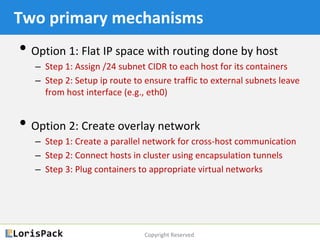
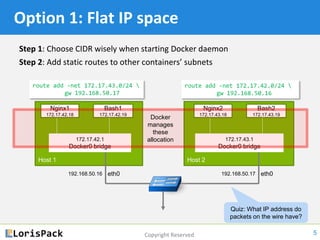
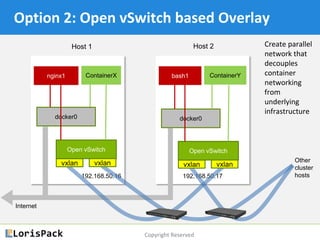
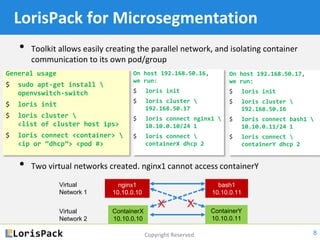
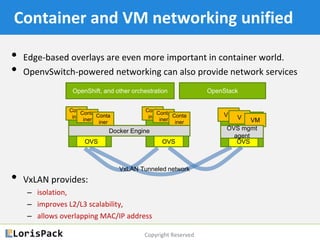
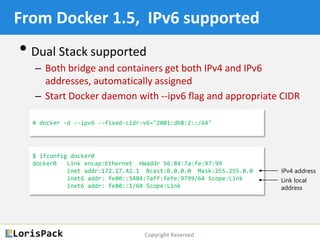
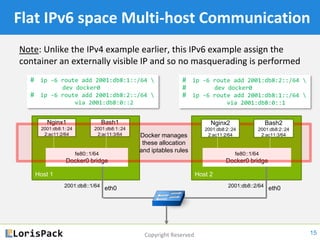
This document provides a tutorial on docker networking, emphasizing its early development, the selection of appropriate networking mechanisms for applications, and the capabilities of open vswitch for enhanced networking. It discusses two primary options for container communication across hosts: flat IP space with routing and overlay networks, detailing configurations and advantages of both. Additionally, the tutorial covers IPv6 support in Docker, highlighting the importance of dual stack and network communication enhancements as ISPs transition away from IPv4.