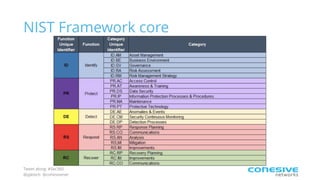
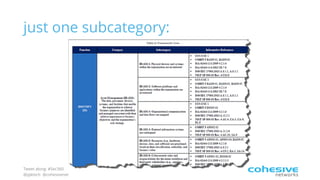
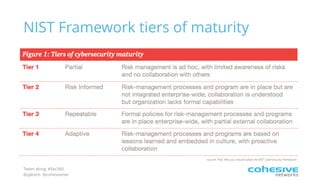
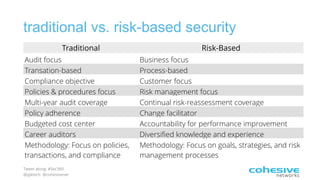
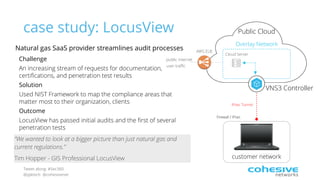
The document discusses the NIST Cybersecurity Framework and risk-based cybersecurity. It provides an overview of the NIST Framework, describing its core components and five tiers of maturity. It also discusses how the Framework establishes a common language and unified process for managing cybersecurity risks across critical infrastructure sectors. Finally, it outlines steps for applying the Framework, including prioritizing risks, assessing cybersecurity programs, and developing action plans to address gaps.