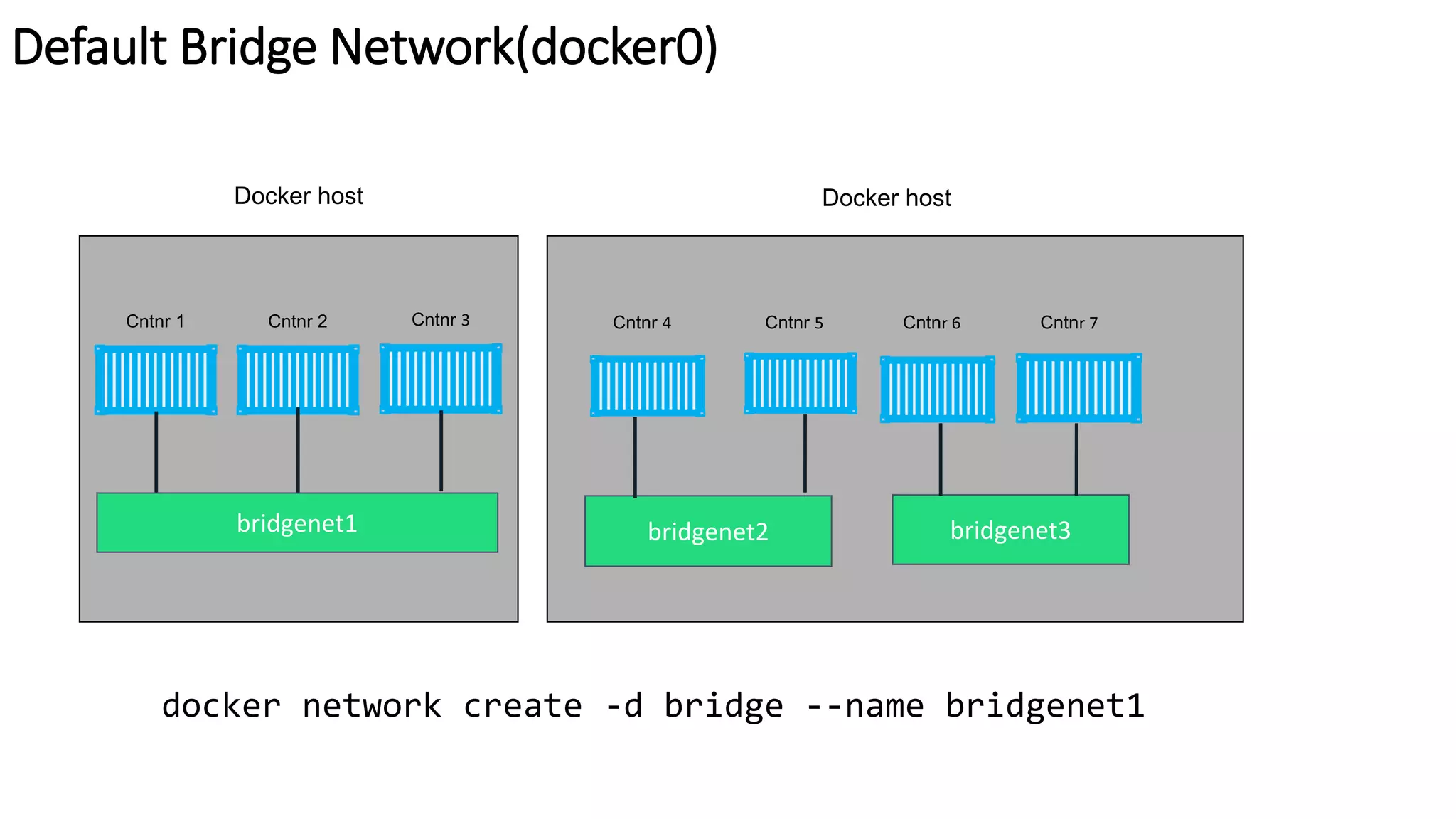
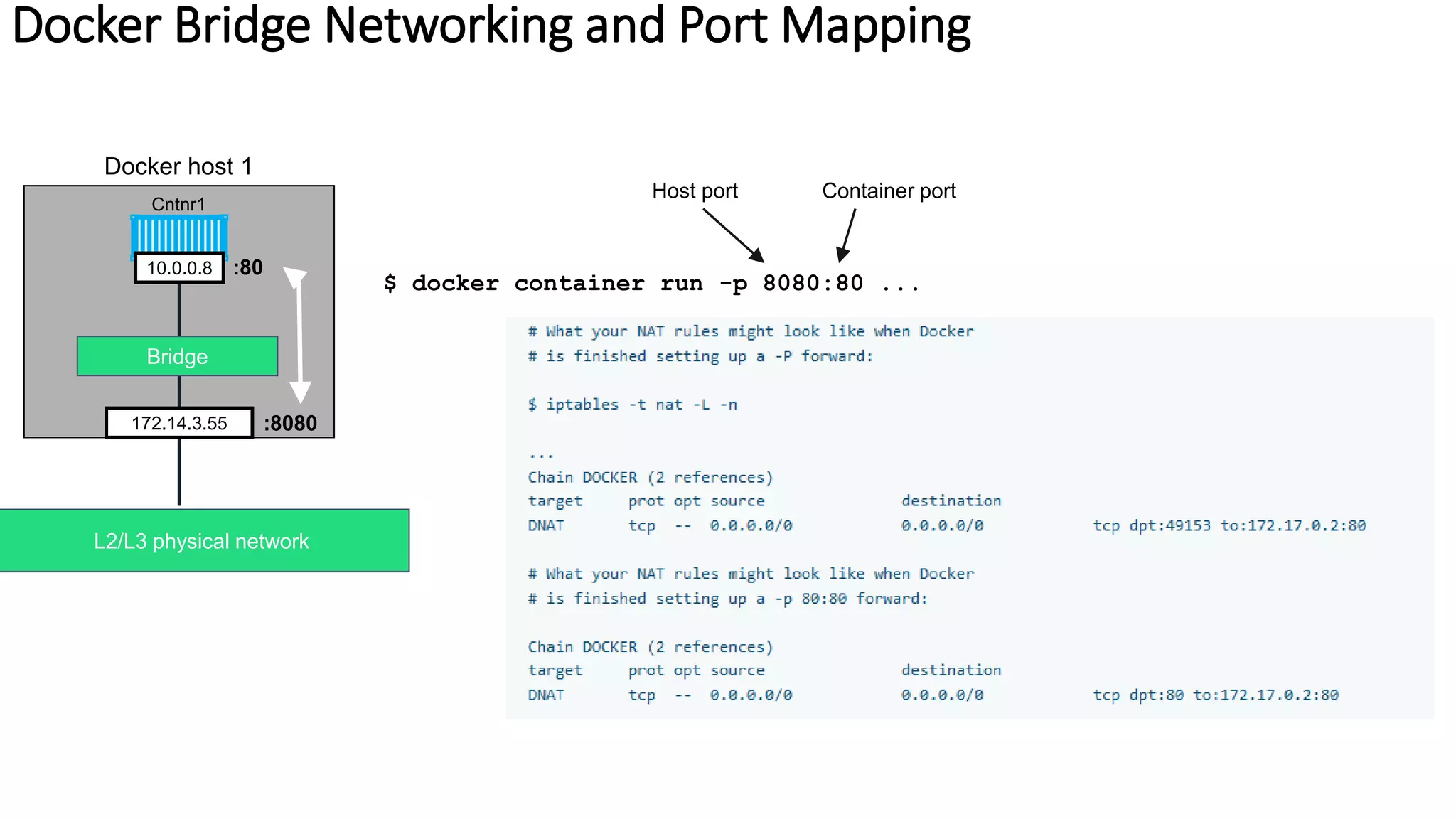
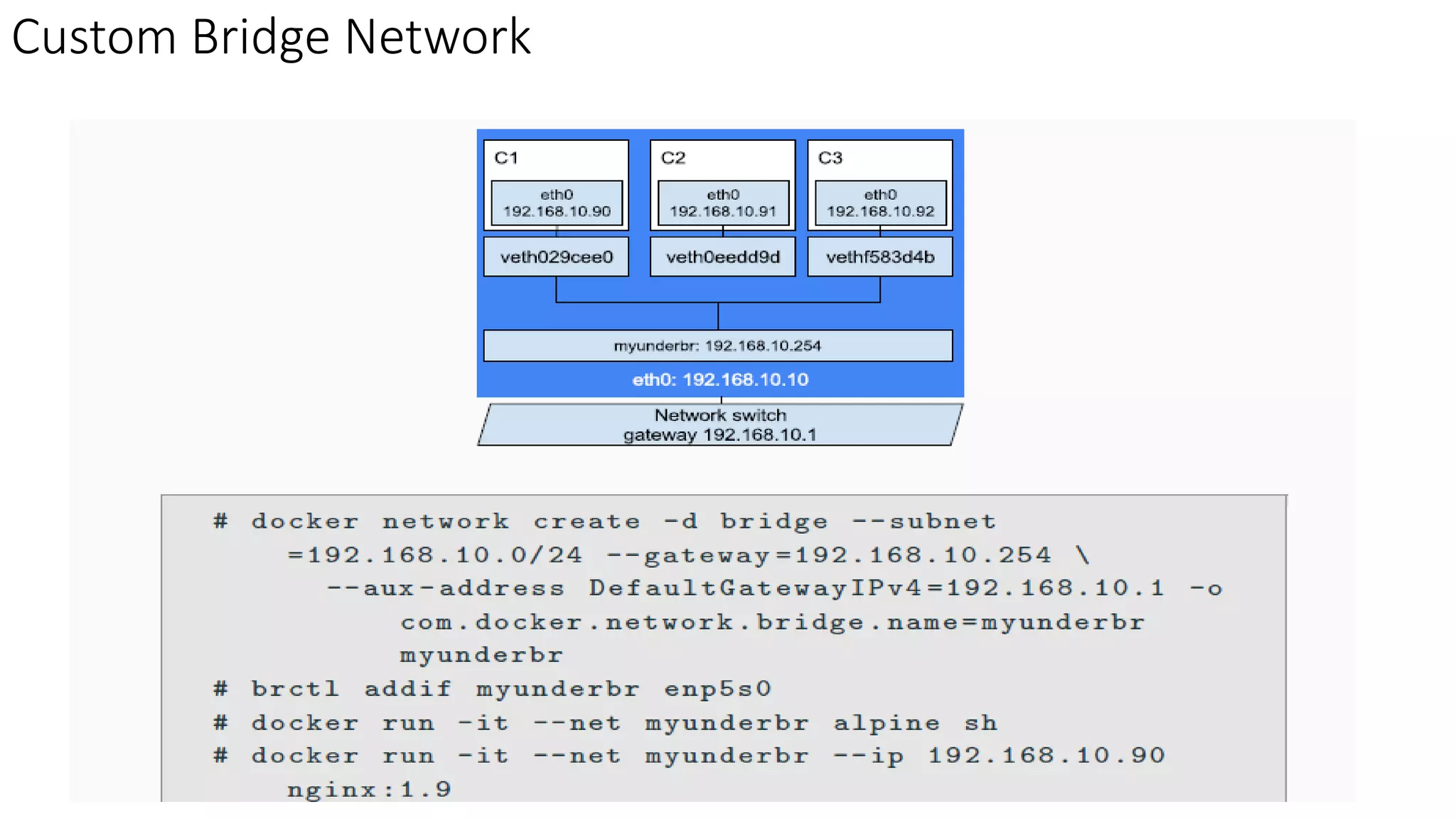
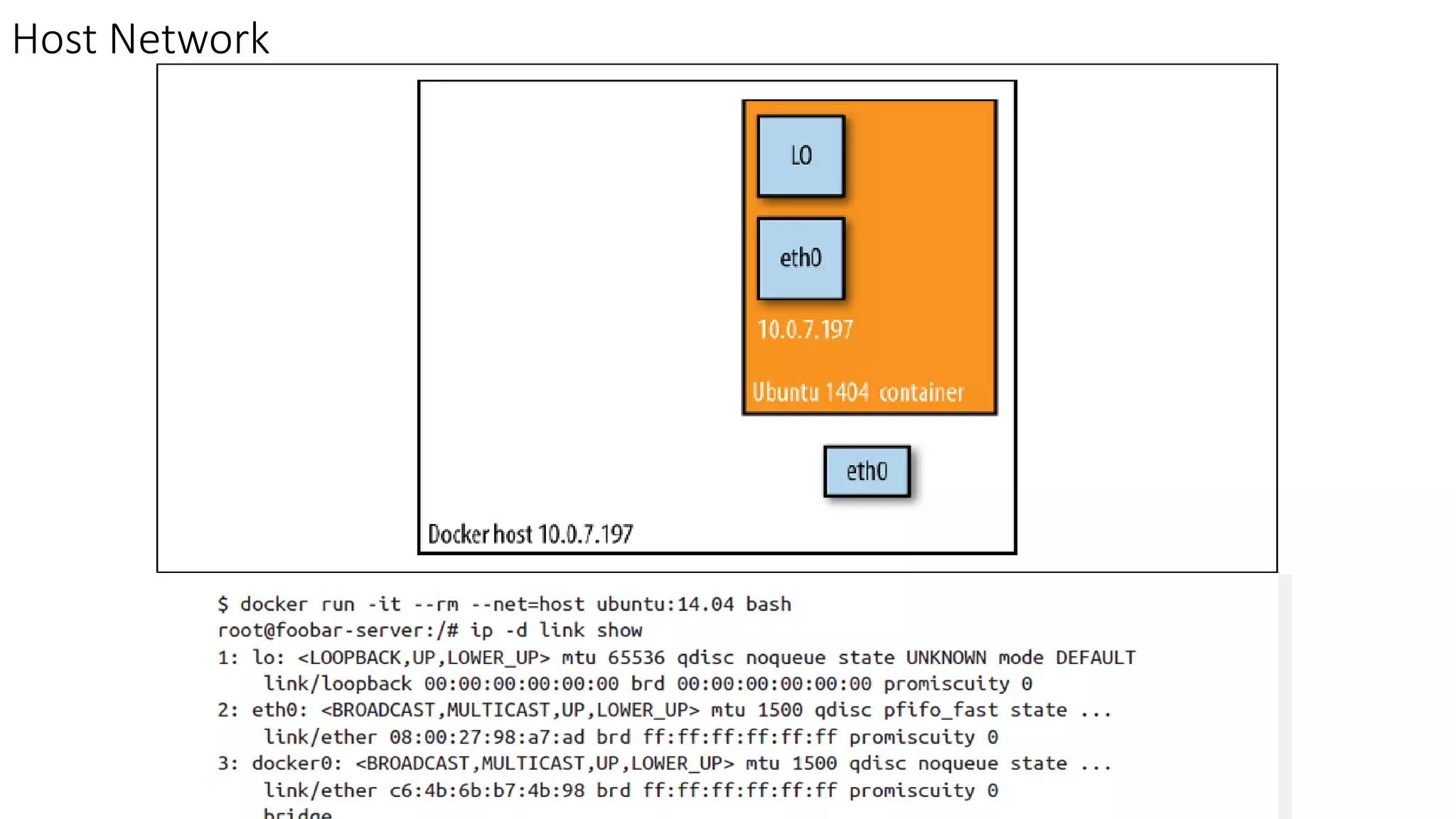
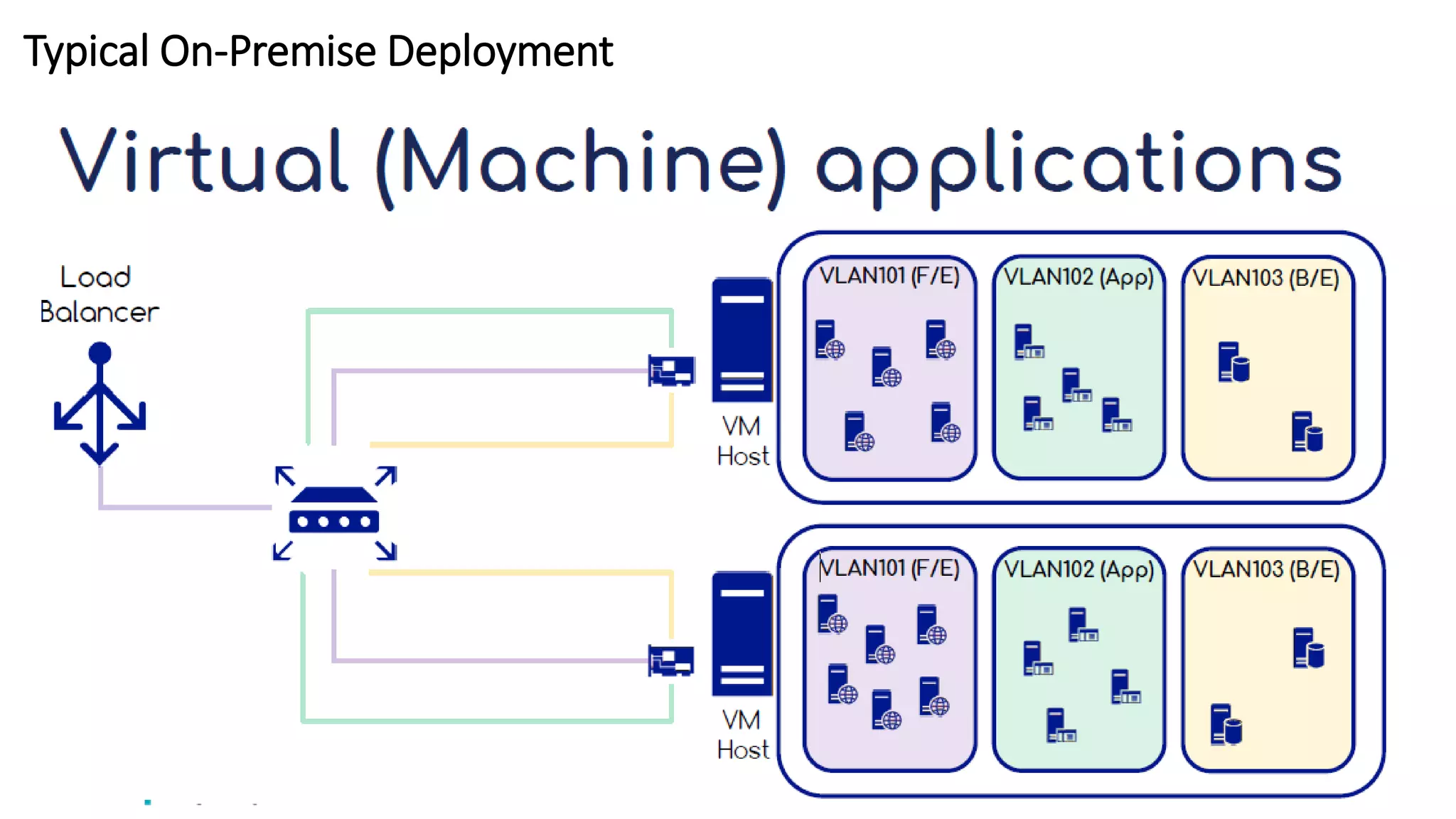
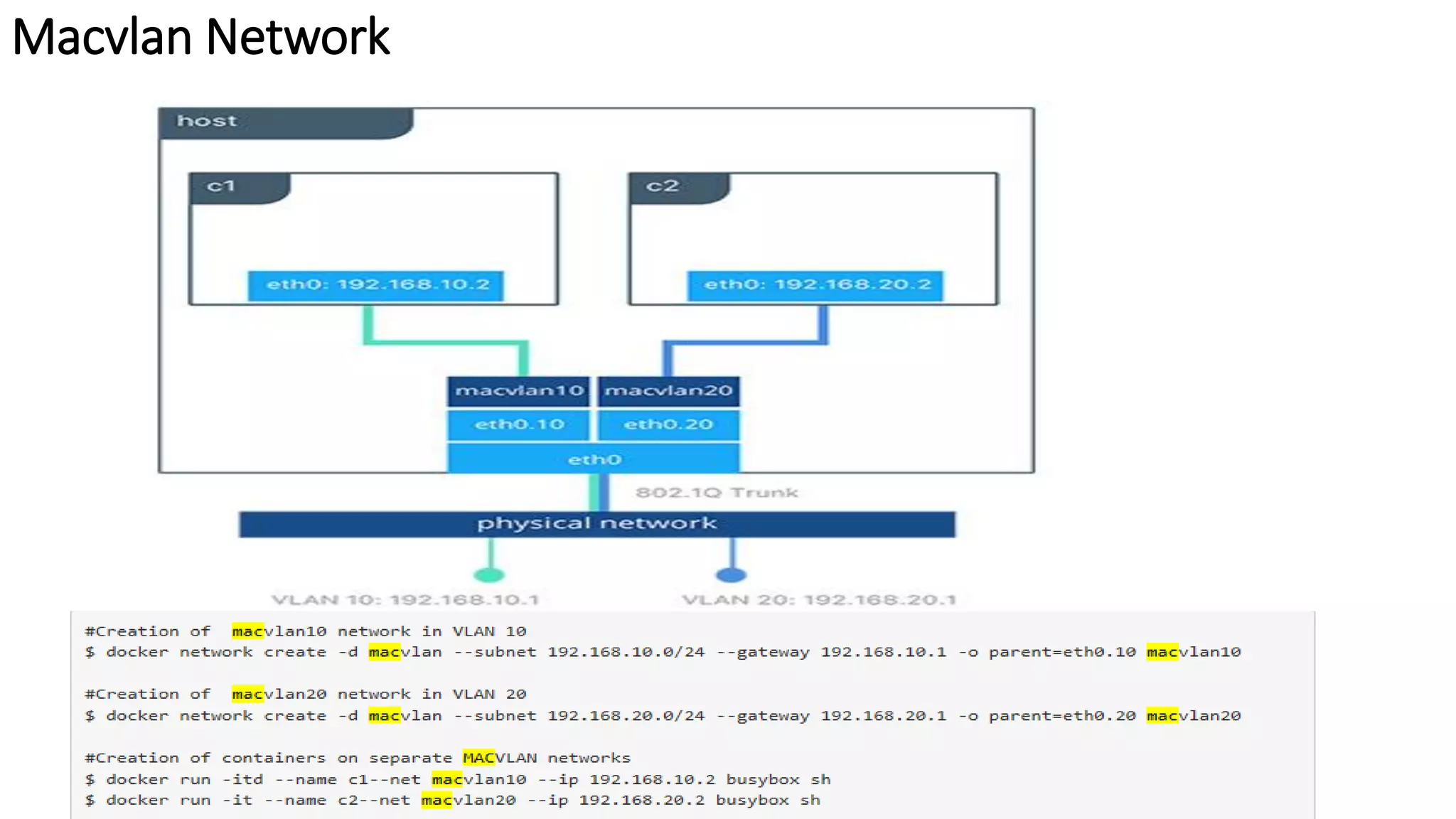
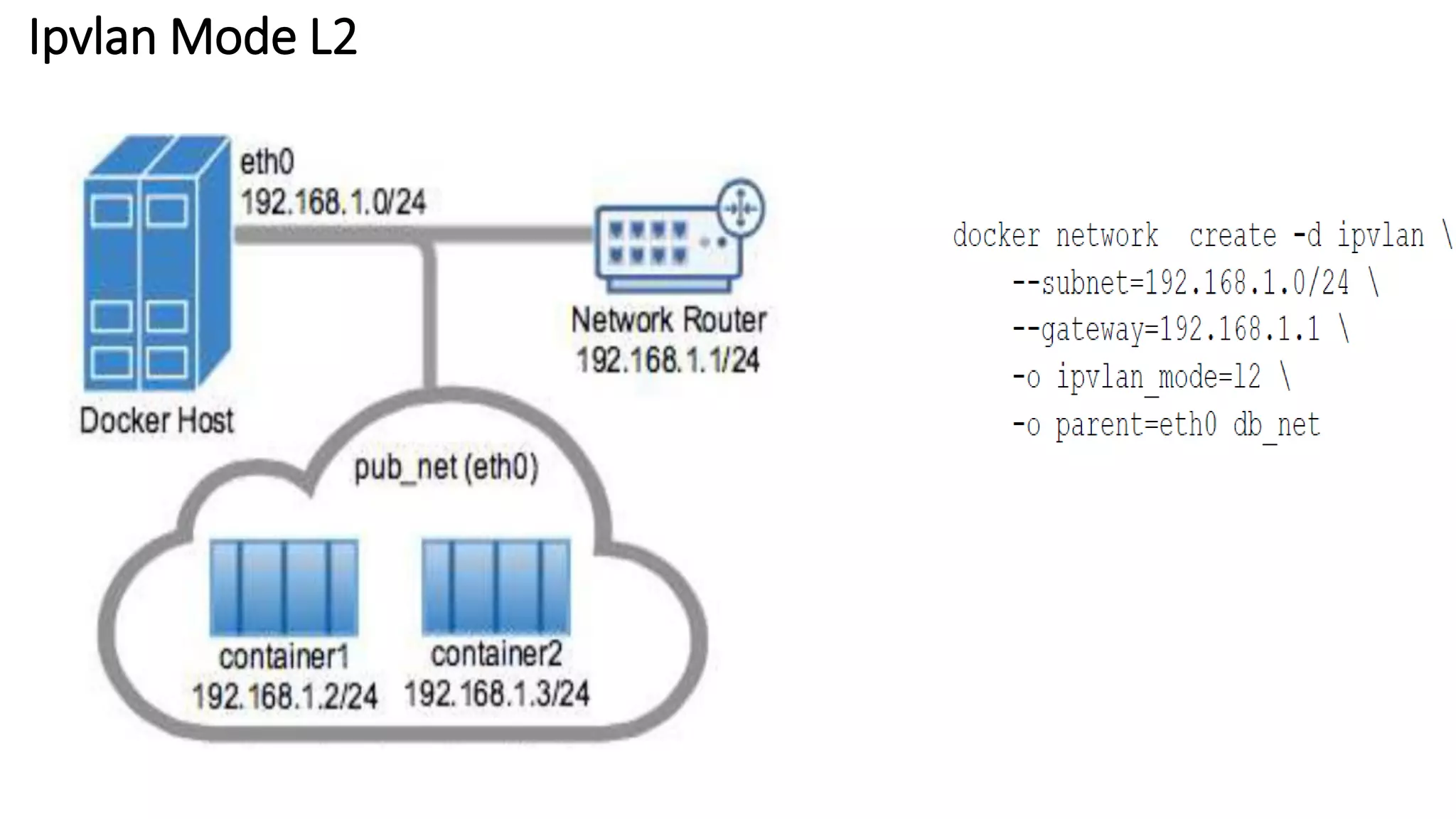
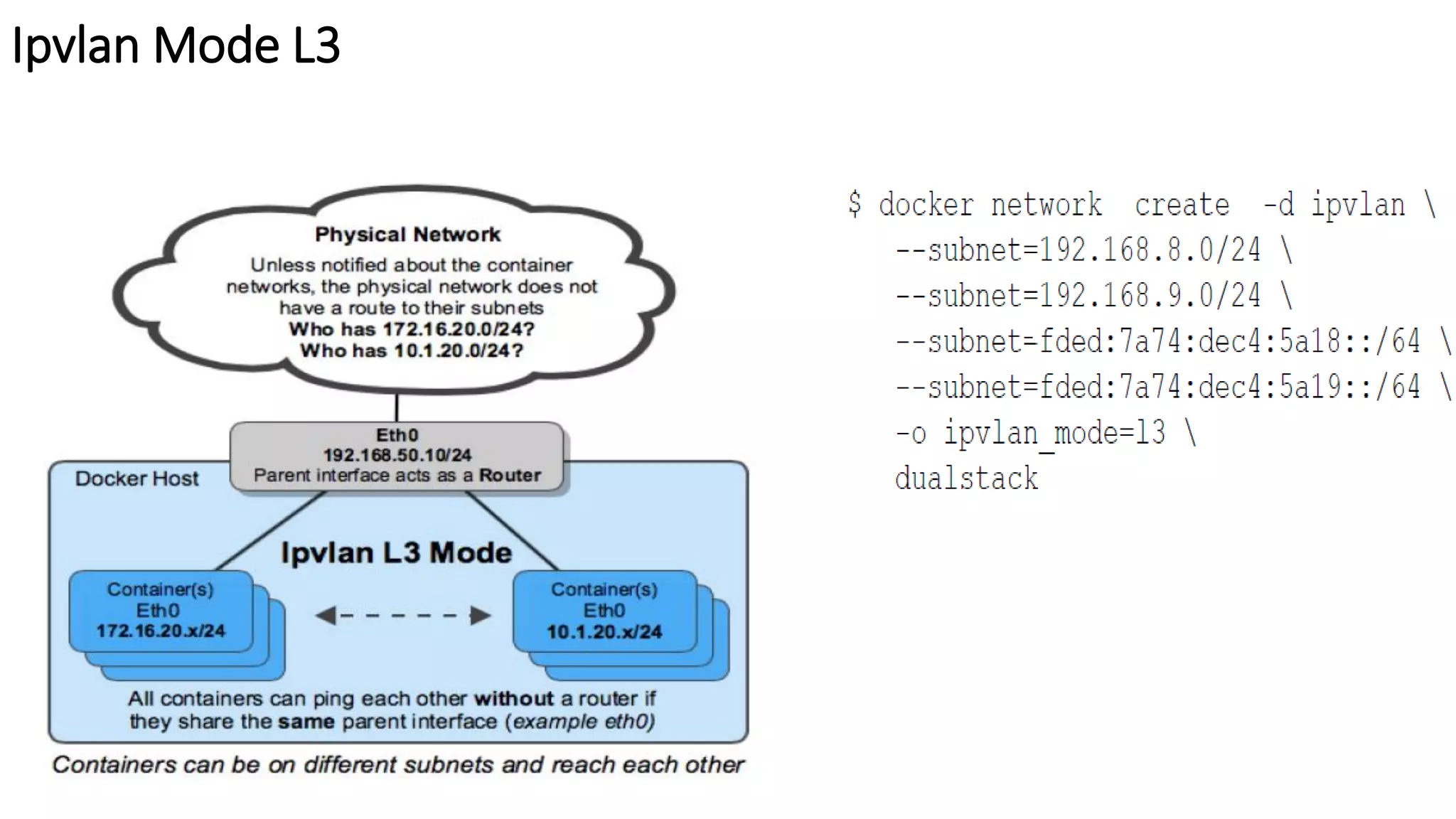
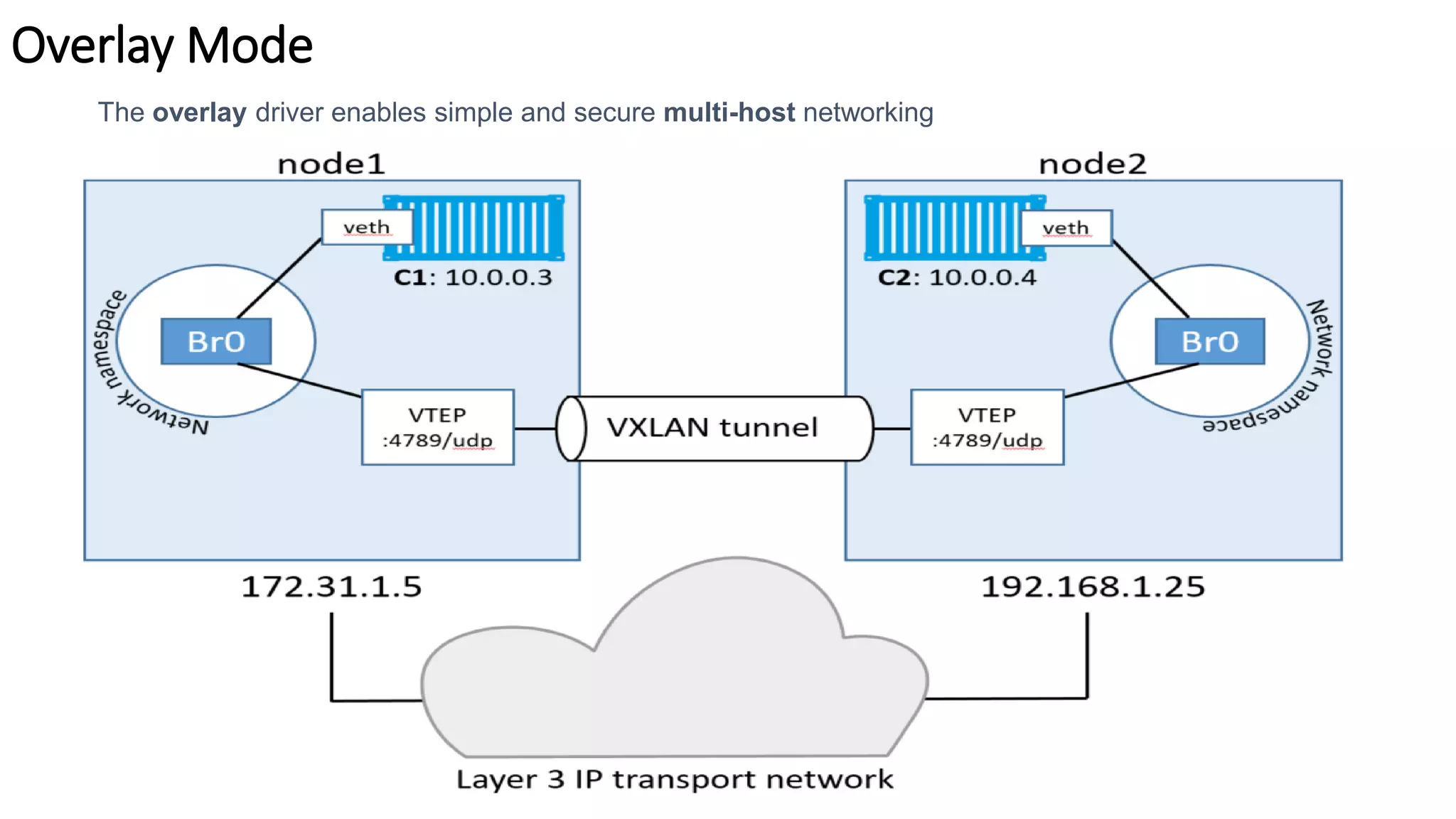
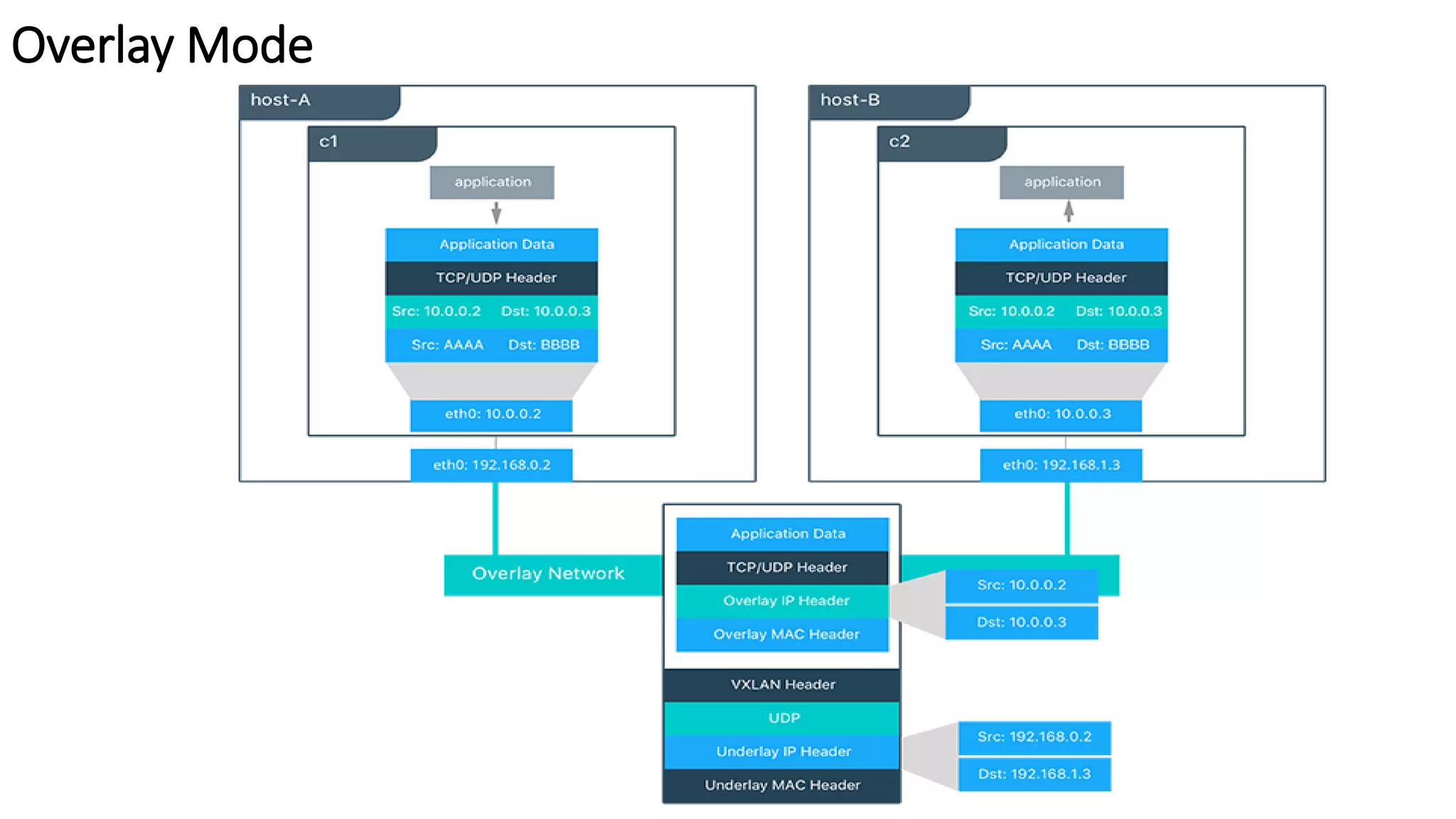
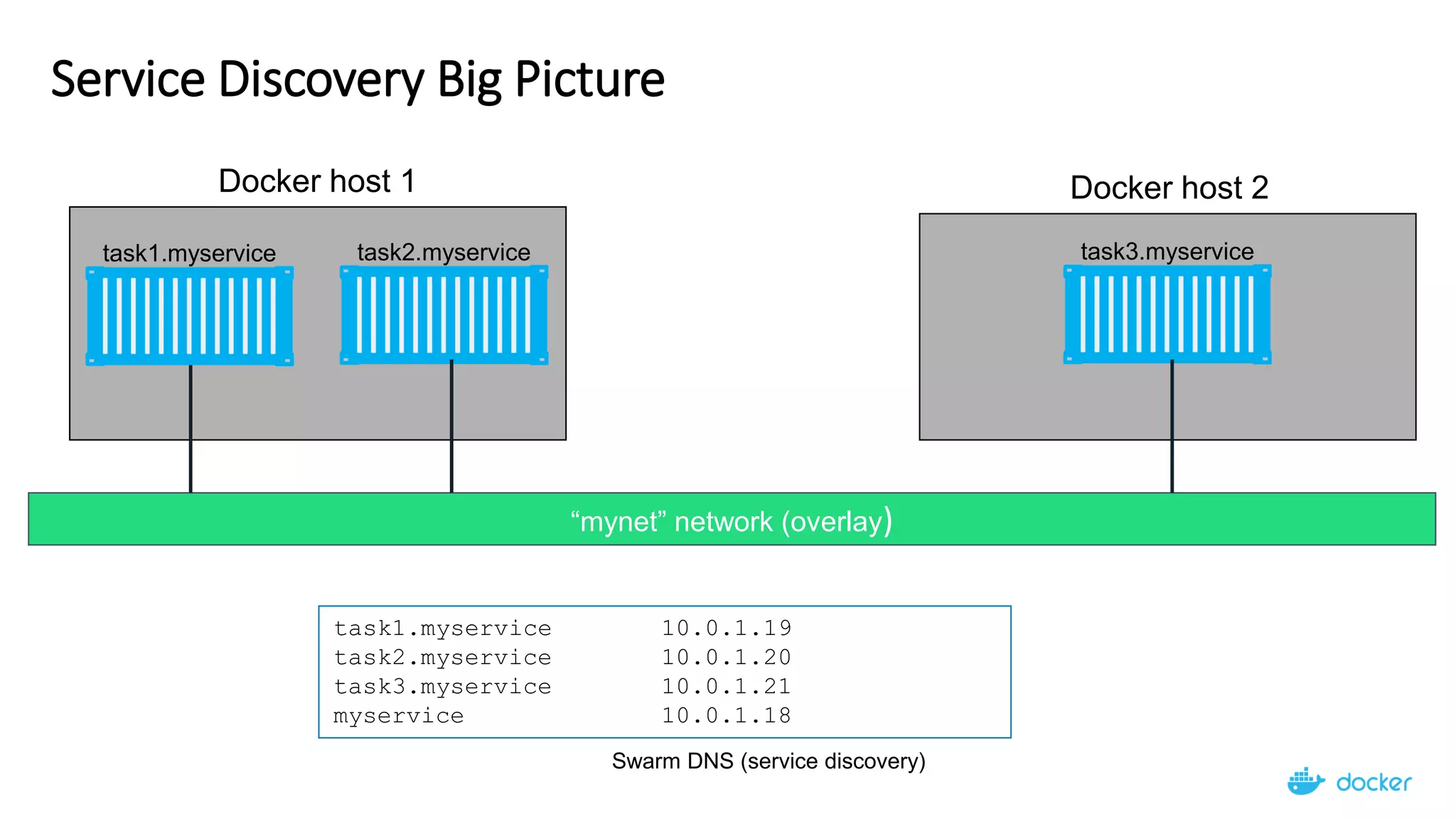
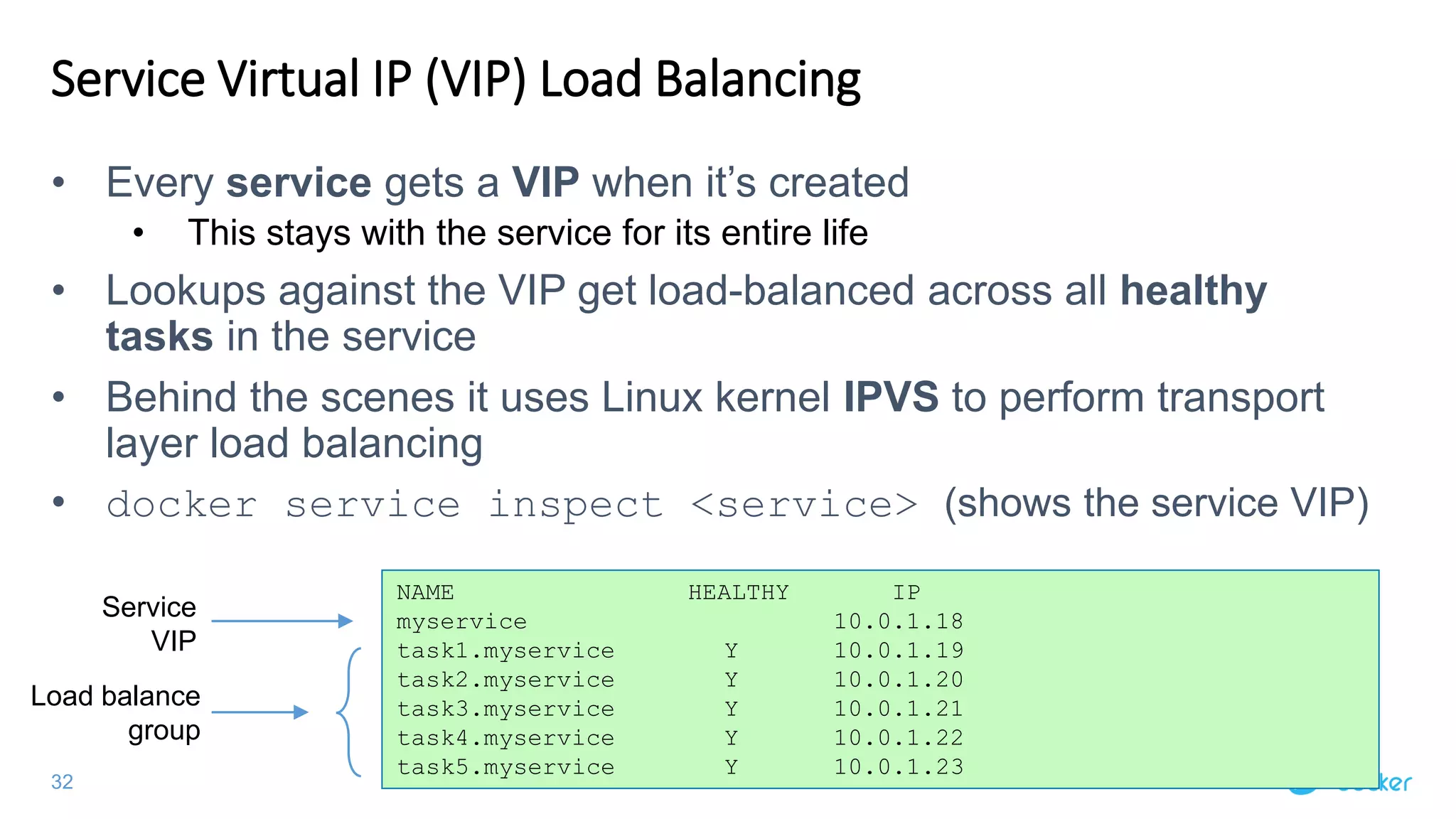
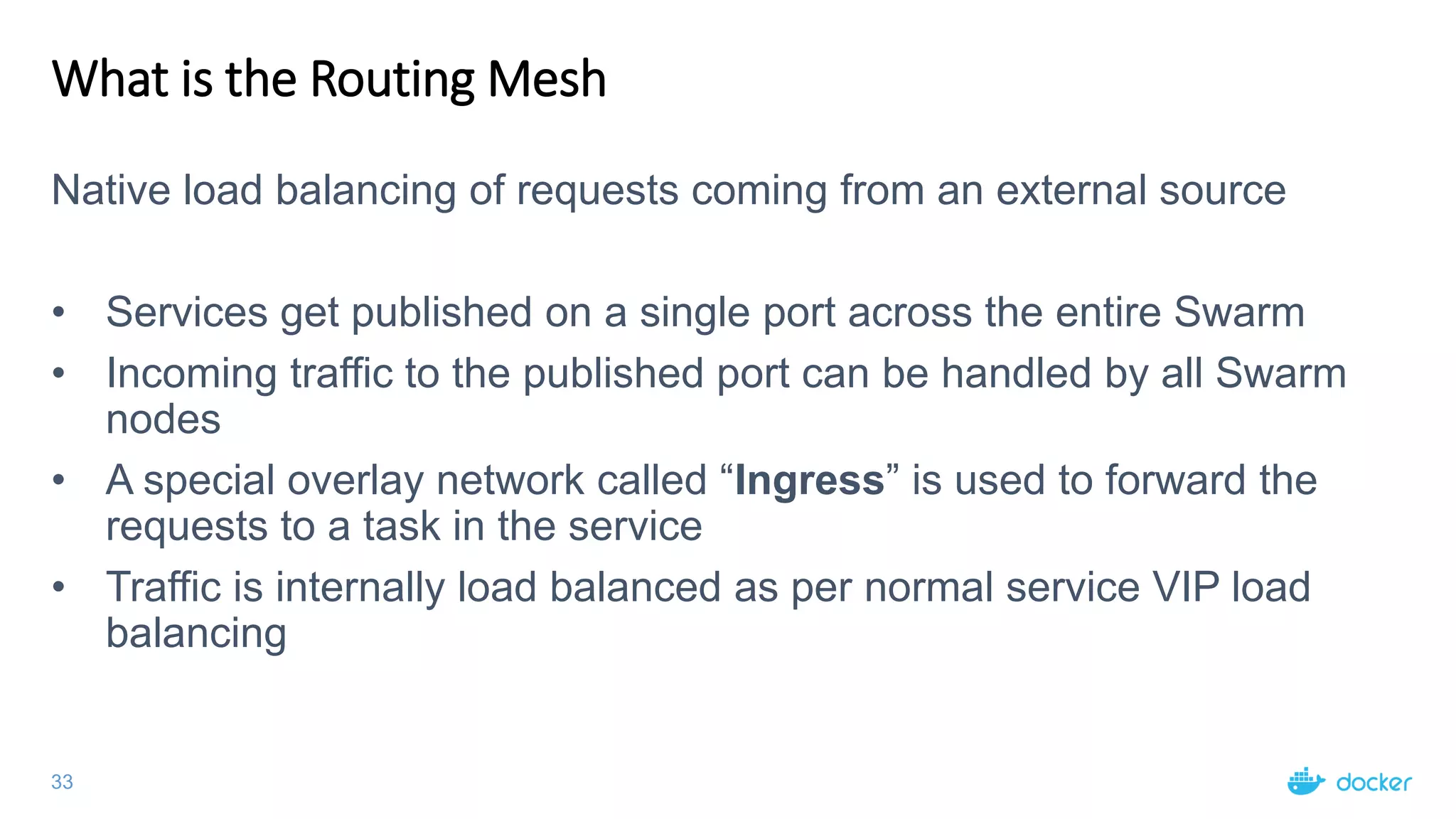
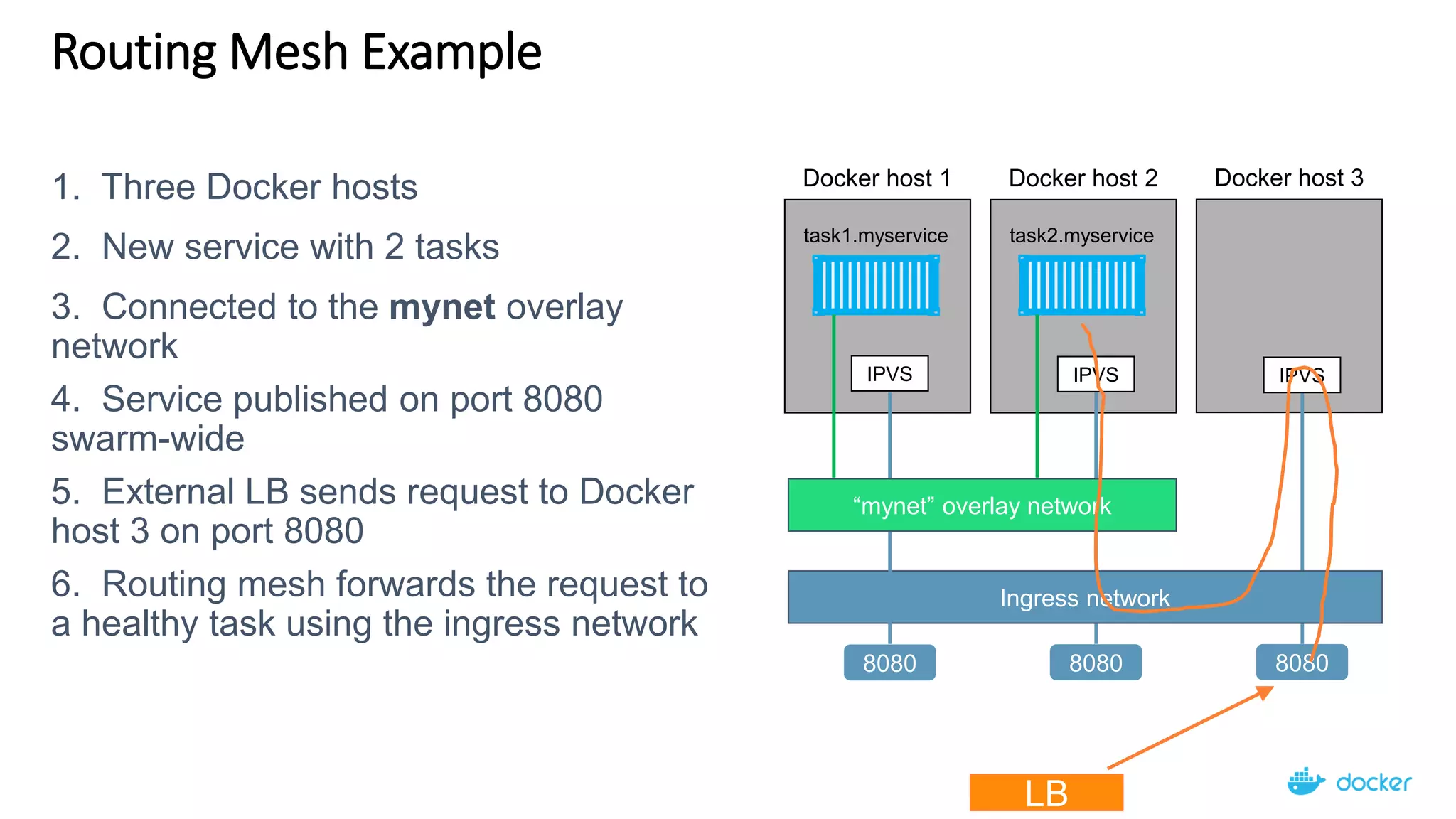
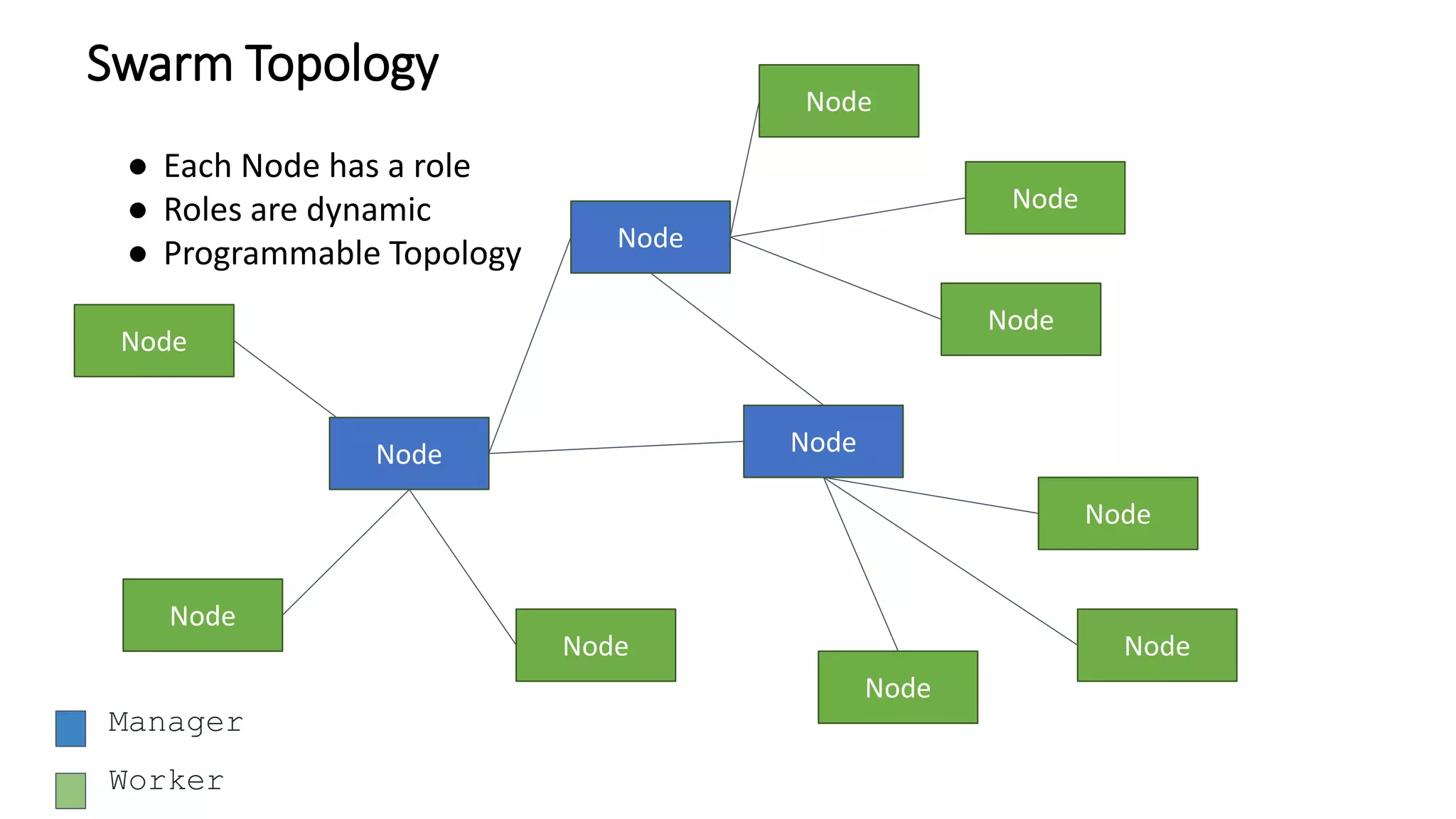
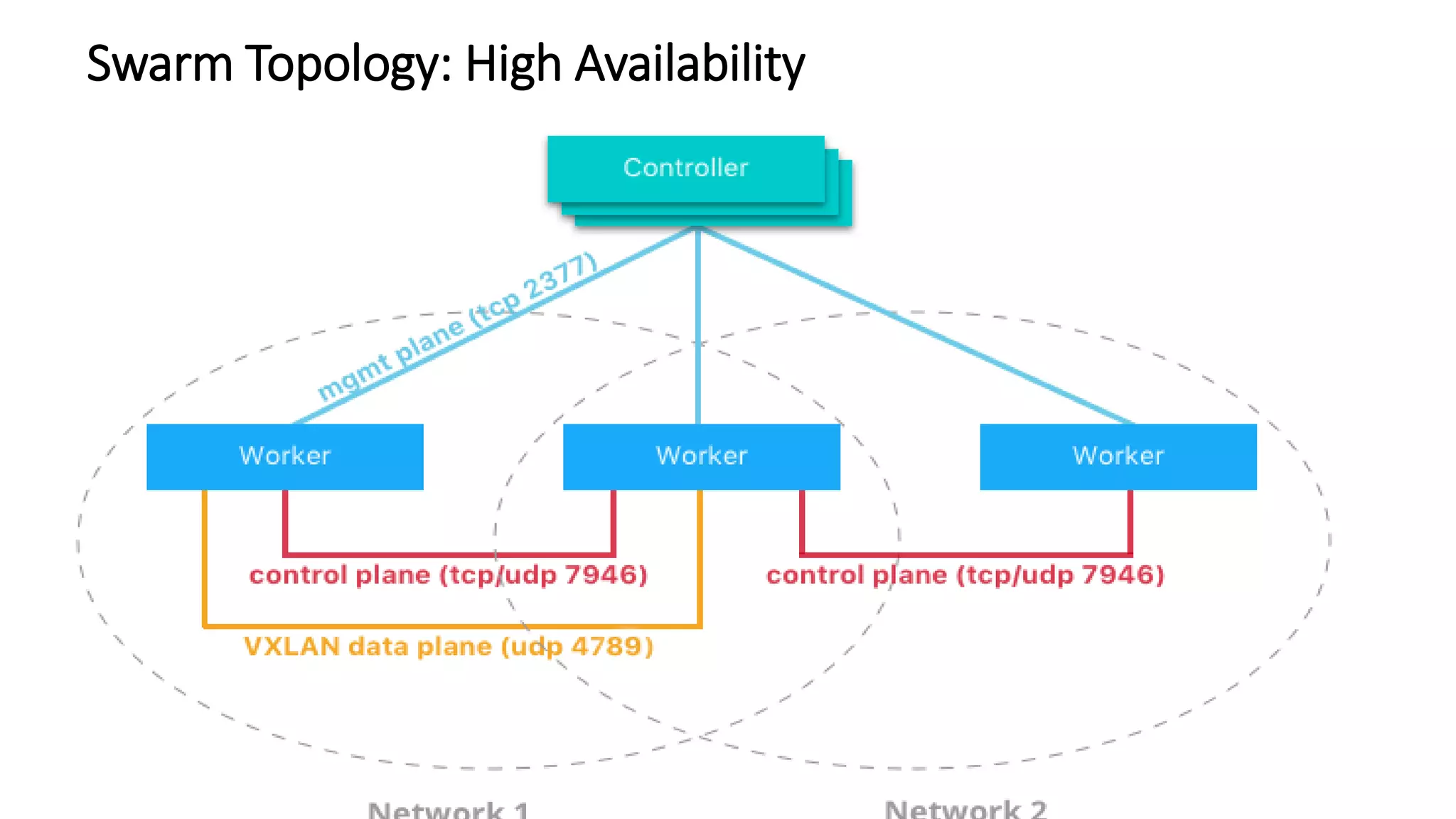
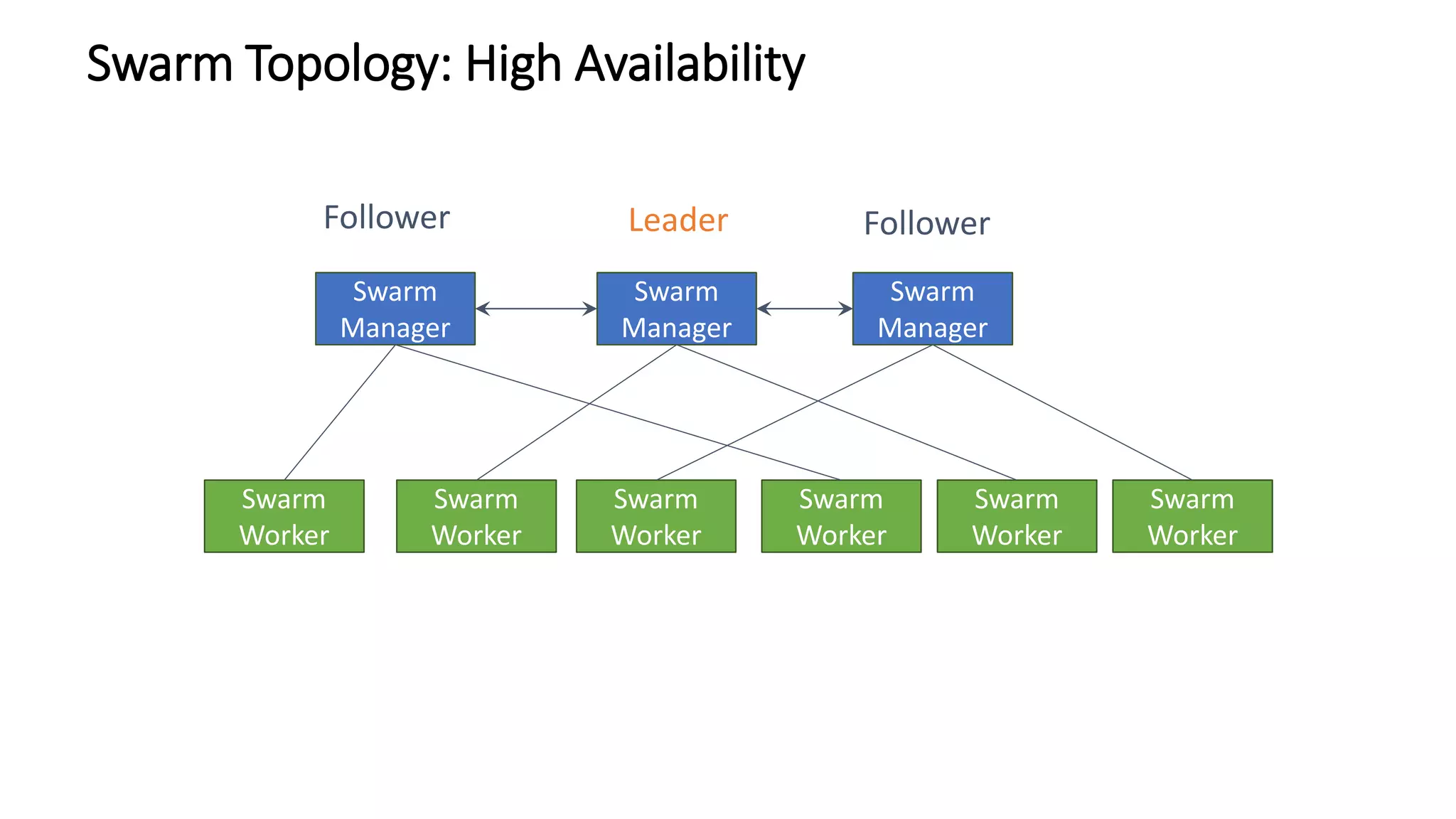
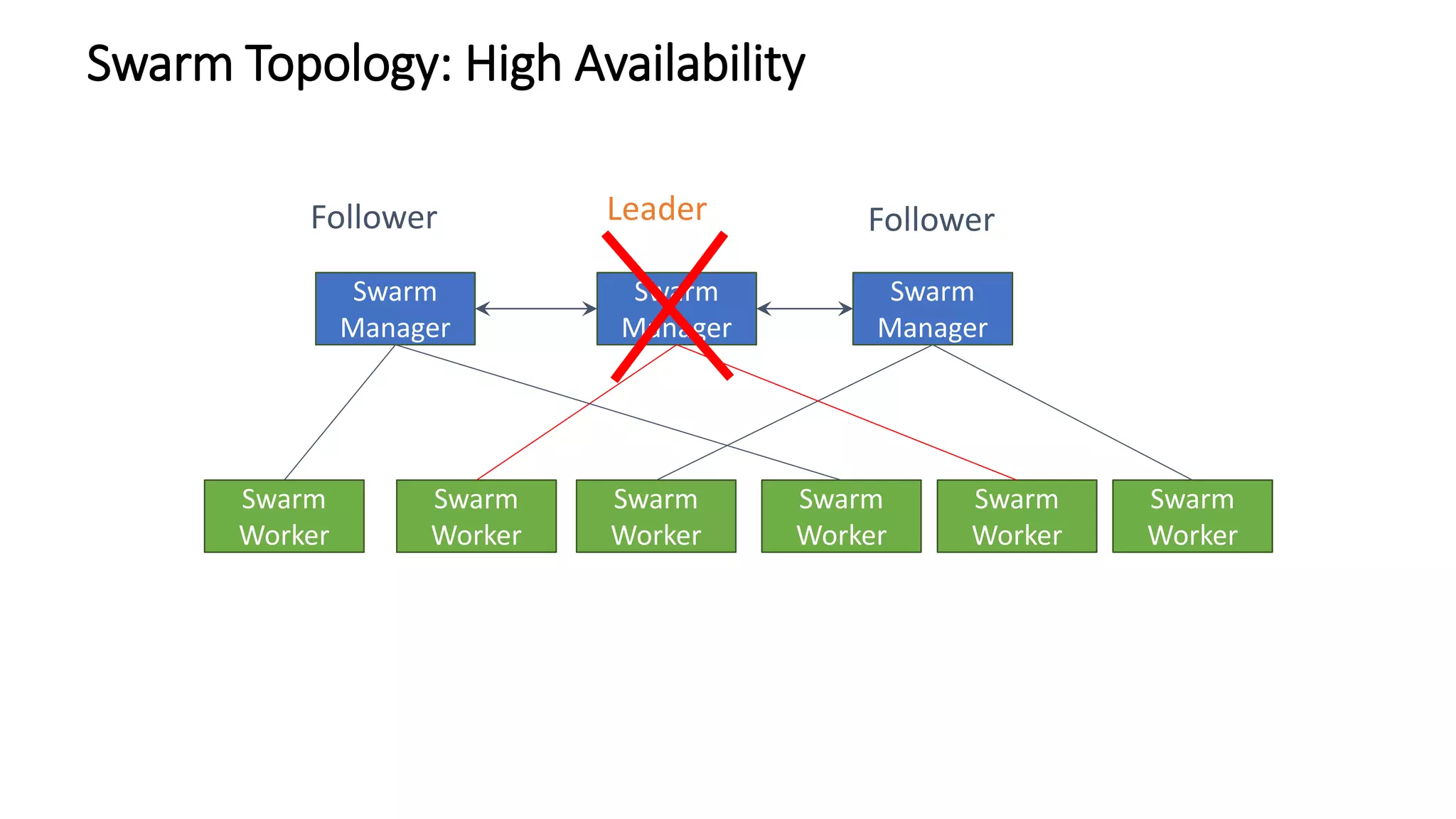
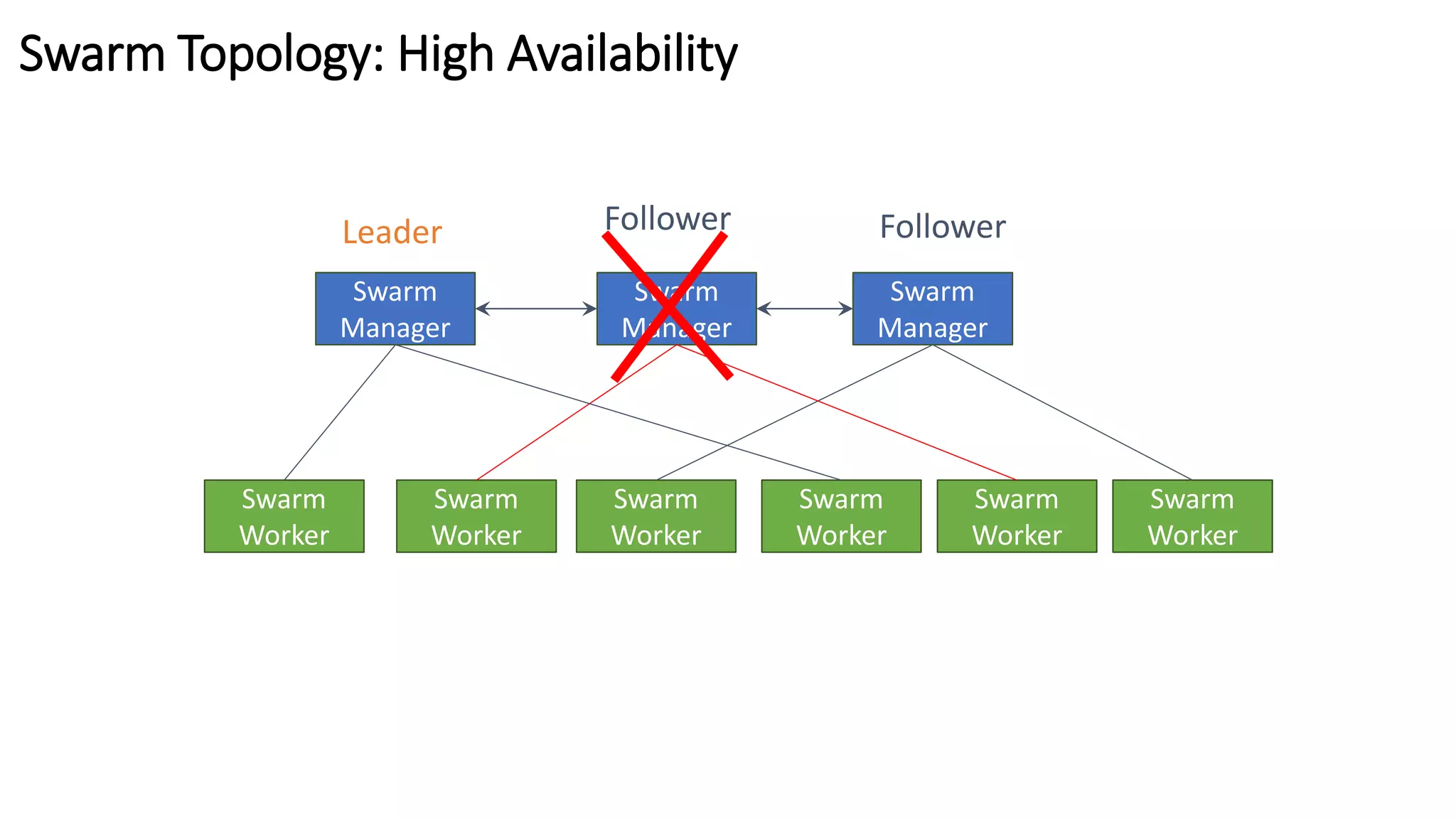
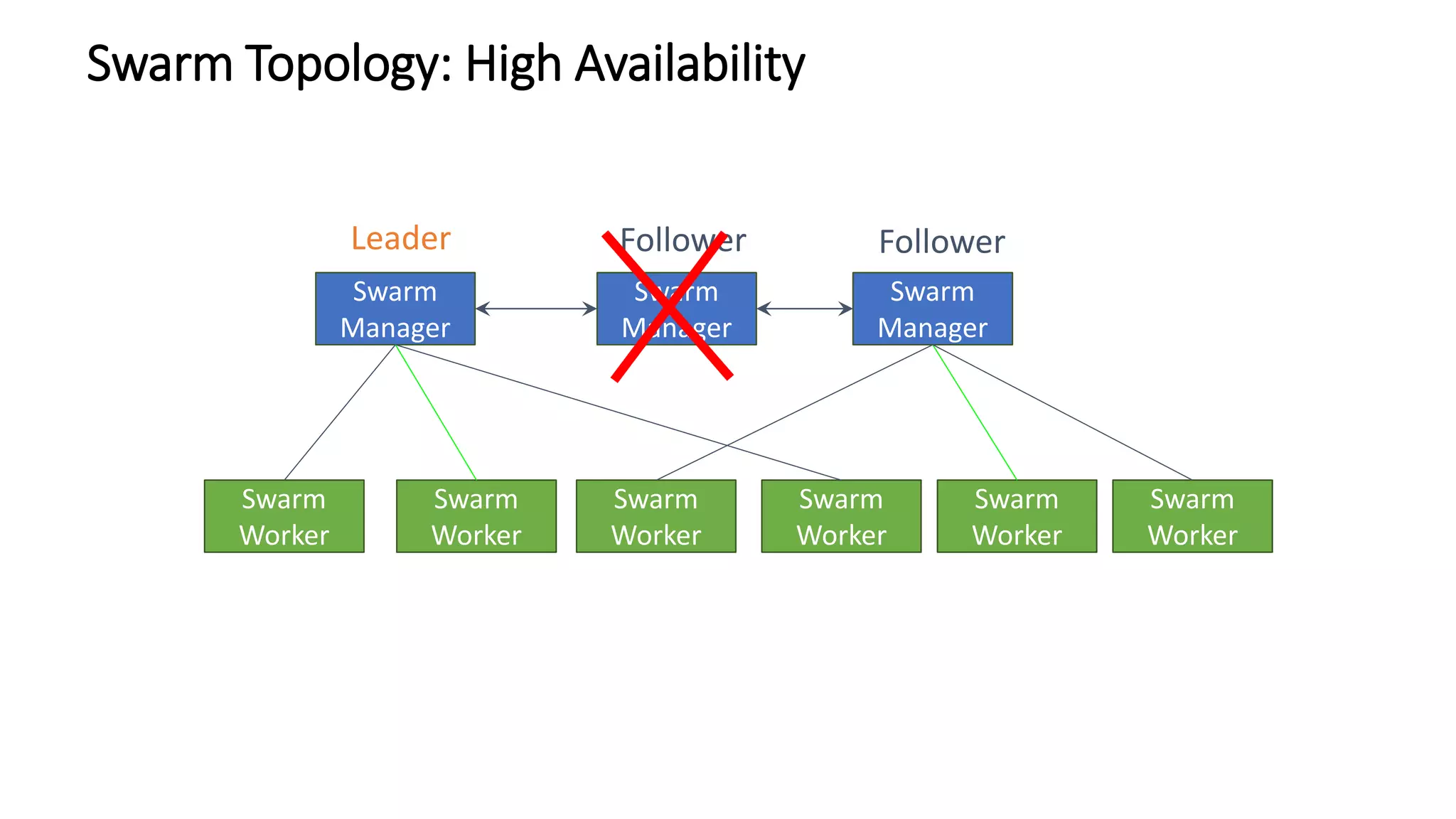
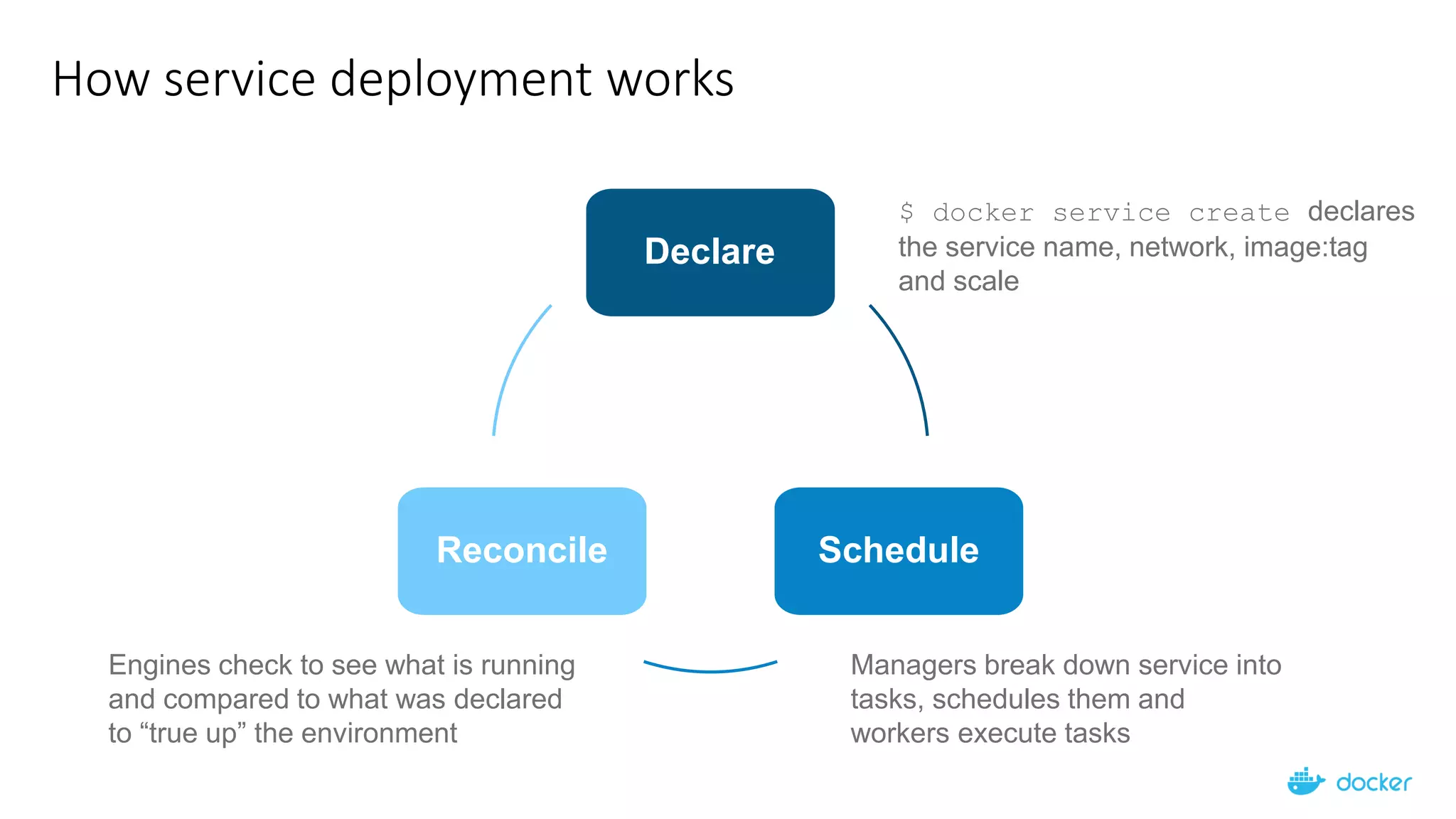
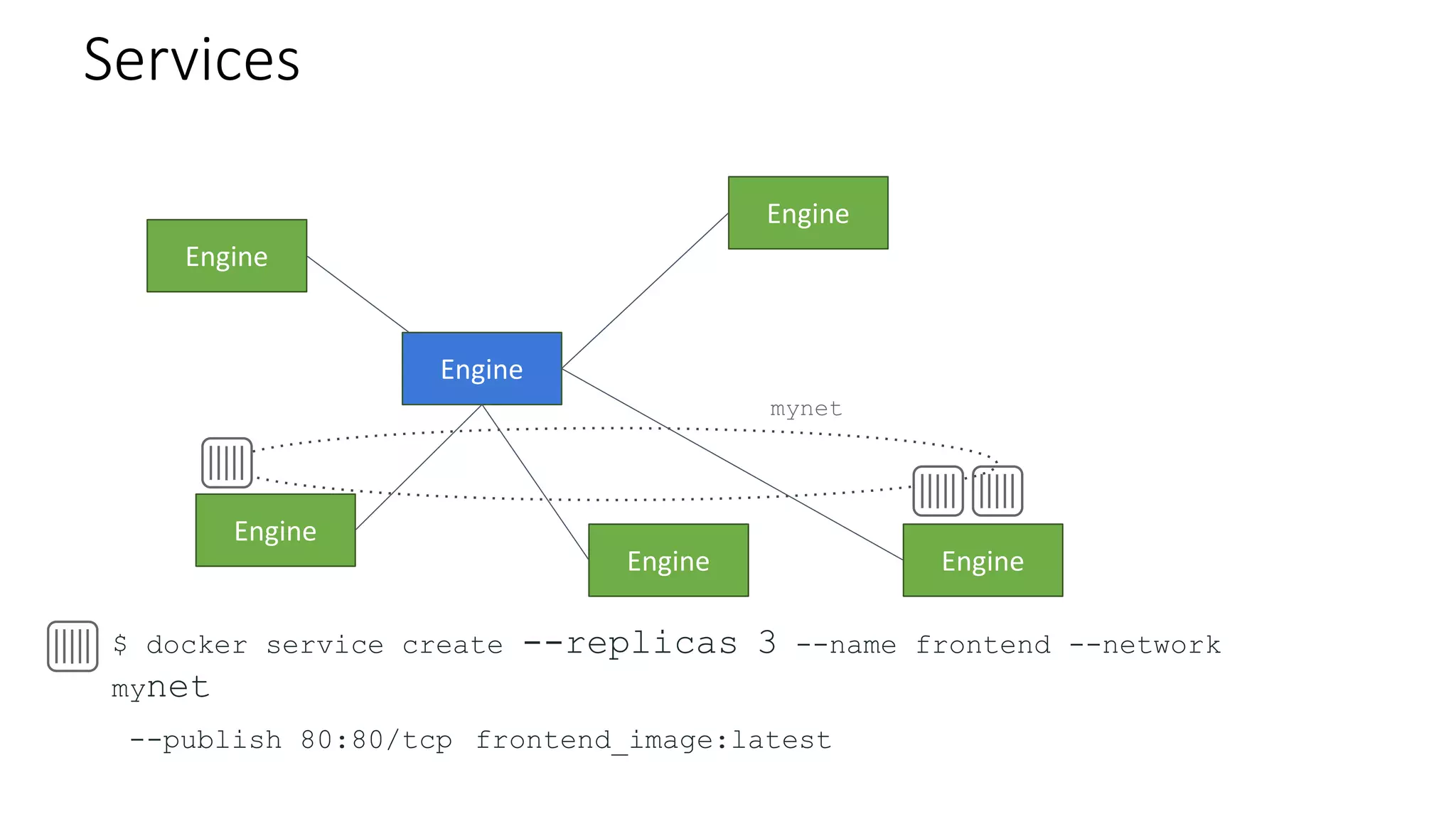
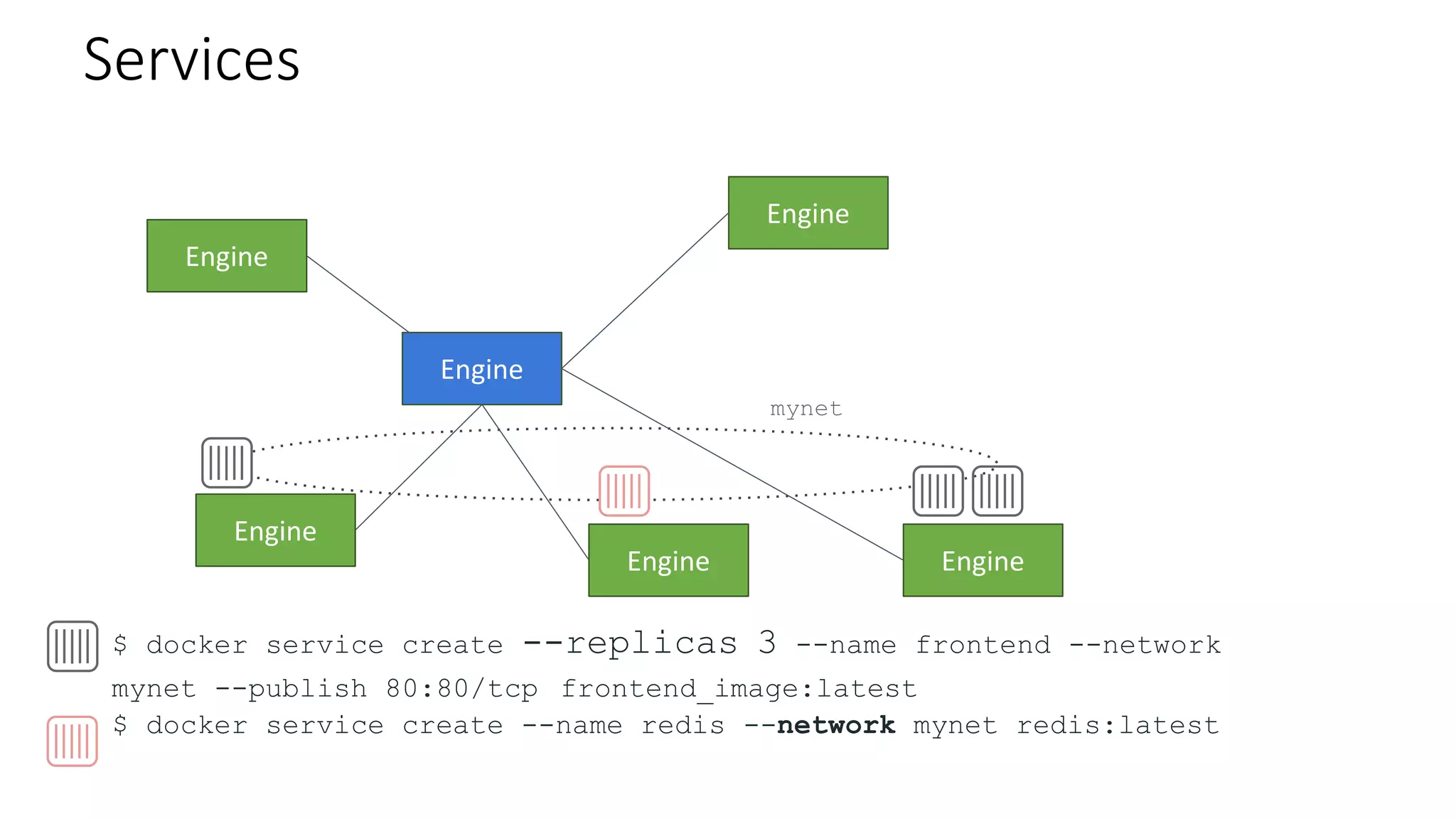
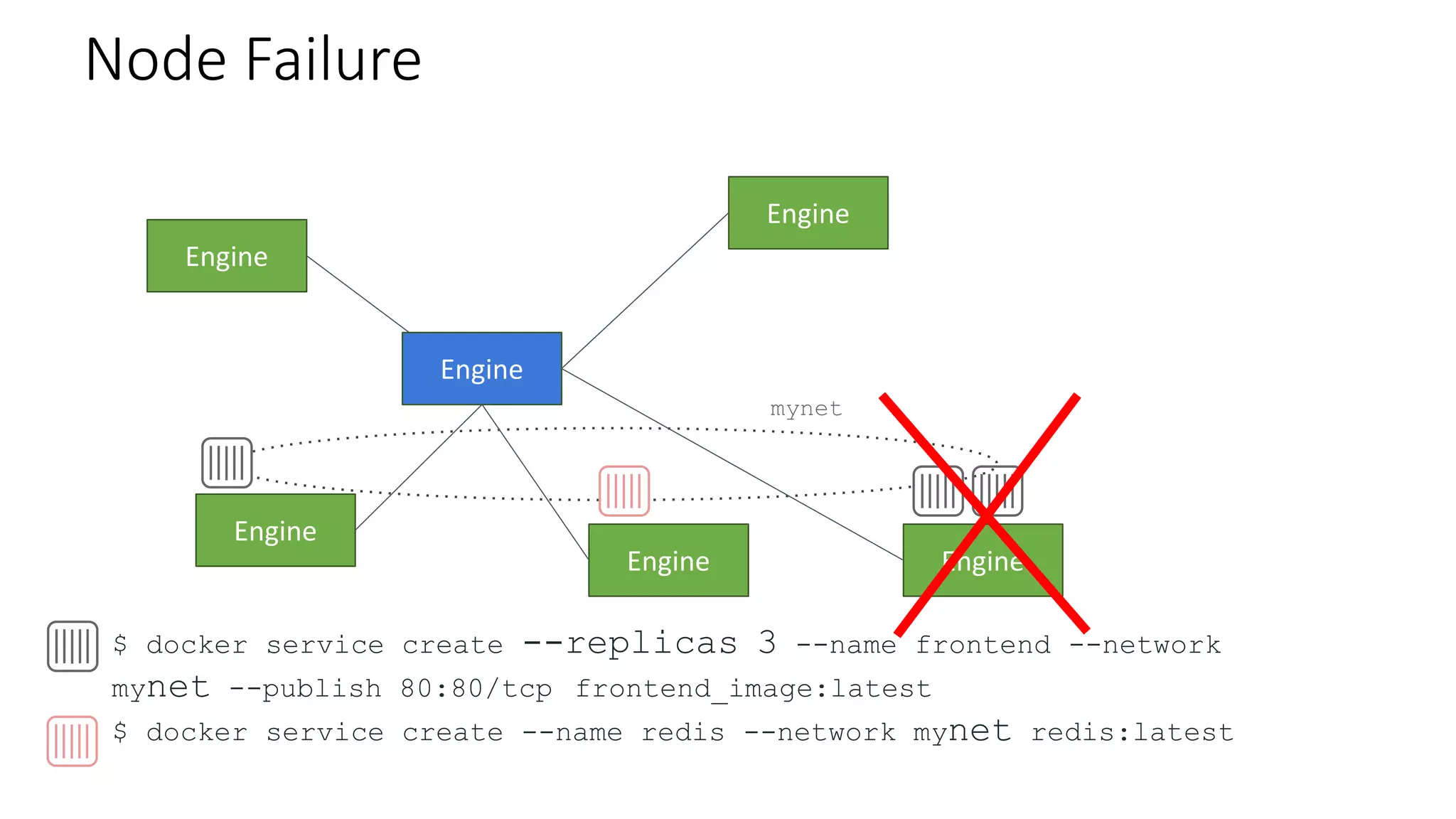
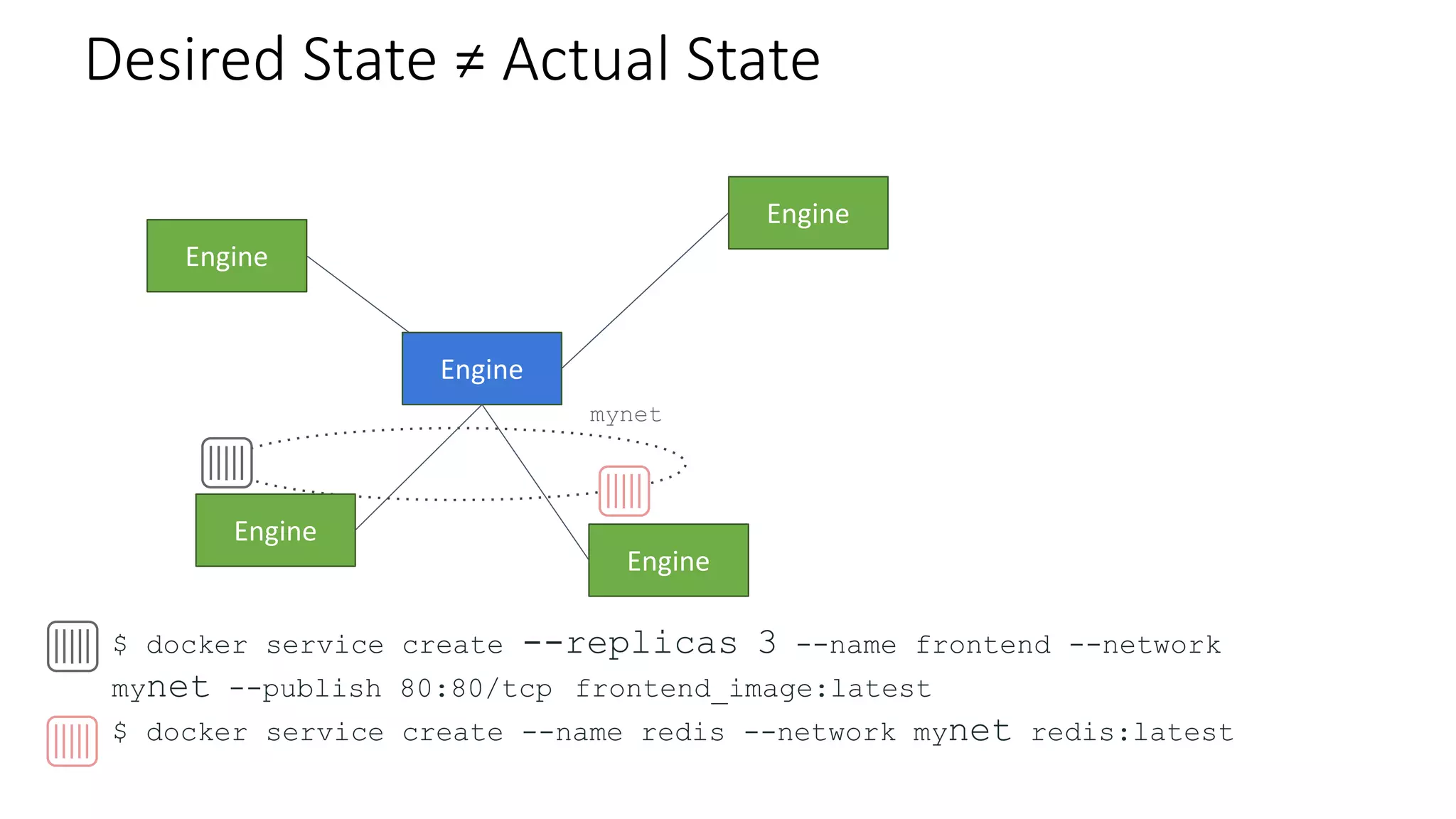
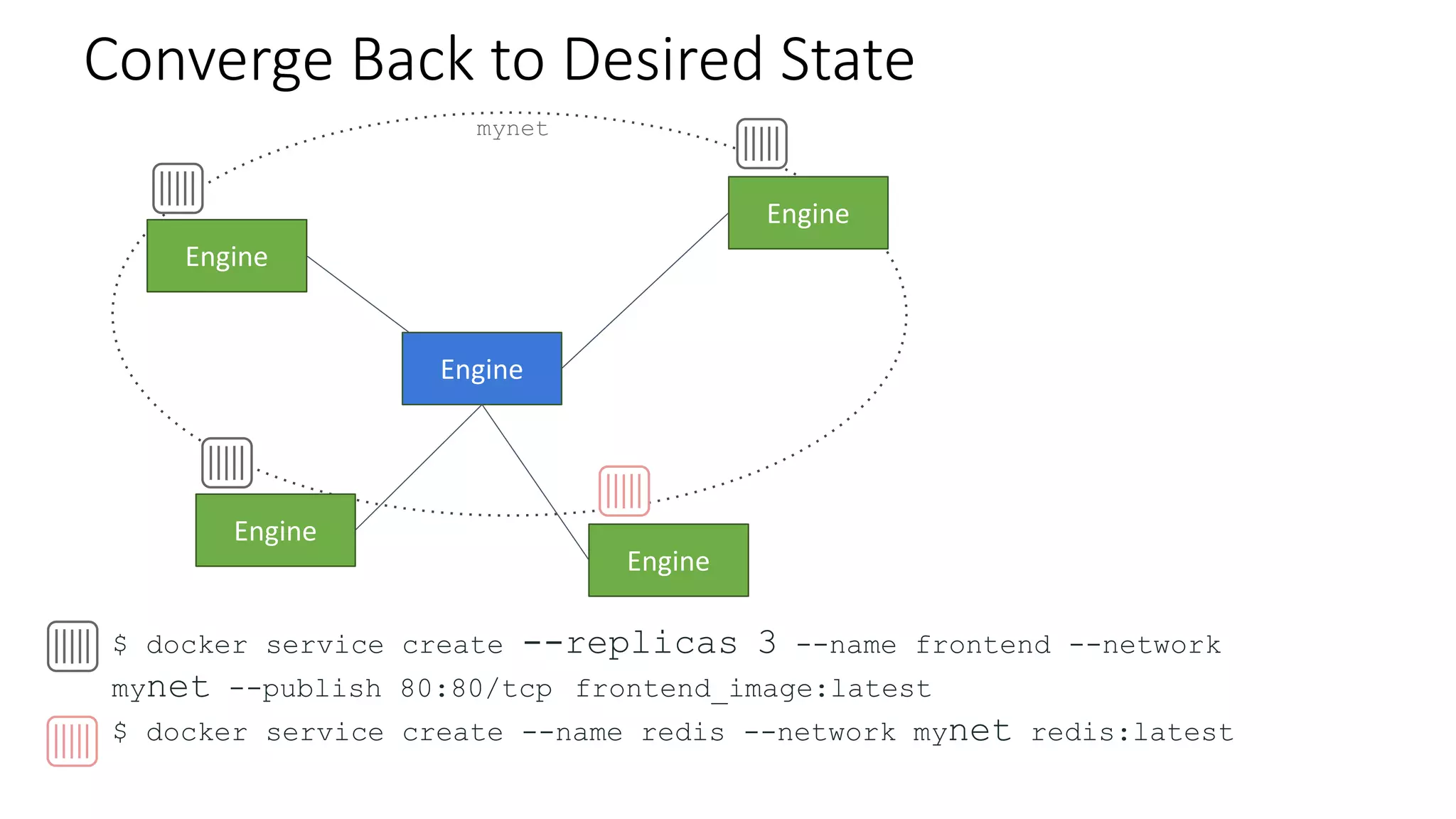
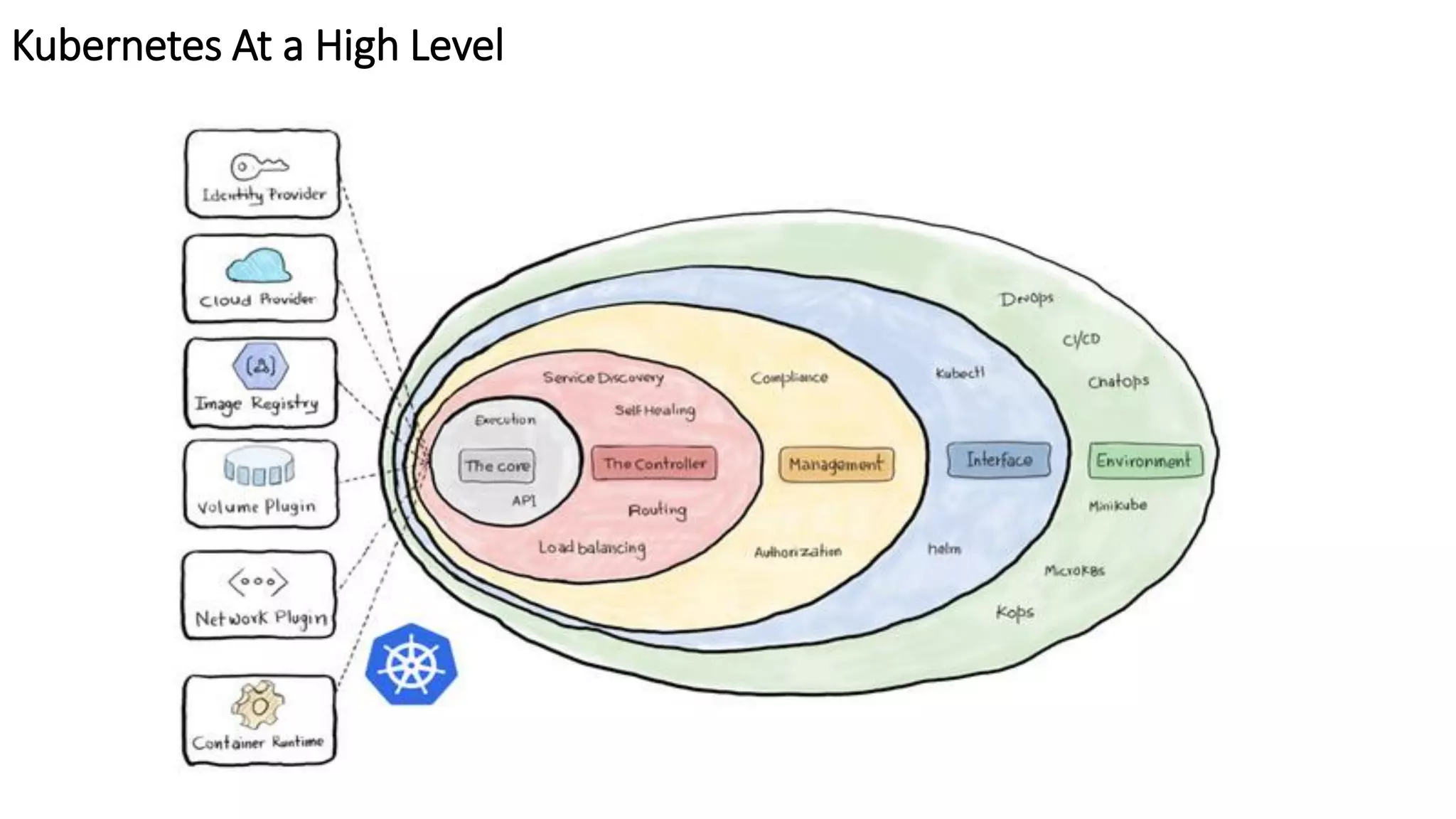
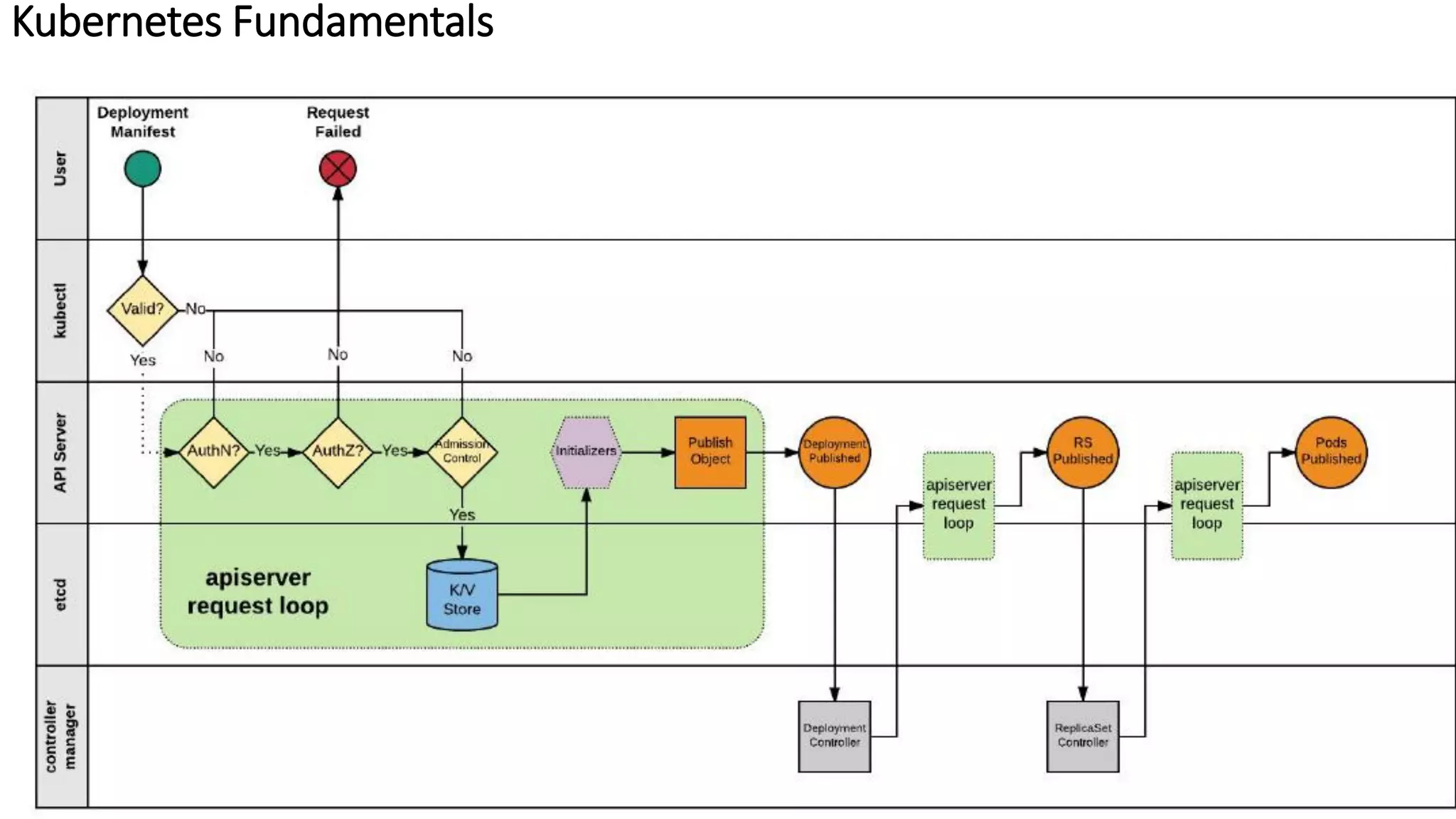
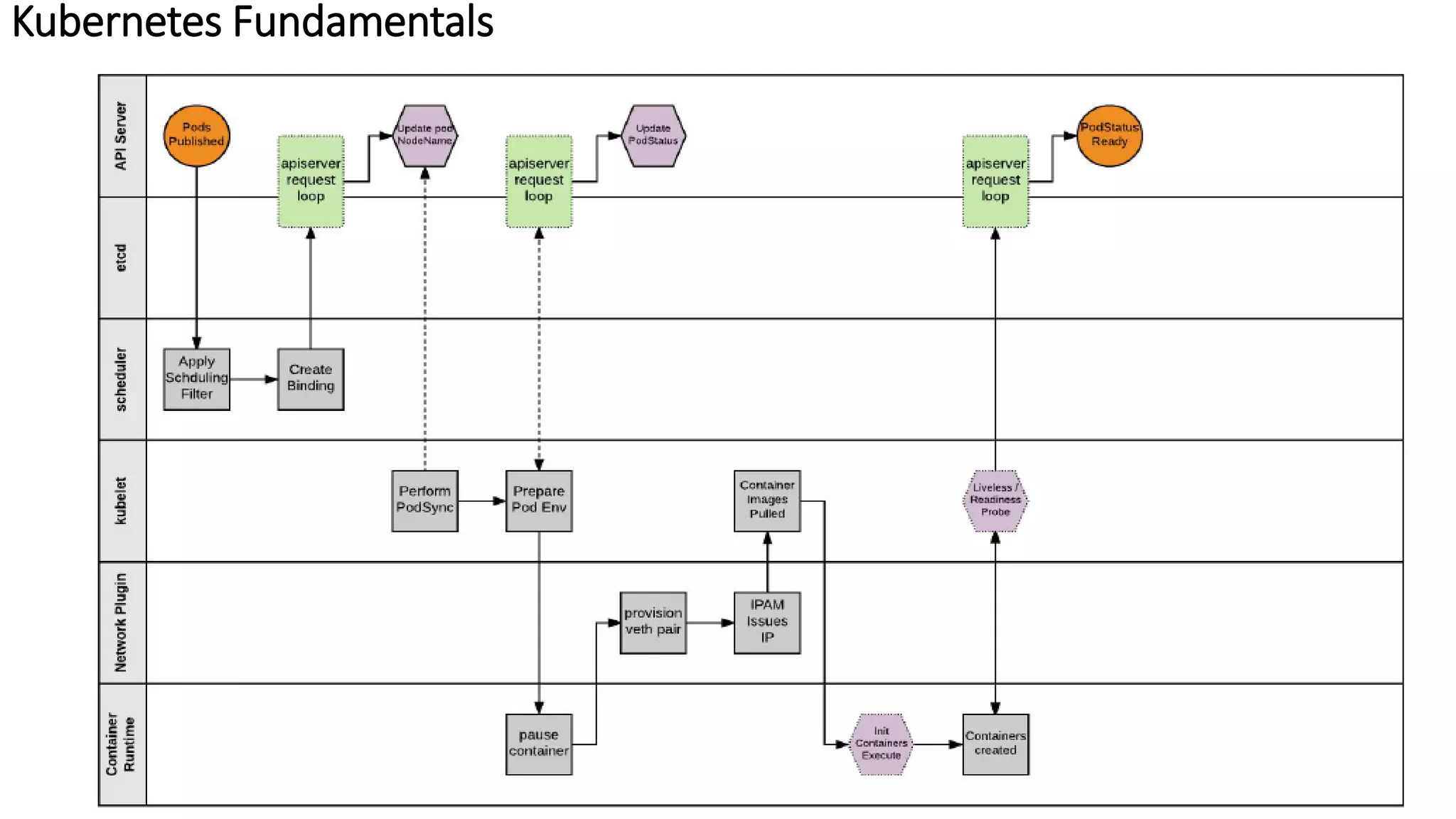
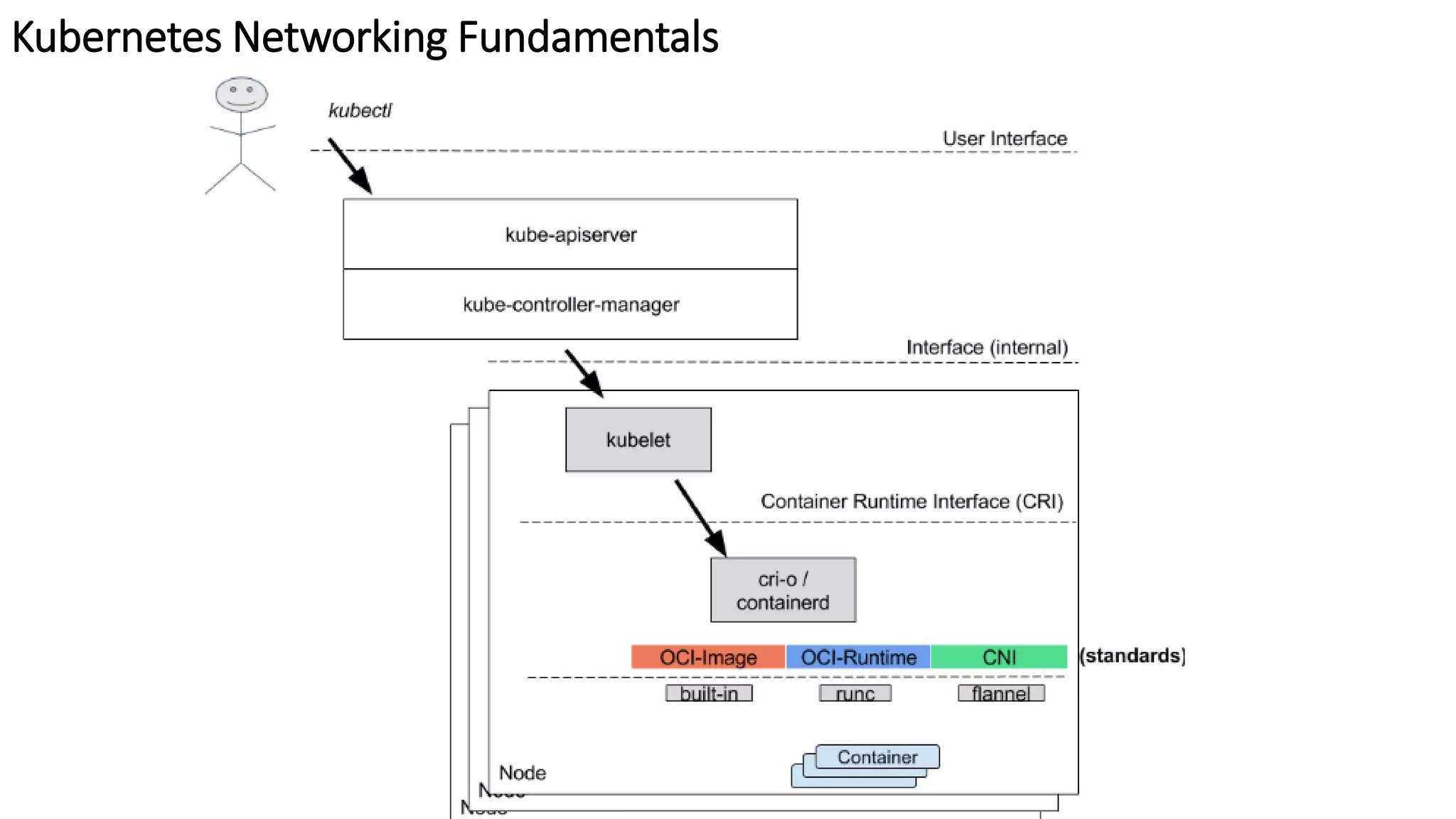
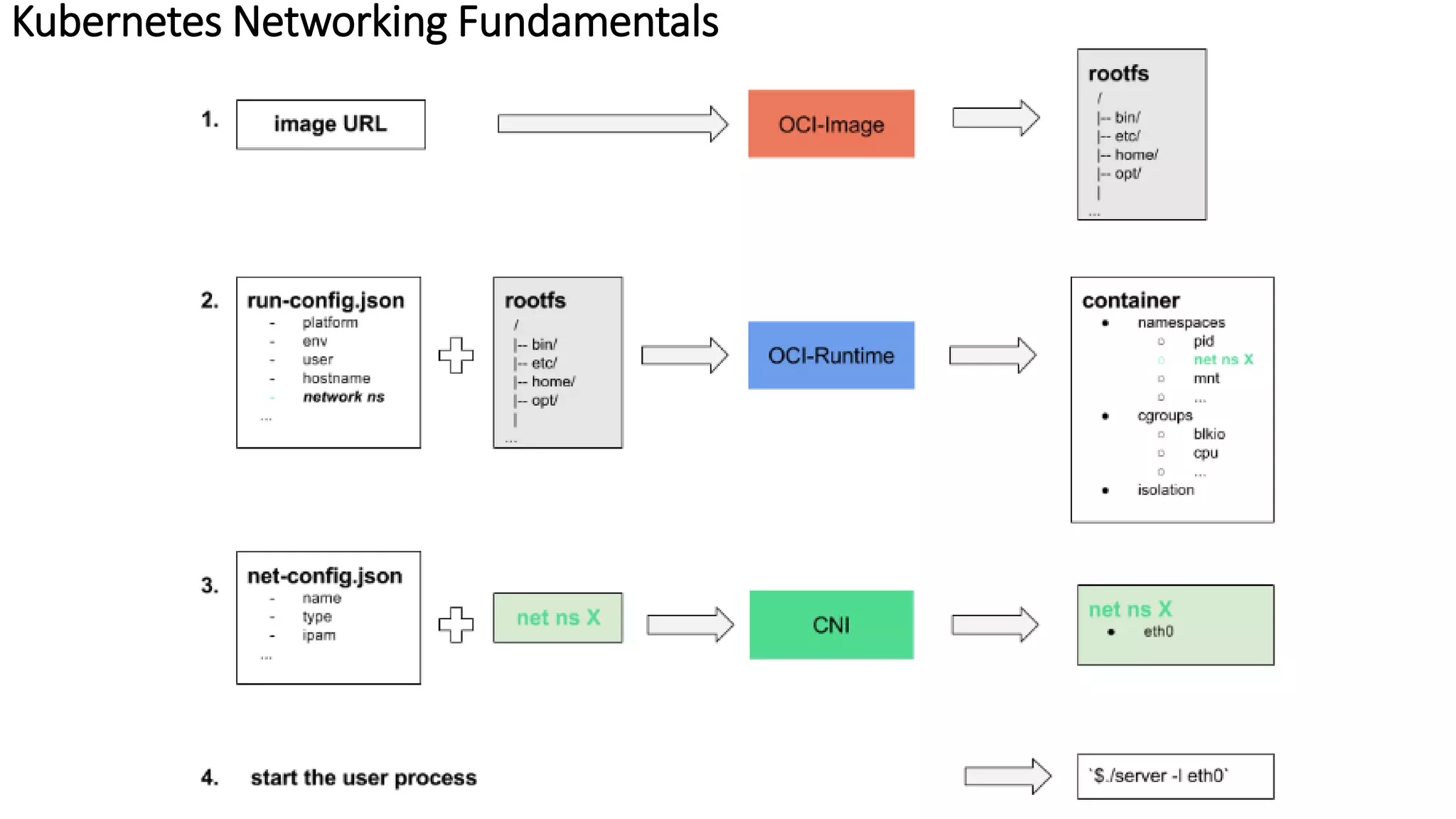
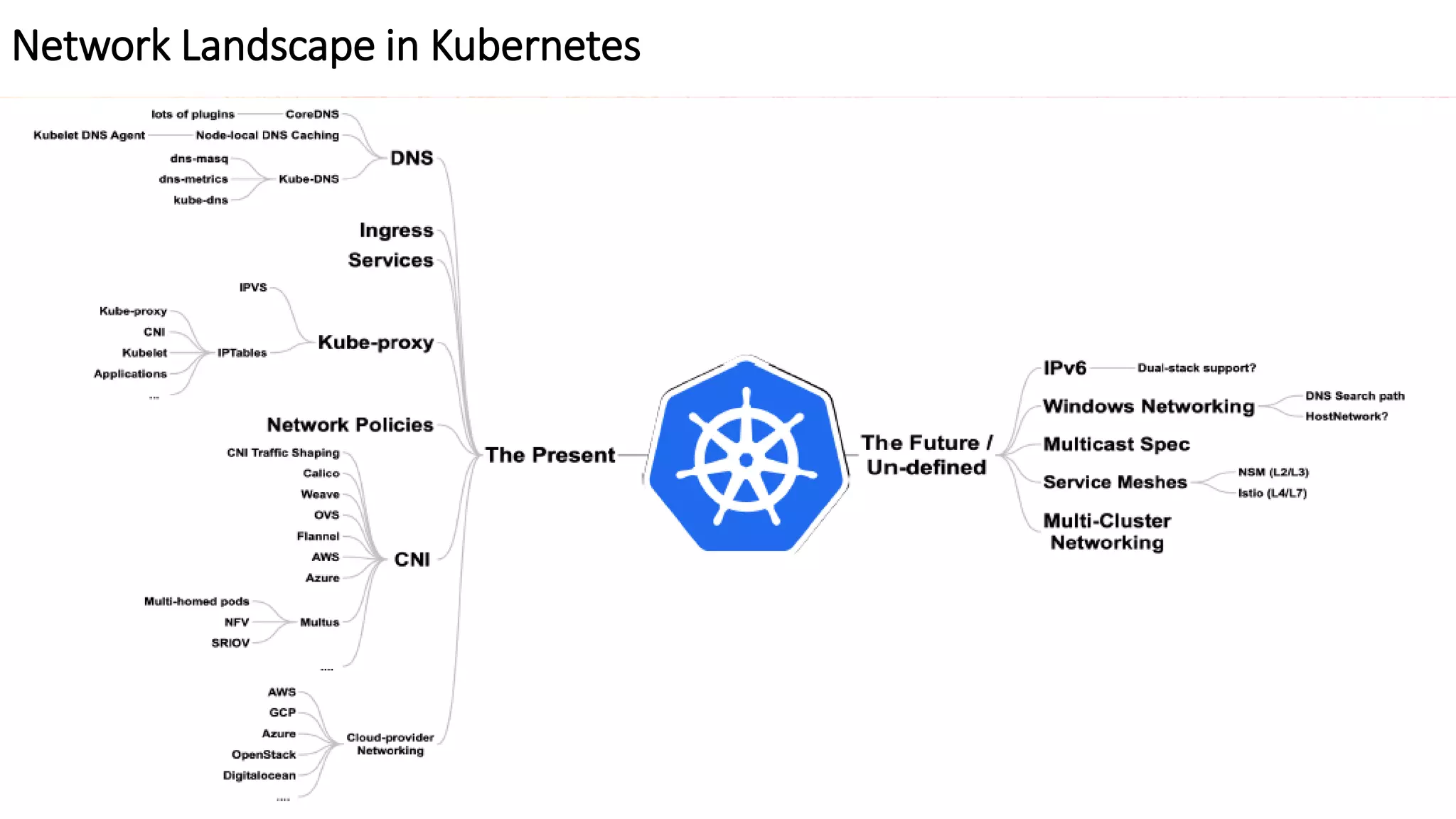
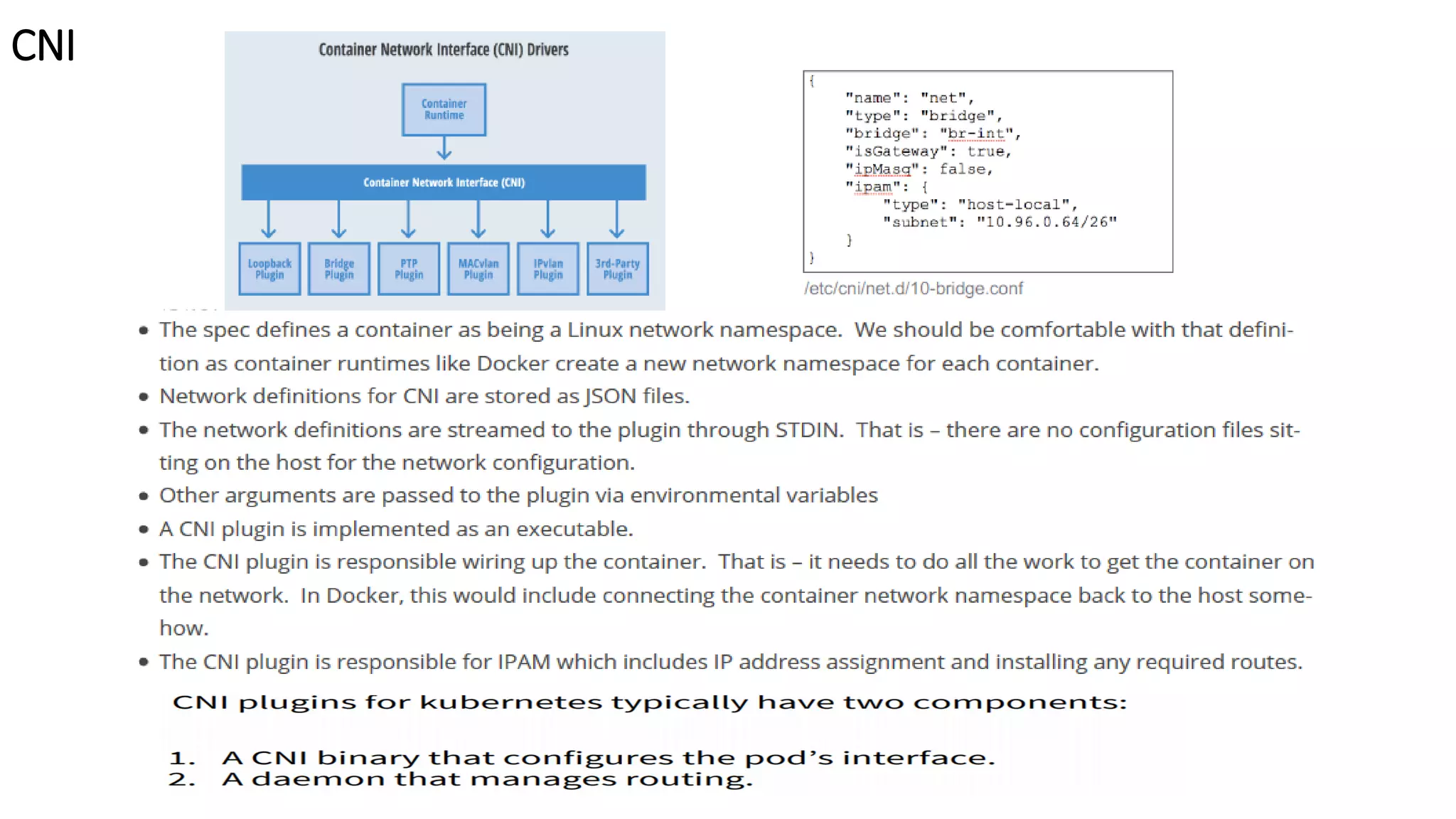
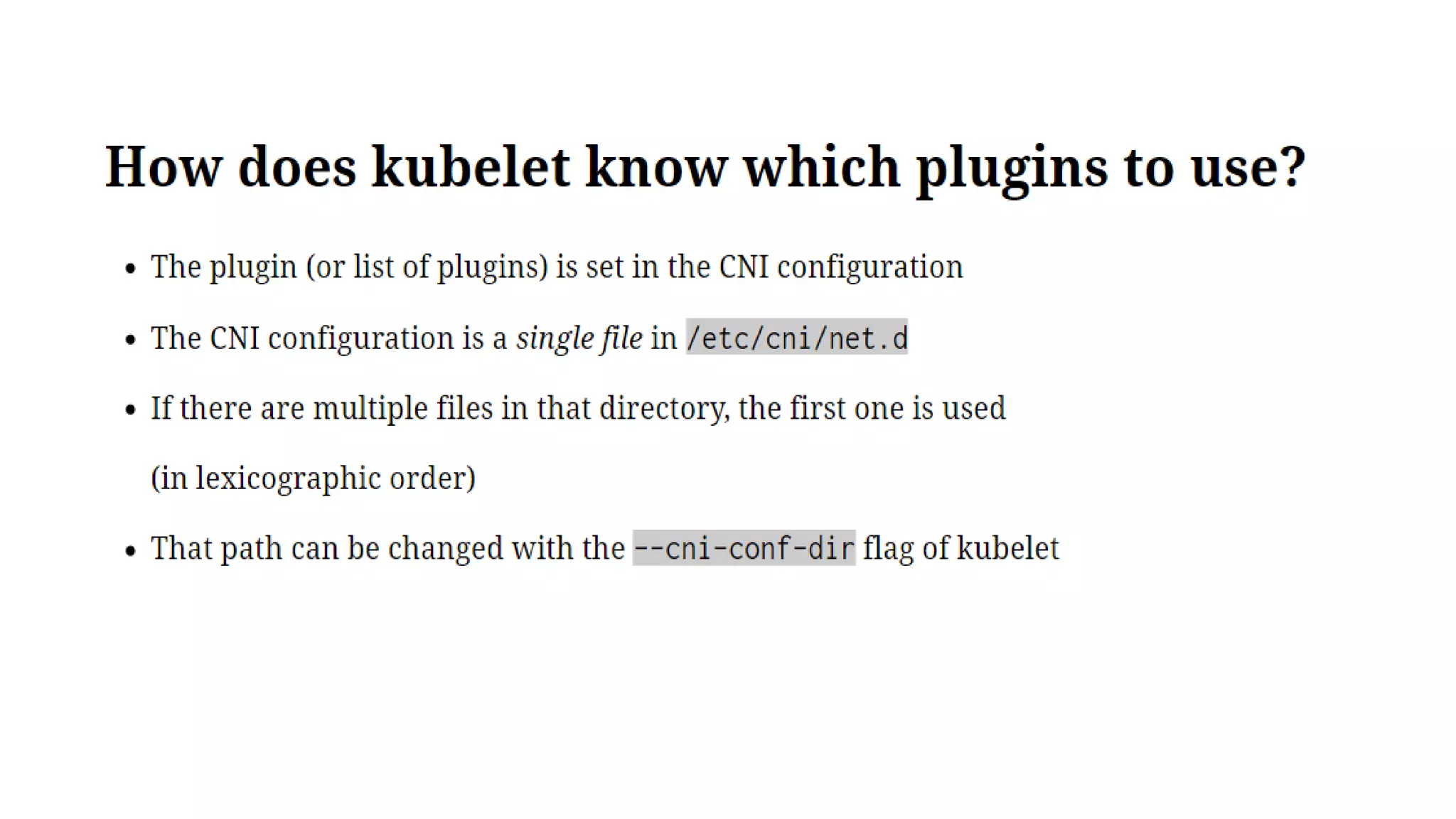
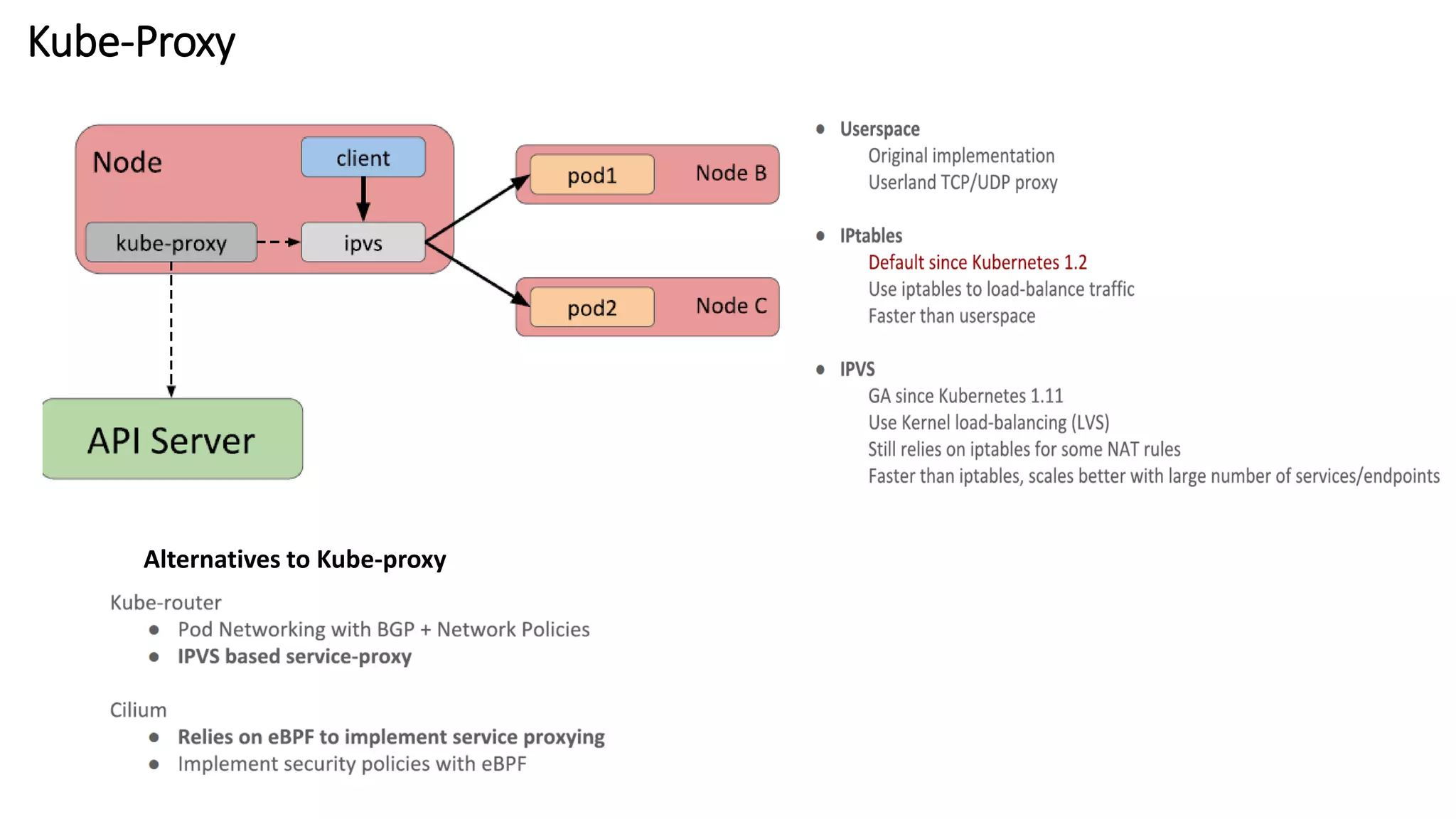
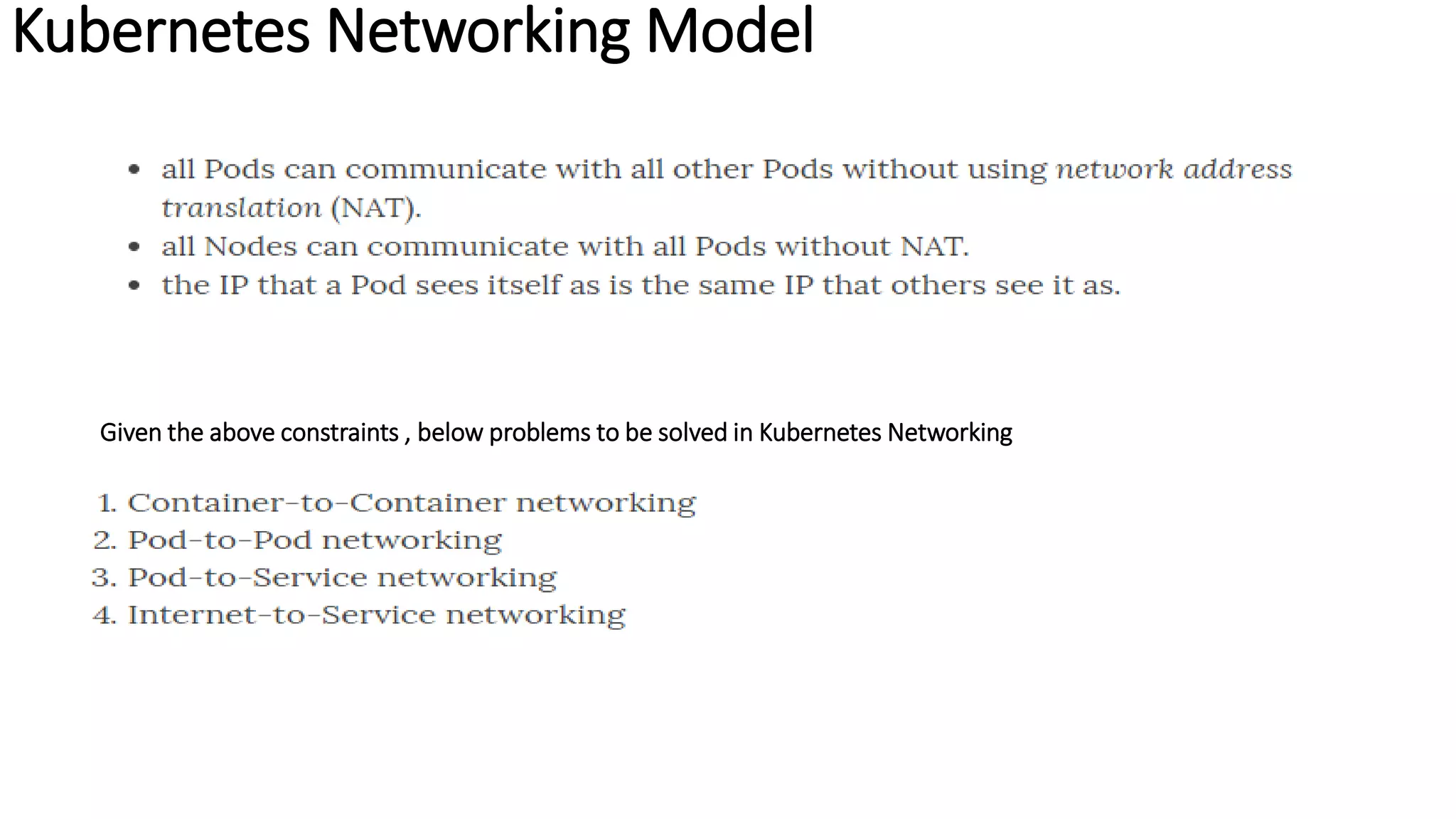
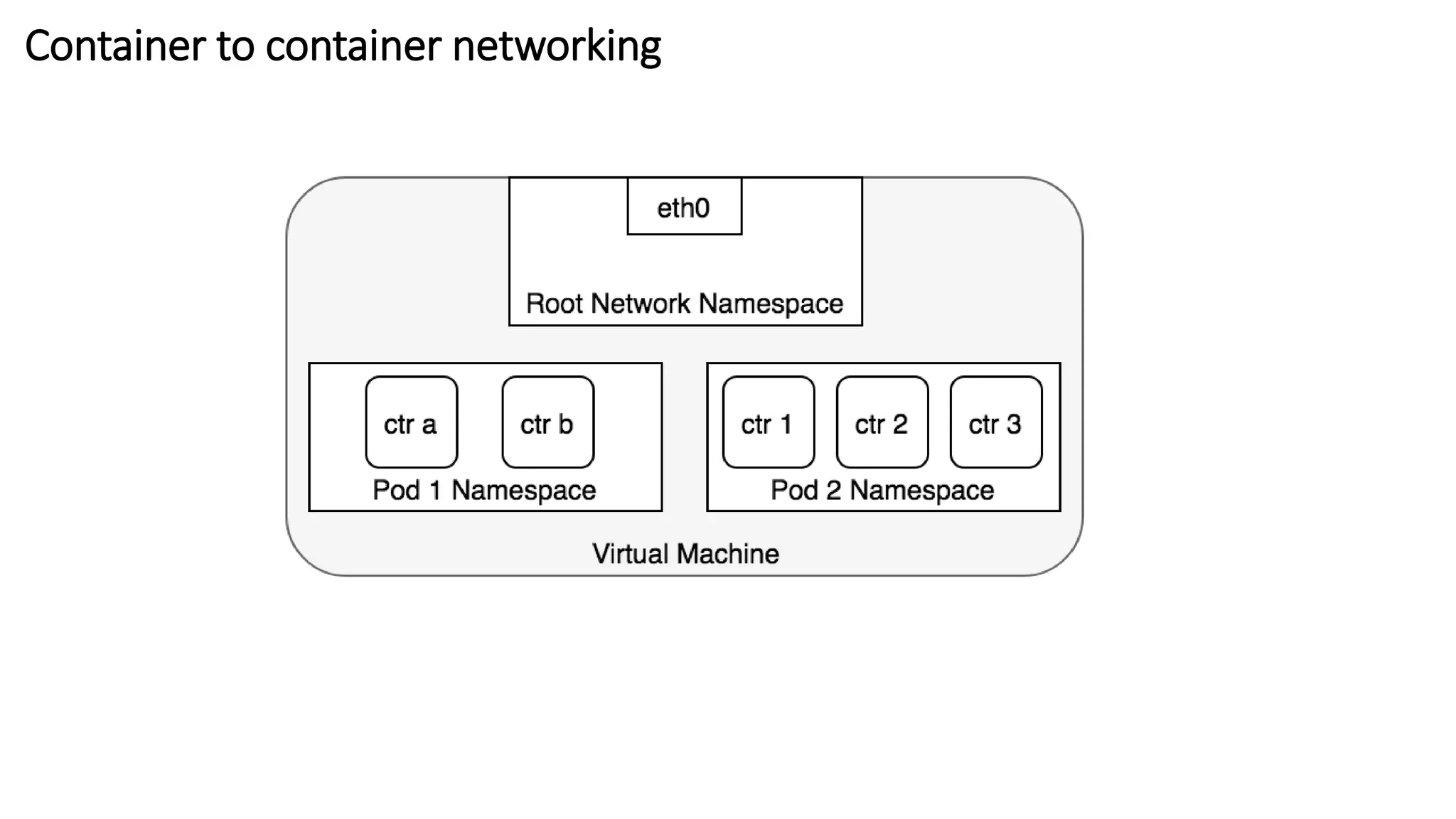
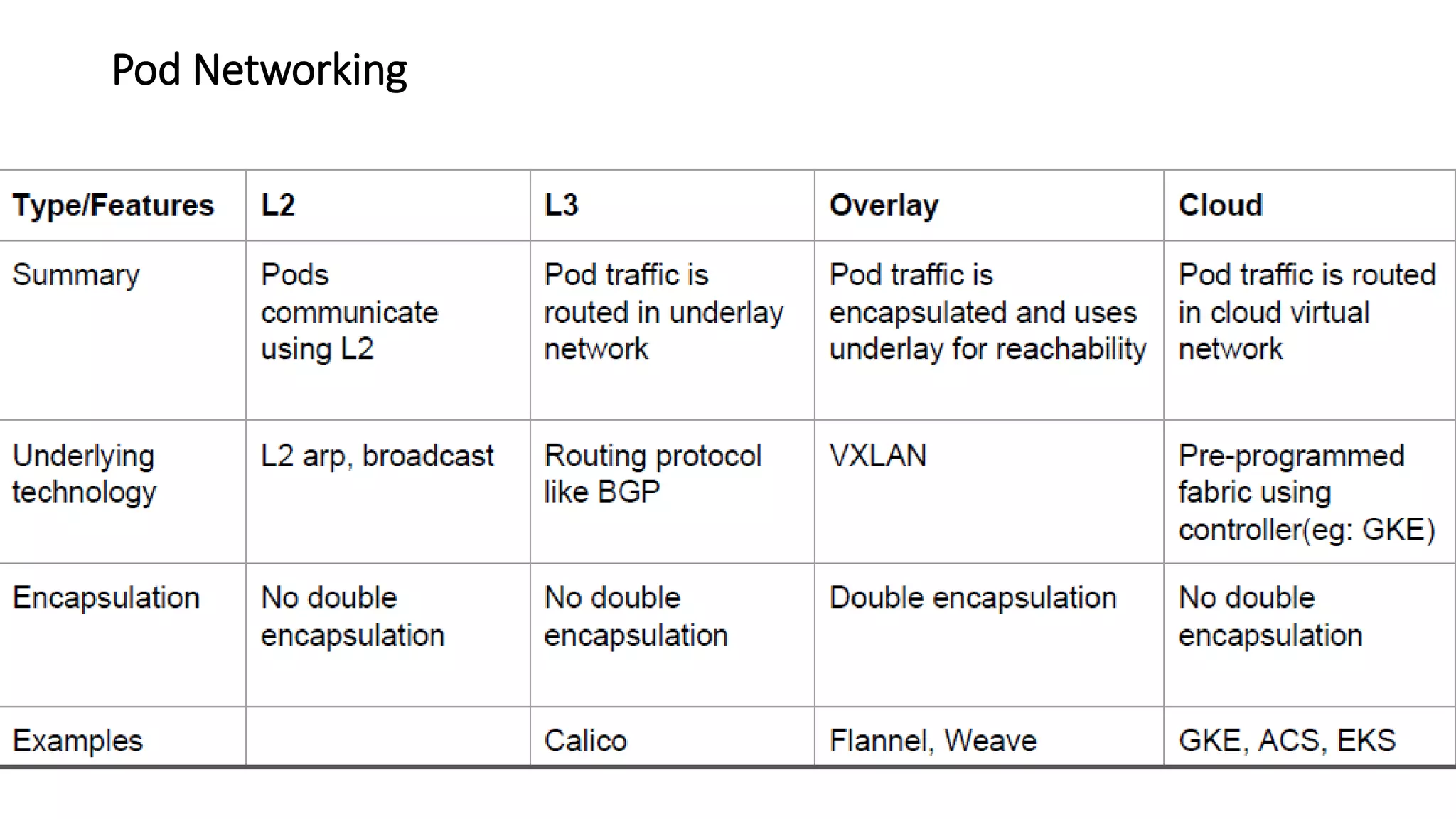
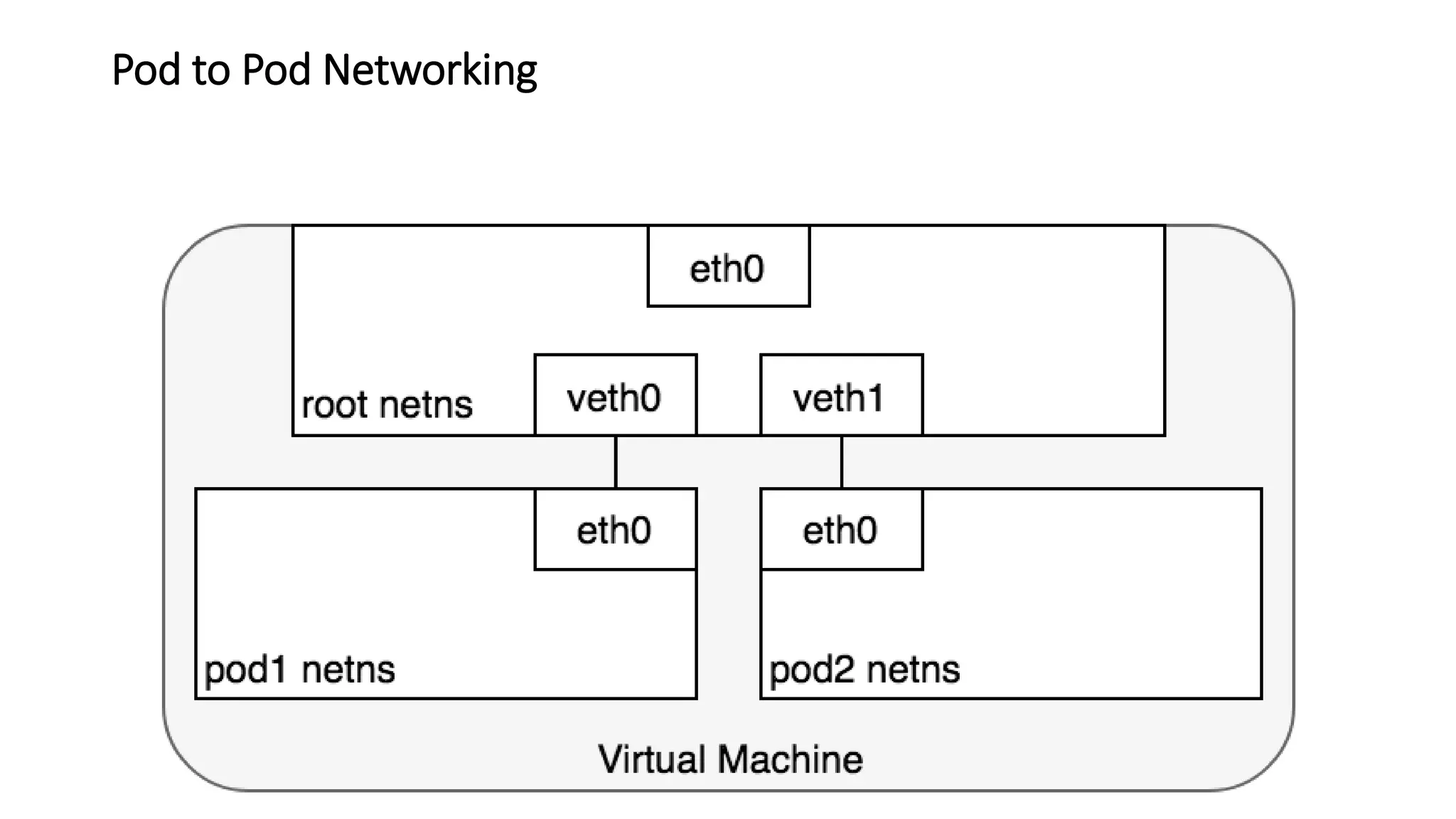
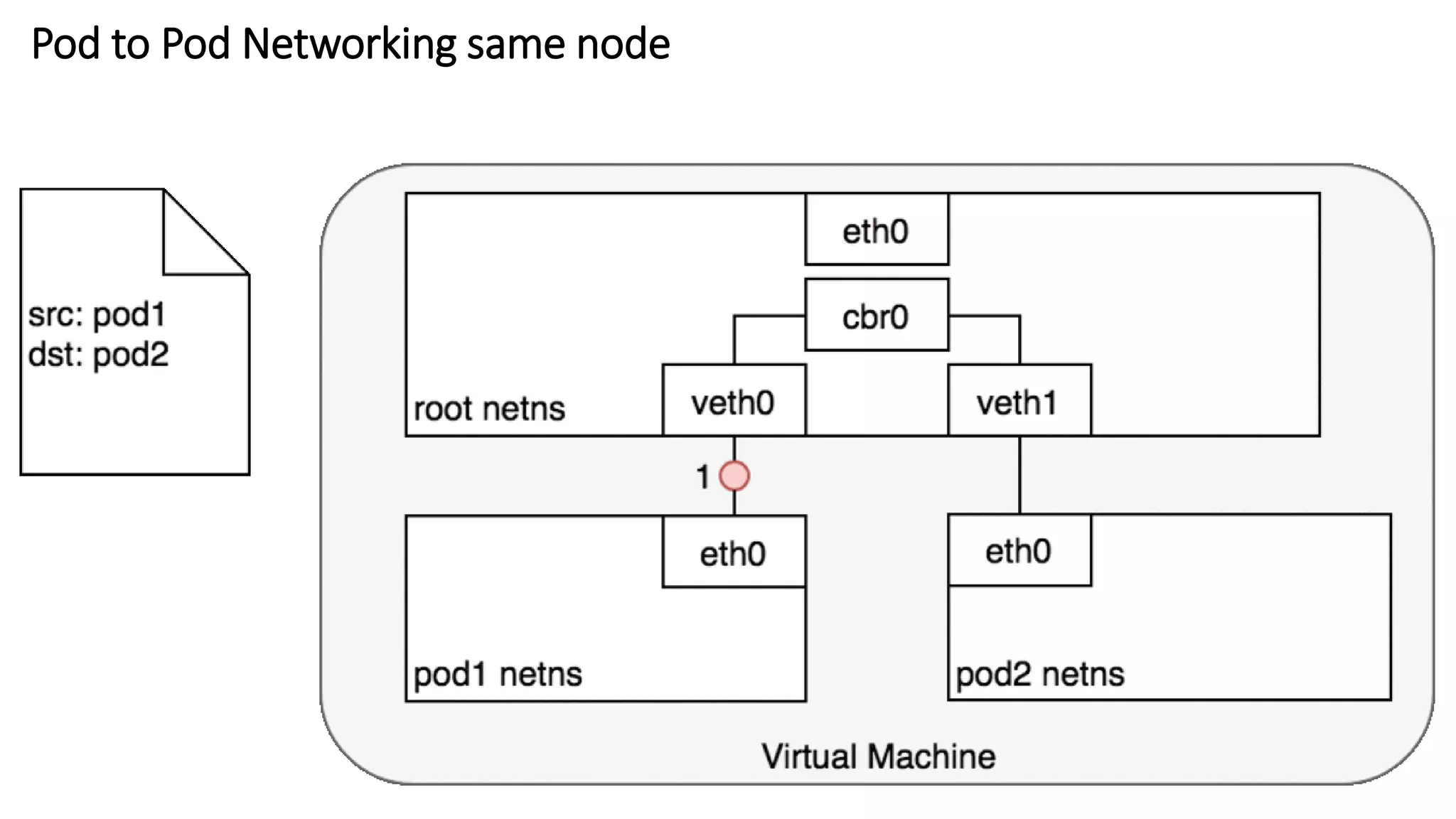
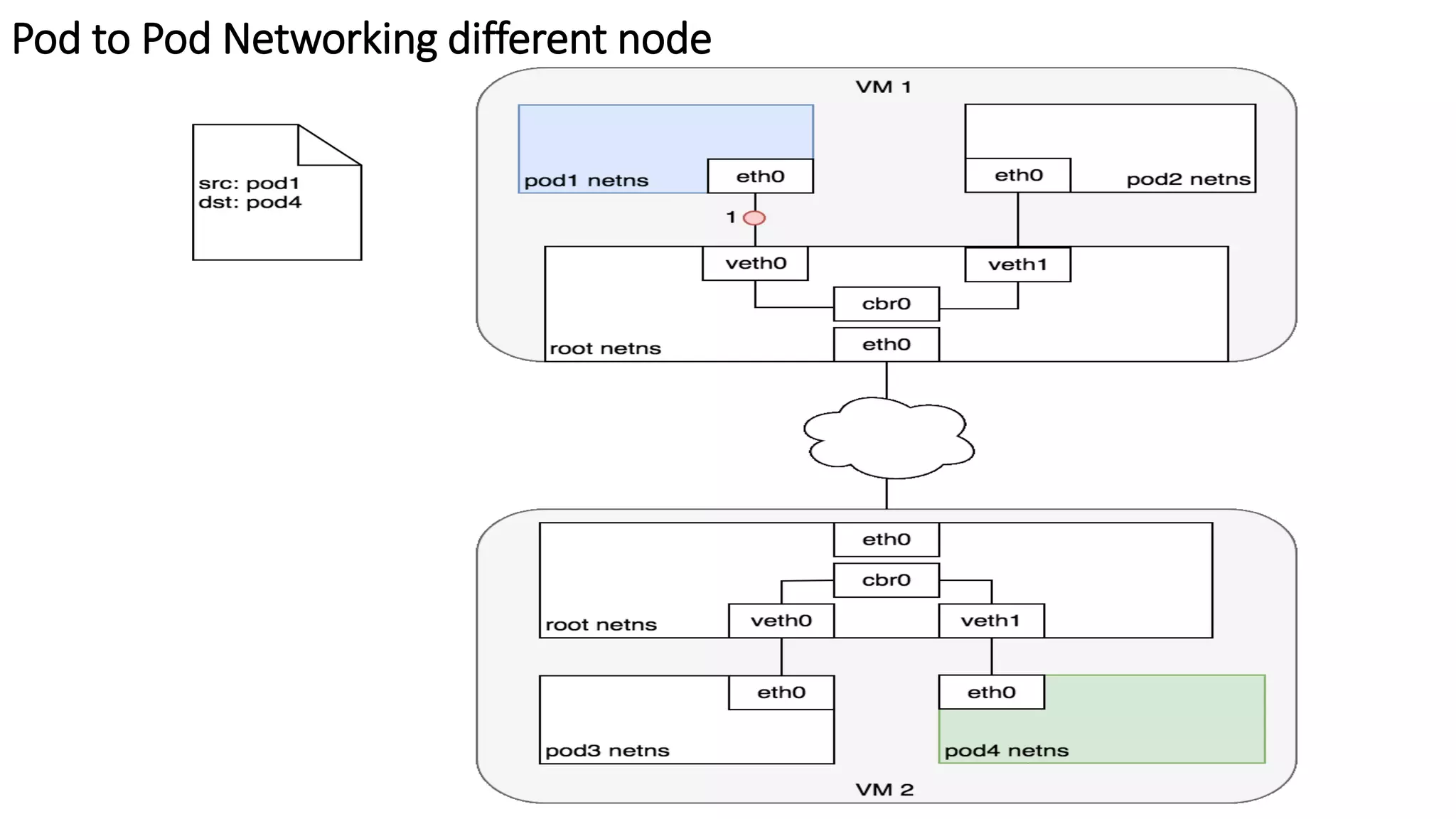
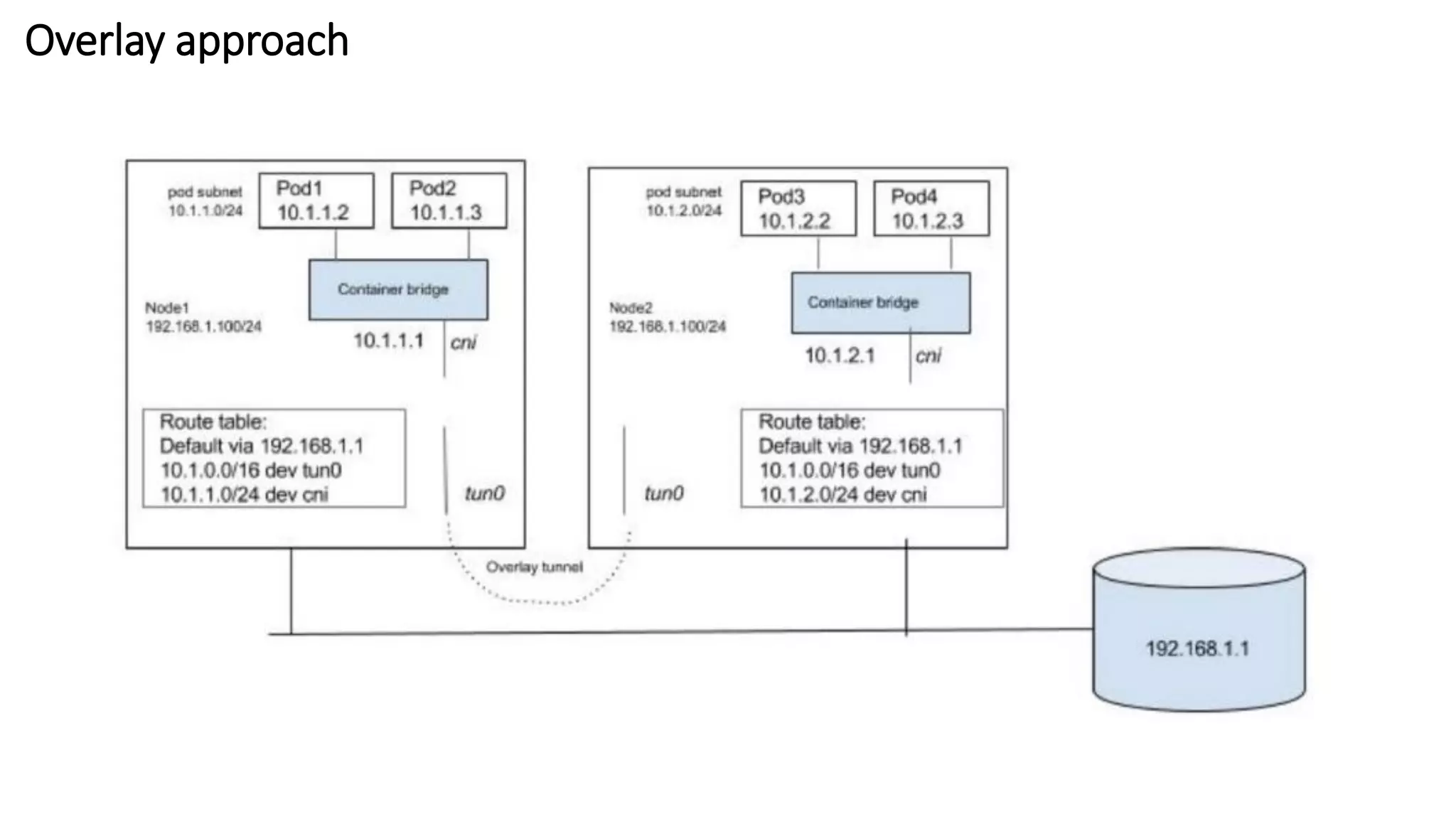
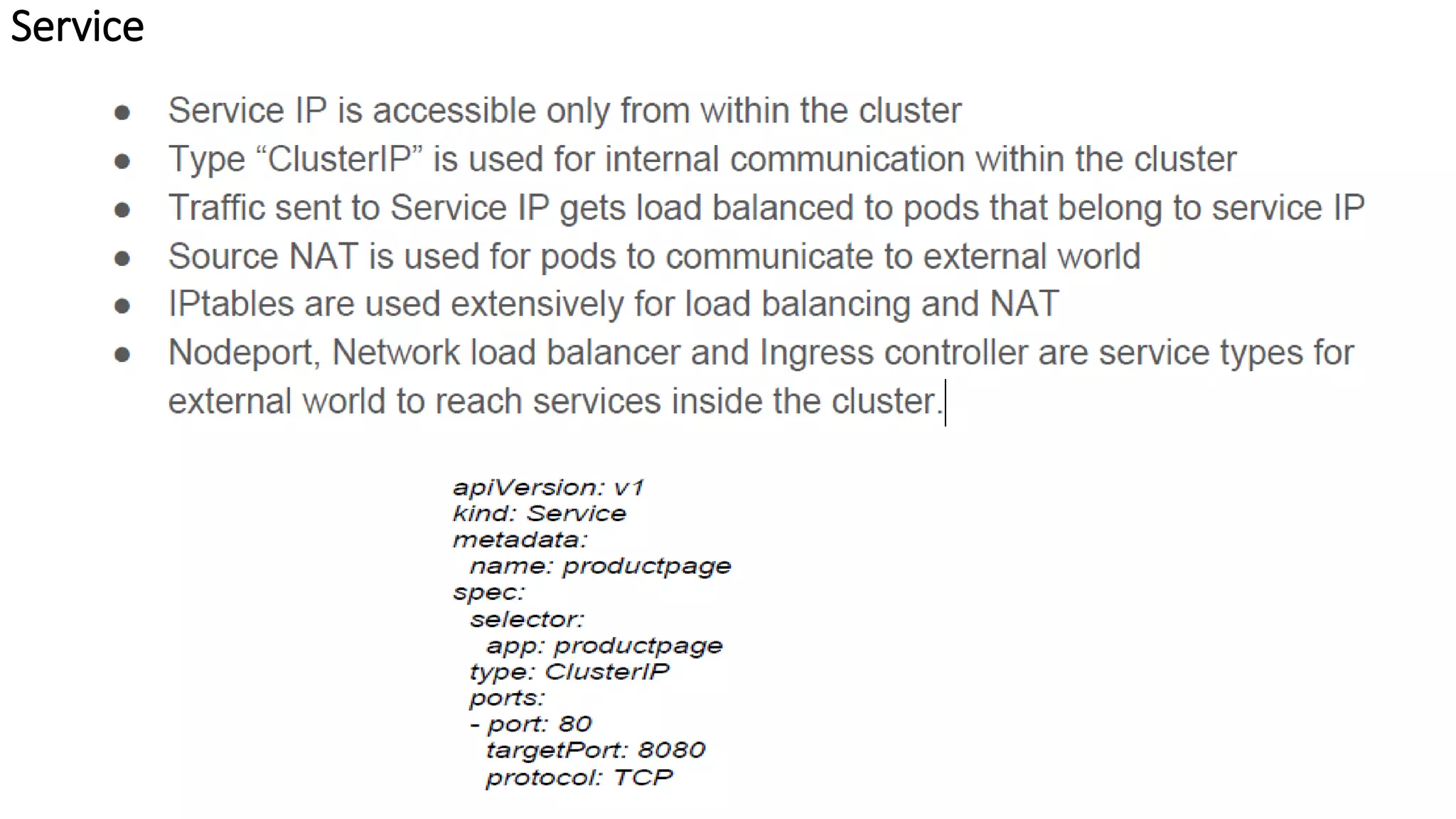
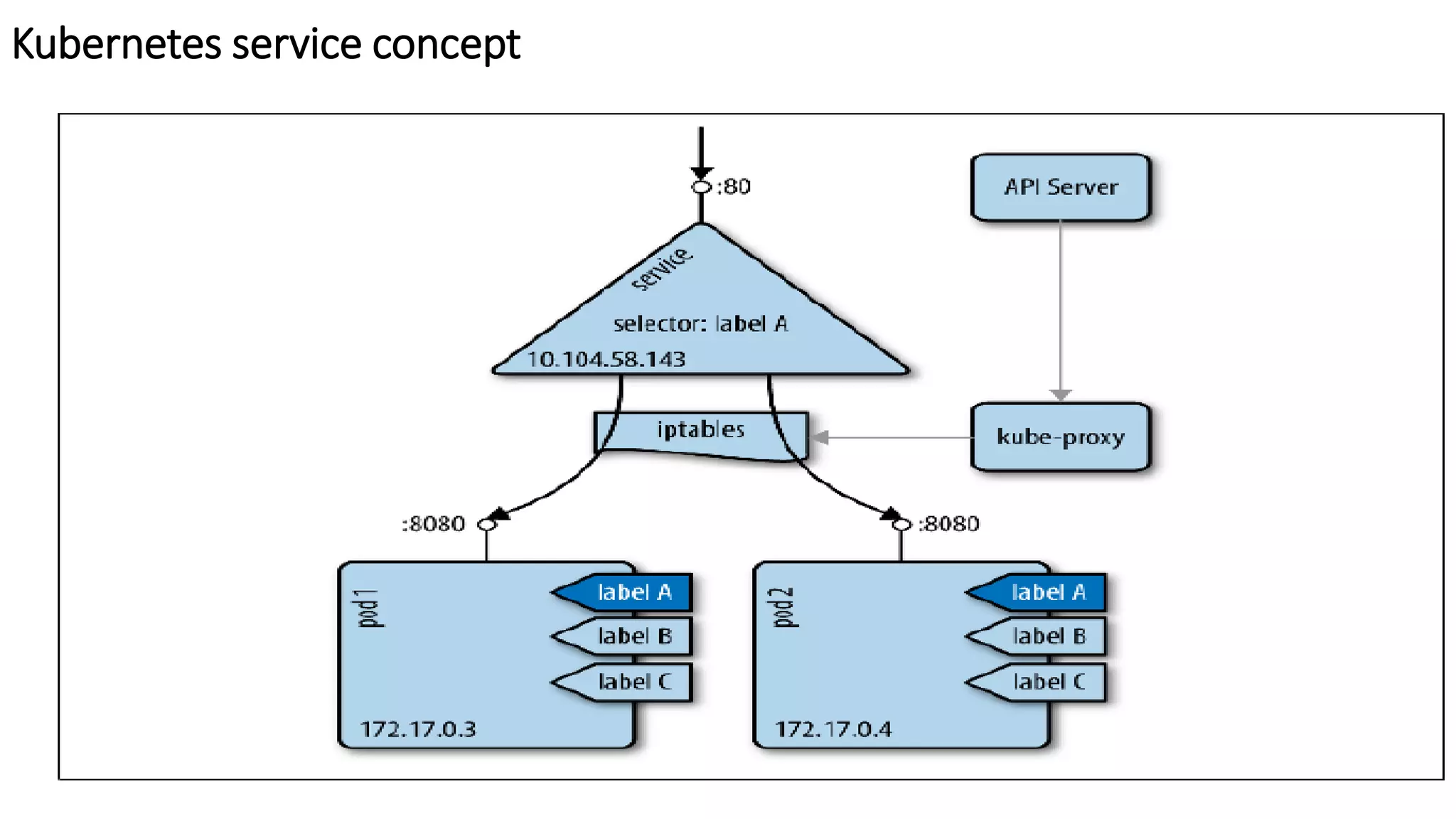
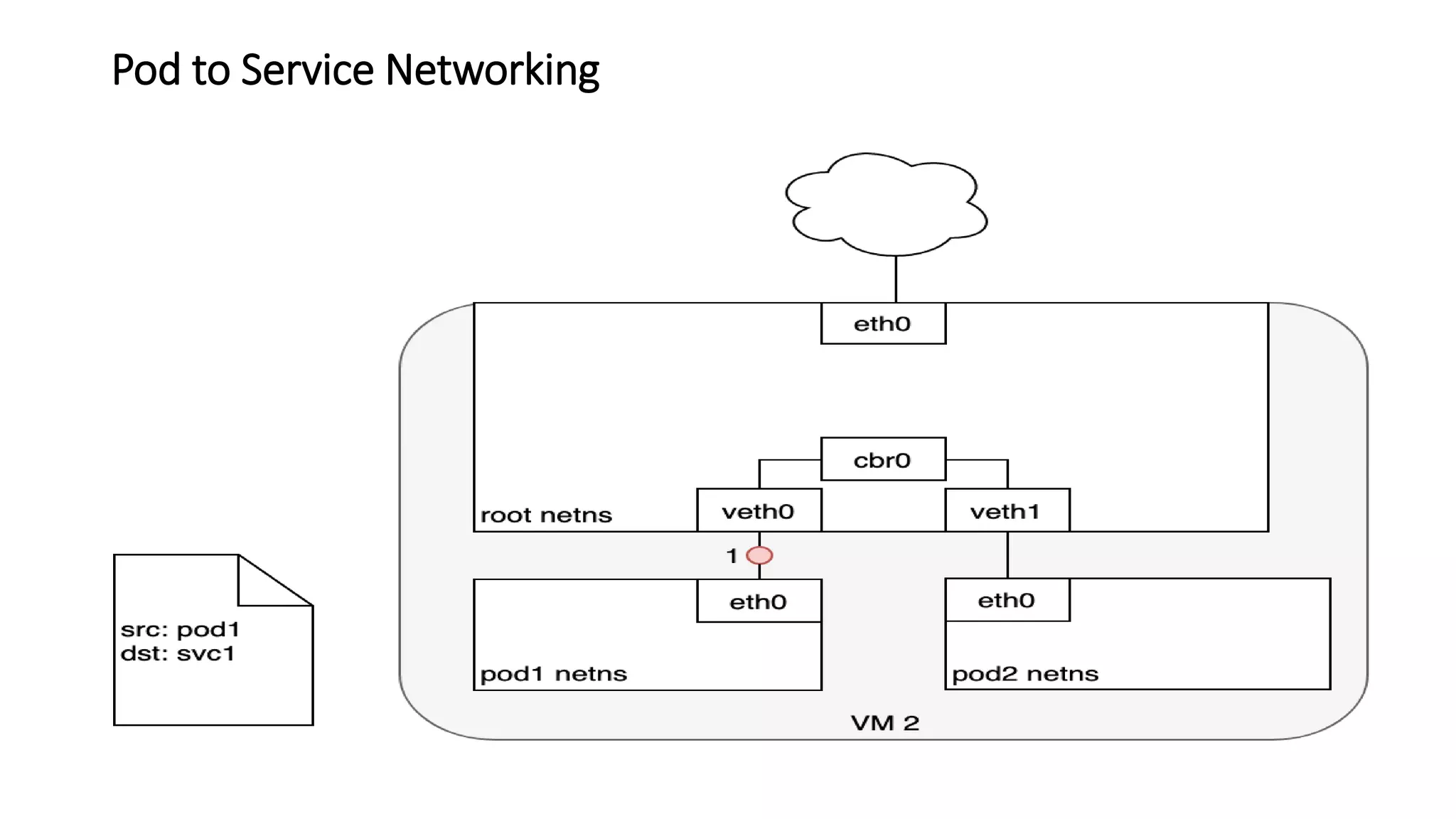
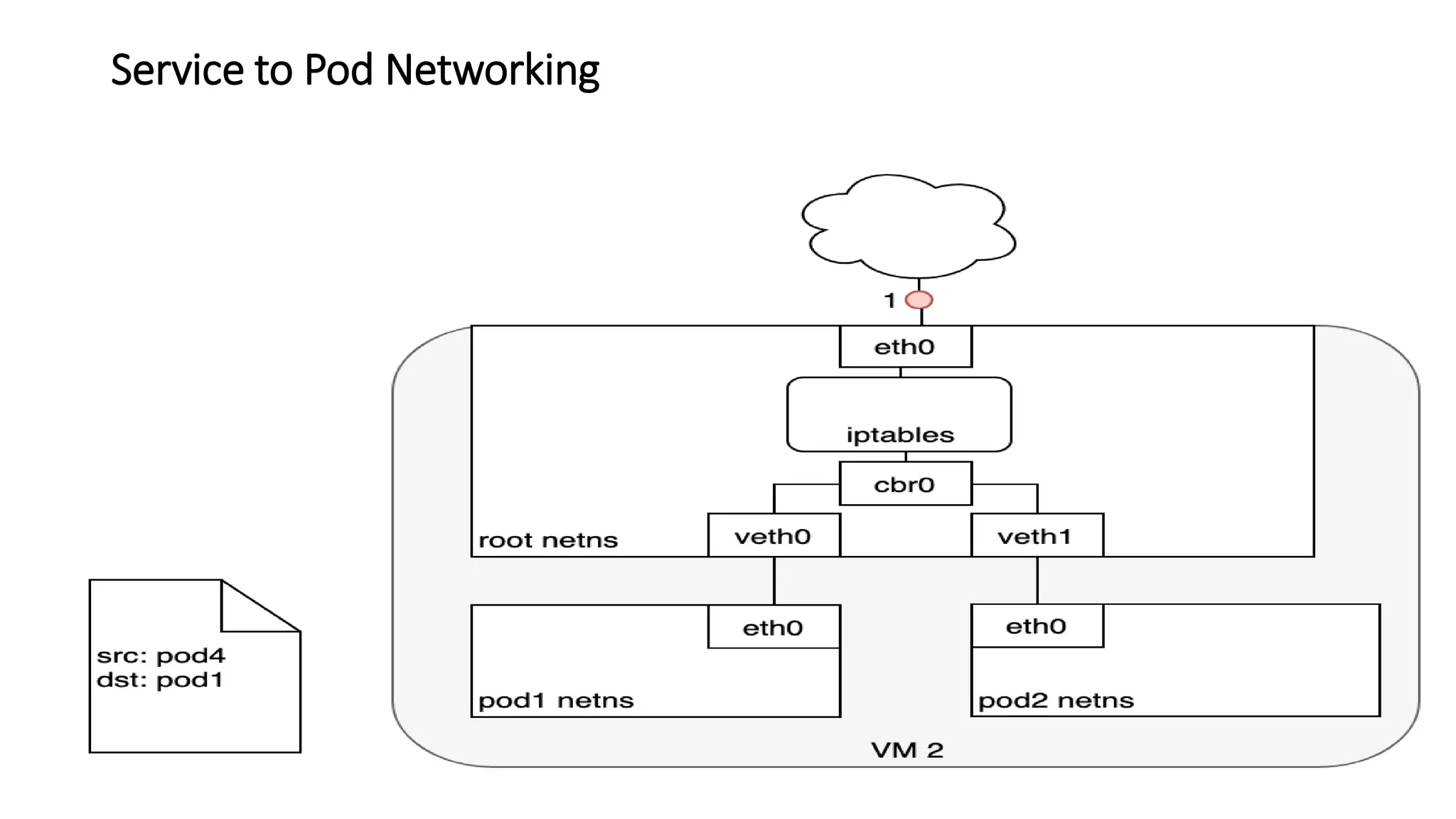
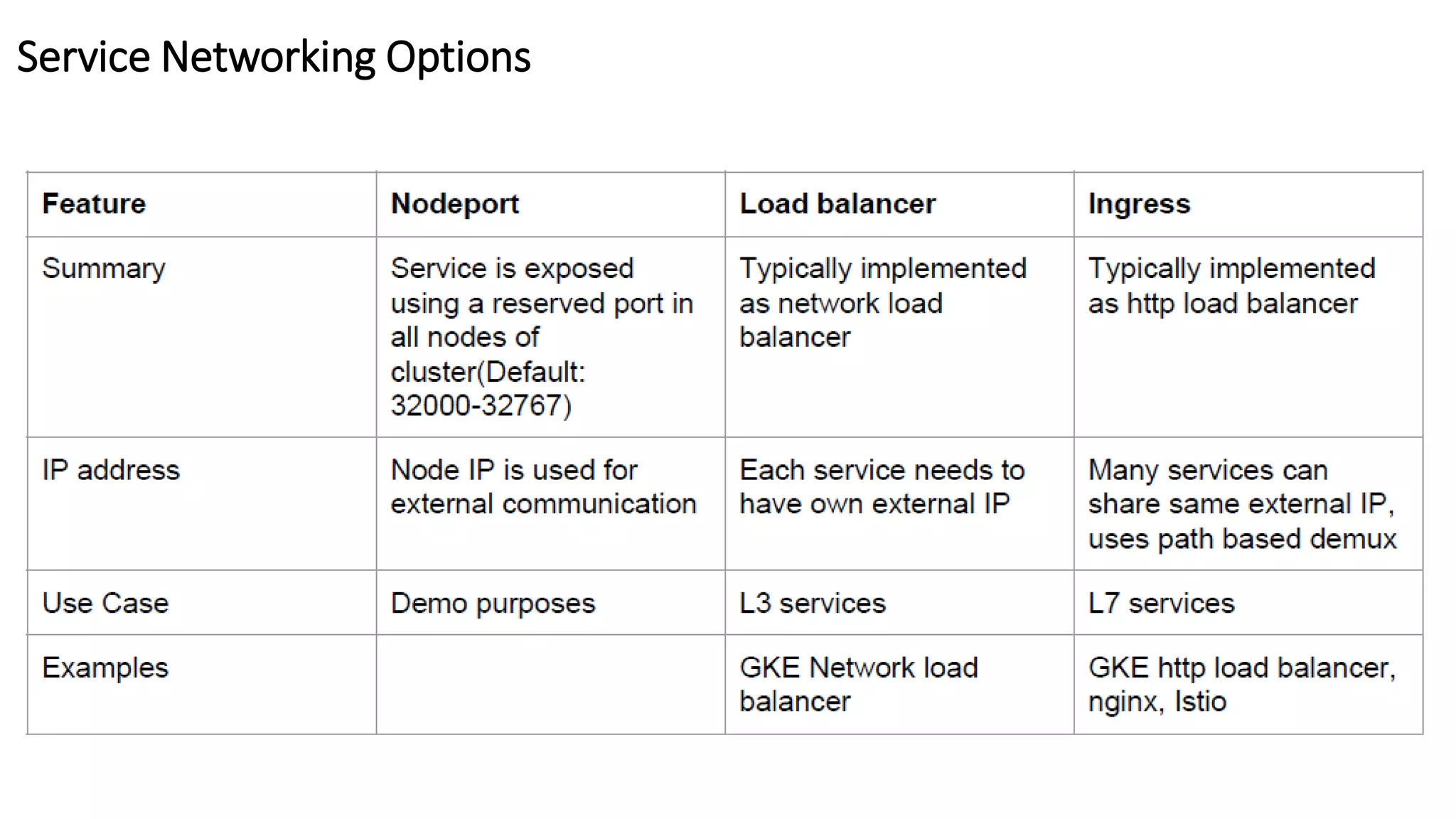
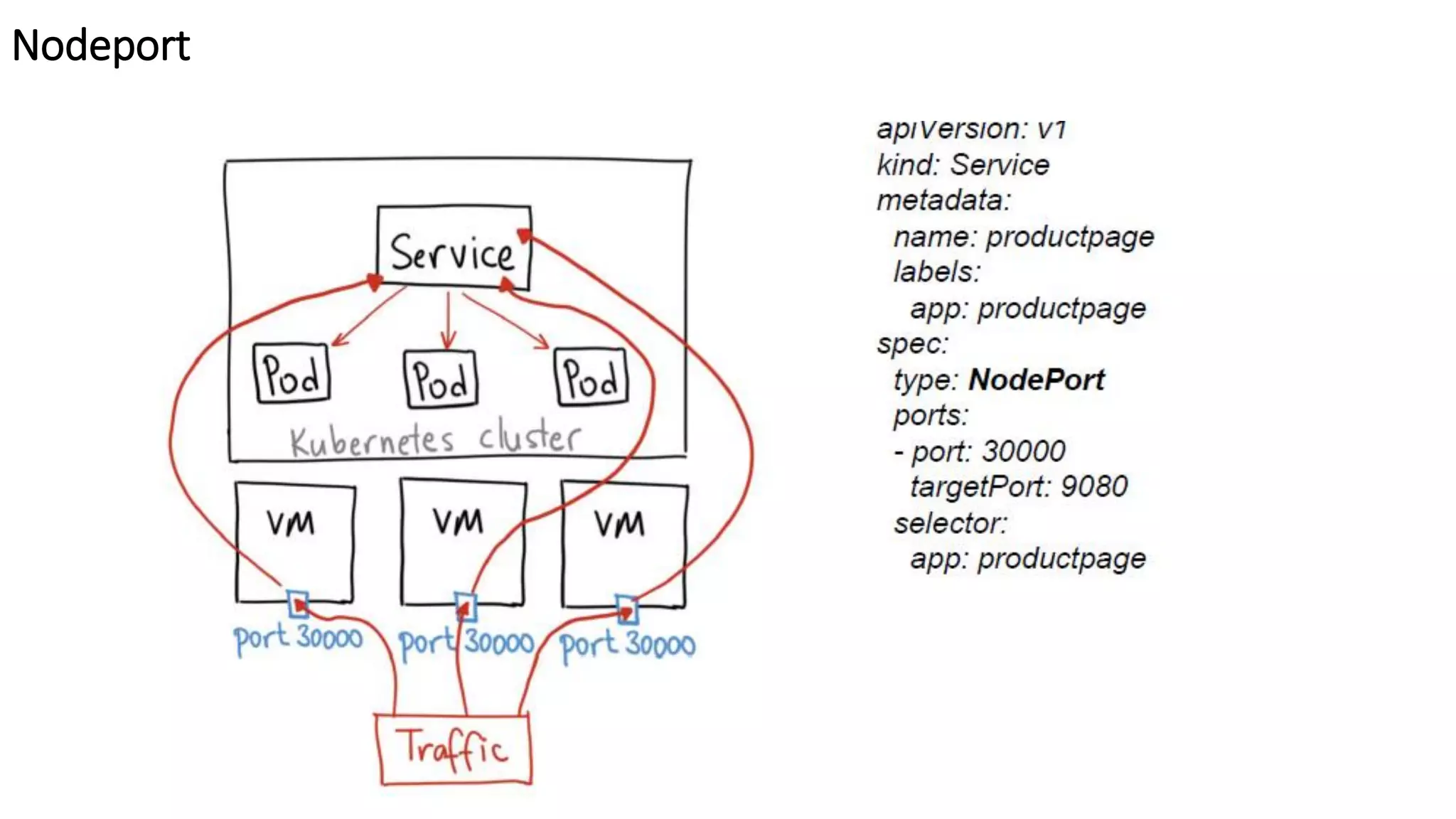
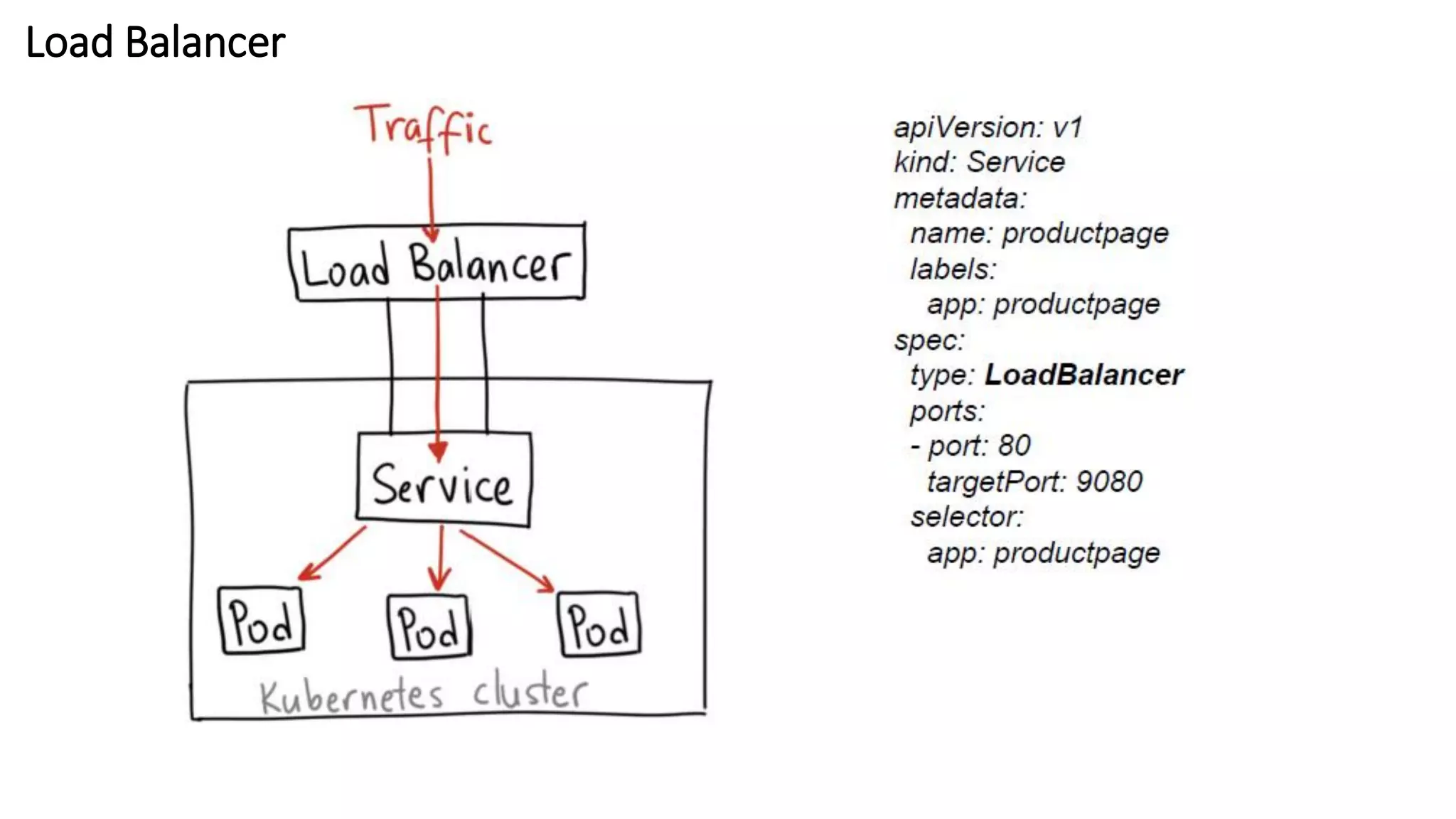
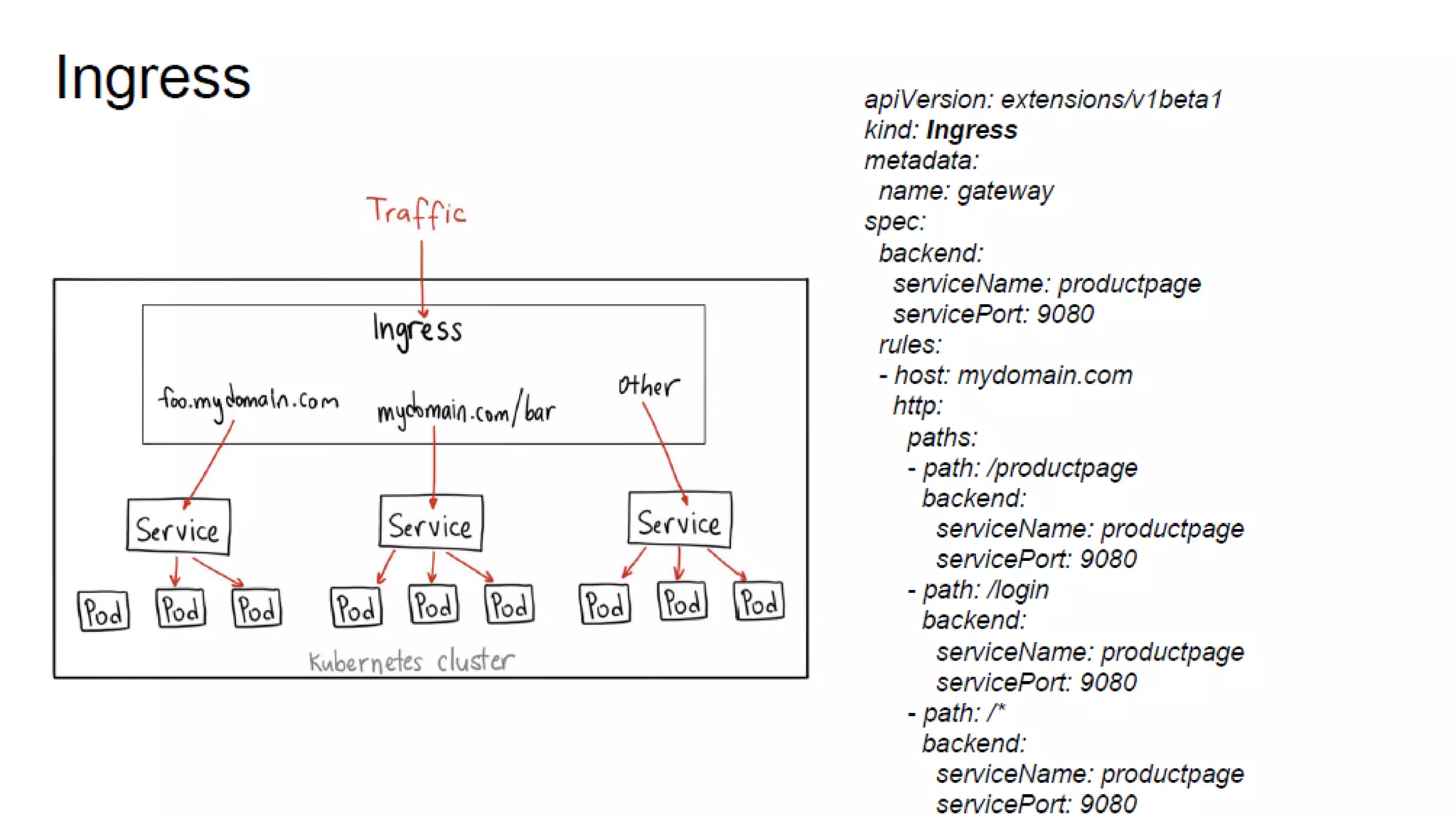
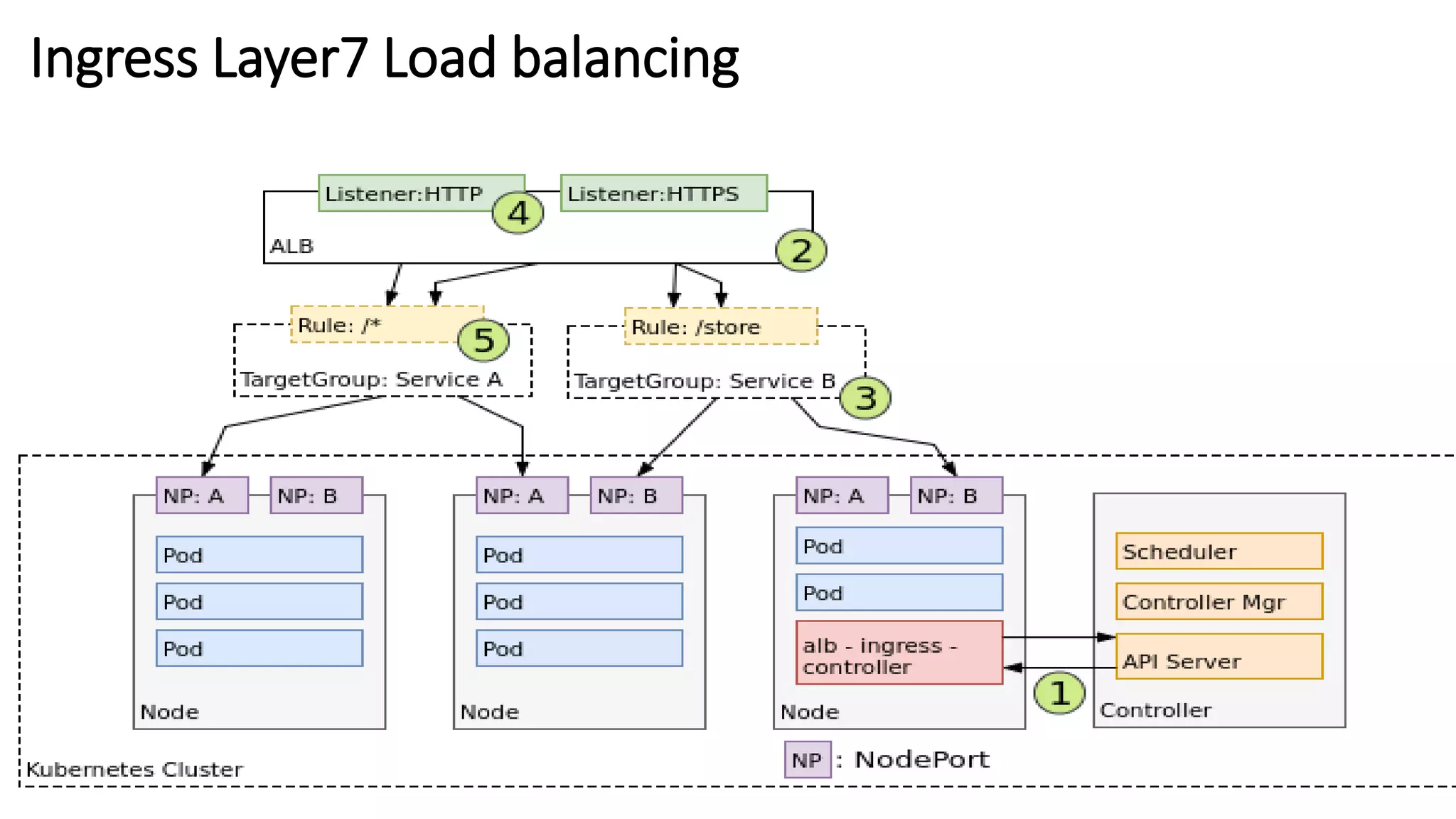
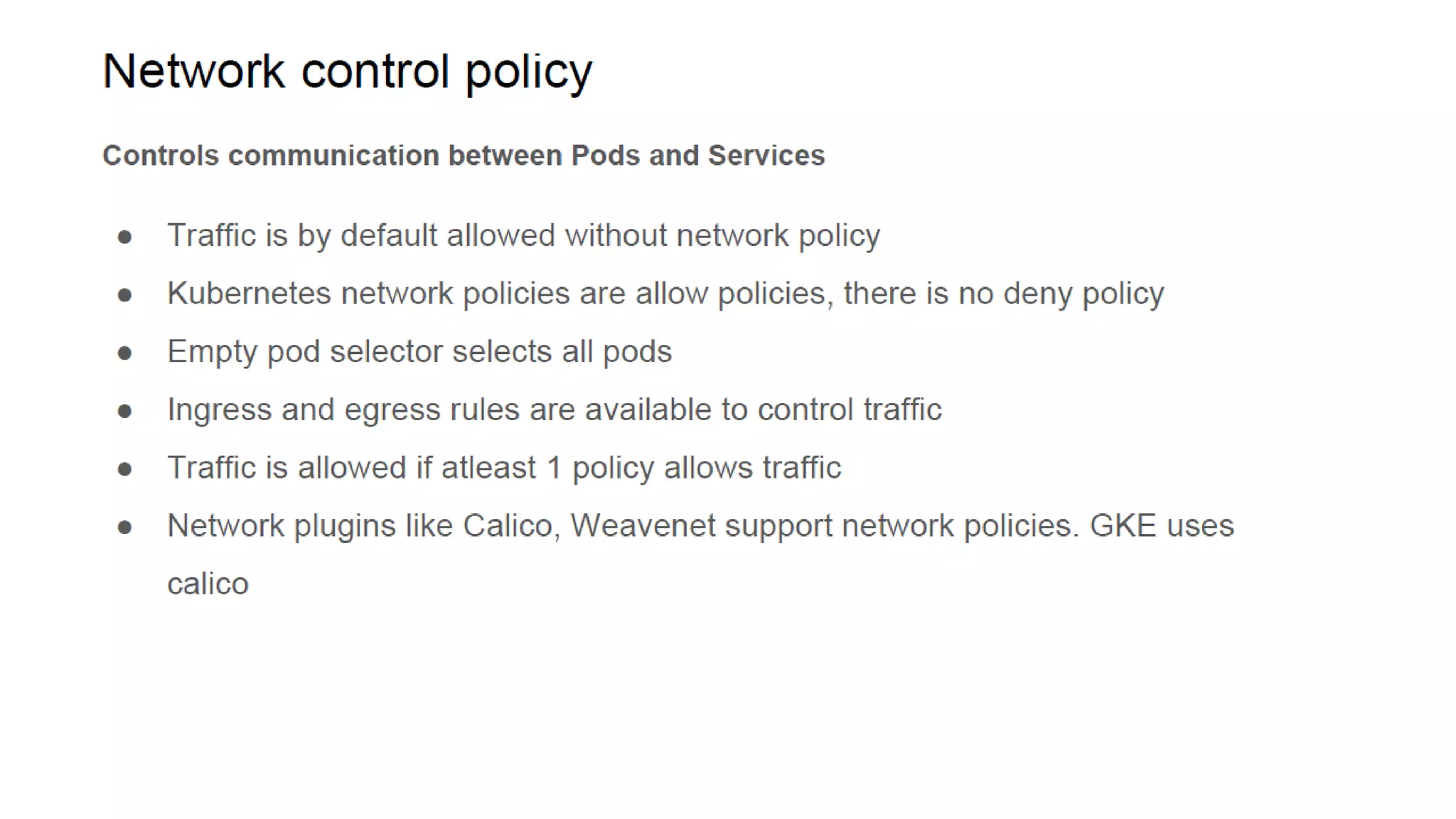
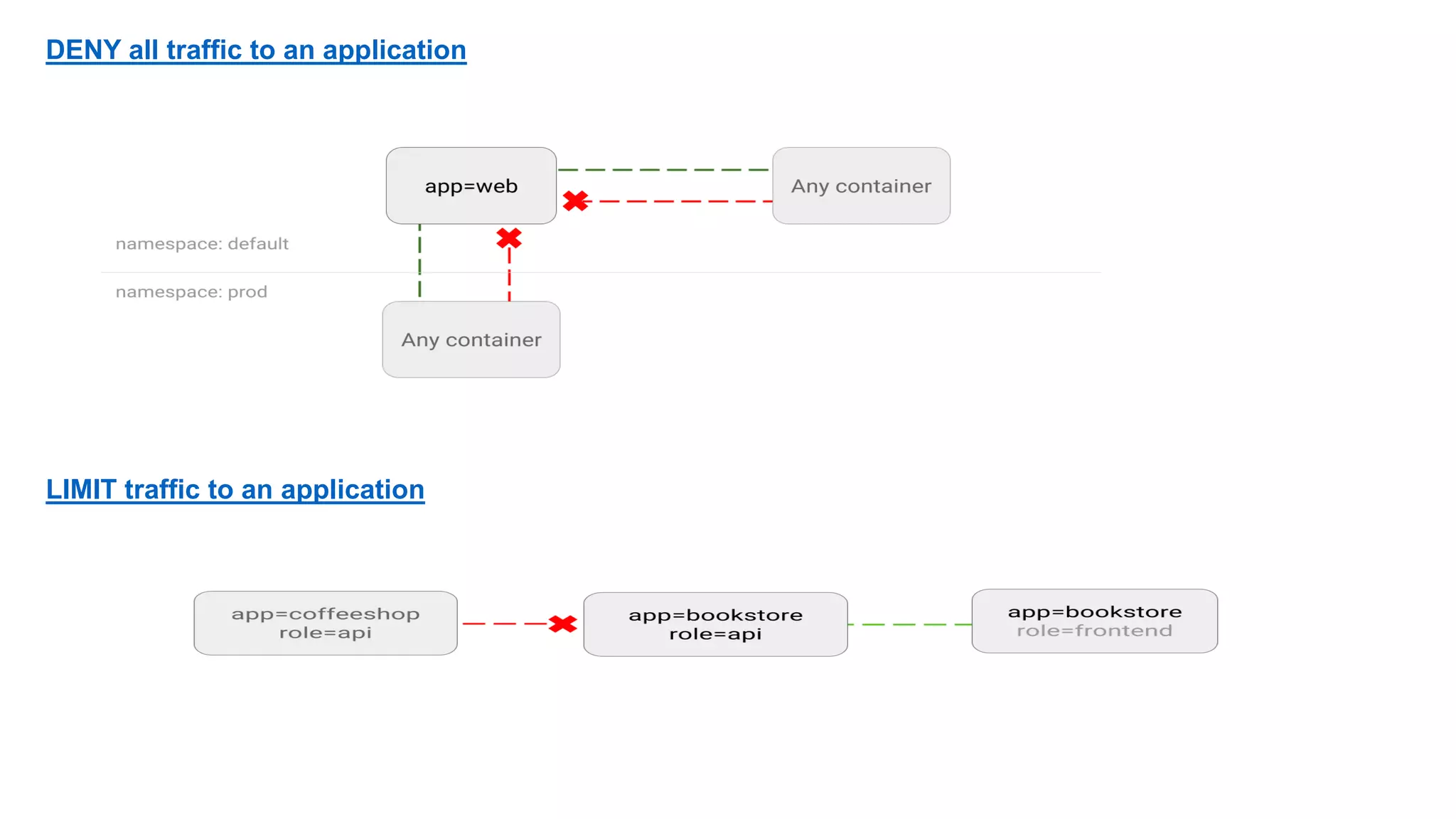
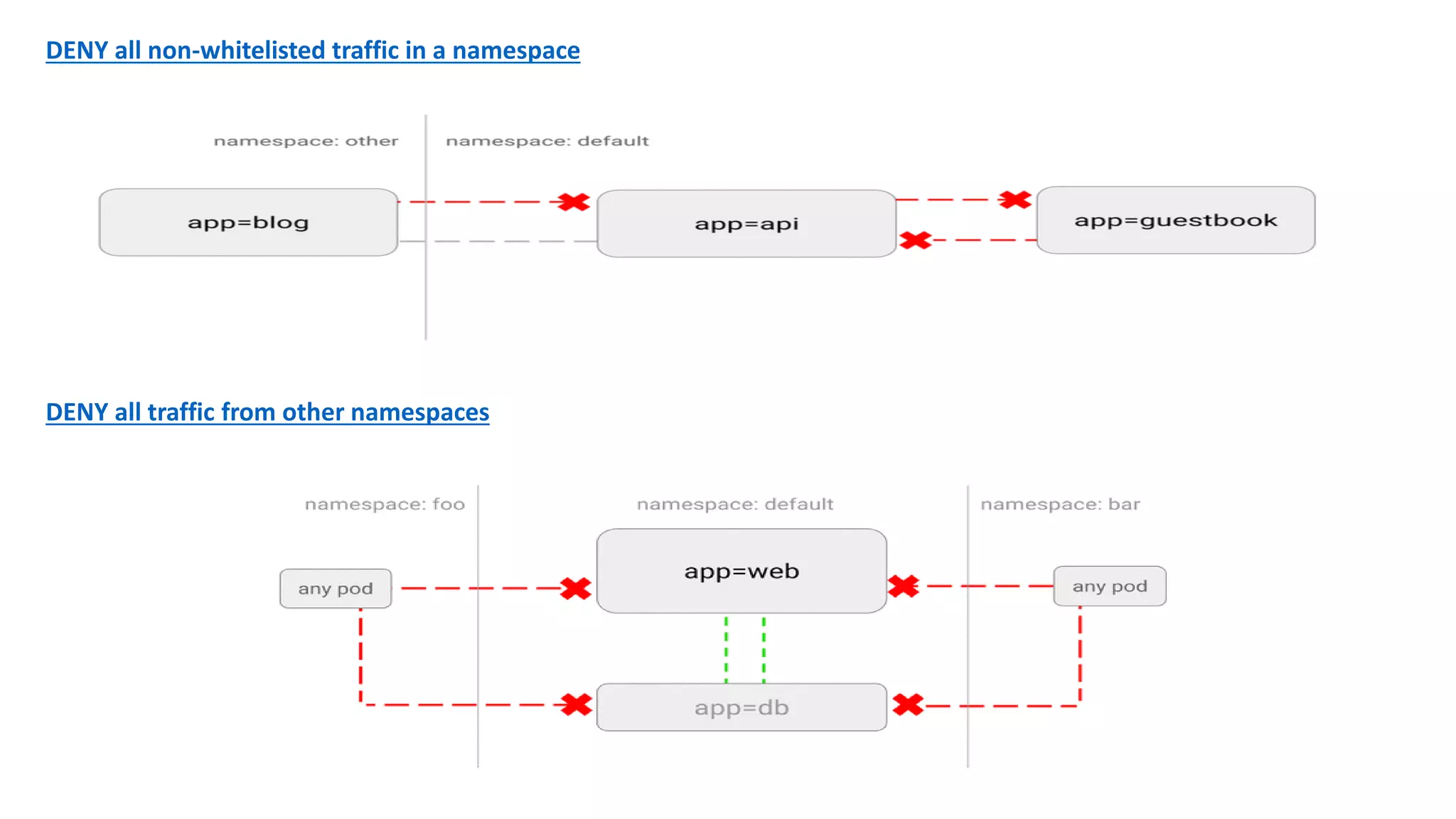
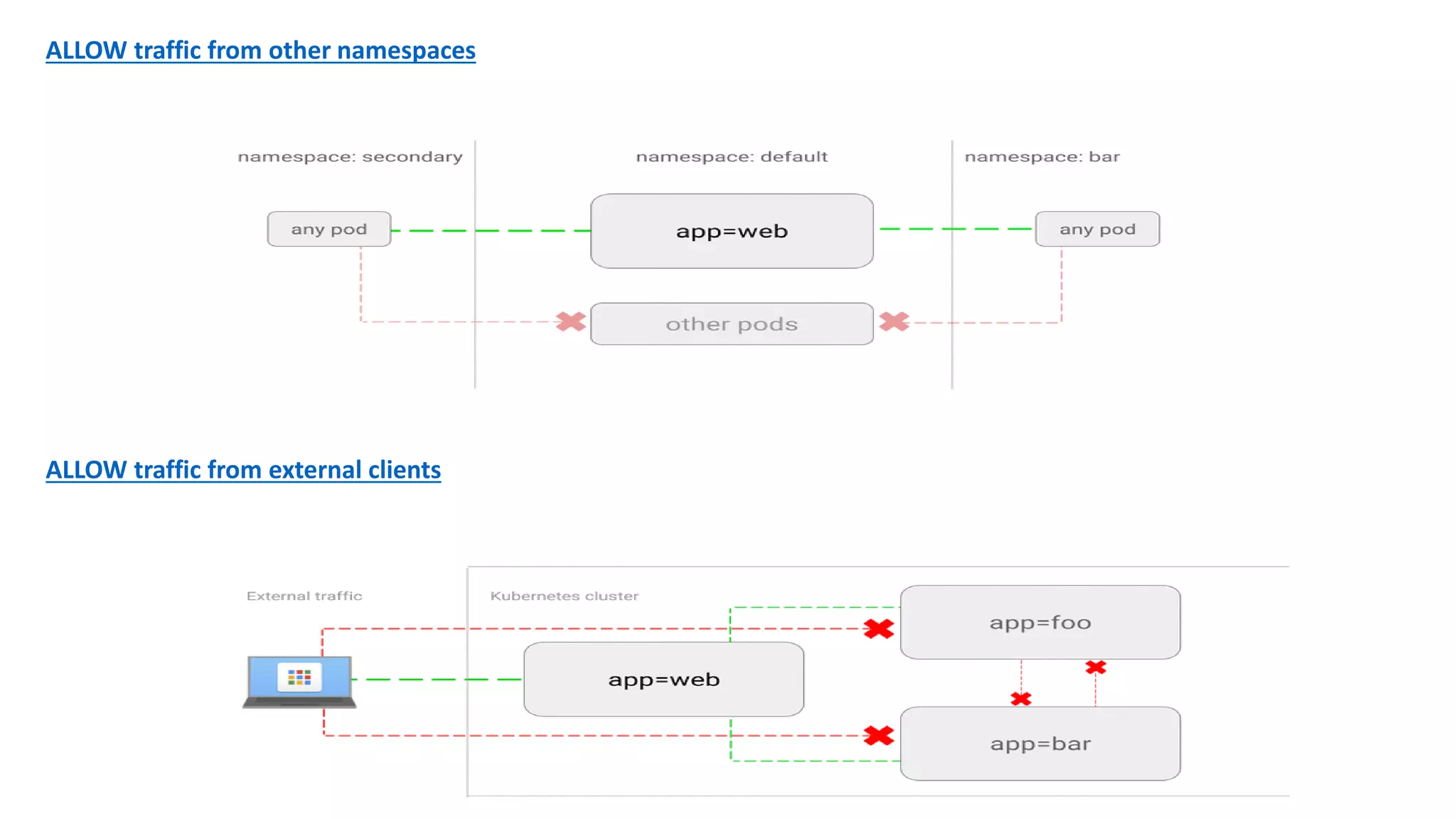
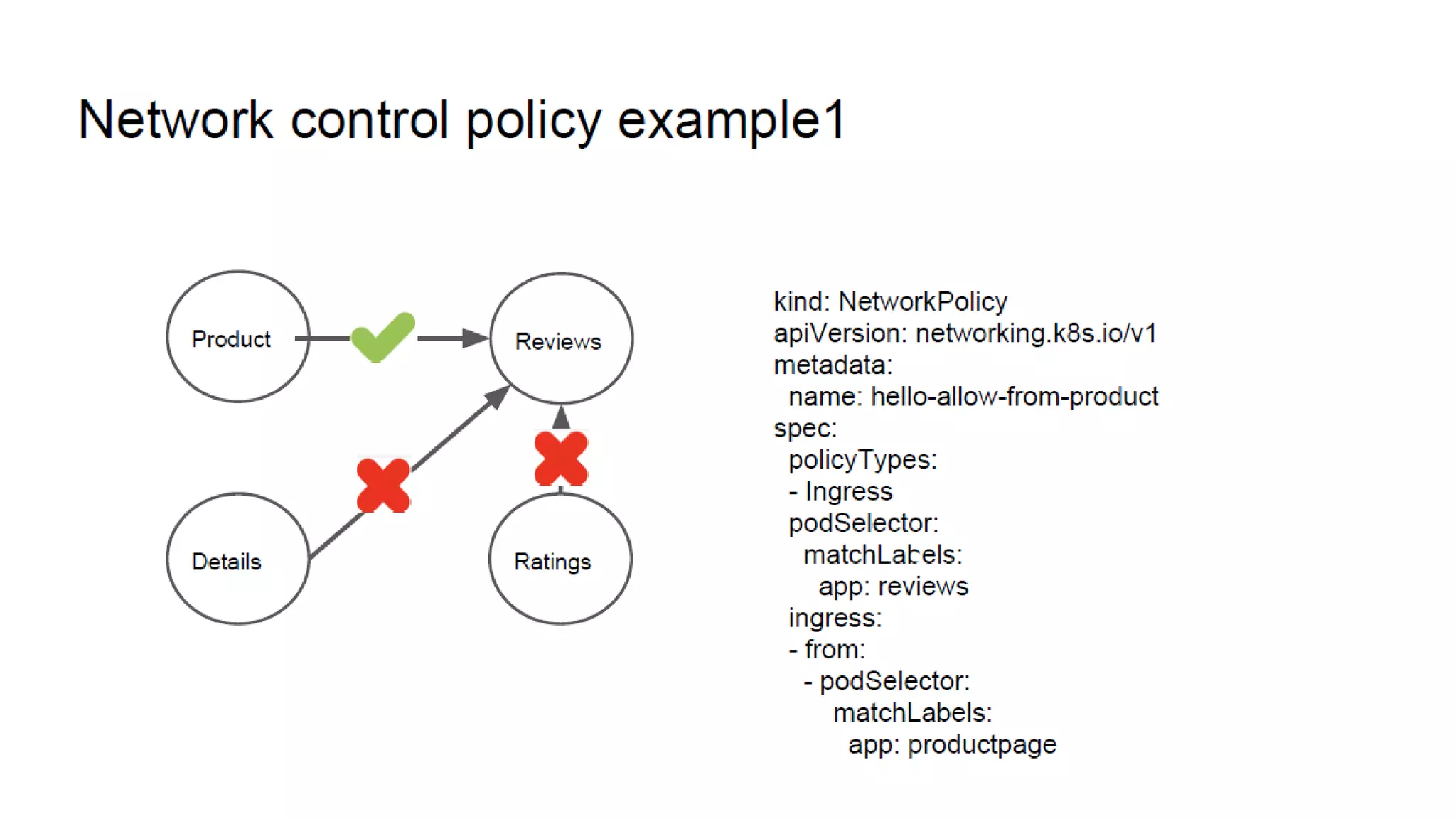
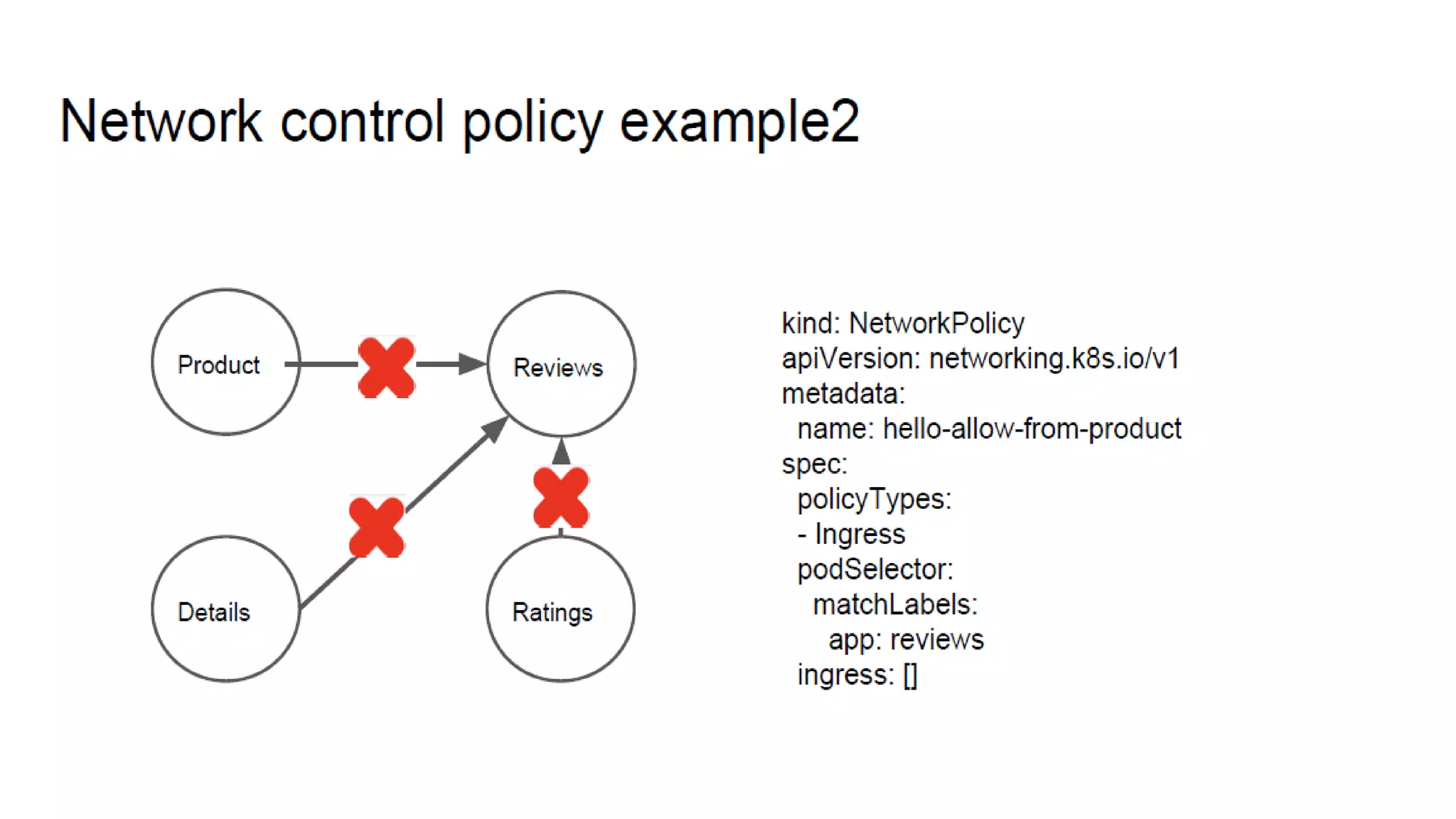
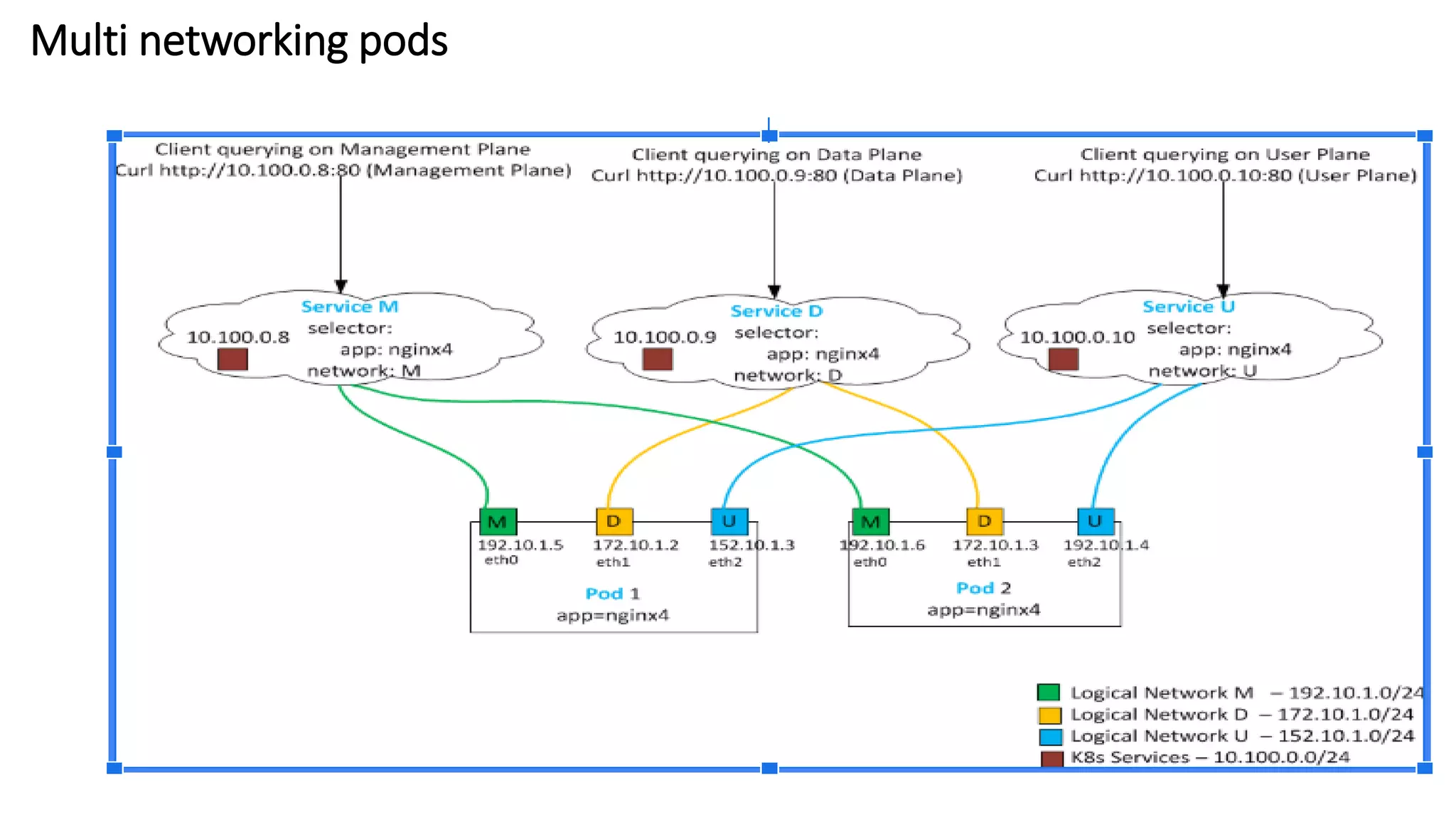
The document provides an overview of container networking standards, including Docker's CNM and Kubernetes' CNI, highlighting the roles of namespaces and cgroups in container networking. It explains service discovery, load balancing, routing mesh, and various deployment mechanisms within Docker and Kubernetes environments, detailing how services and tasks are managed. It also includes numerous references to resources for further exploration of the topics discussed.