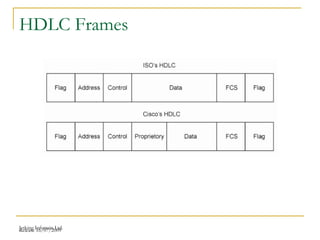
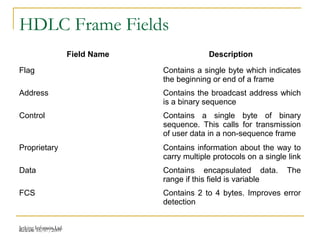
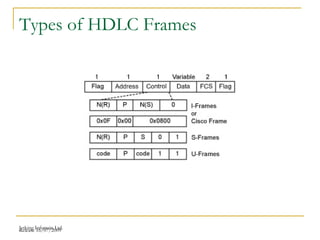
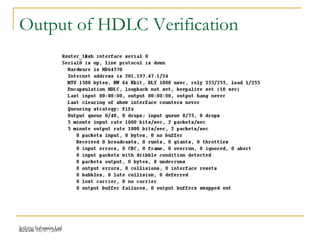
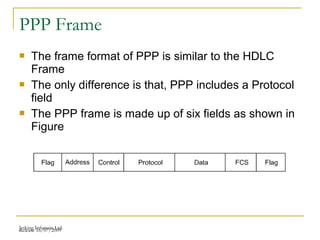
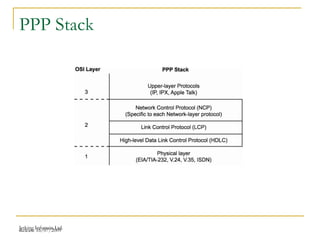
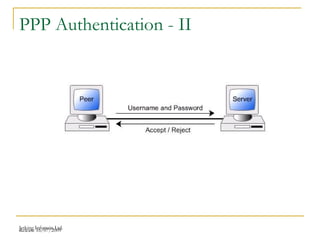
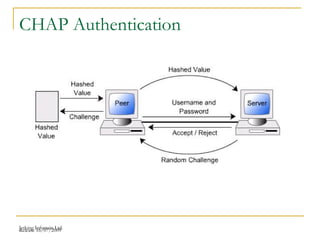
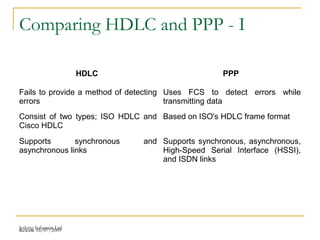
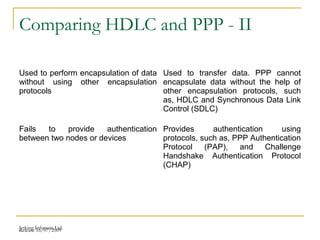
The document discusses point-to-point connections using HDLC and PPP protocols. It begins by explaining wide area networks and the components that make them up. It then describes data-link protocols HDLC and PPP in detail, including their frame formats and how they establish and verify connections. The document also provides guidance on configuring these protocols on routers and troubleshooting potential issues that could arise with mismatched configurations.