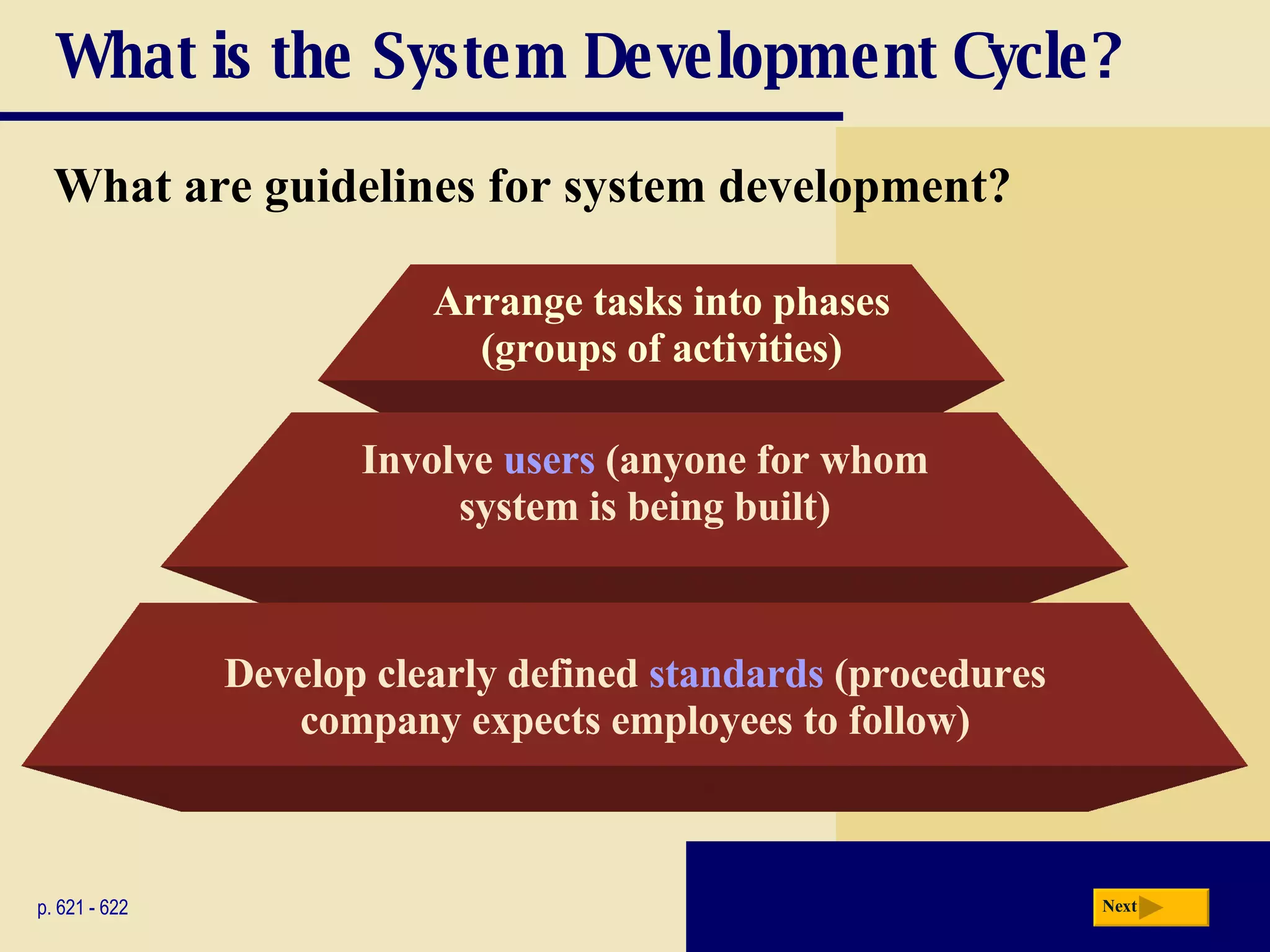
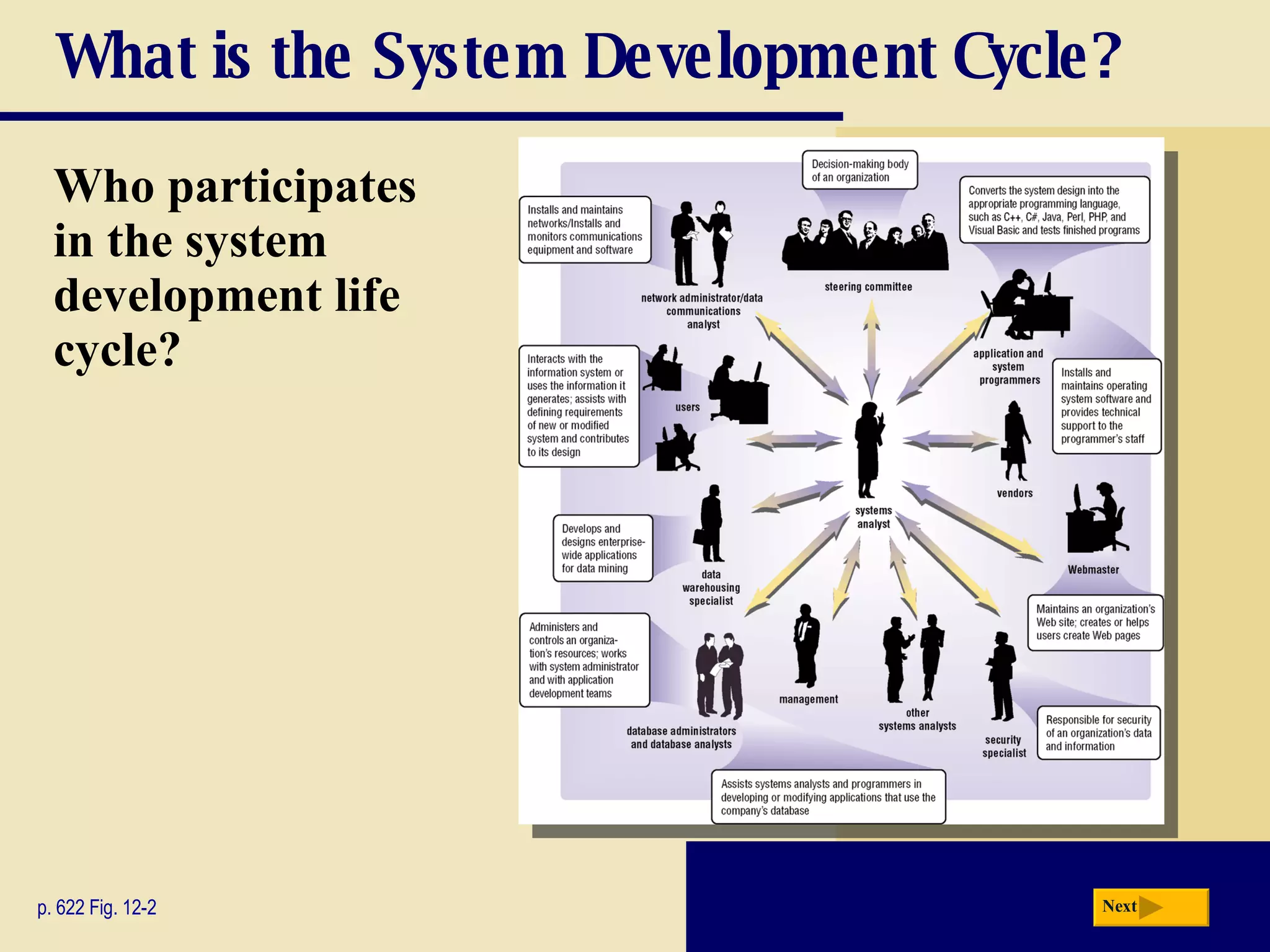
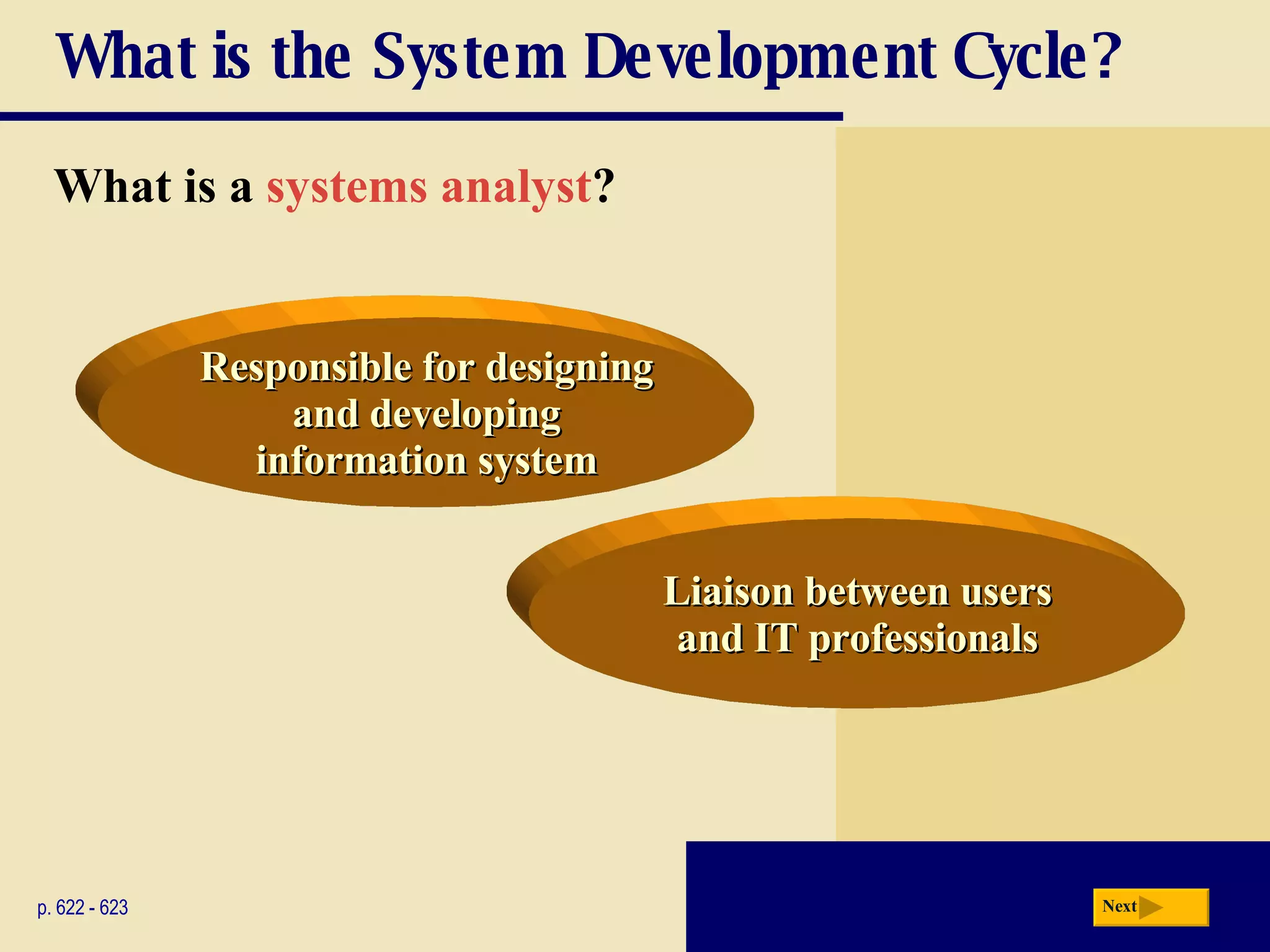
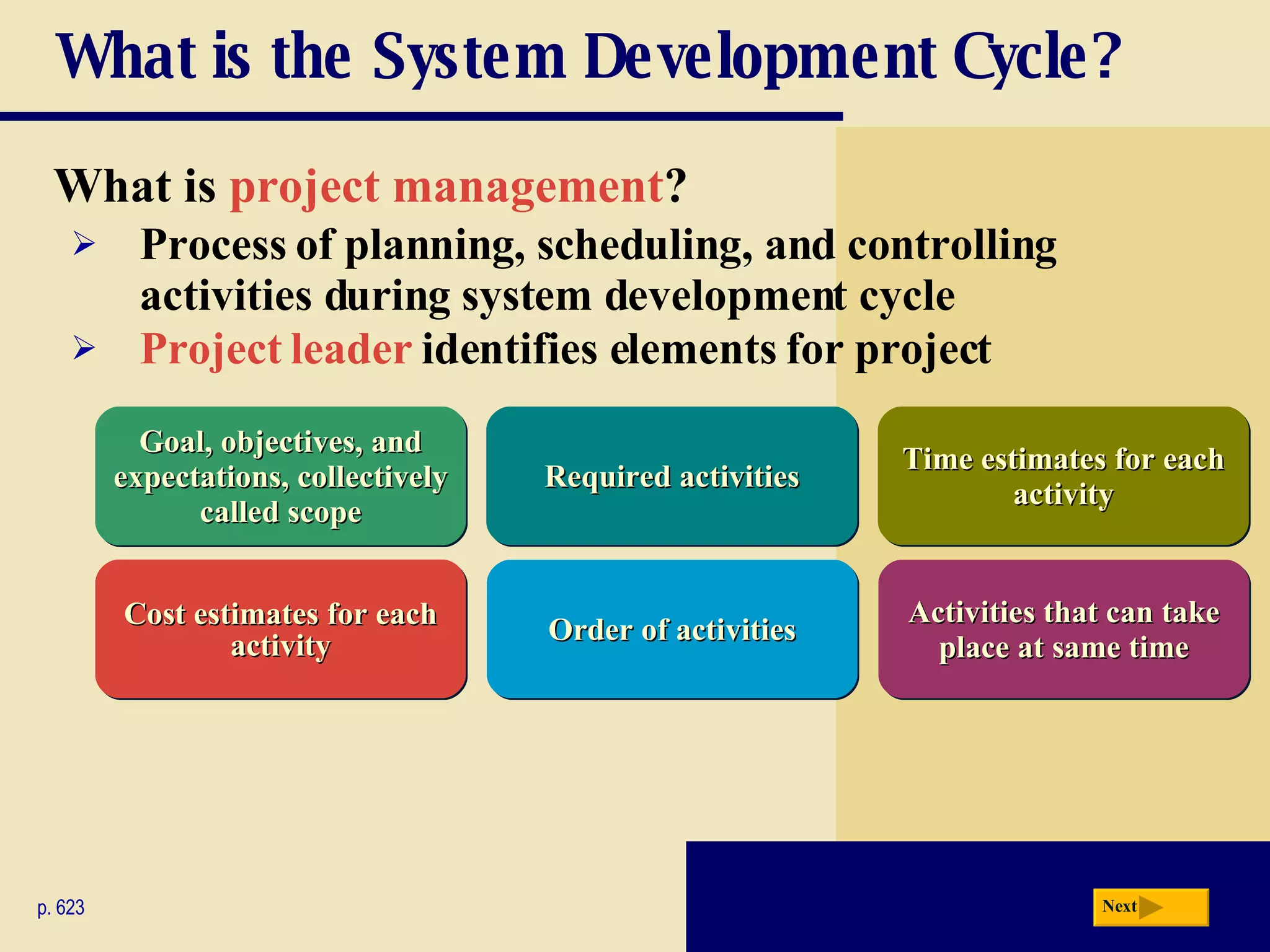
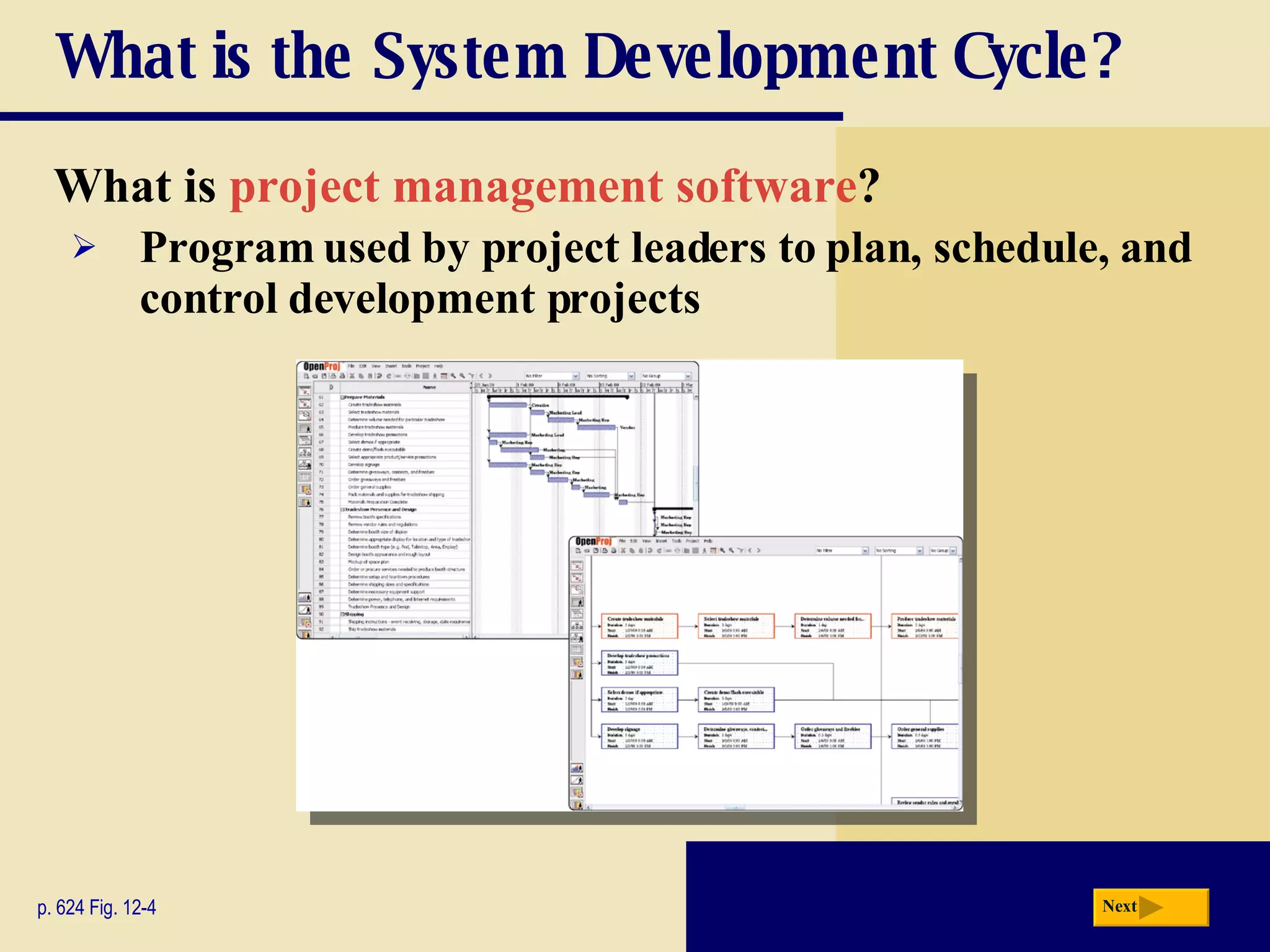
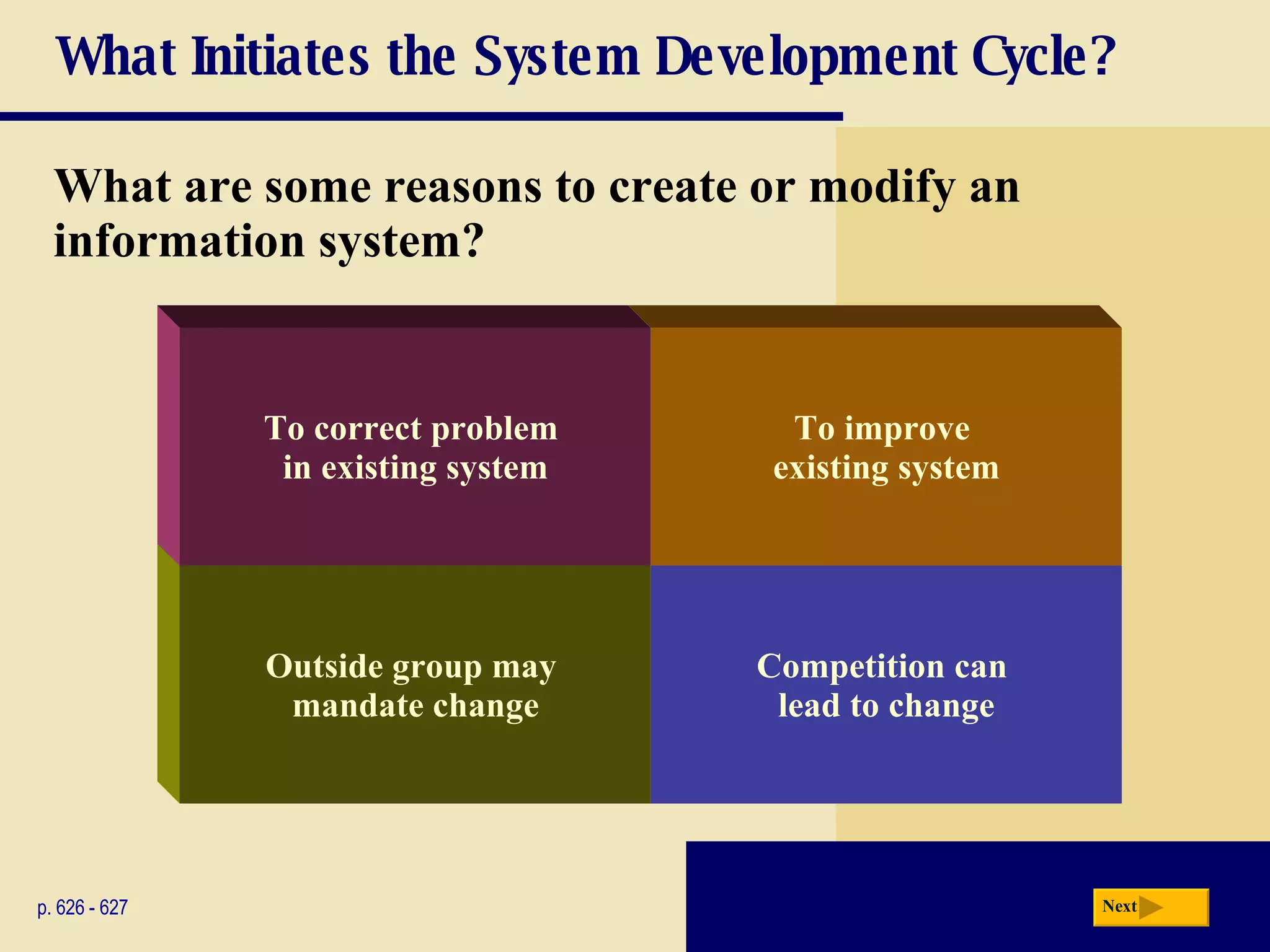
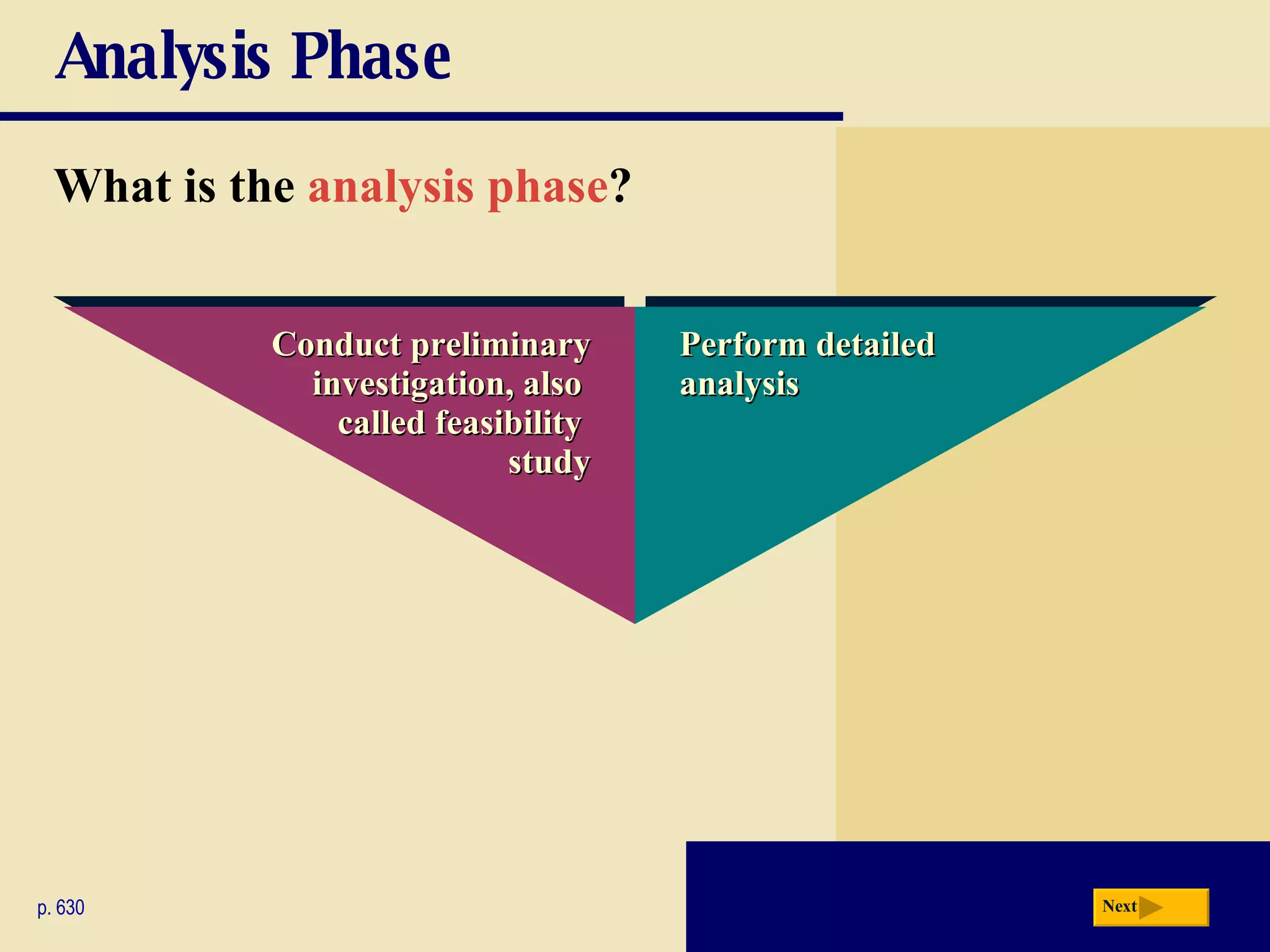
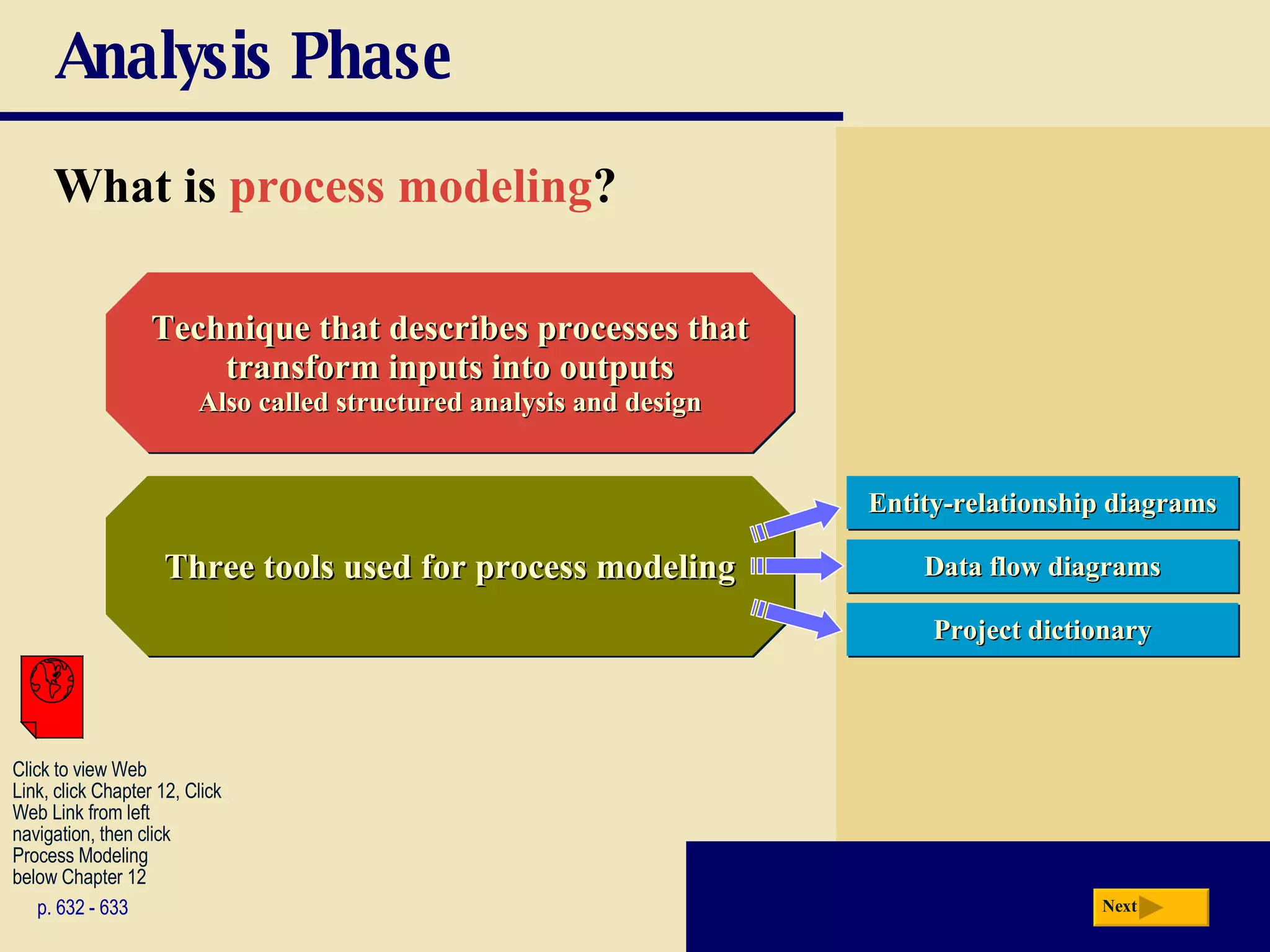
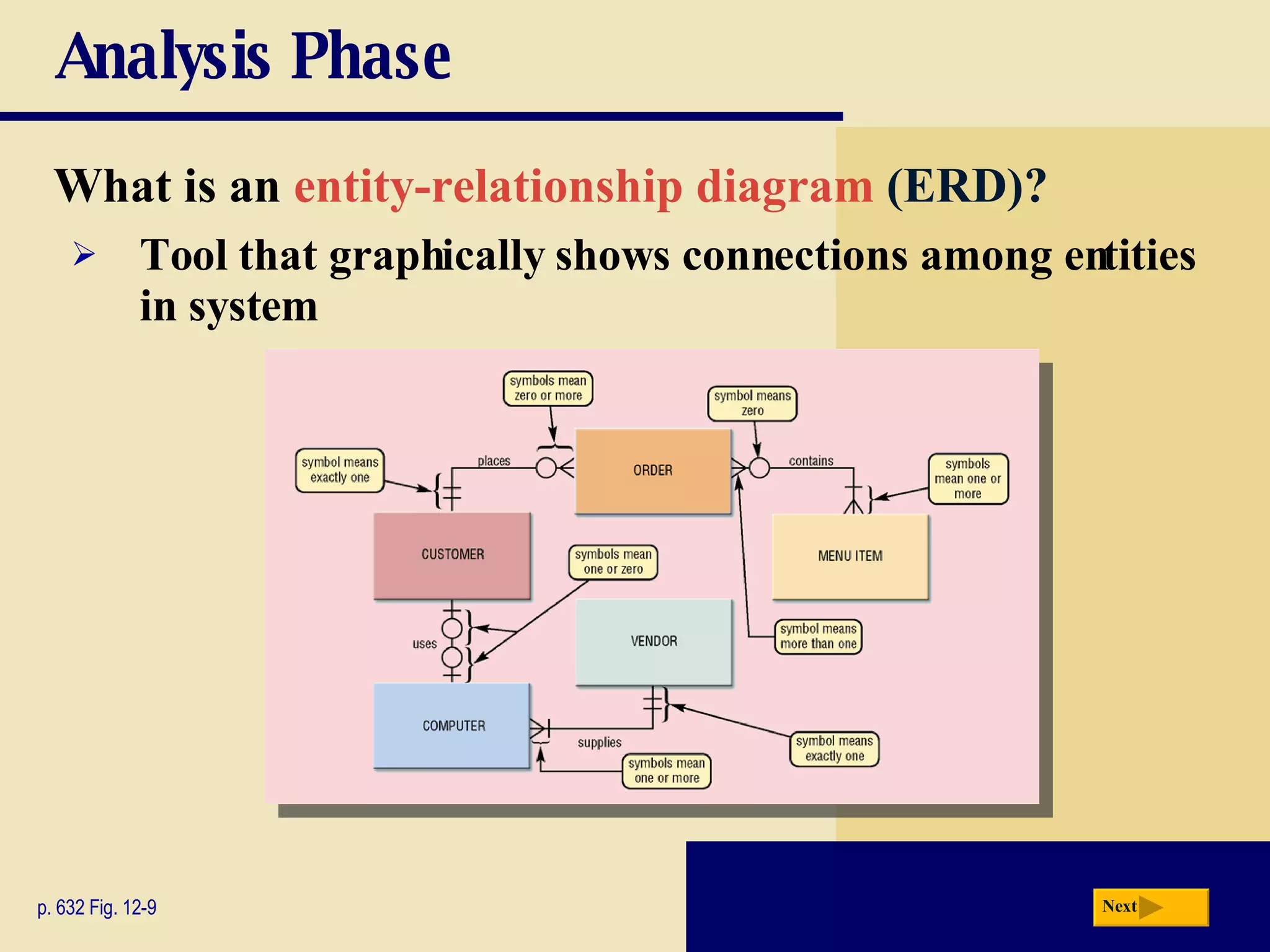
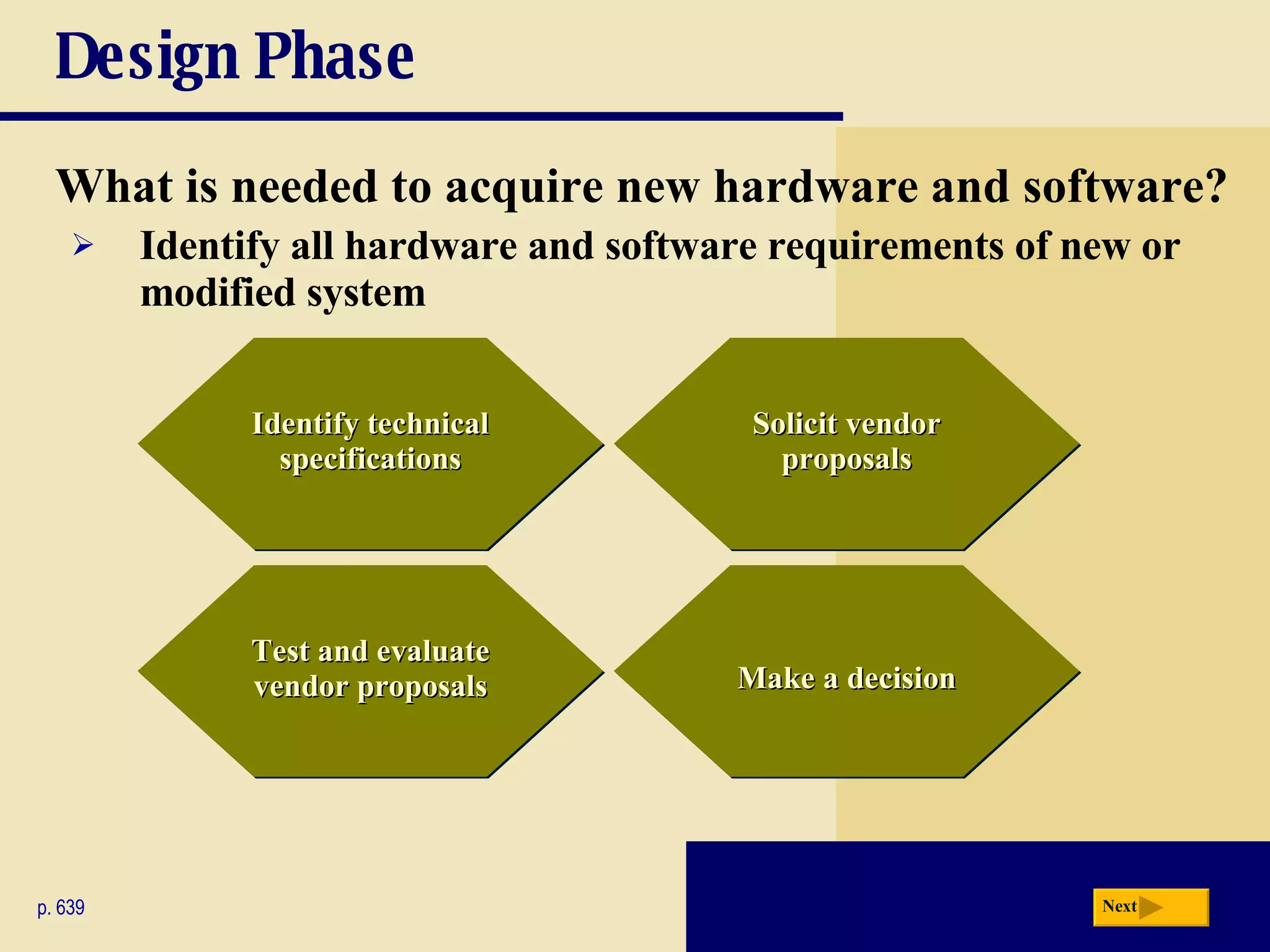
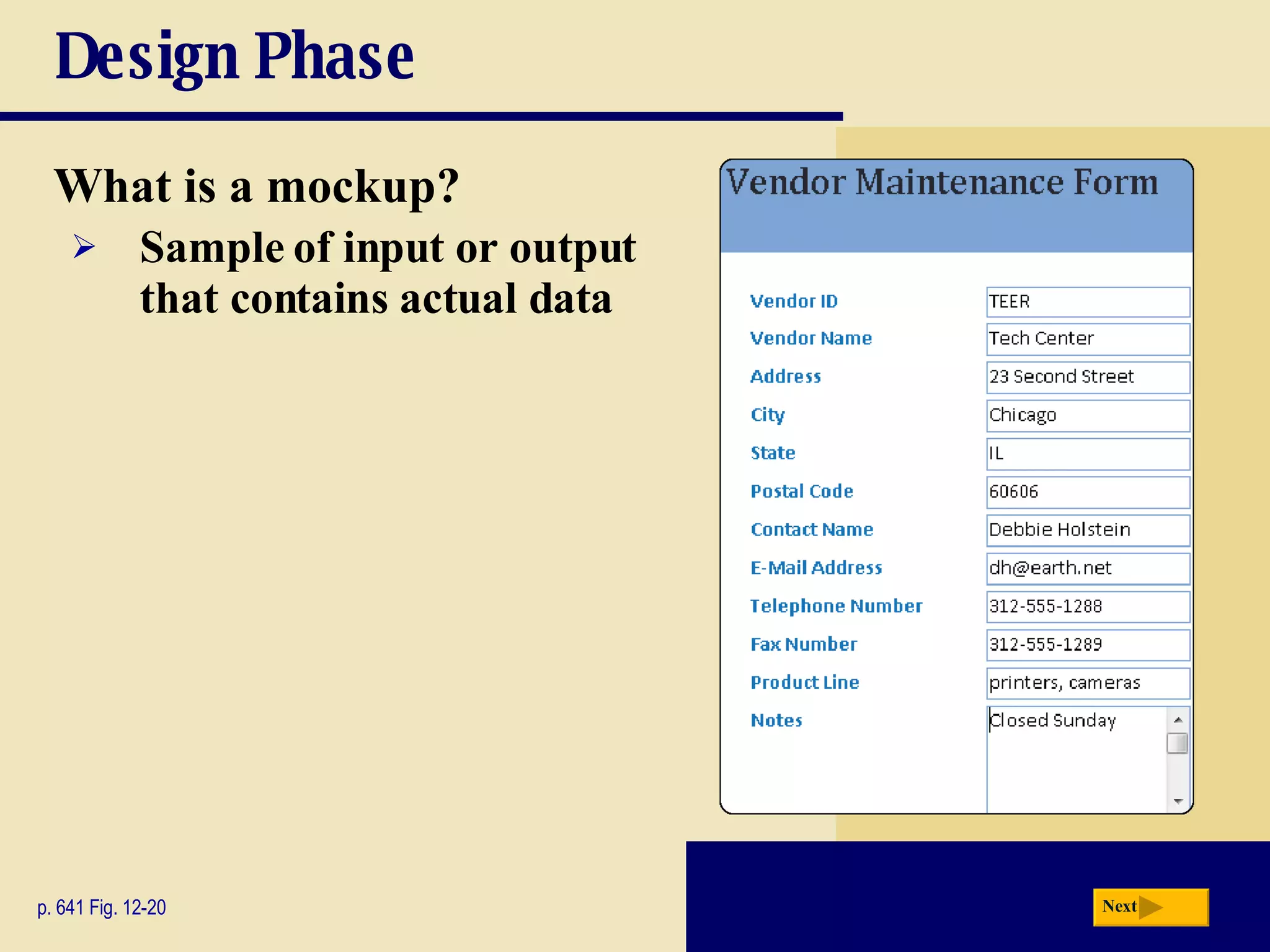
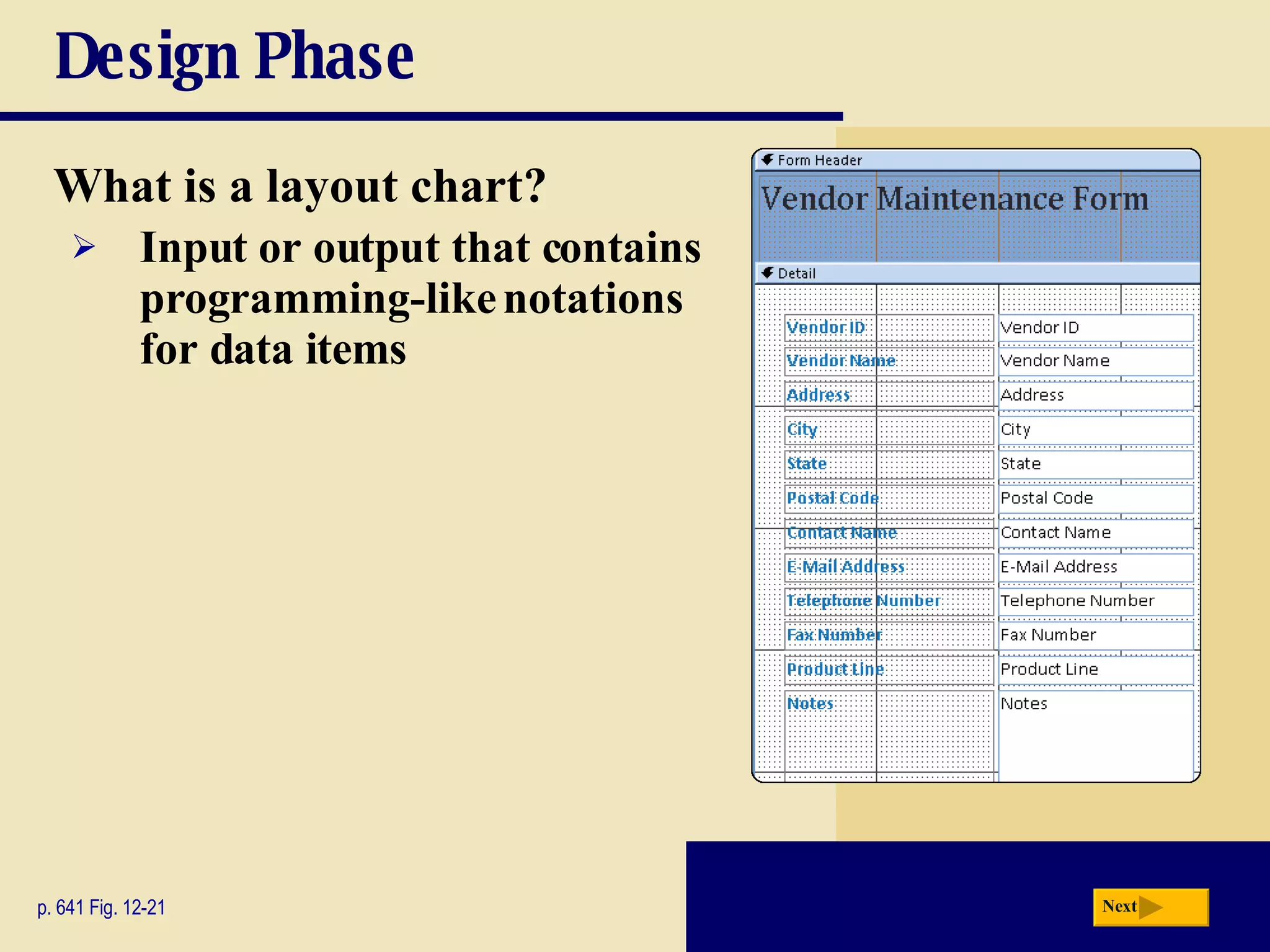
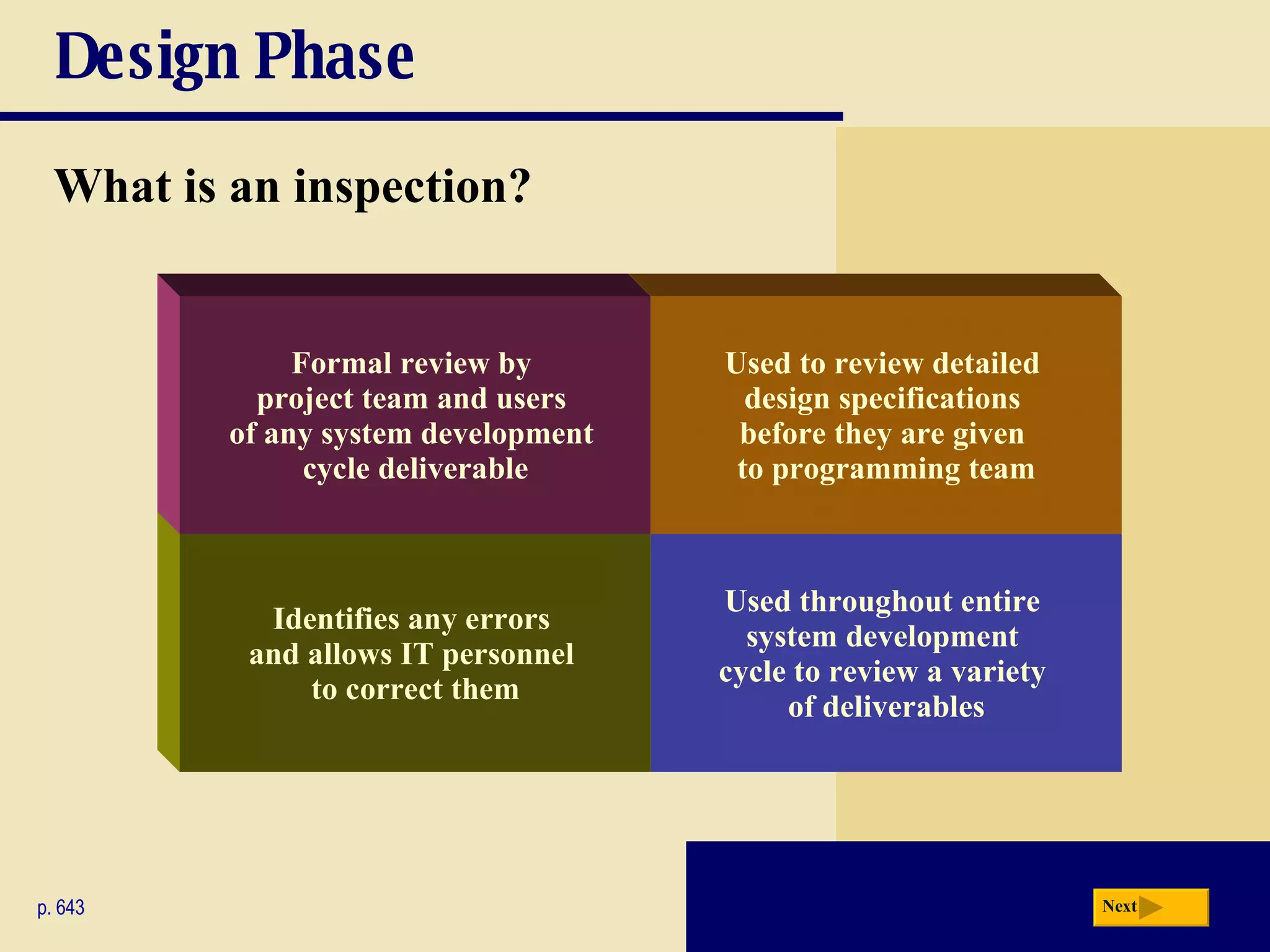
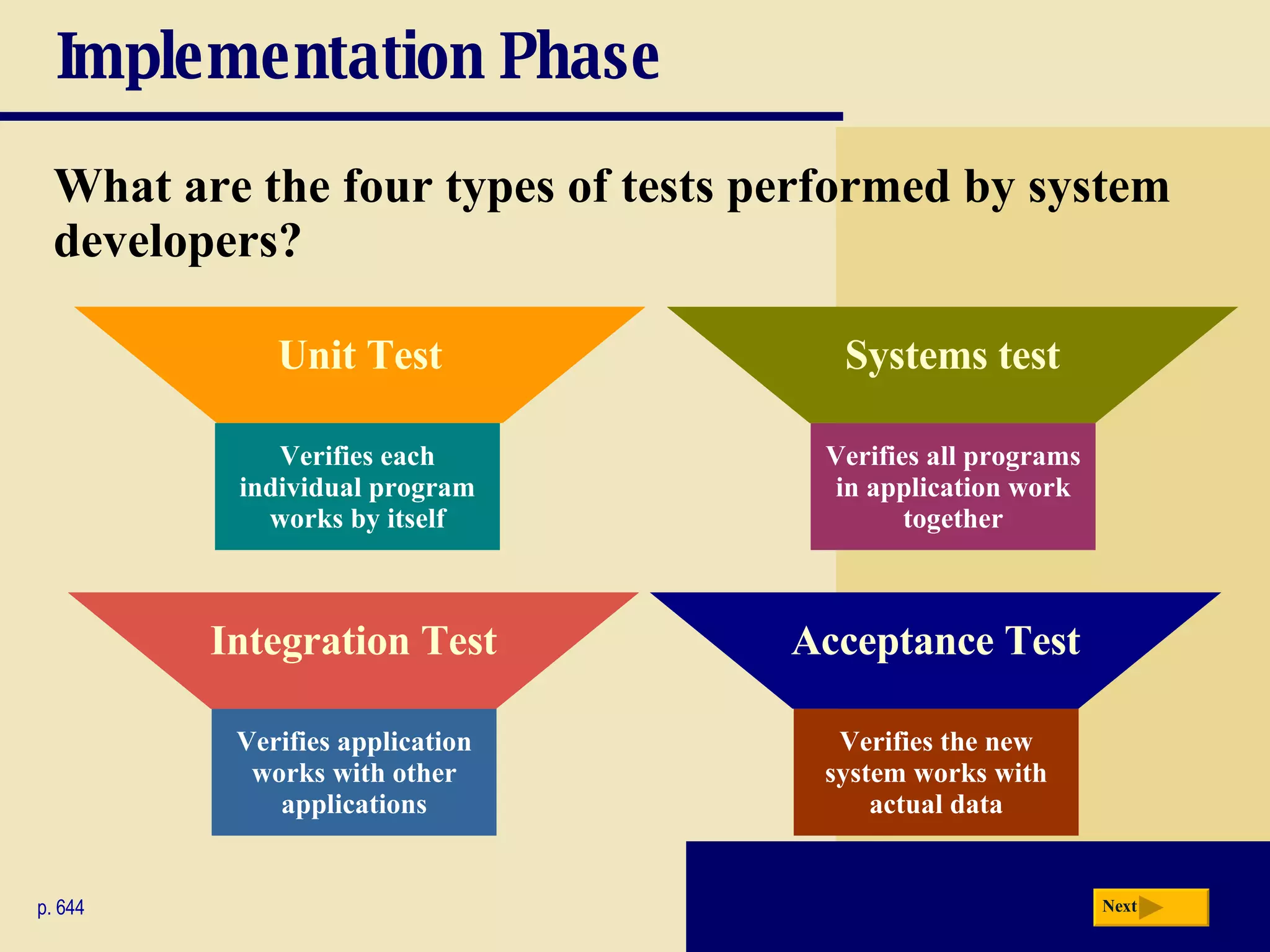
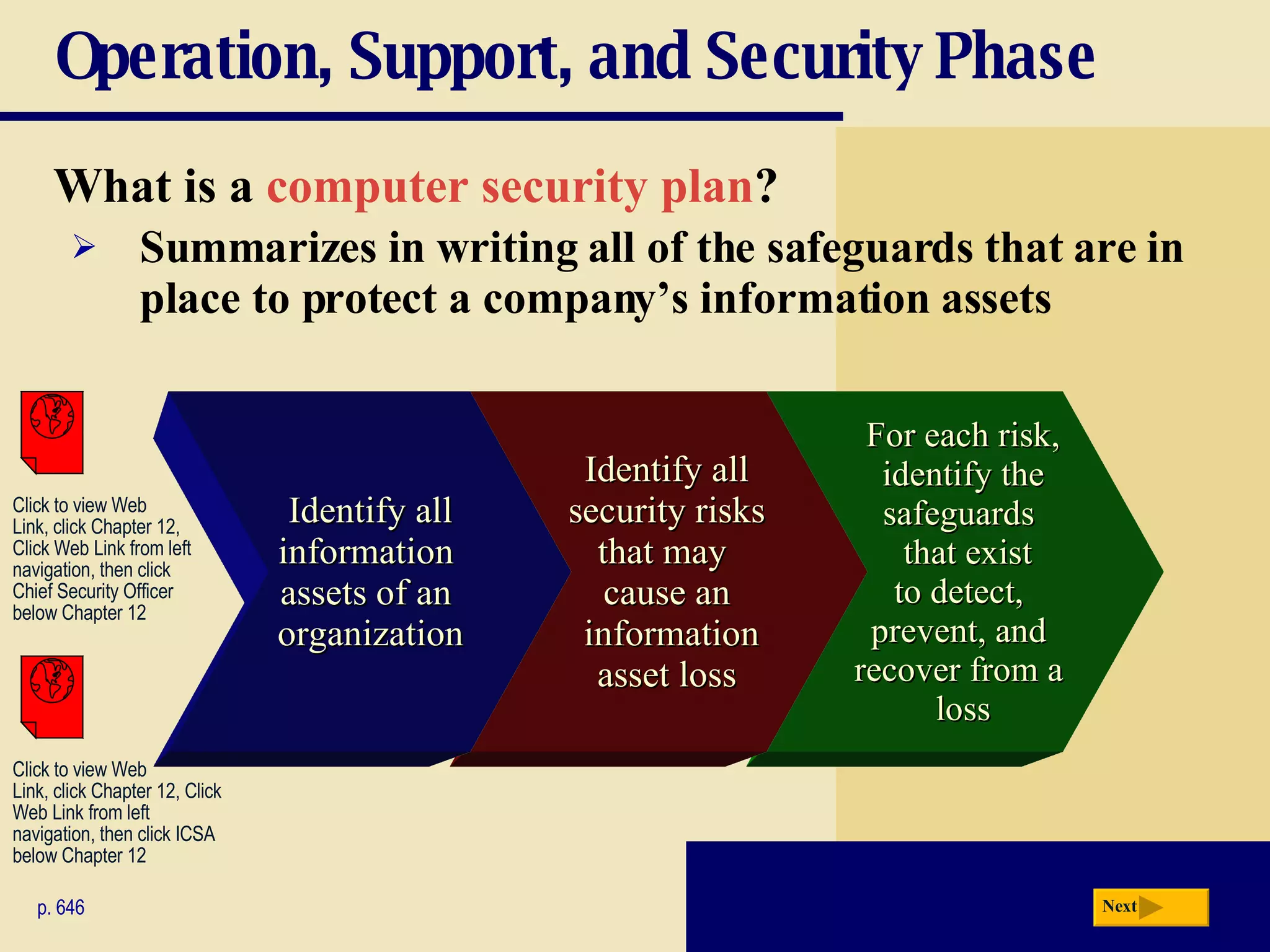
The document discusses the system development life cycle, which includes 5 phases: planning, analysis, design, implementation, and operation/support/security. It describes the activities performed in each phase such as conducting feasibility studies, gathering requirements, designing system details, acquiring hardware/software, testing, and training users. Project management techniques like Gantt charts are used to plan and schedule development projects.