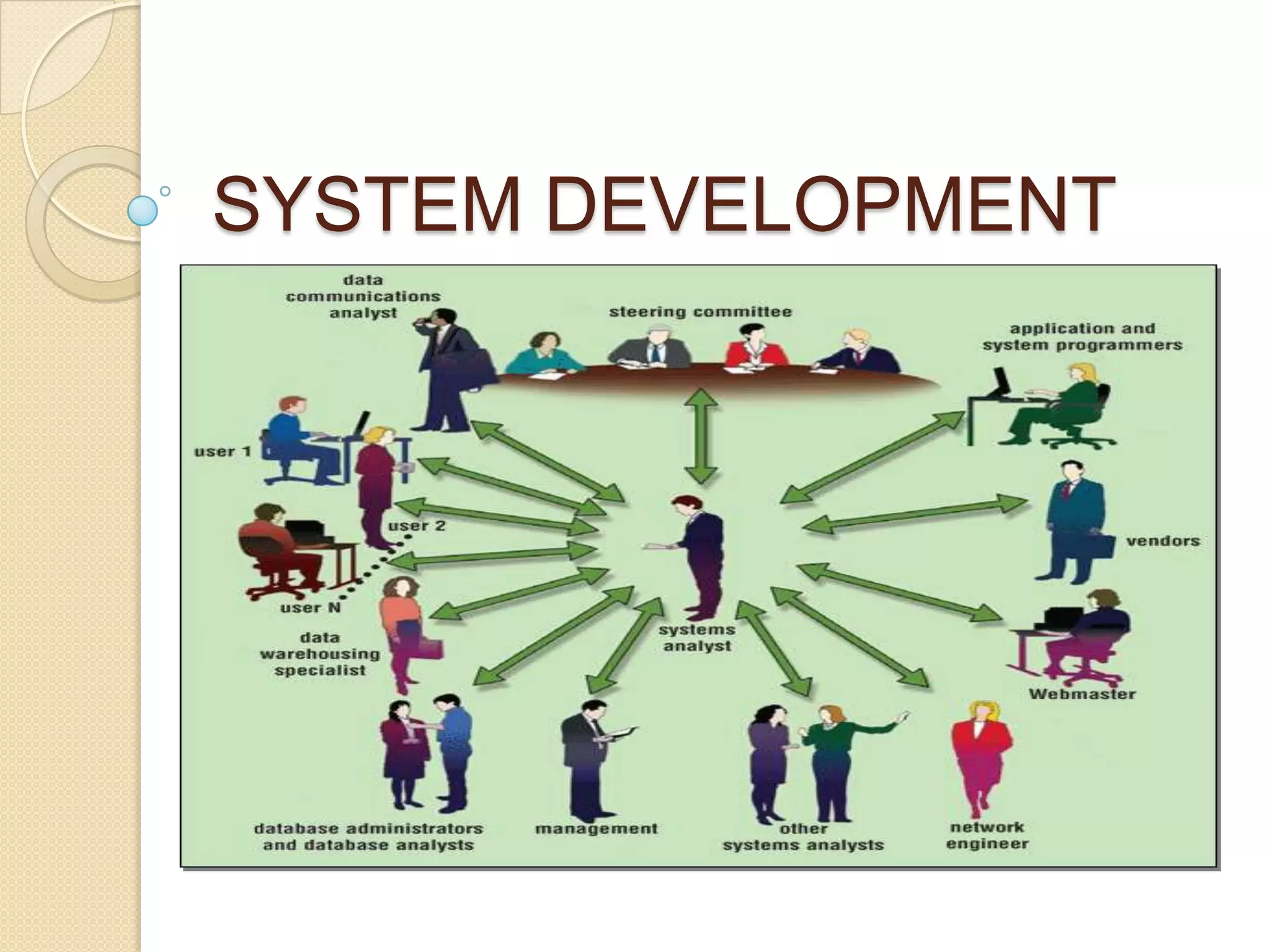
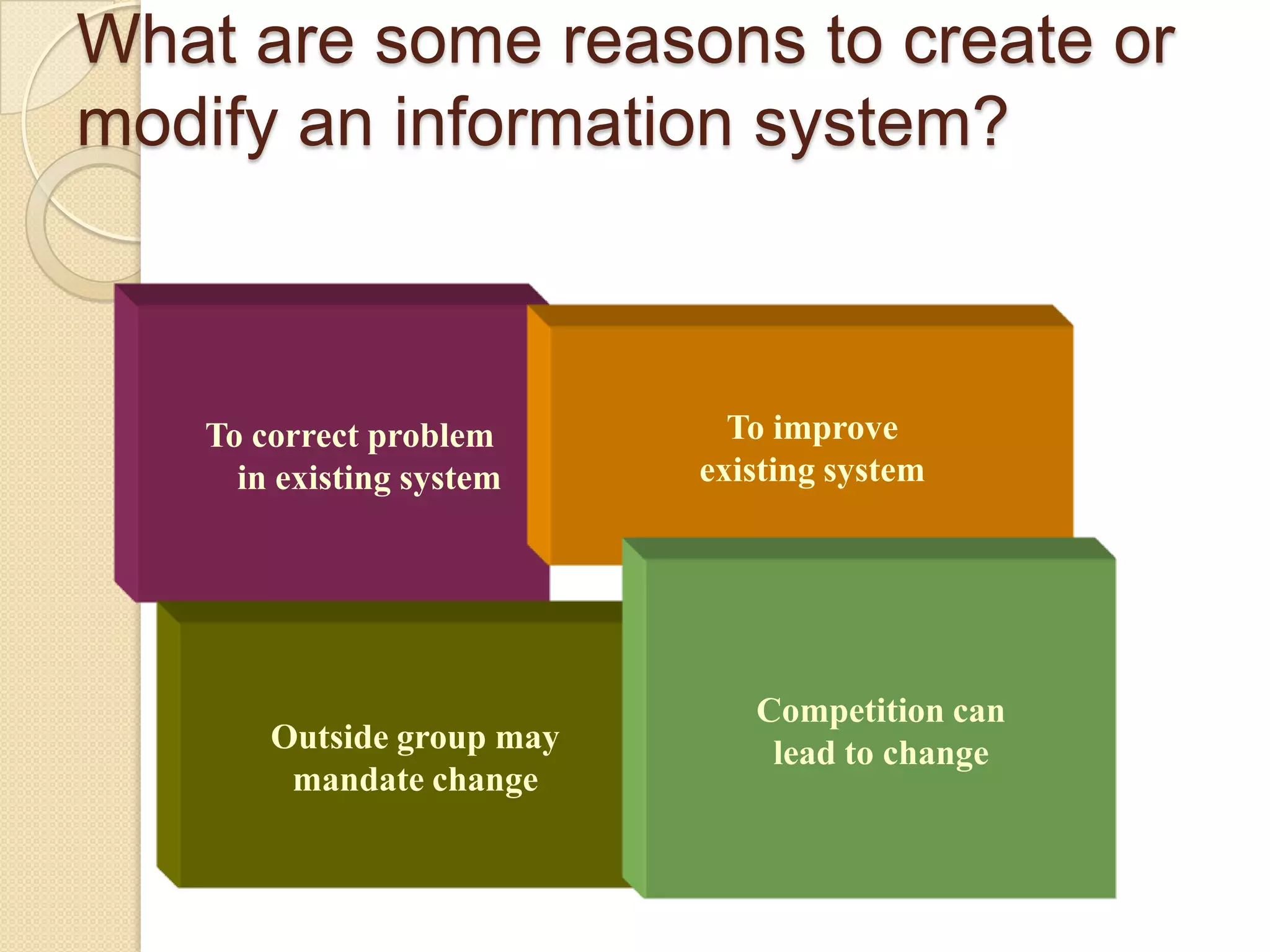
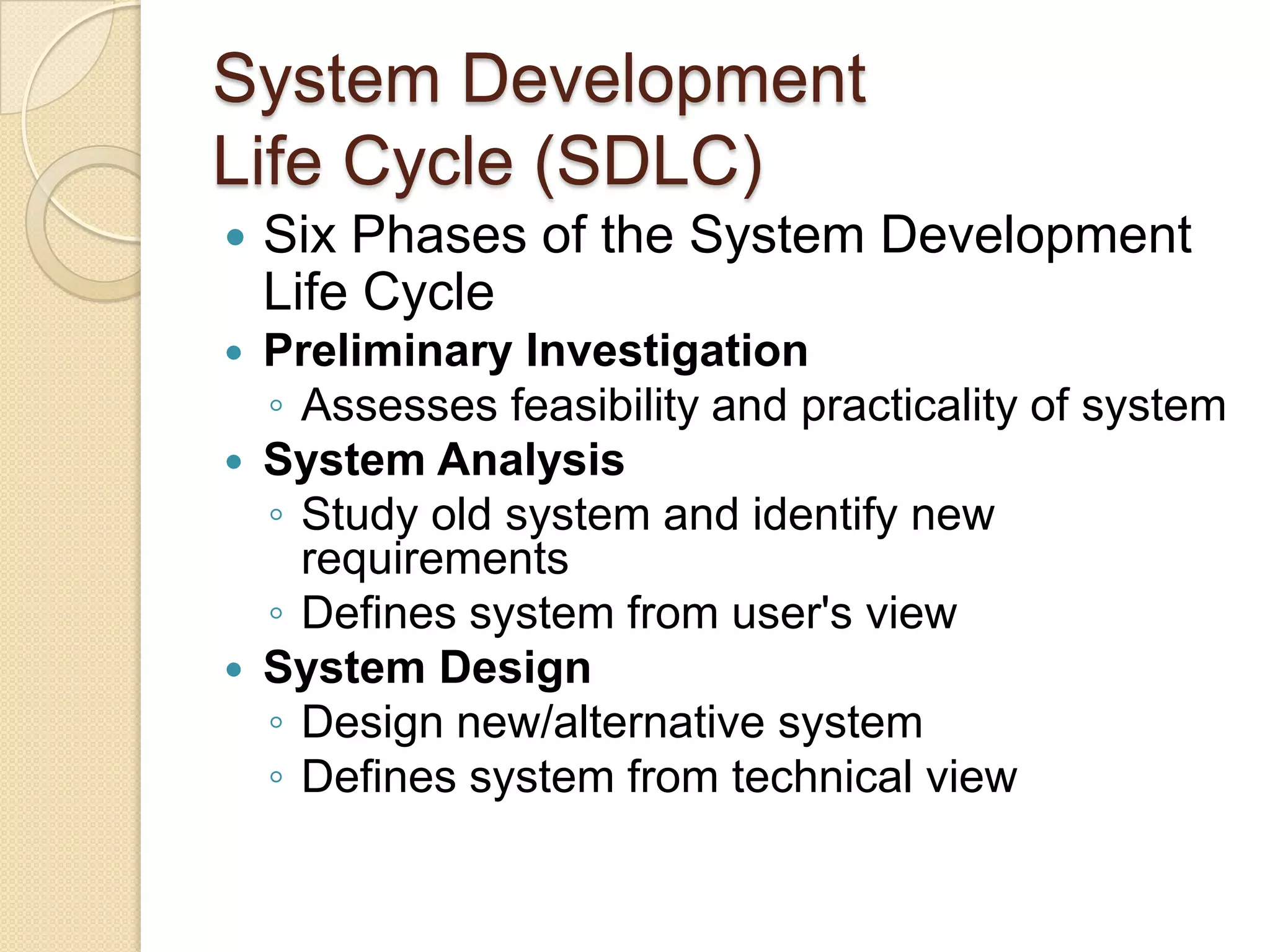
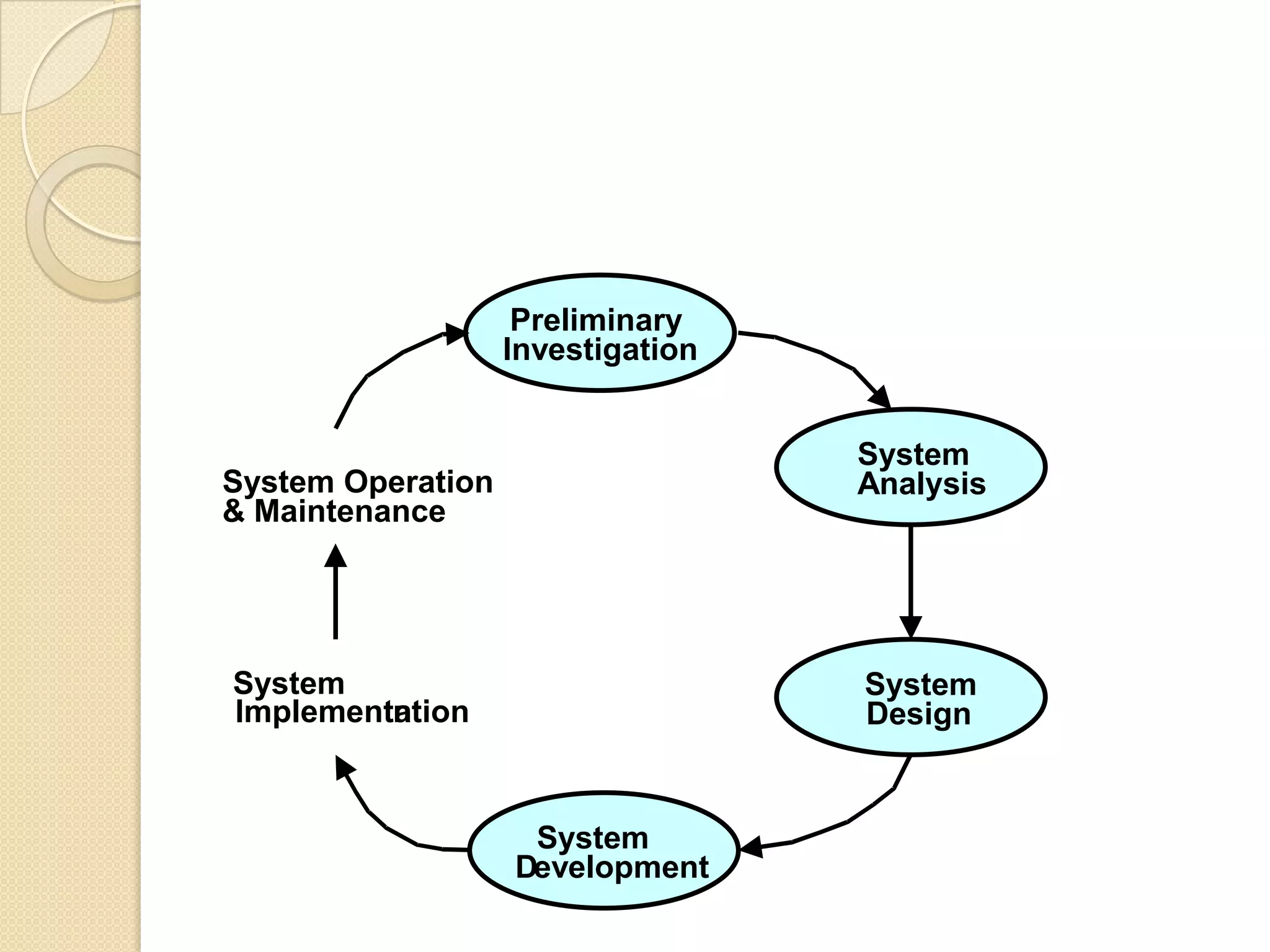
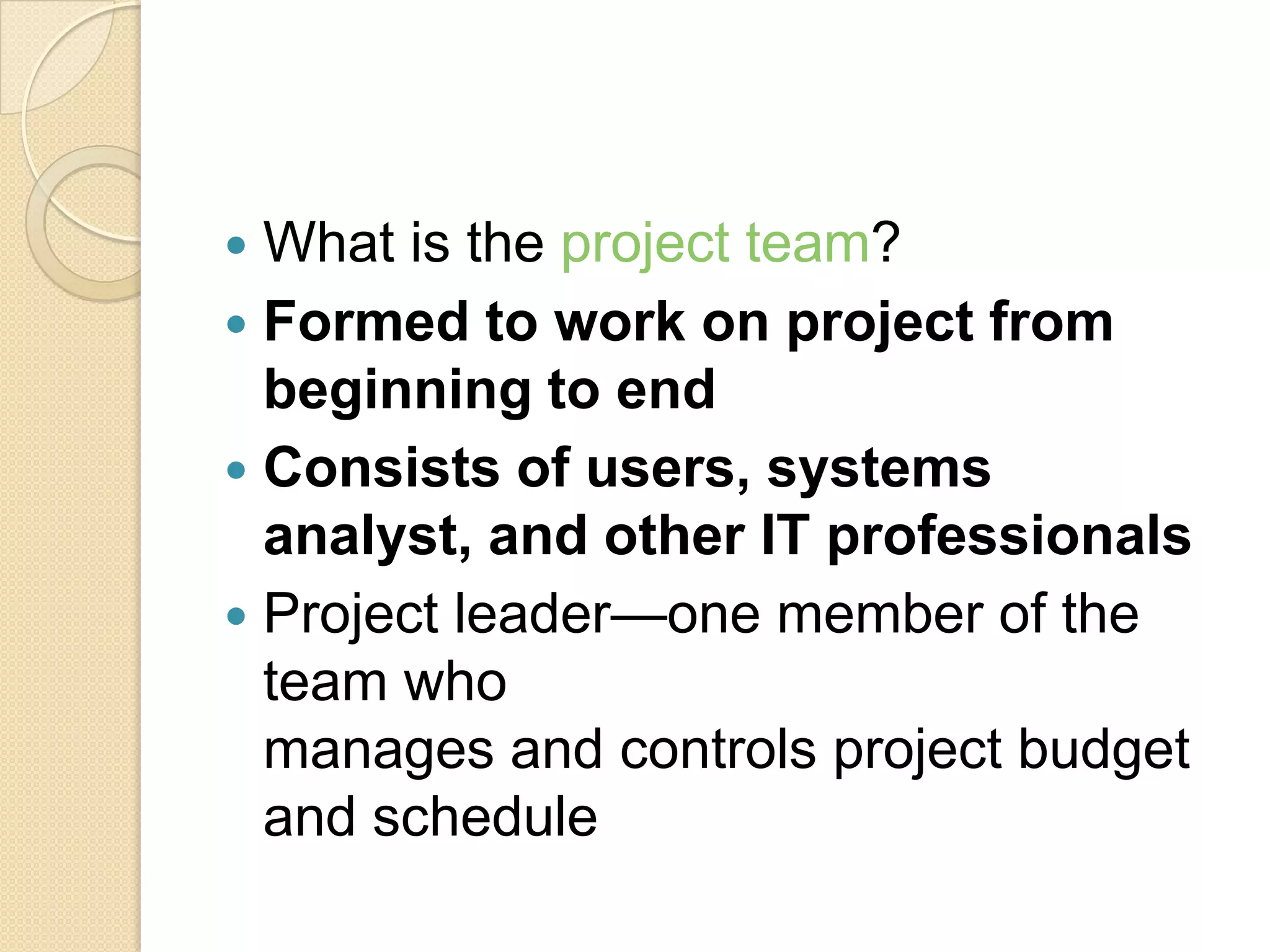
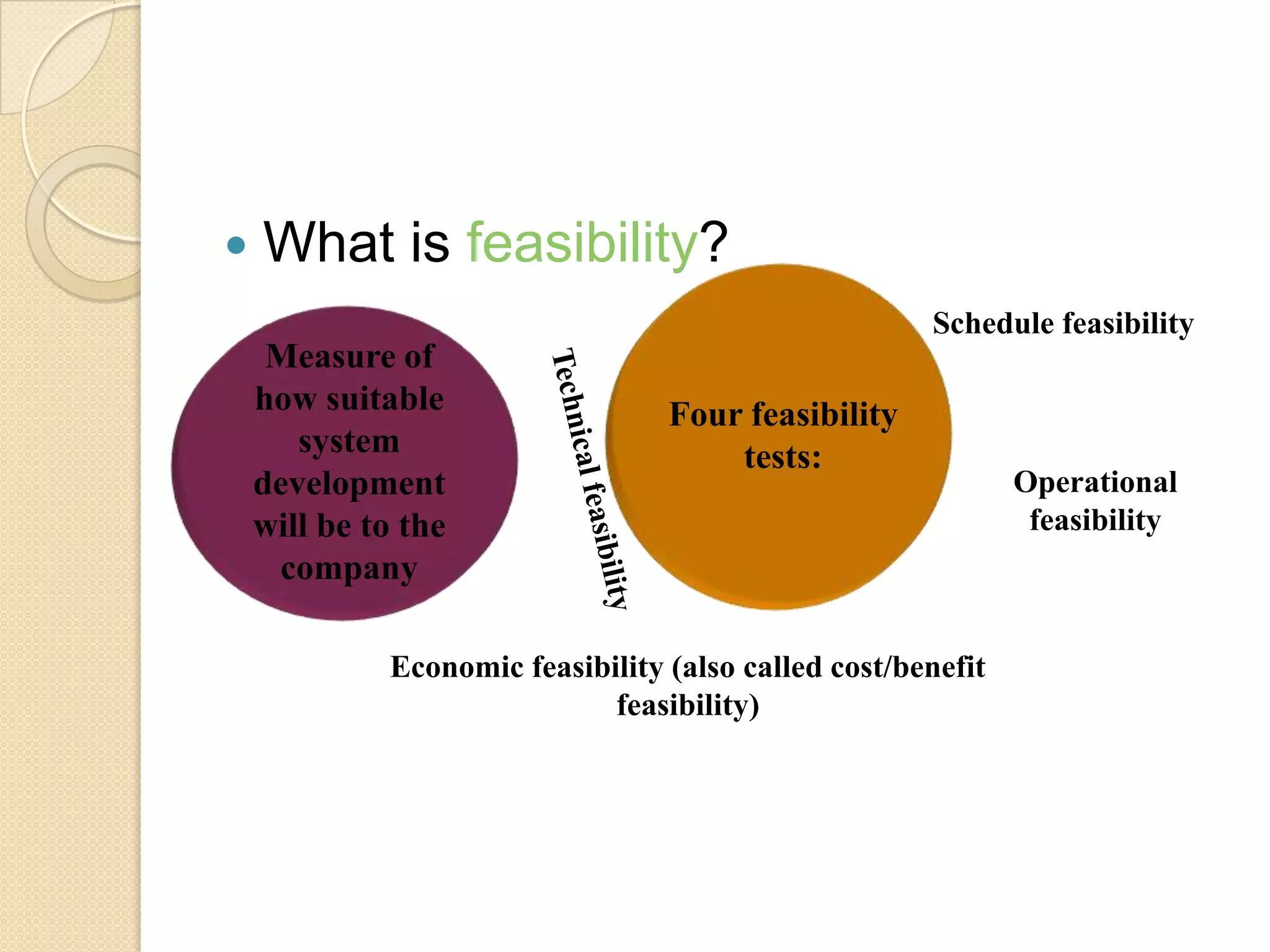
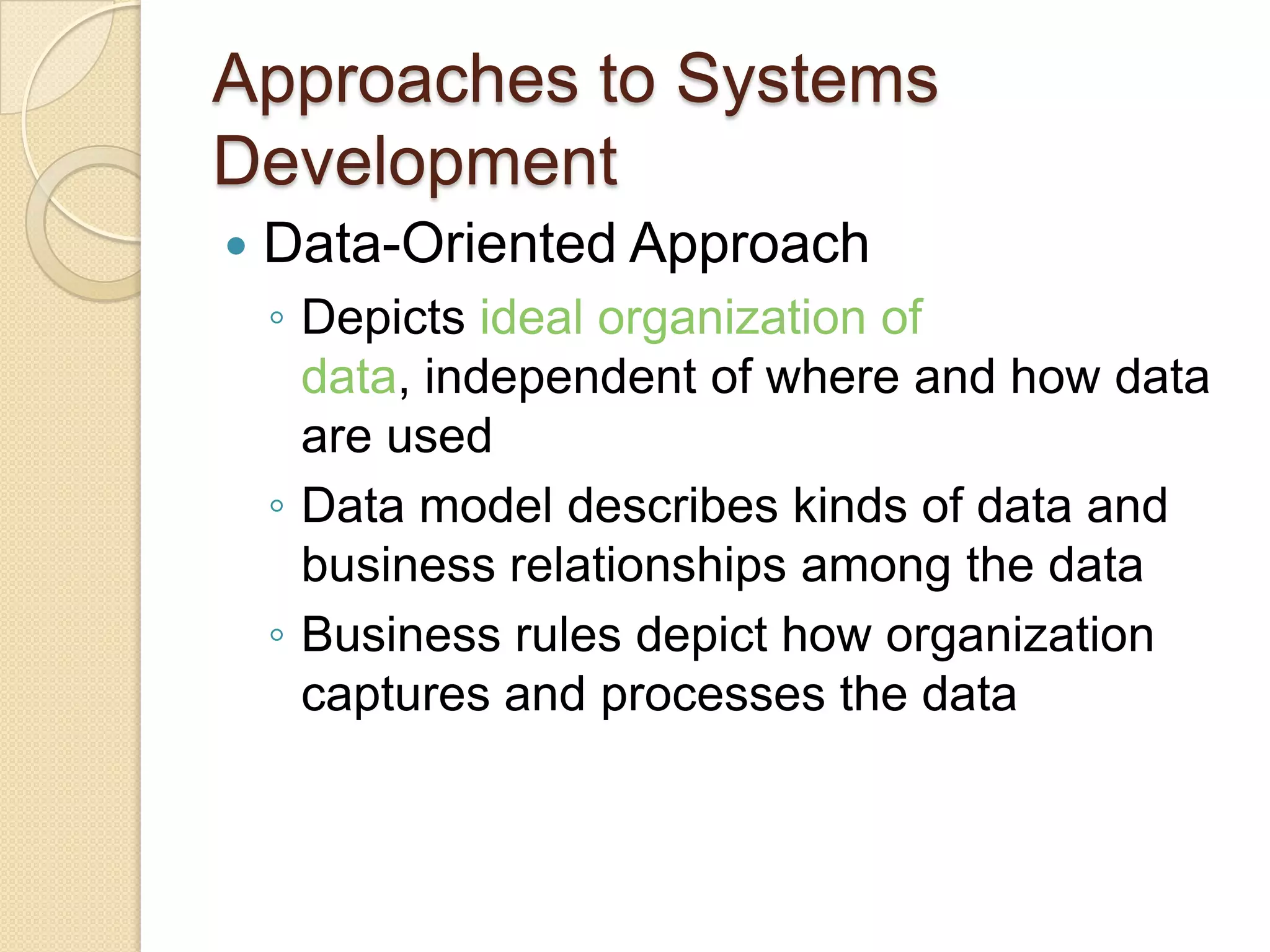
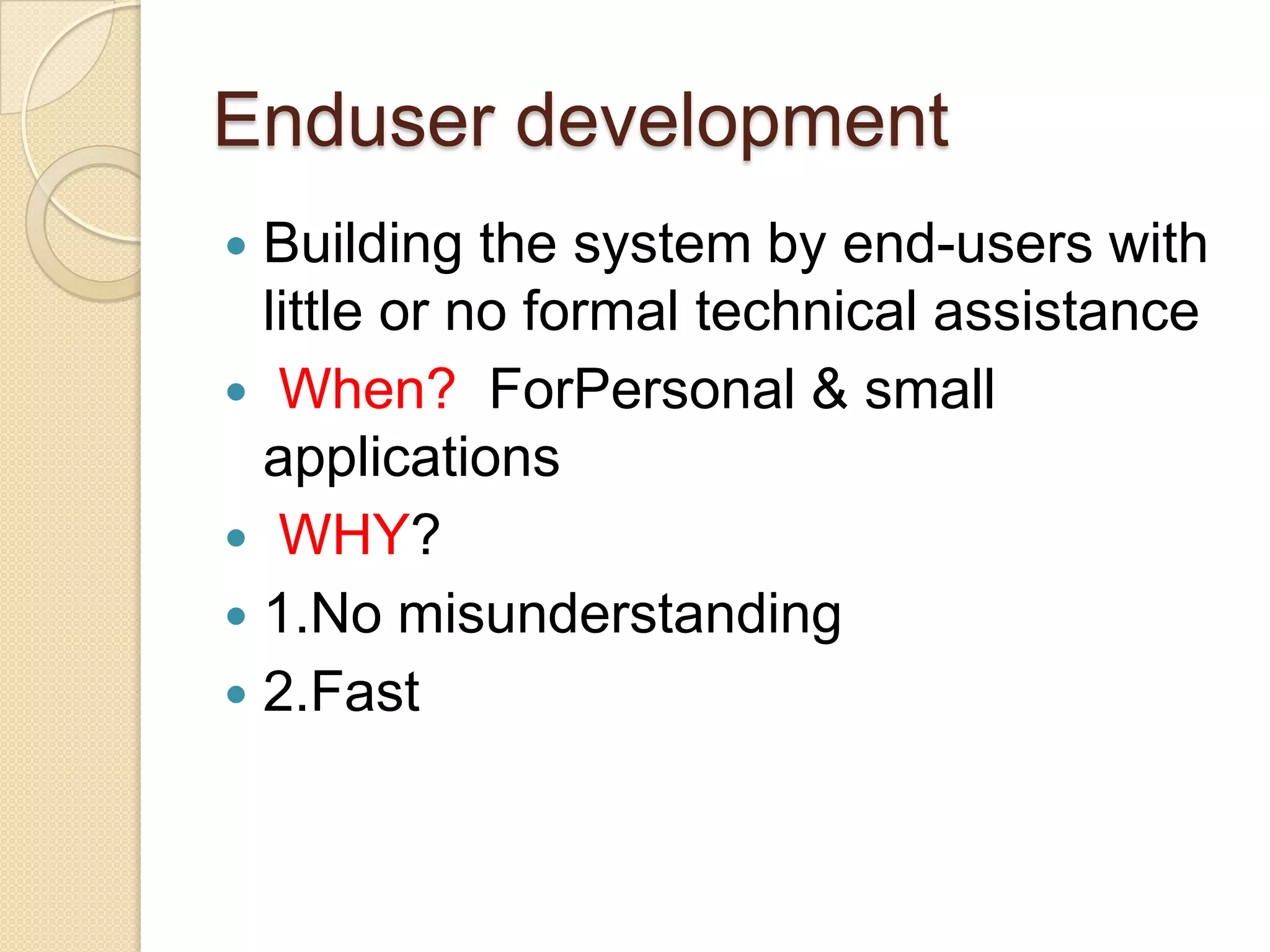
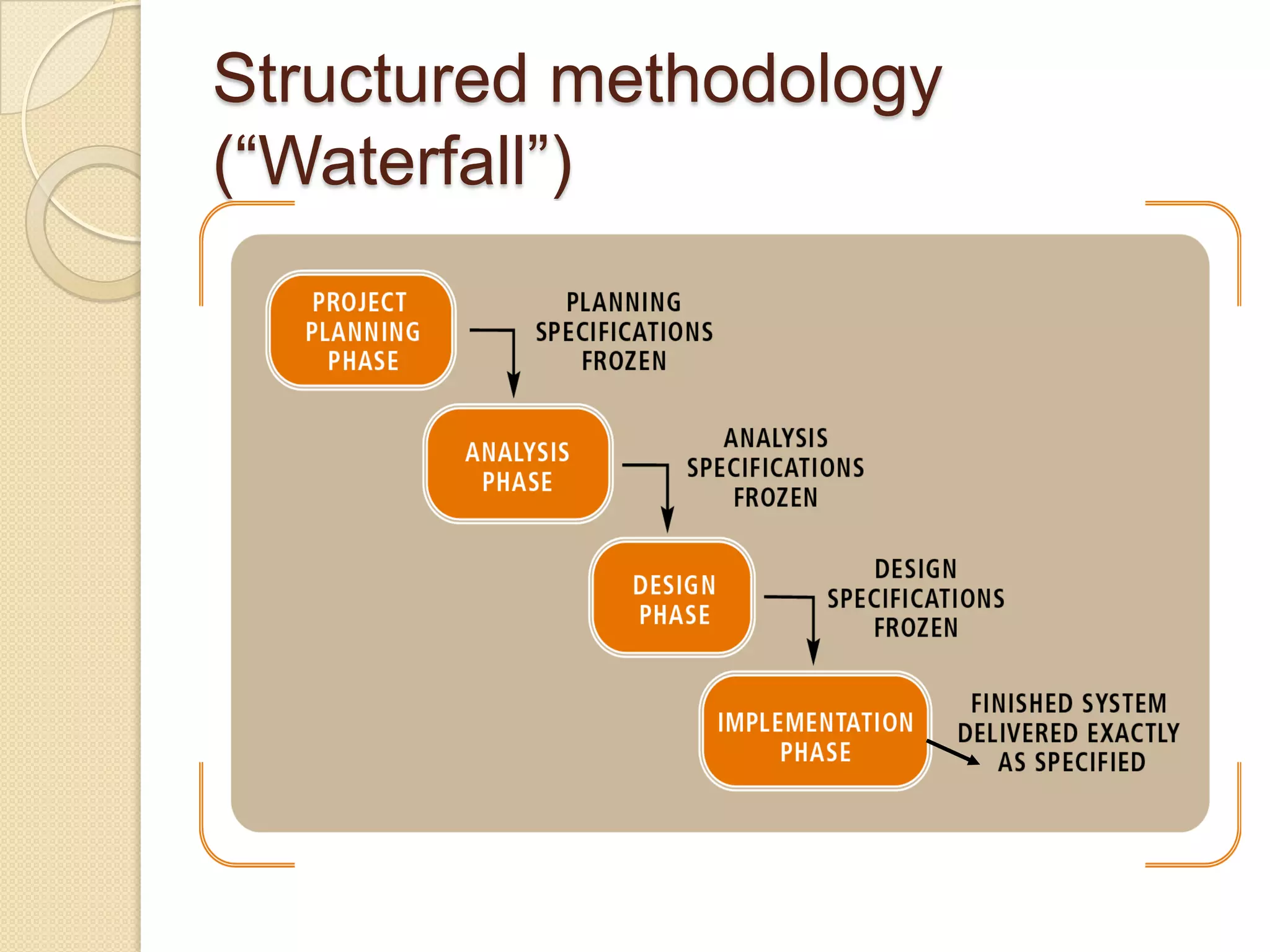
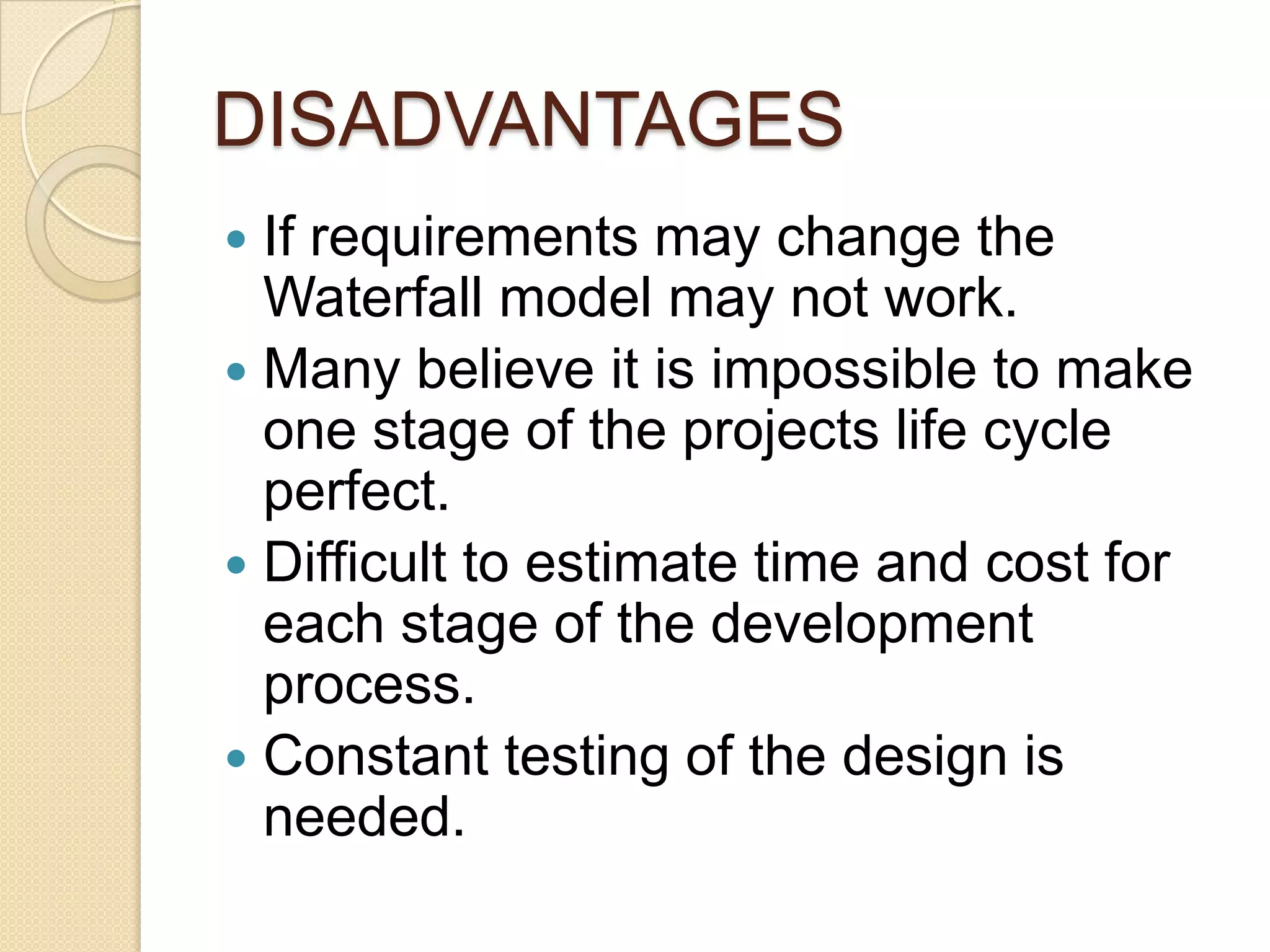
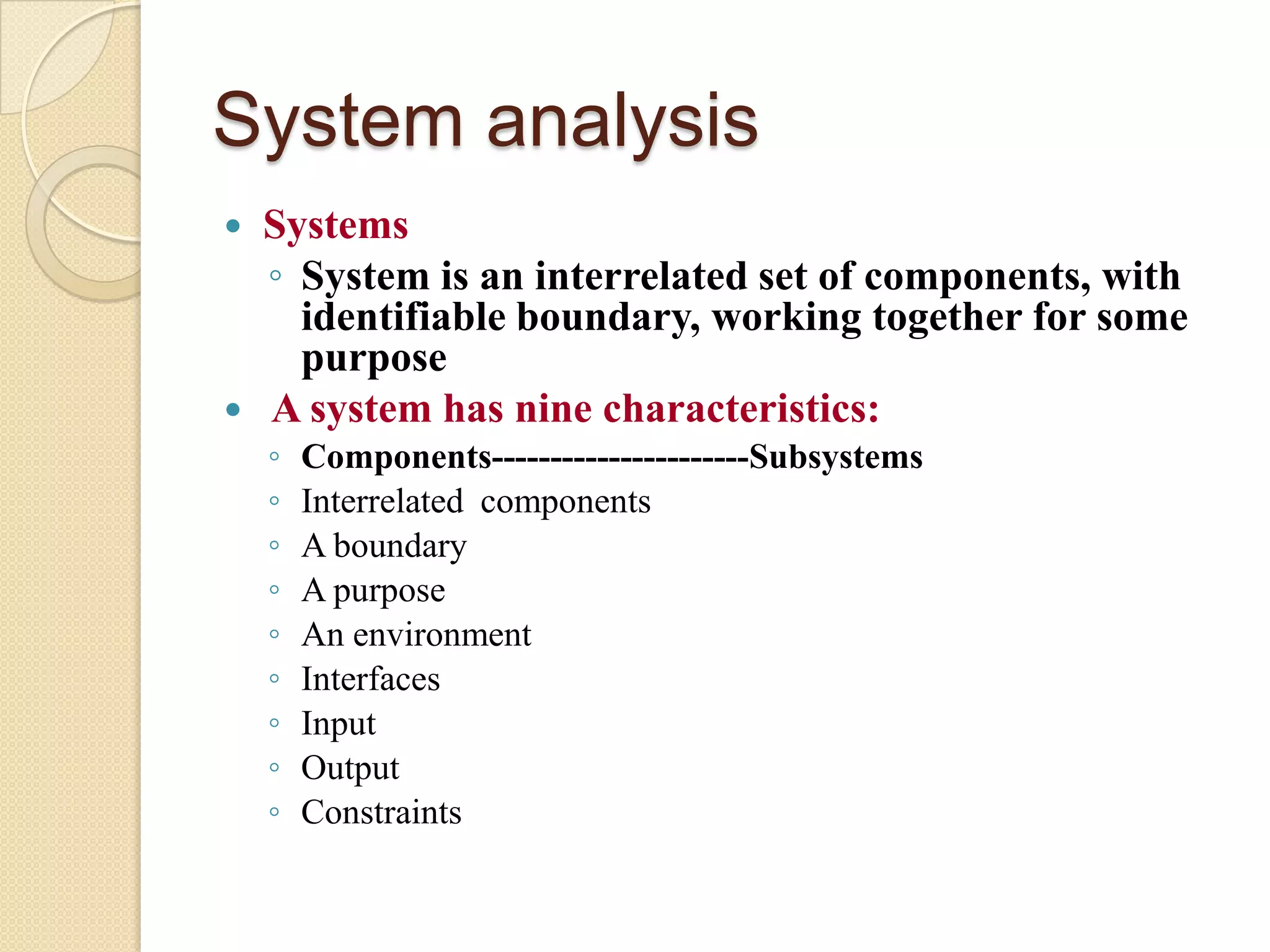
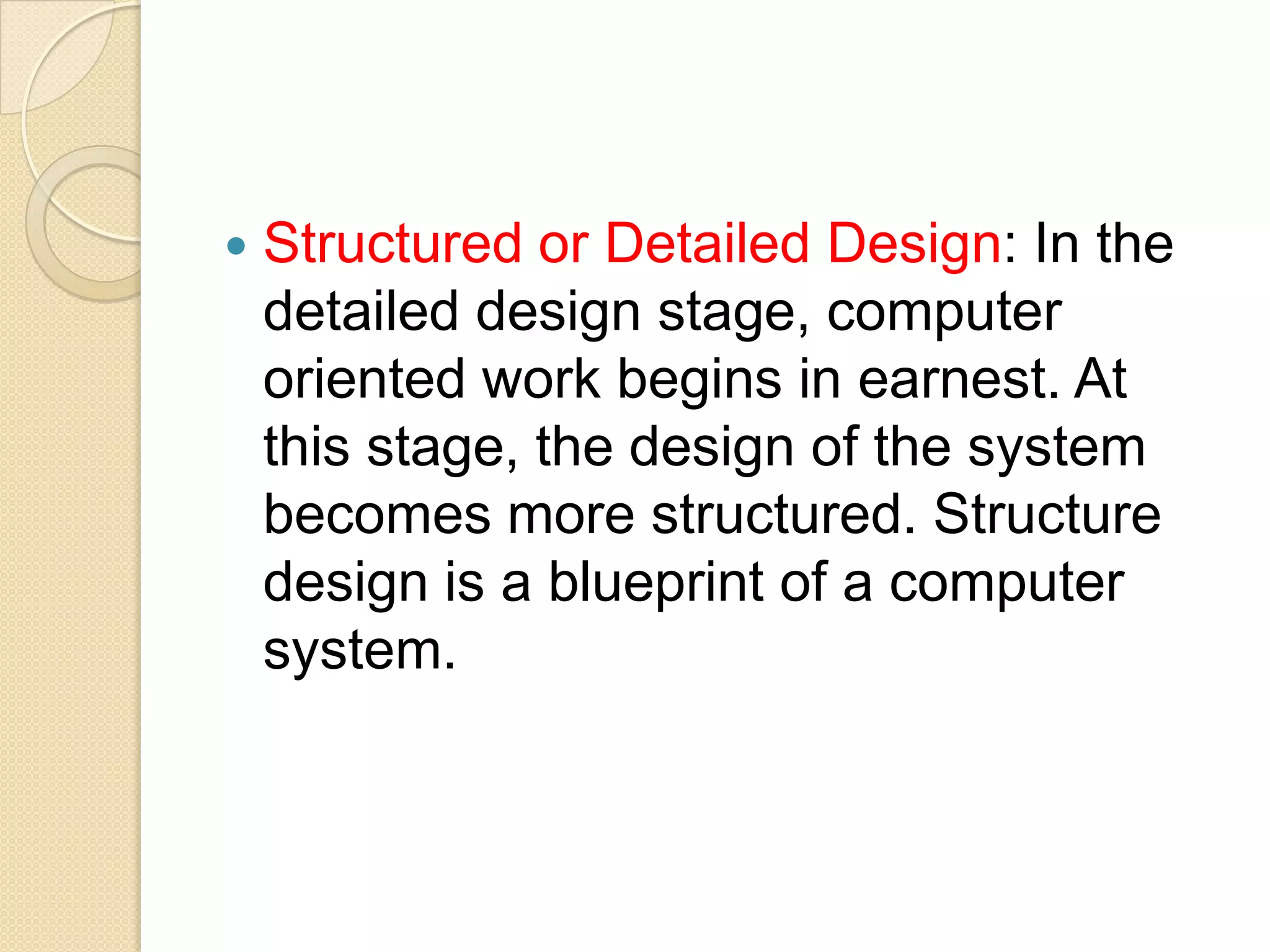
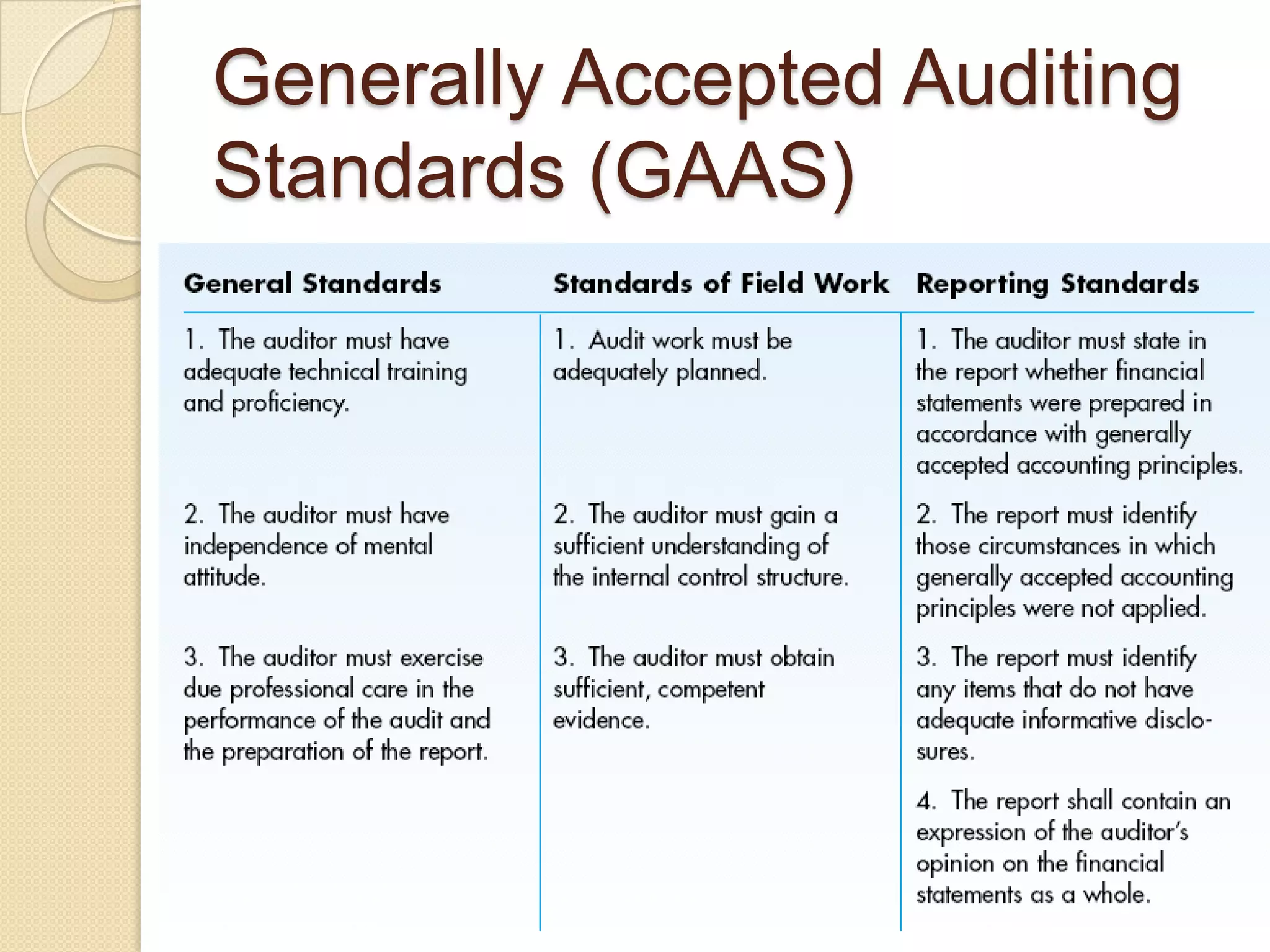
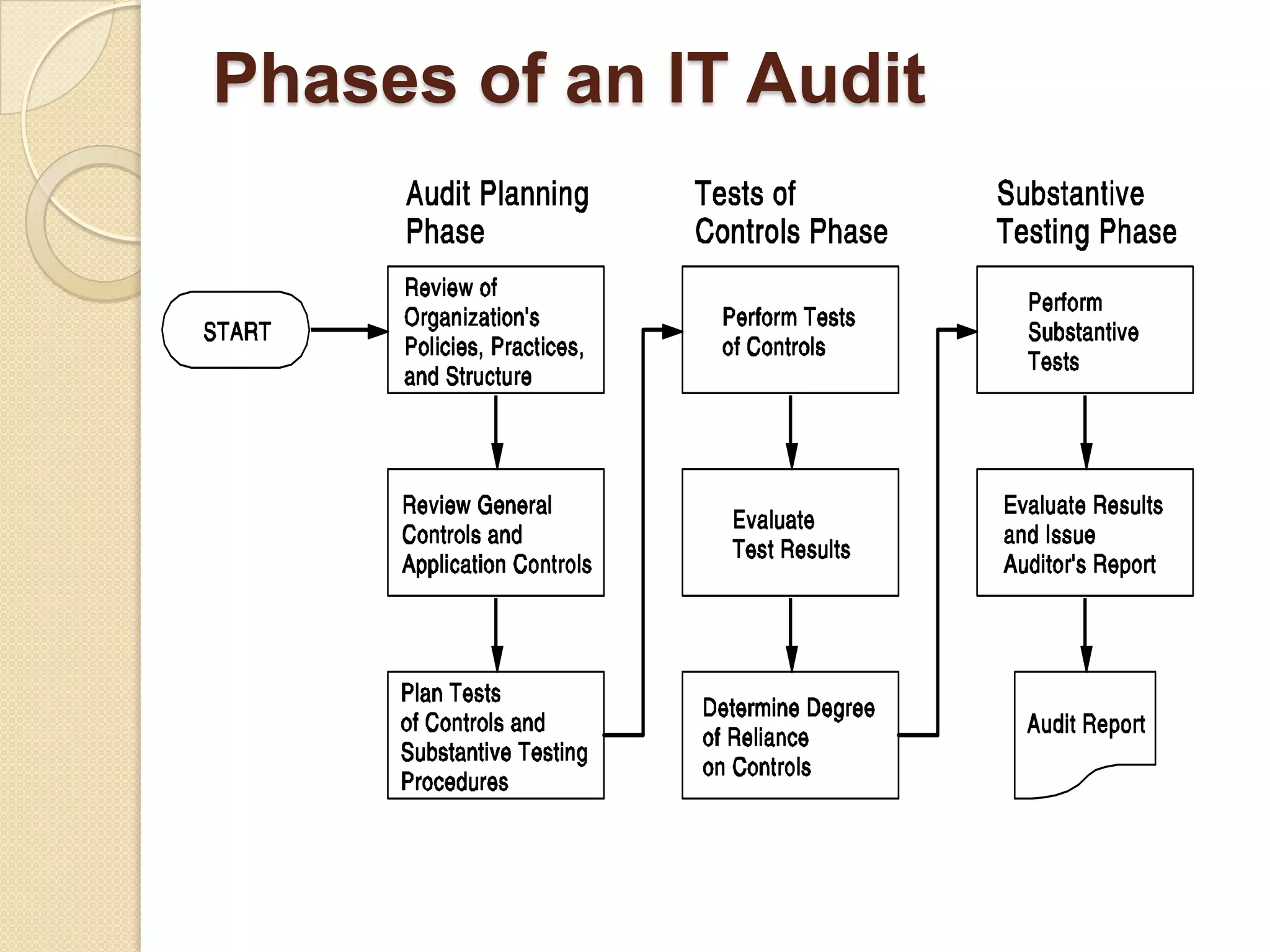
This document provides an overview of system development and information systems. It discusses reasons for creating or modifying systems, such as to correct problems or improve existing systems. It then describes the system development life cycle process, which involves six phases: preliminary investigation, system analysis, system design, system development, system implementation, and system operation and maintenance. It also discusses topics such as the roles of systems analysts, feasibility analysis, different approaches to system development, and implementation considerations.