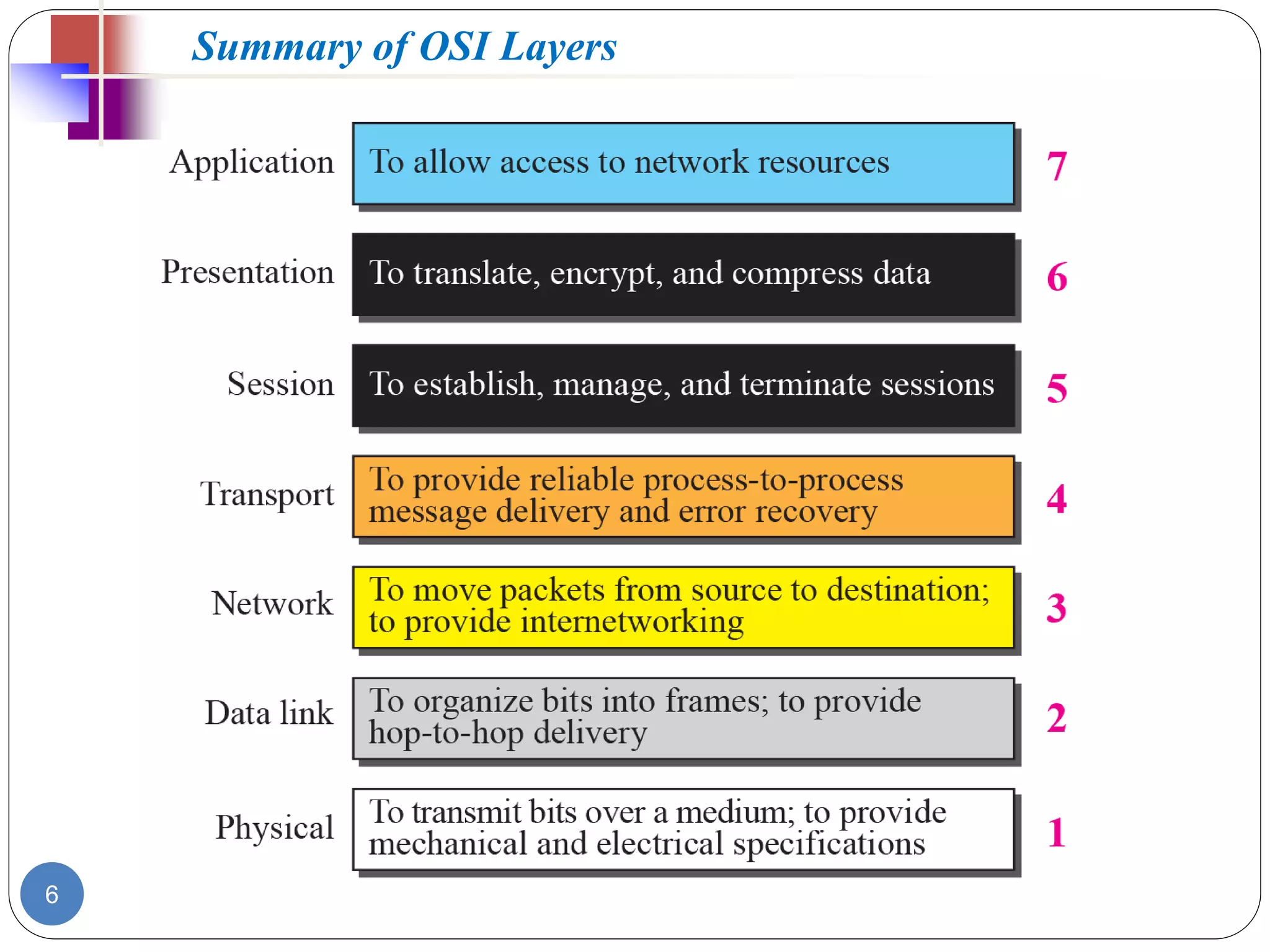
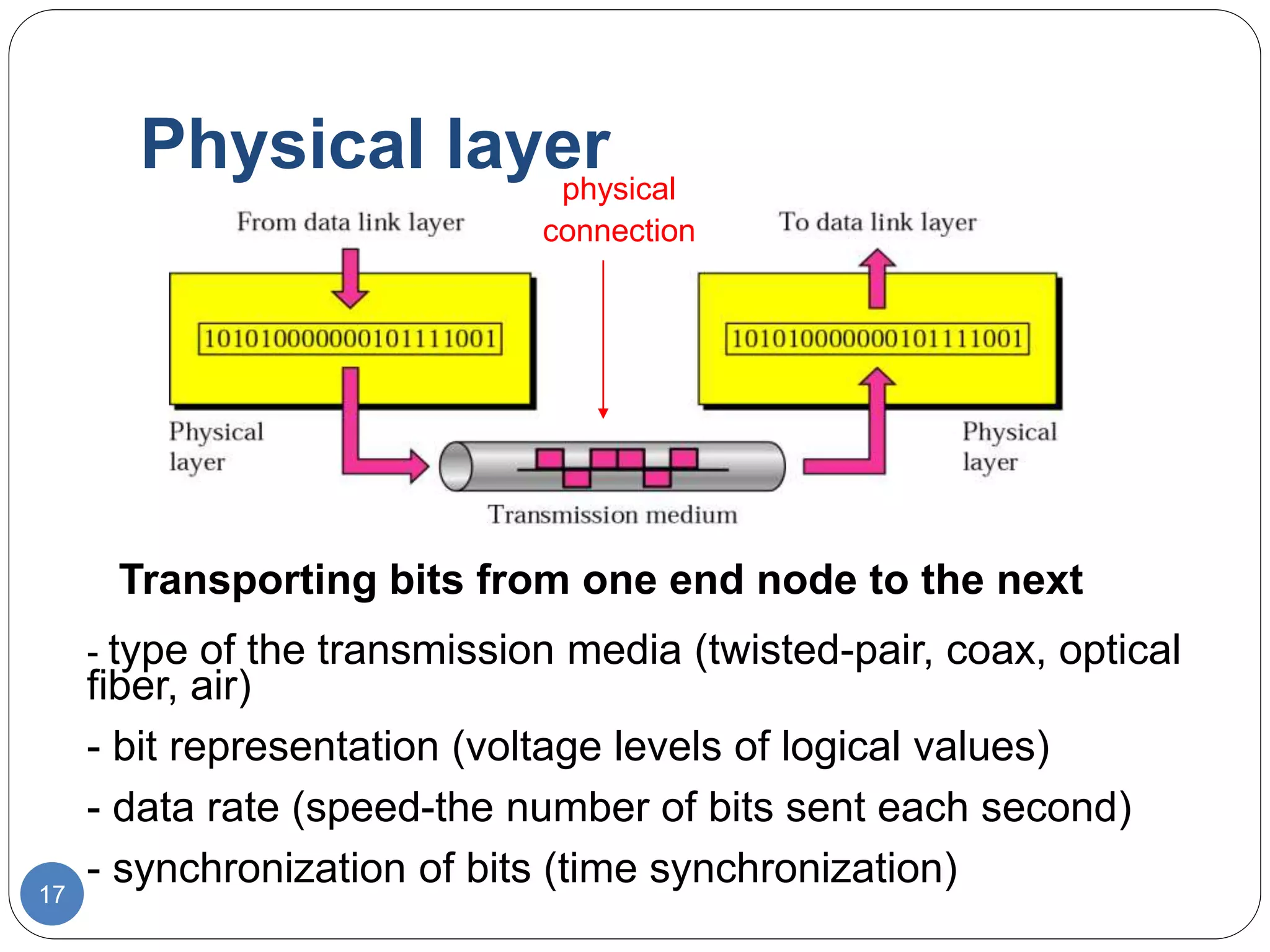
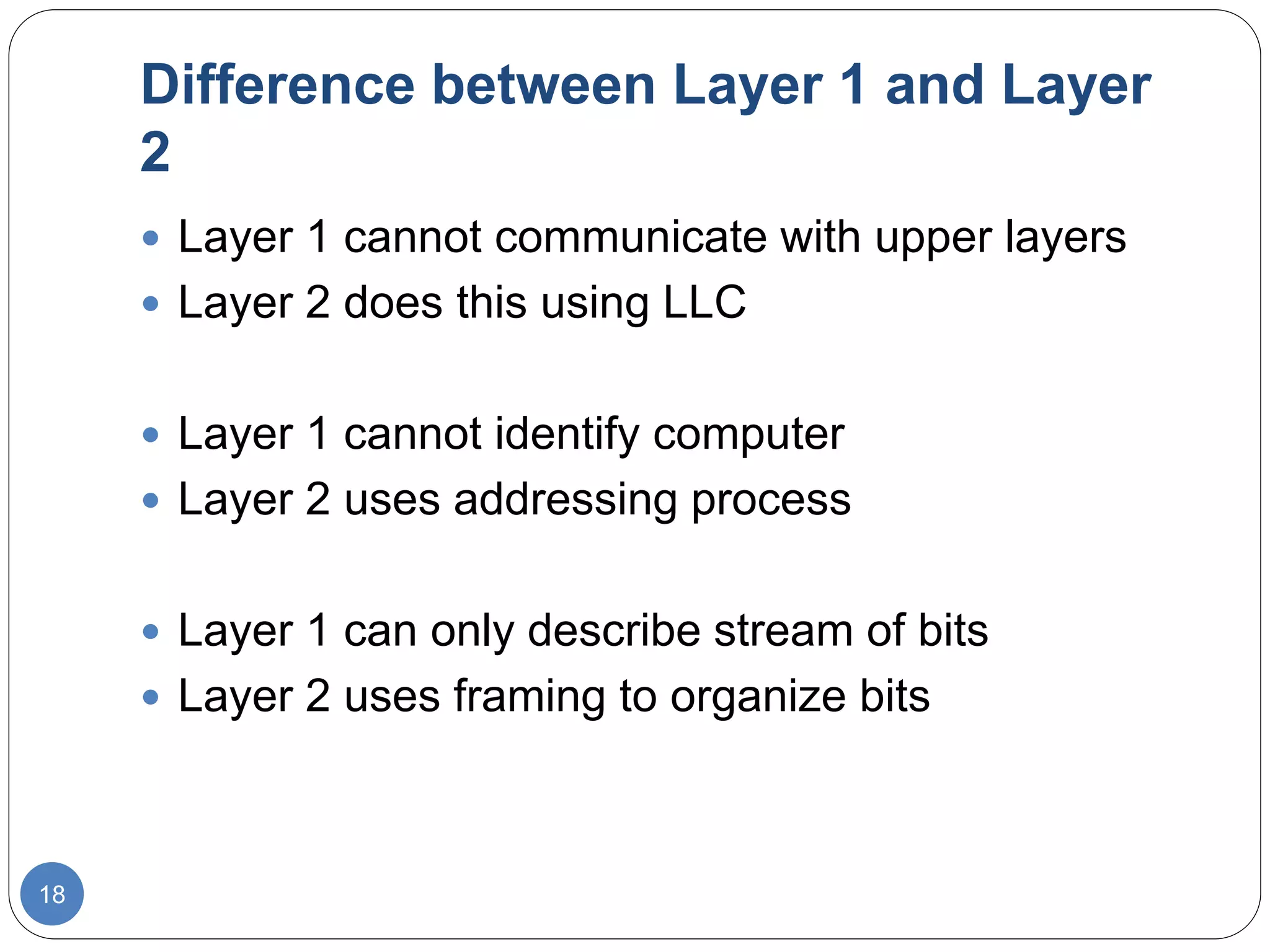
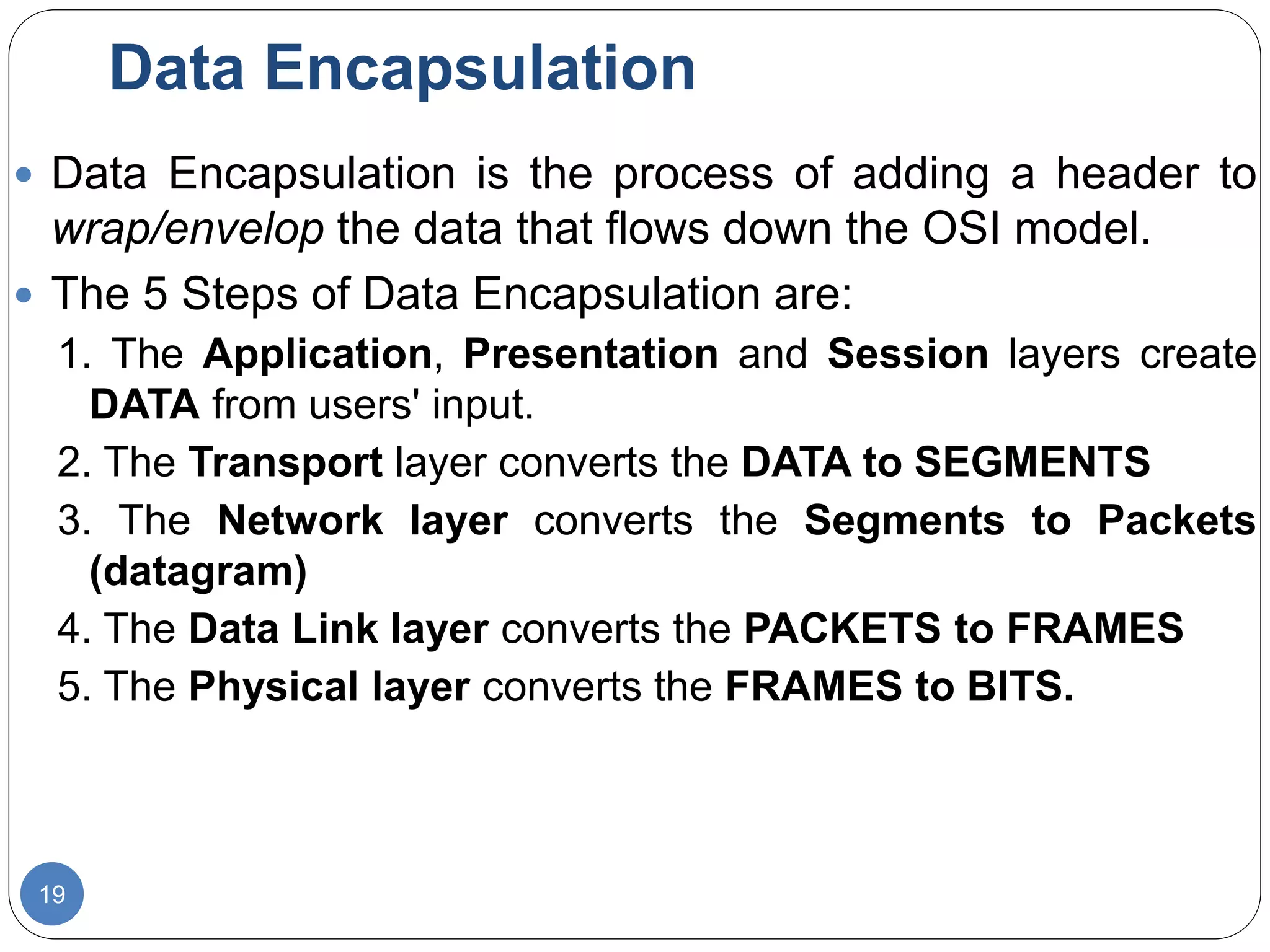
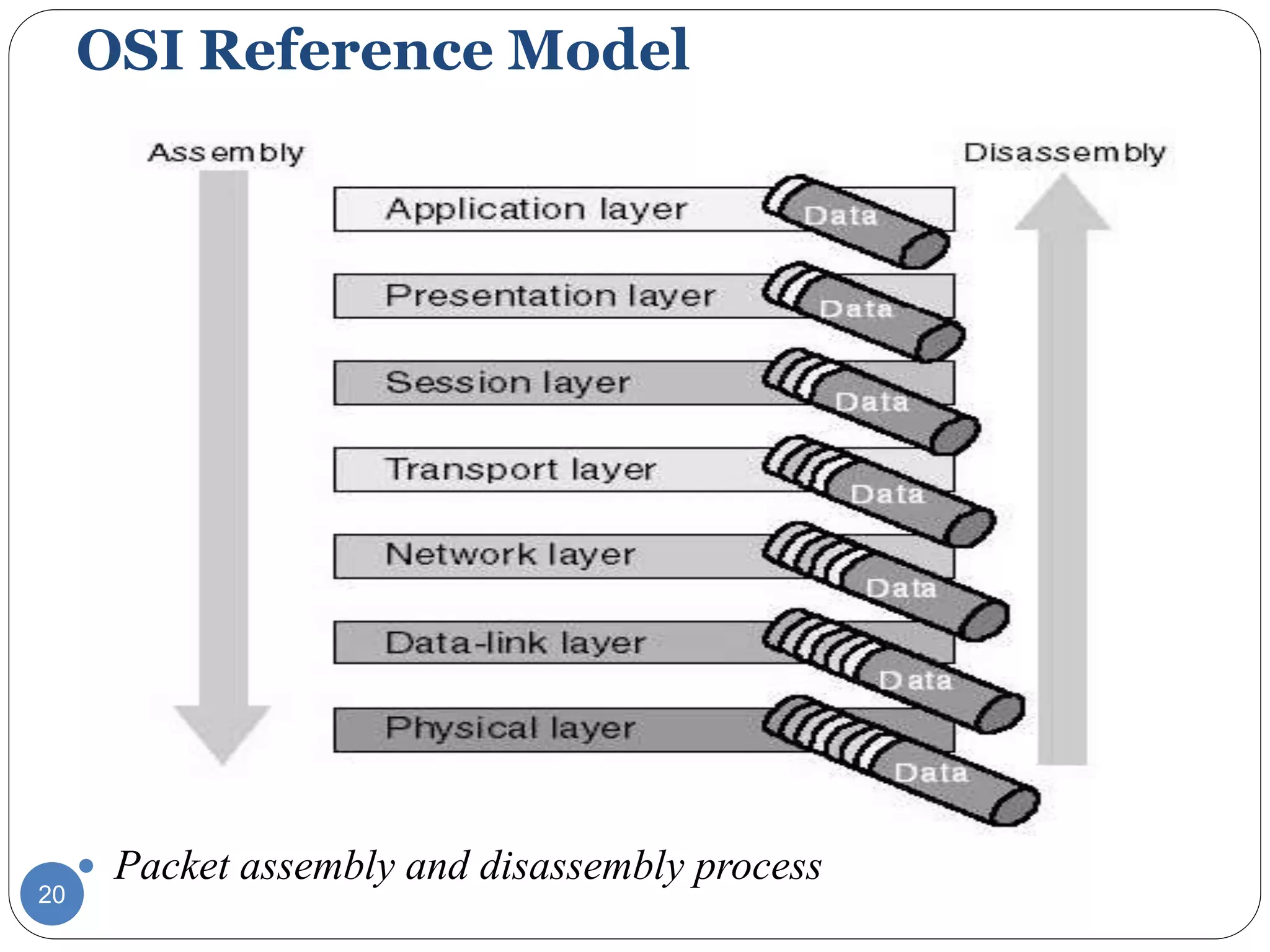
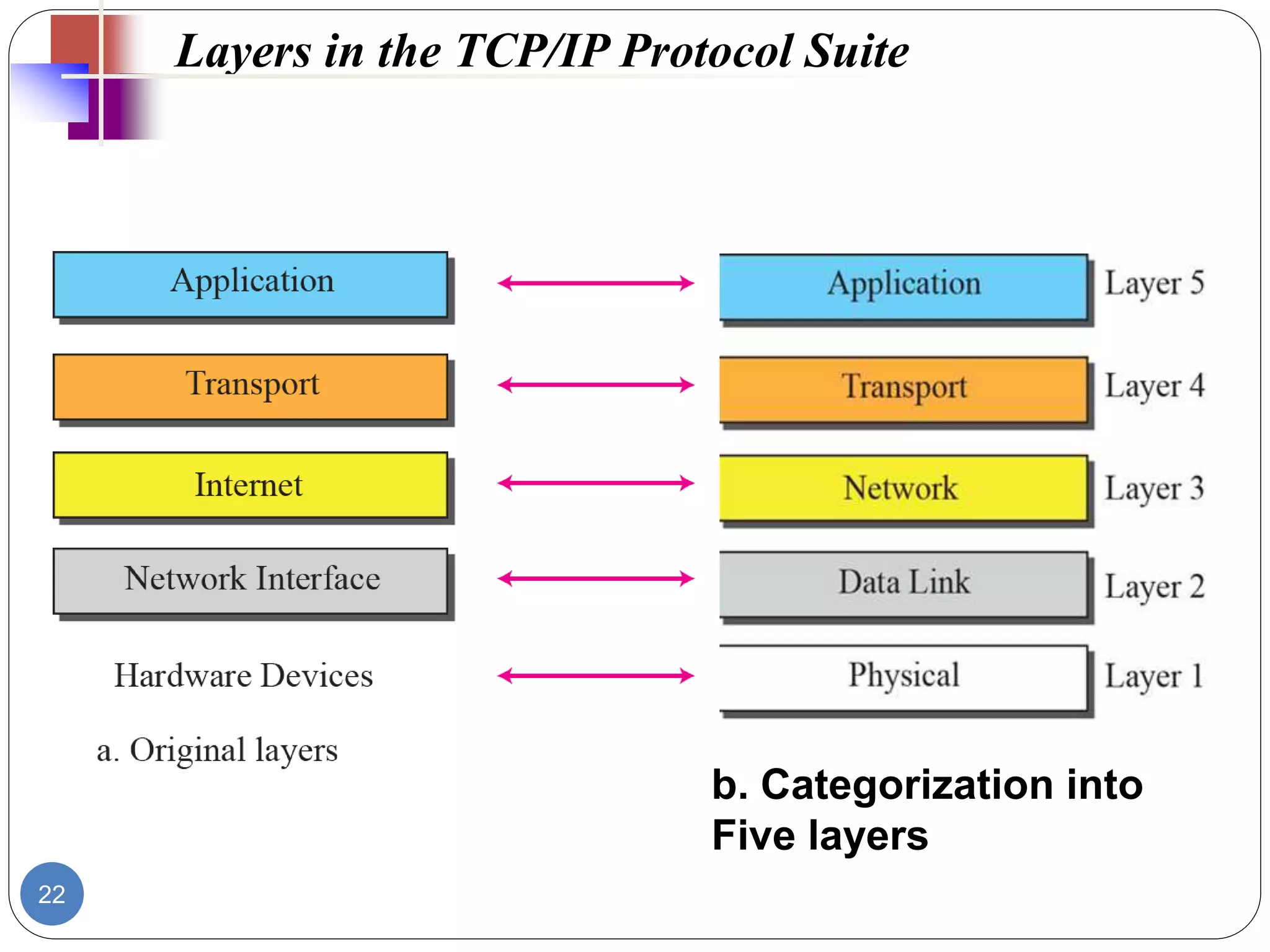
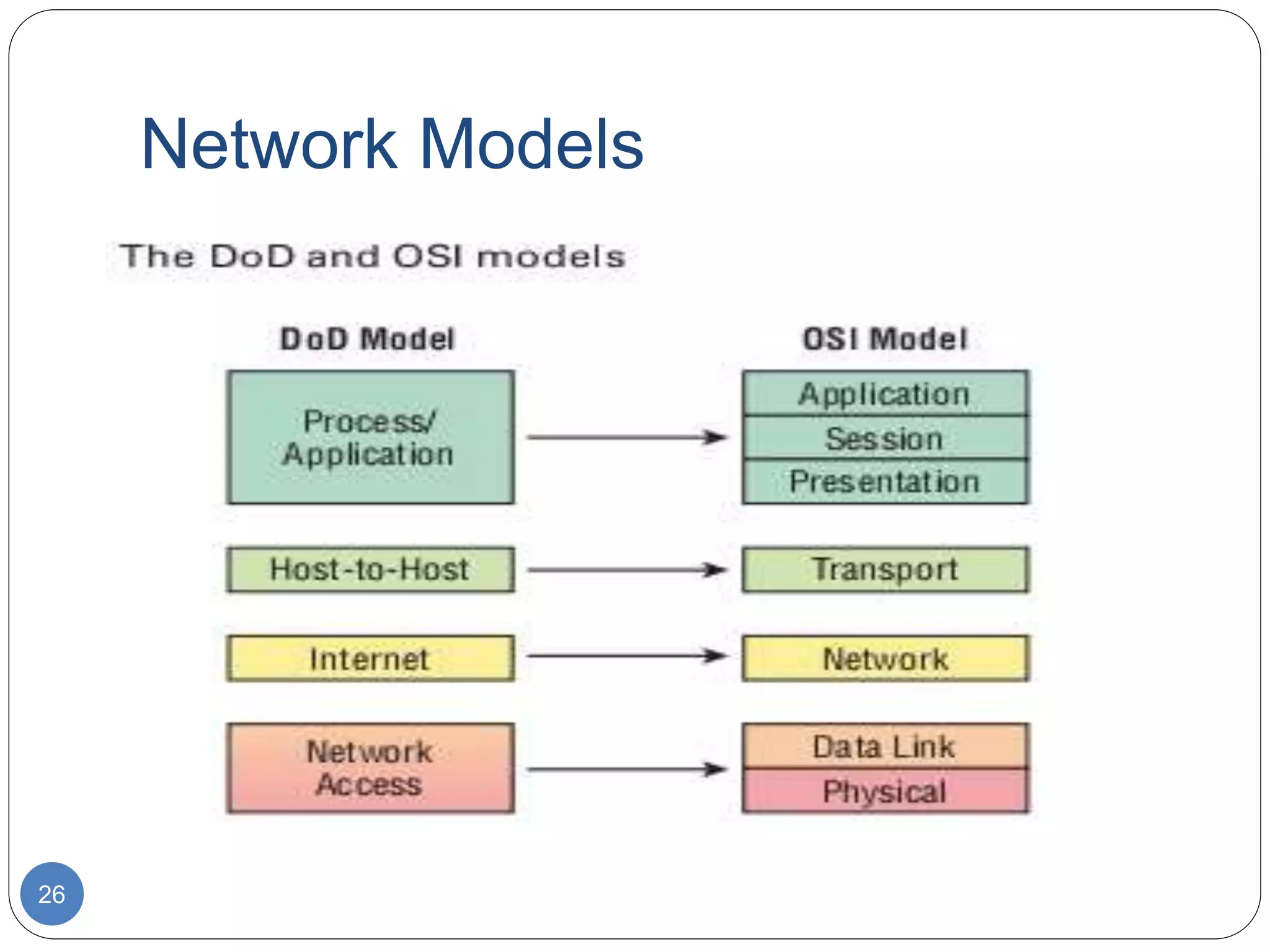
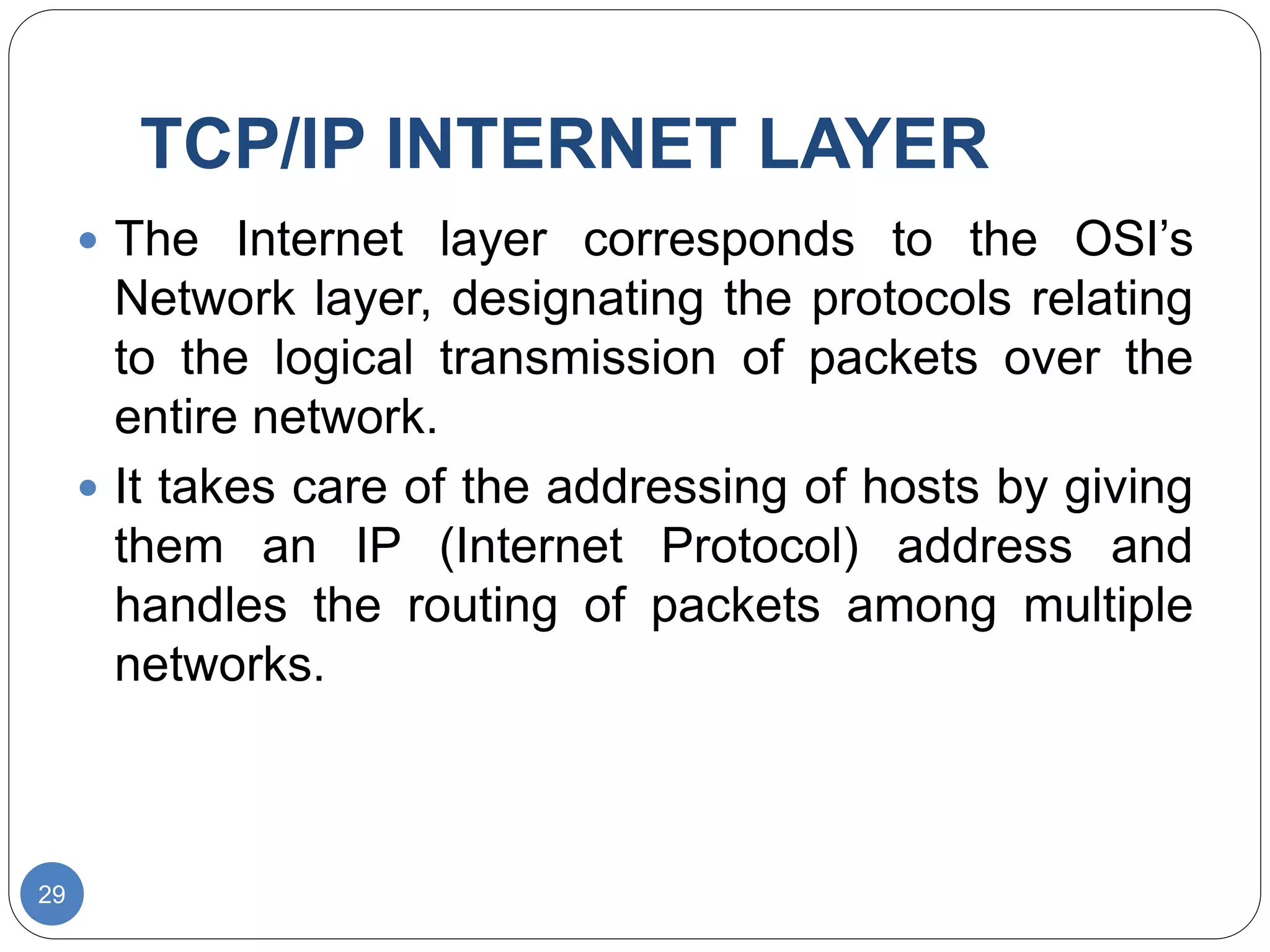
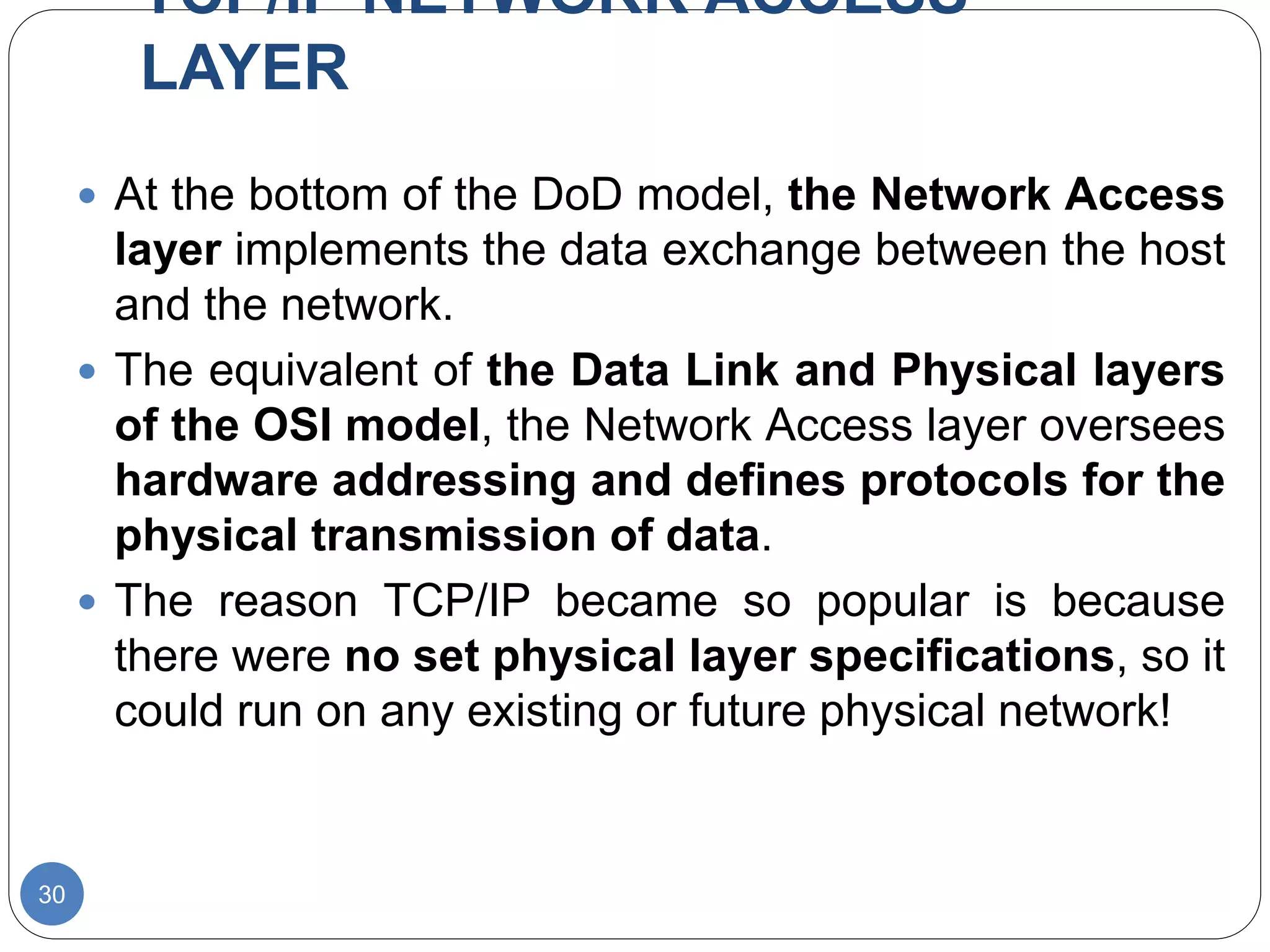
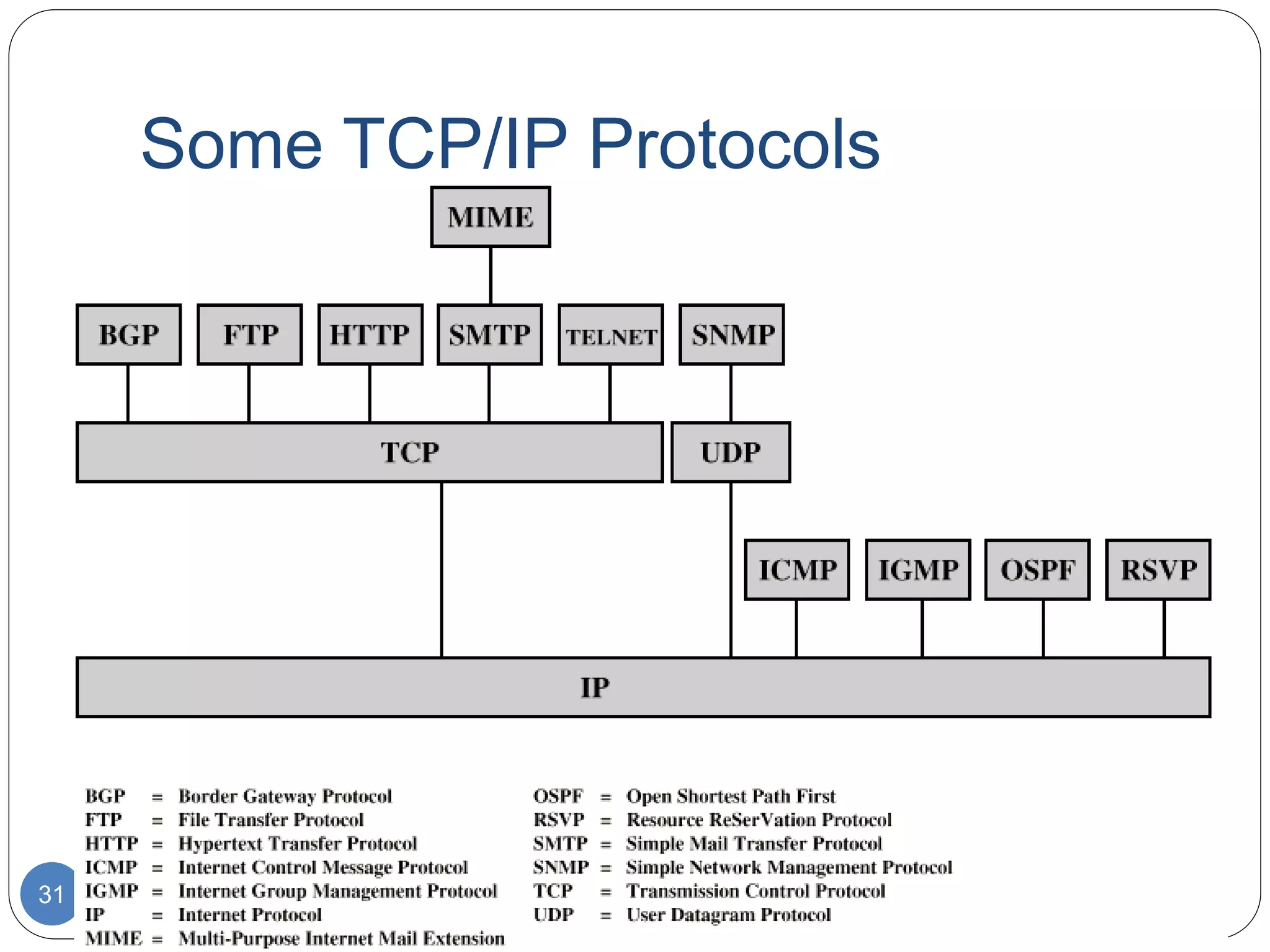
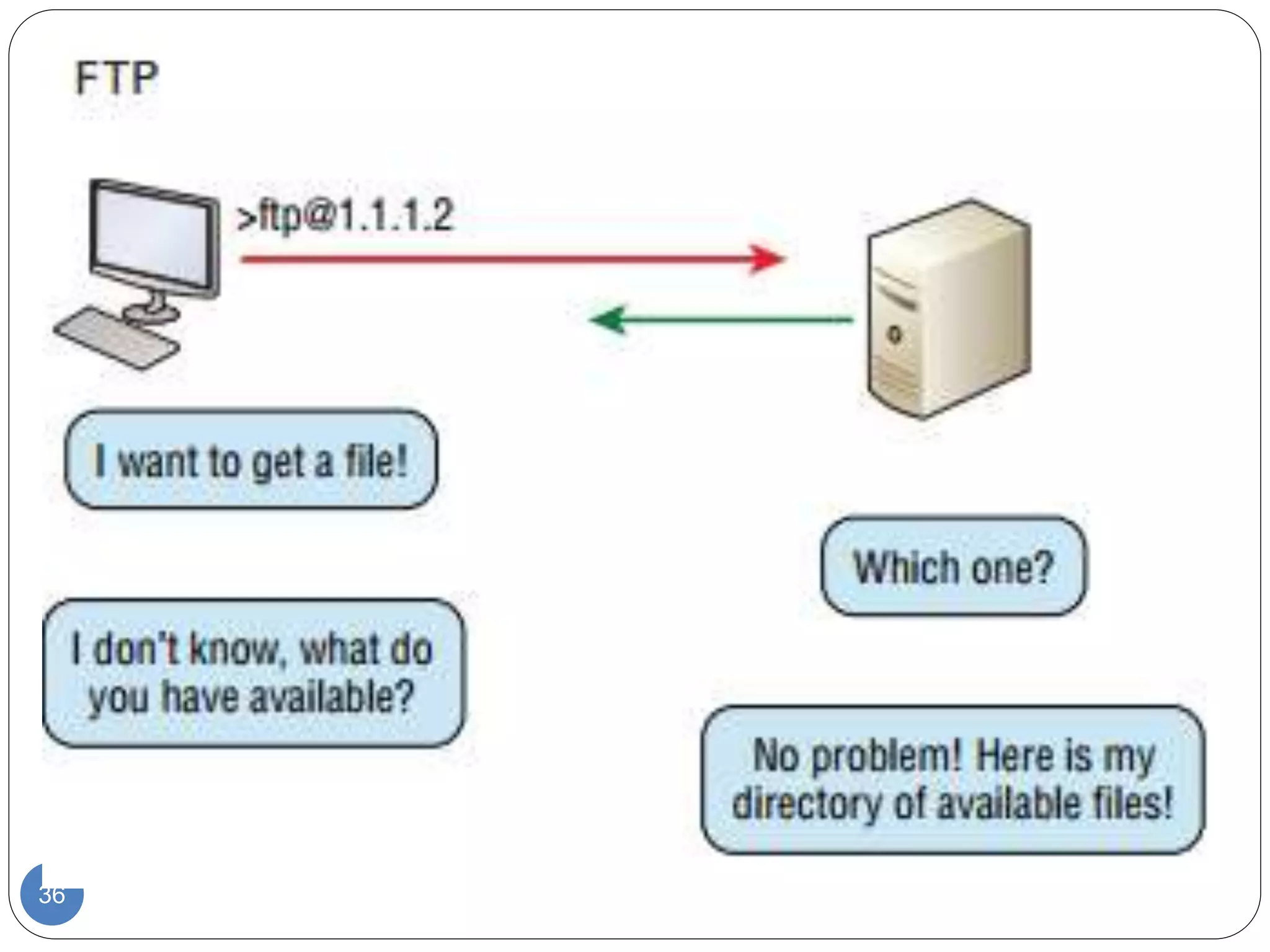
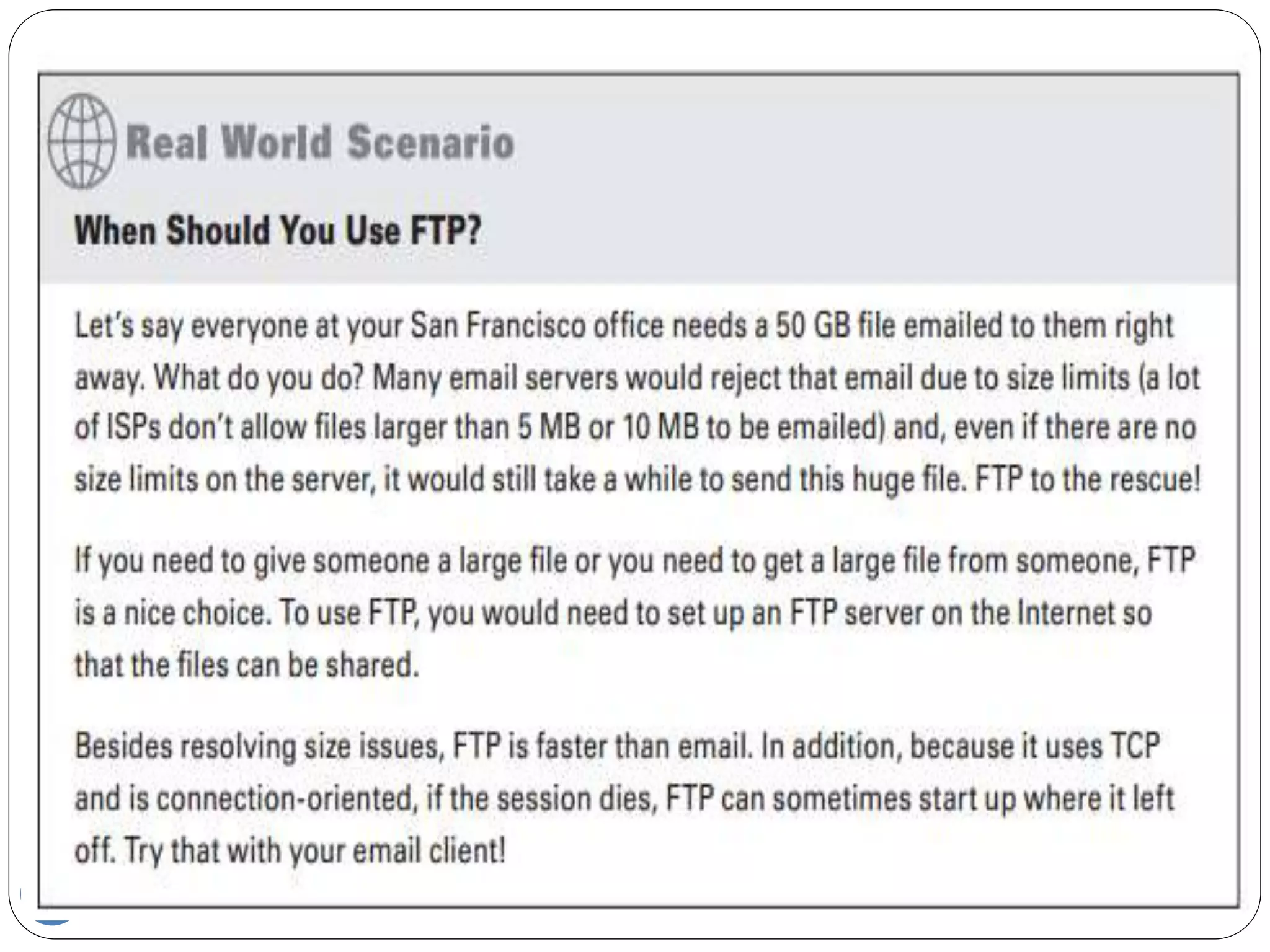
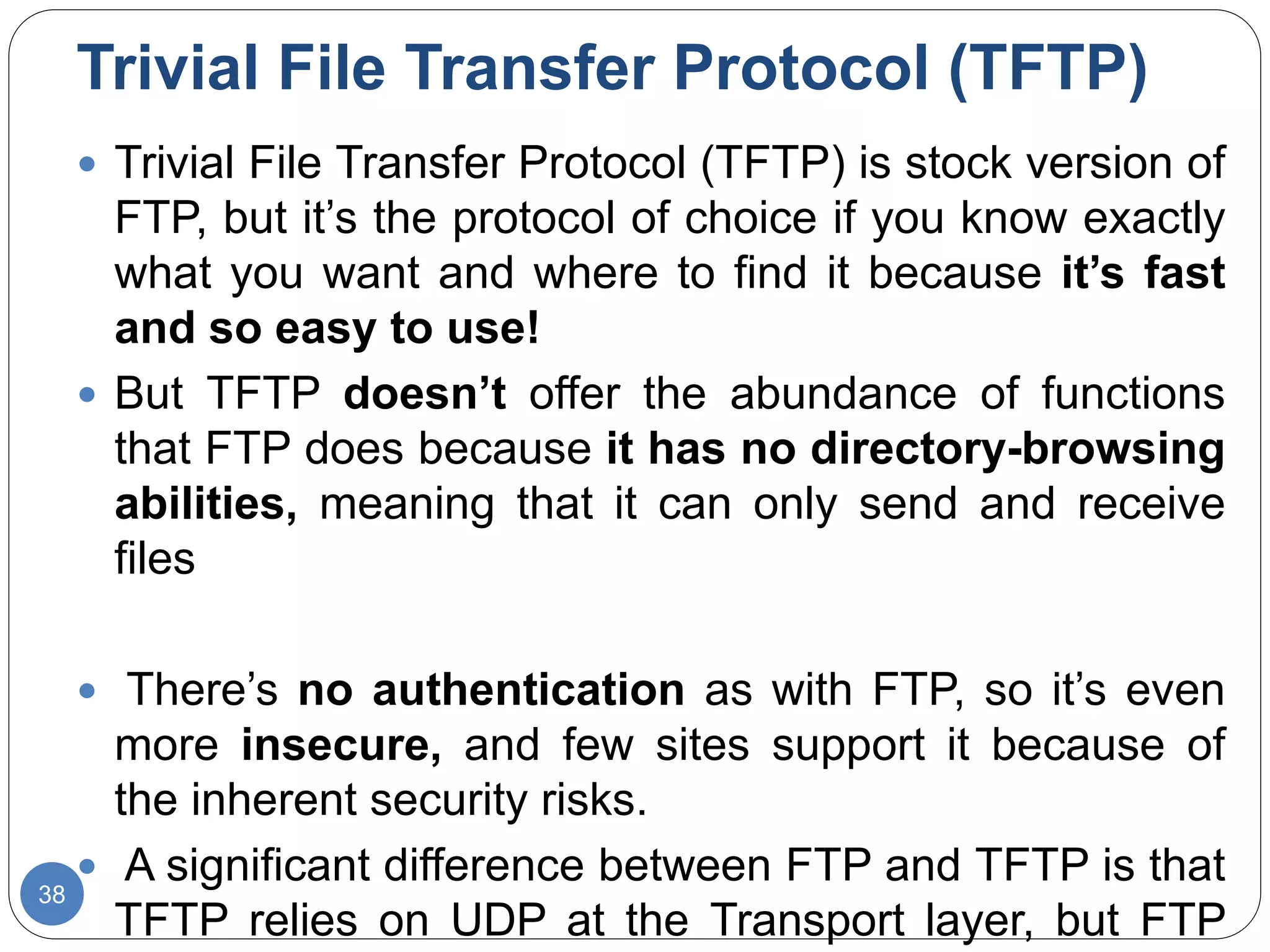
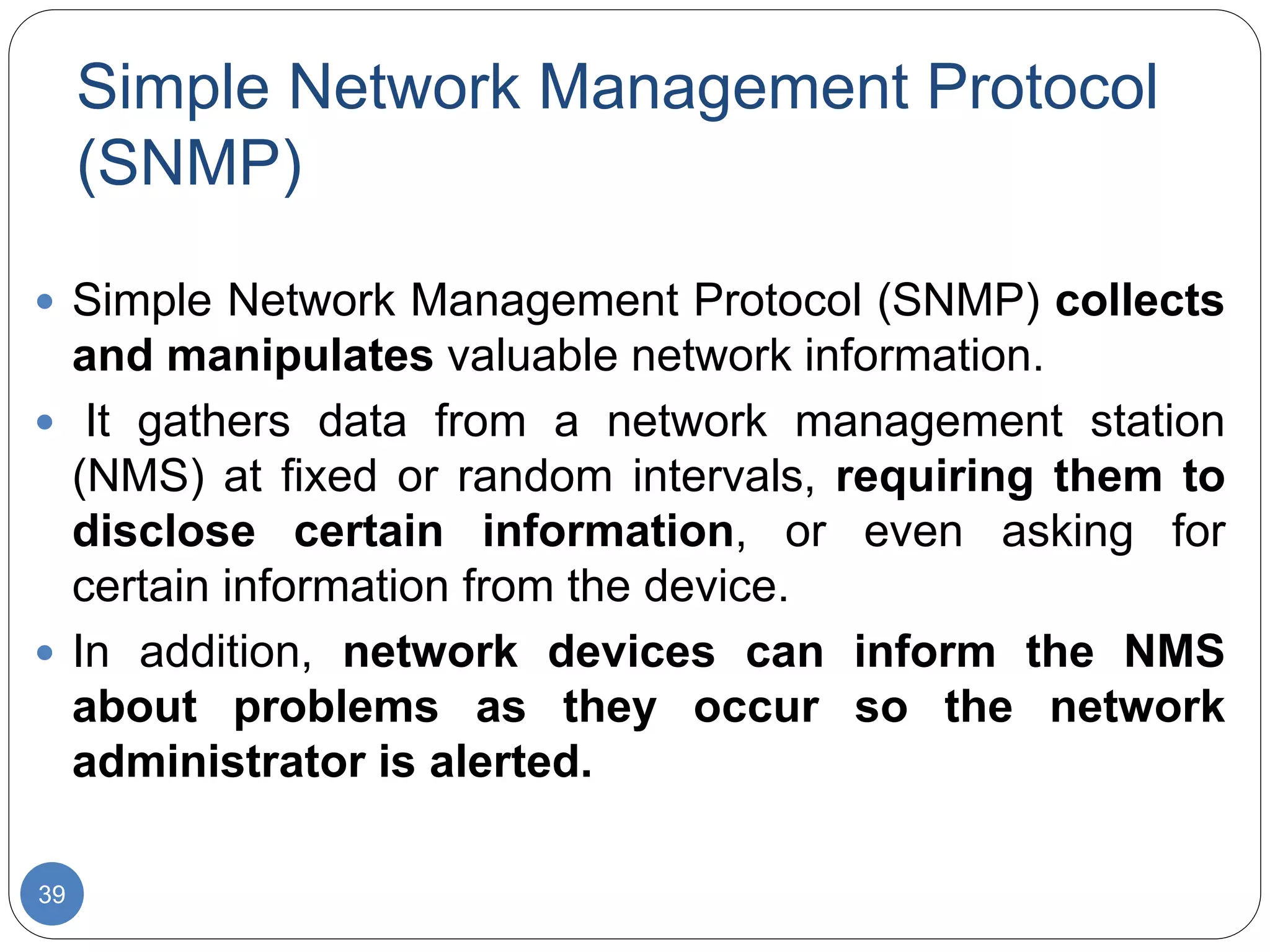
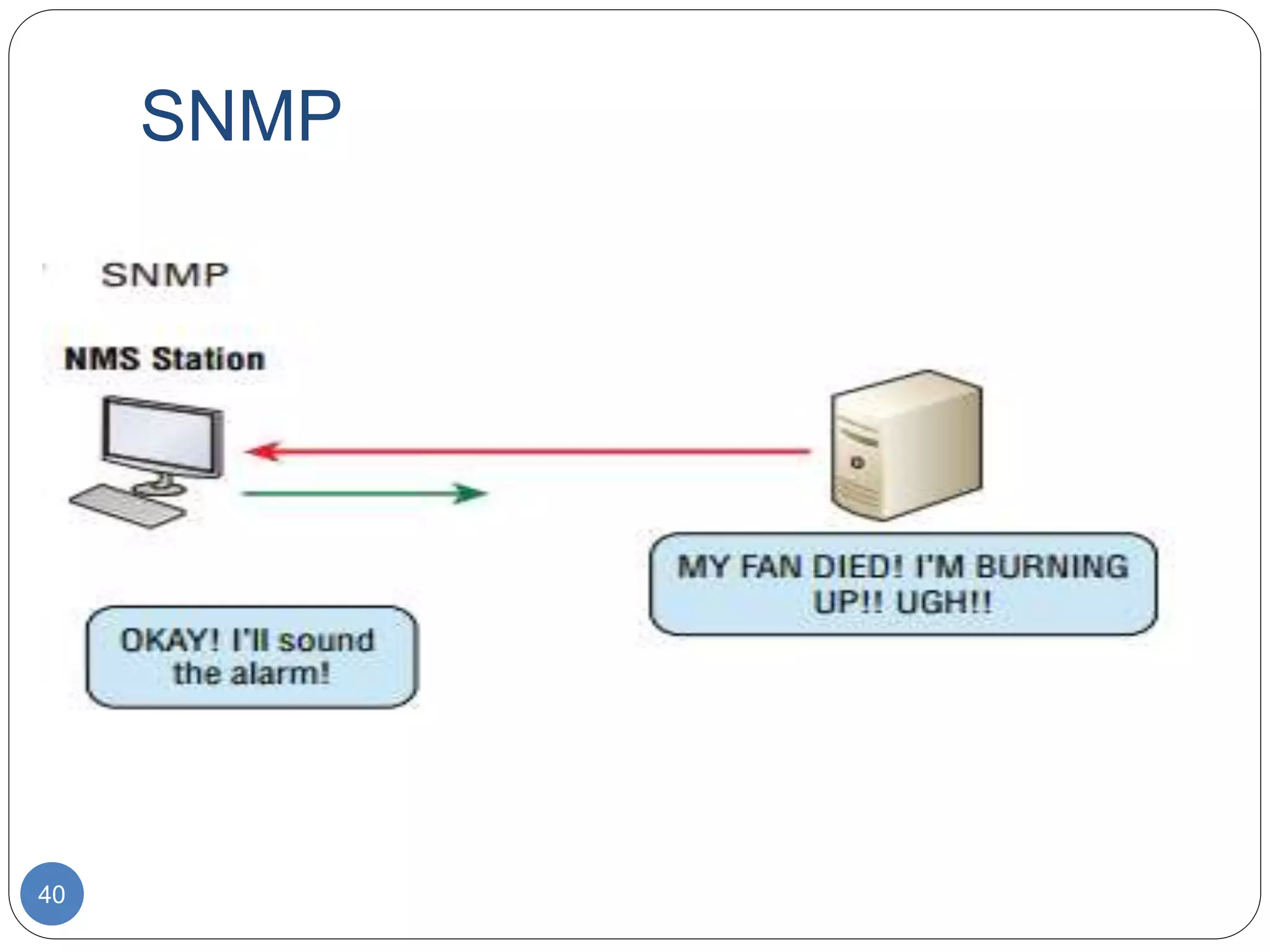
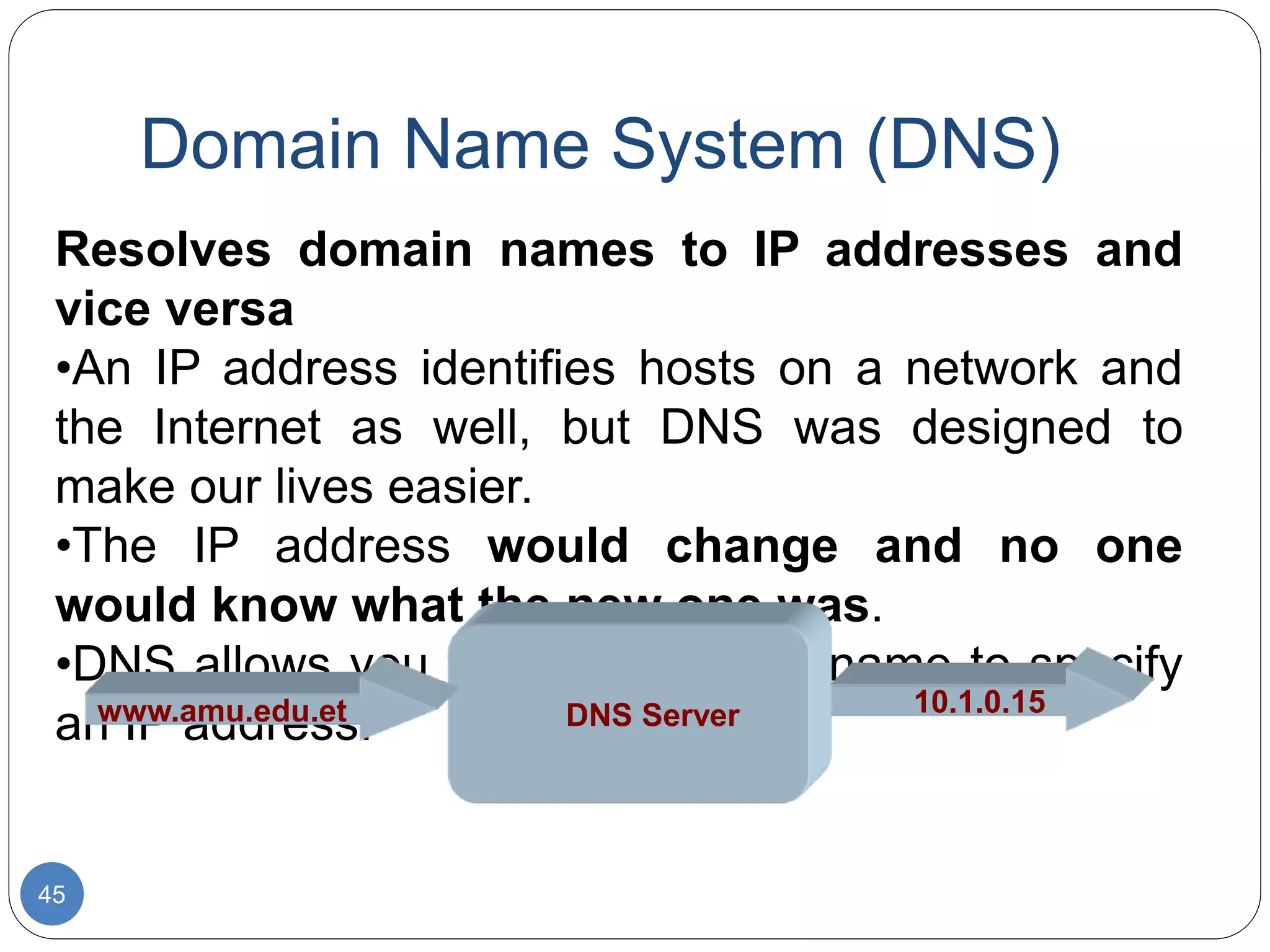
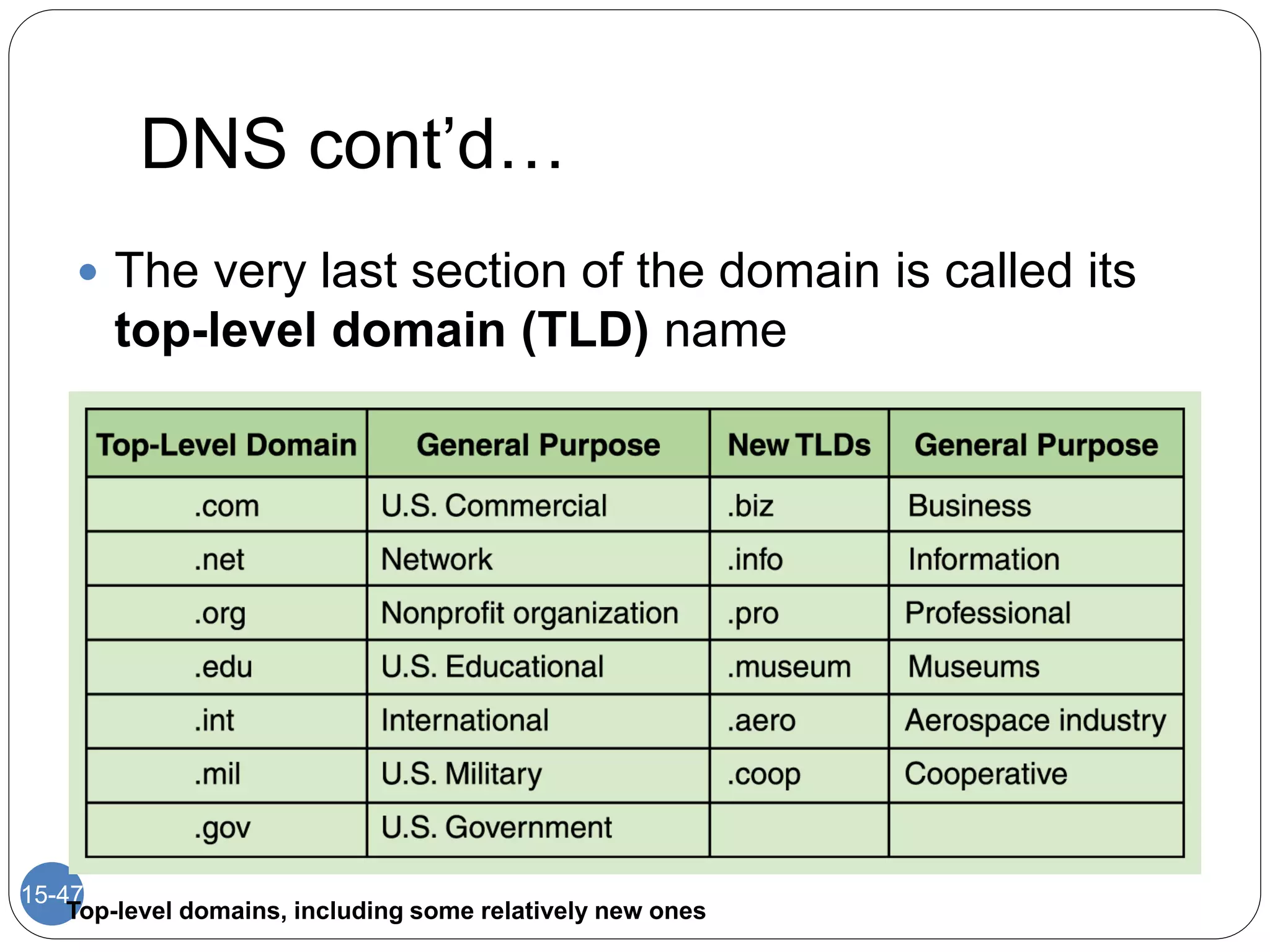
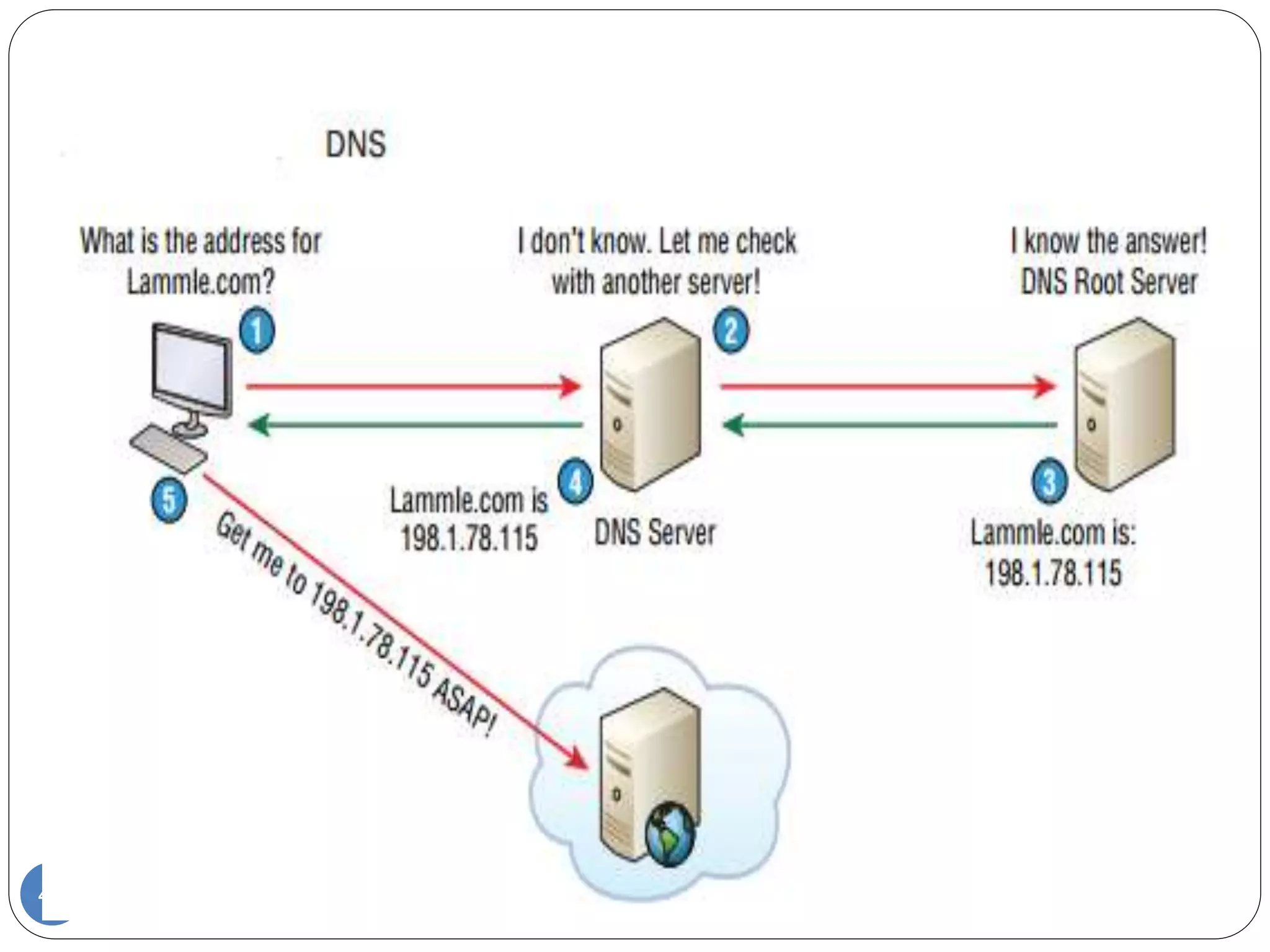
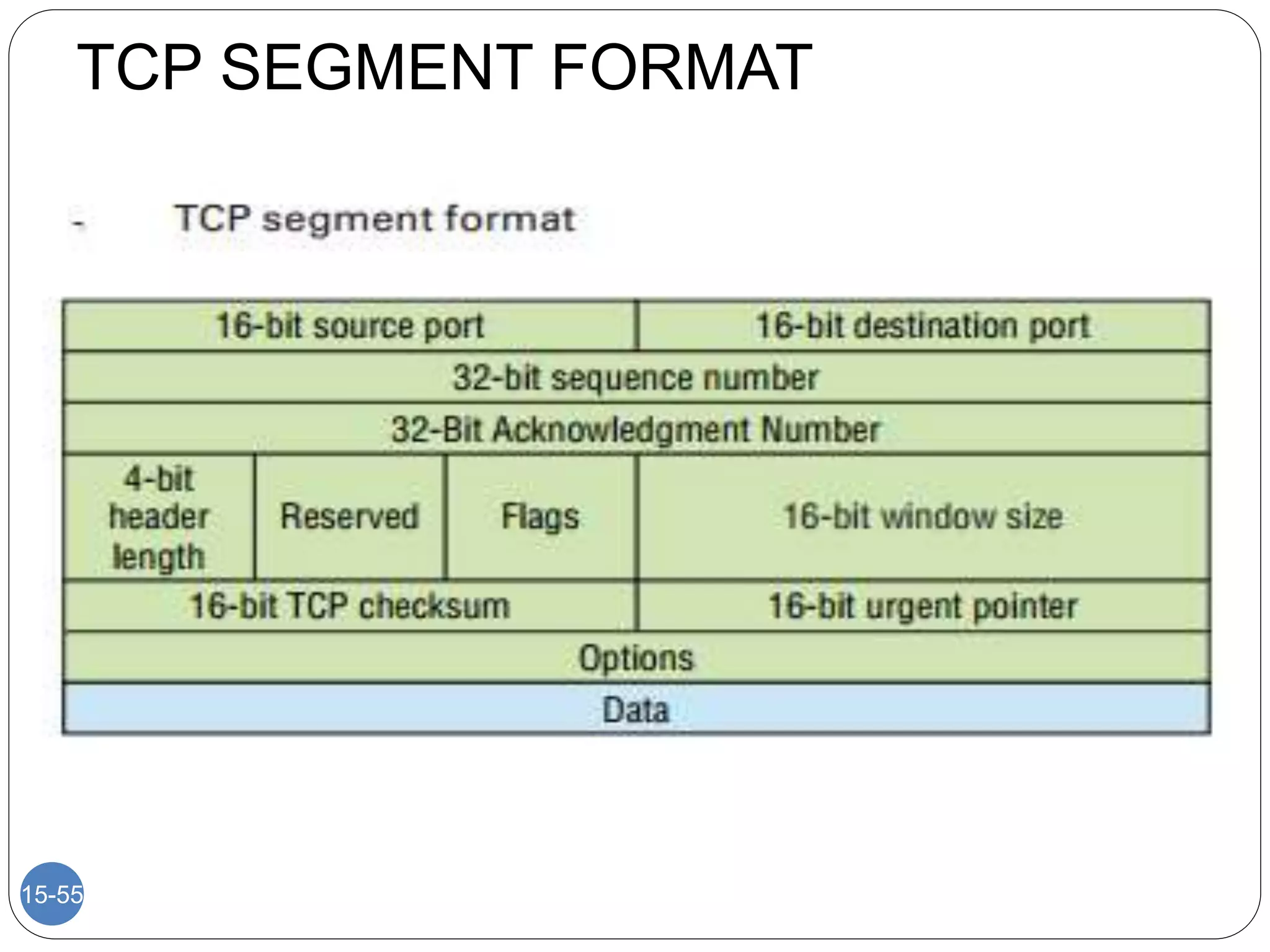
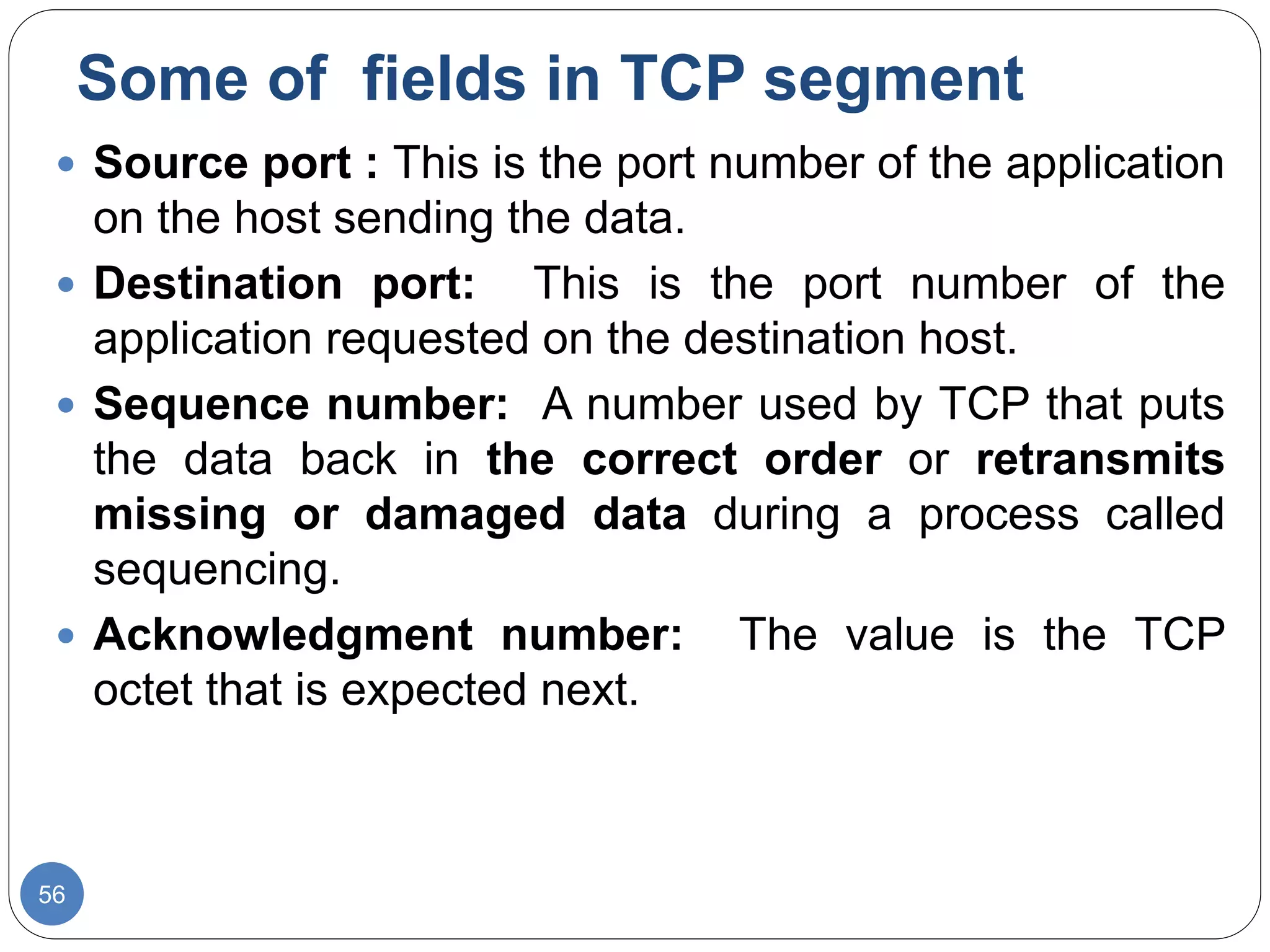
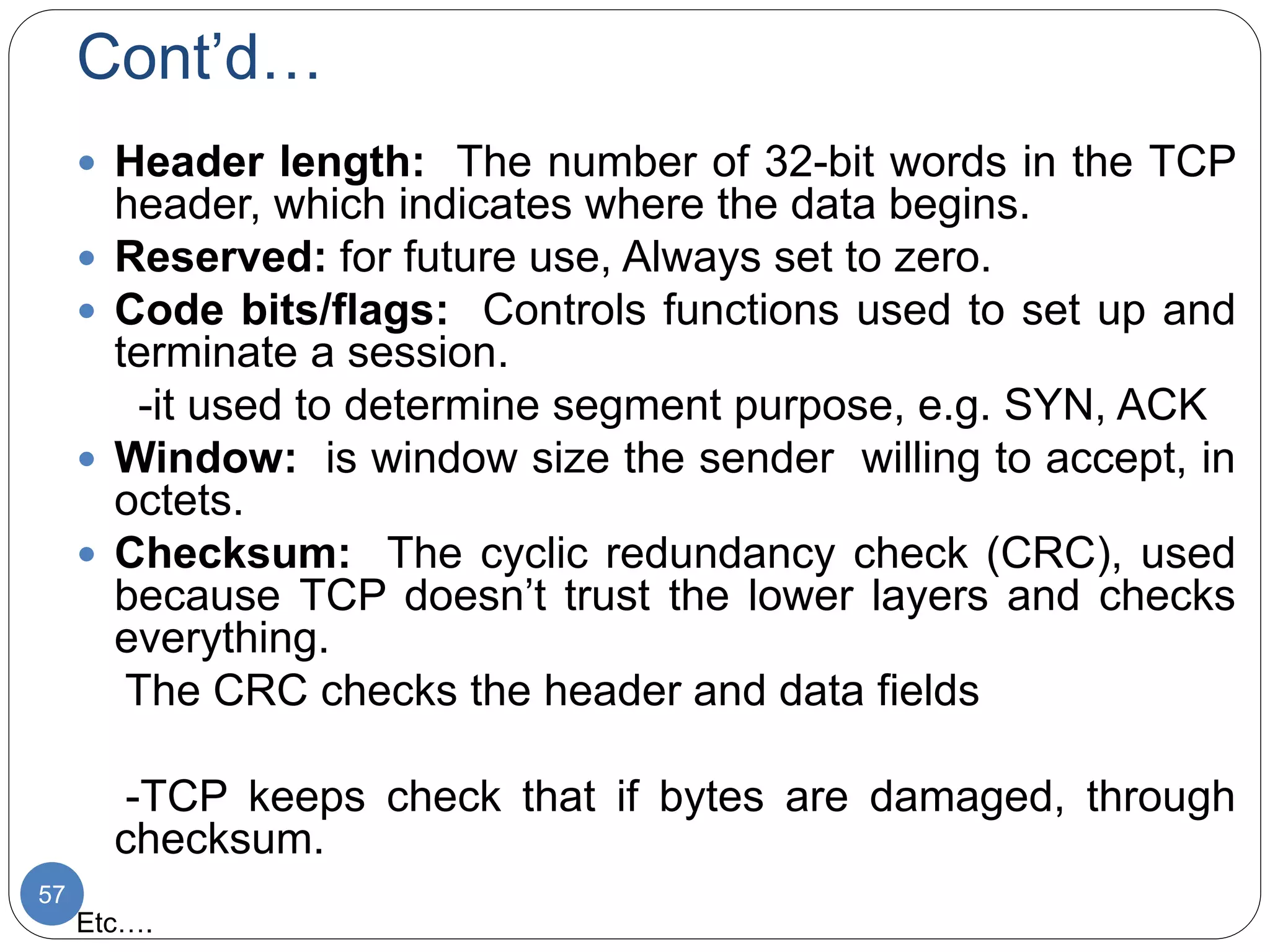
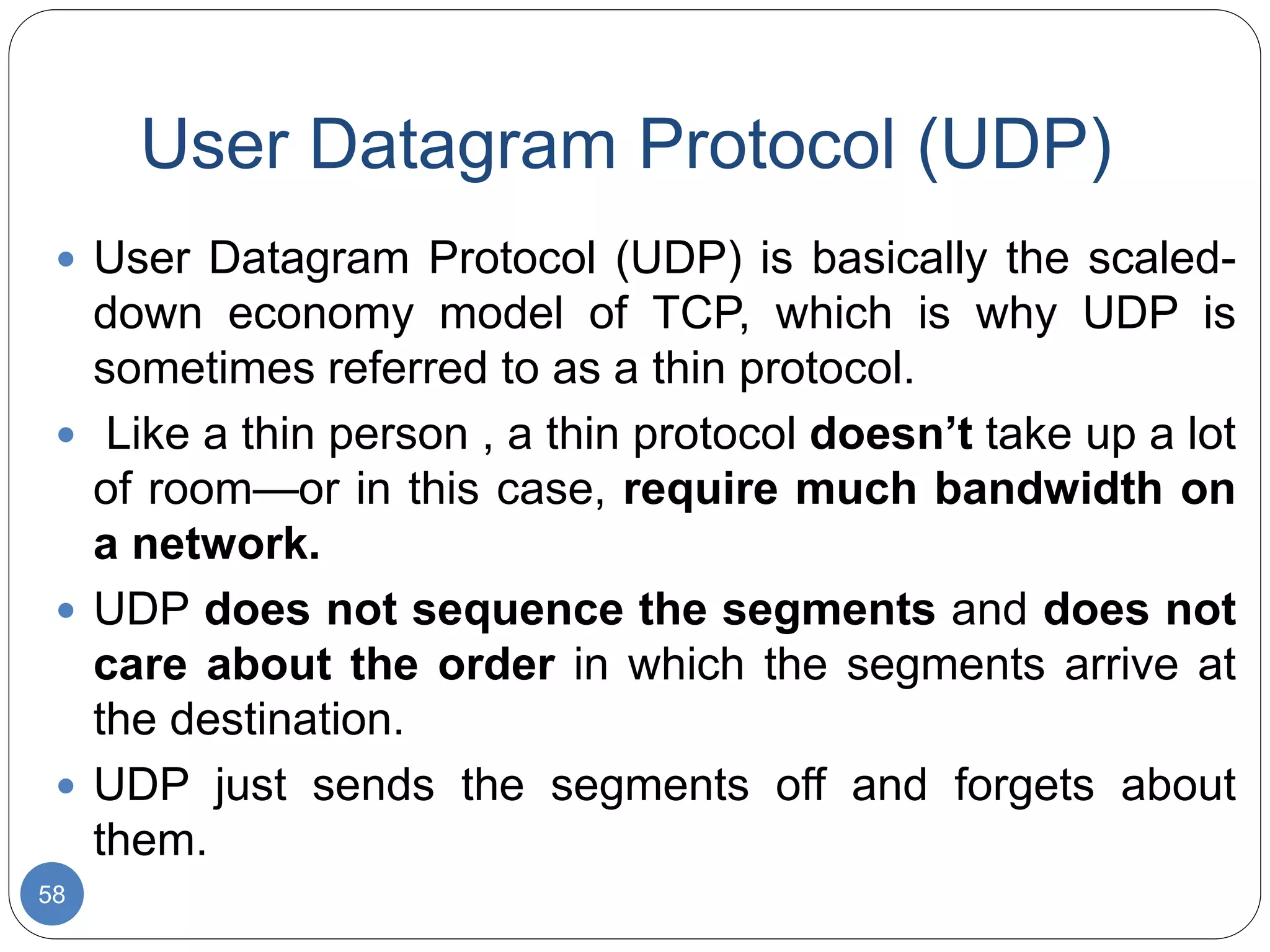
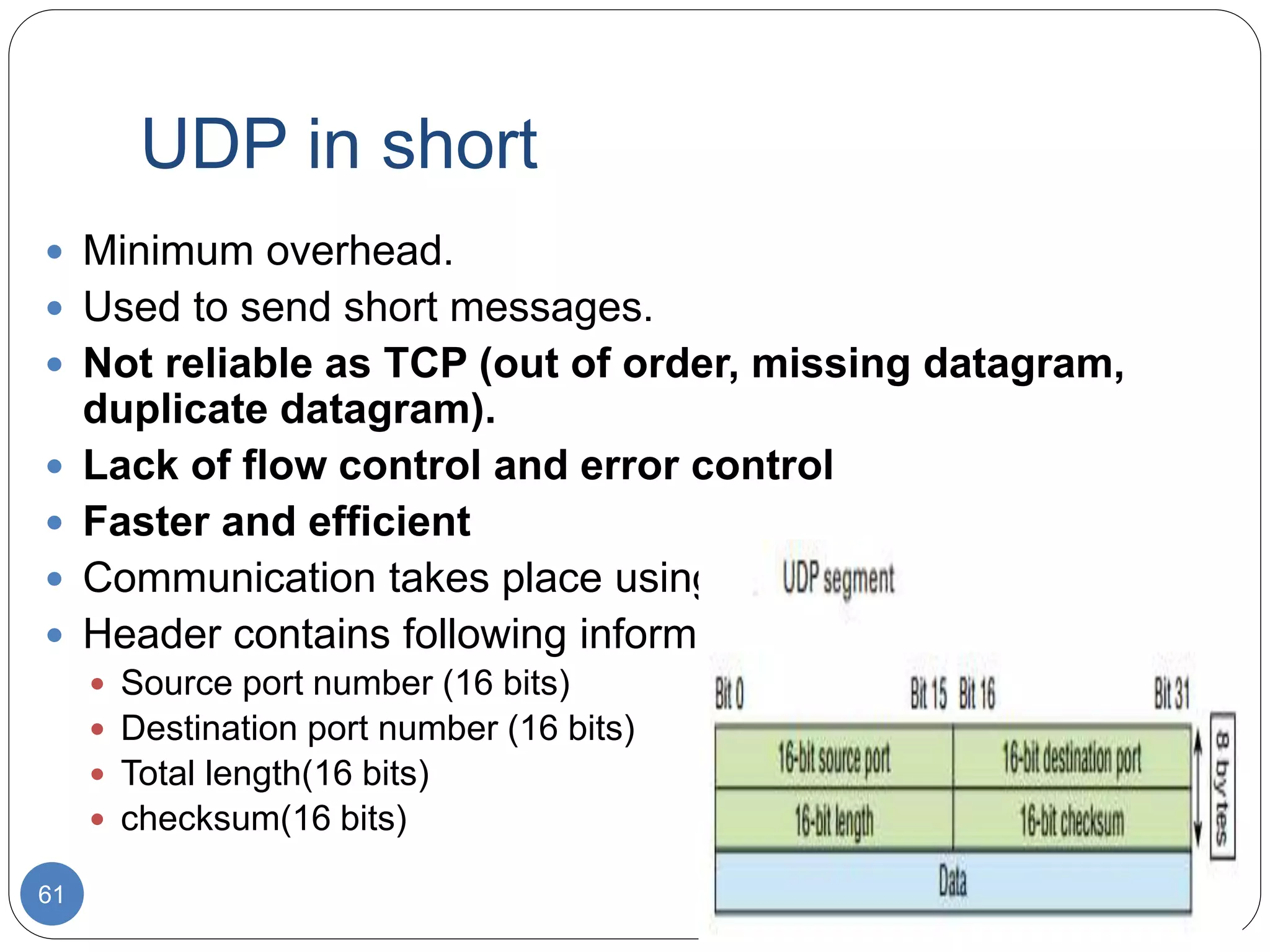
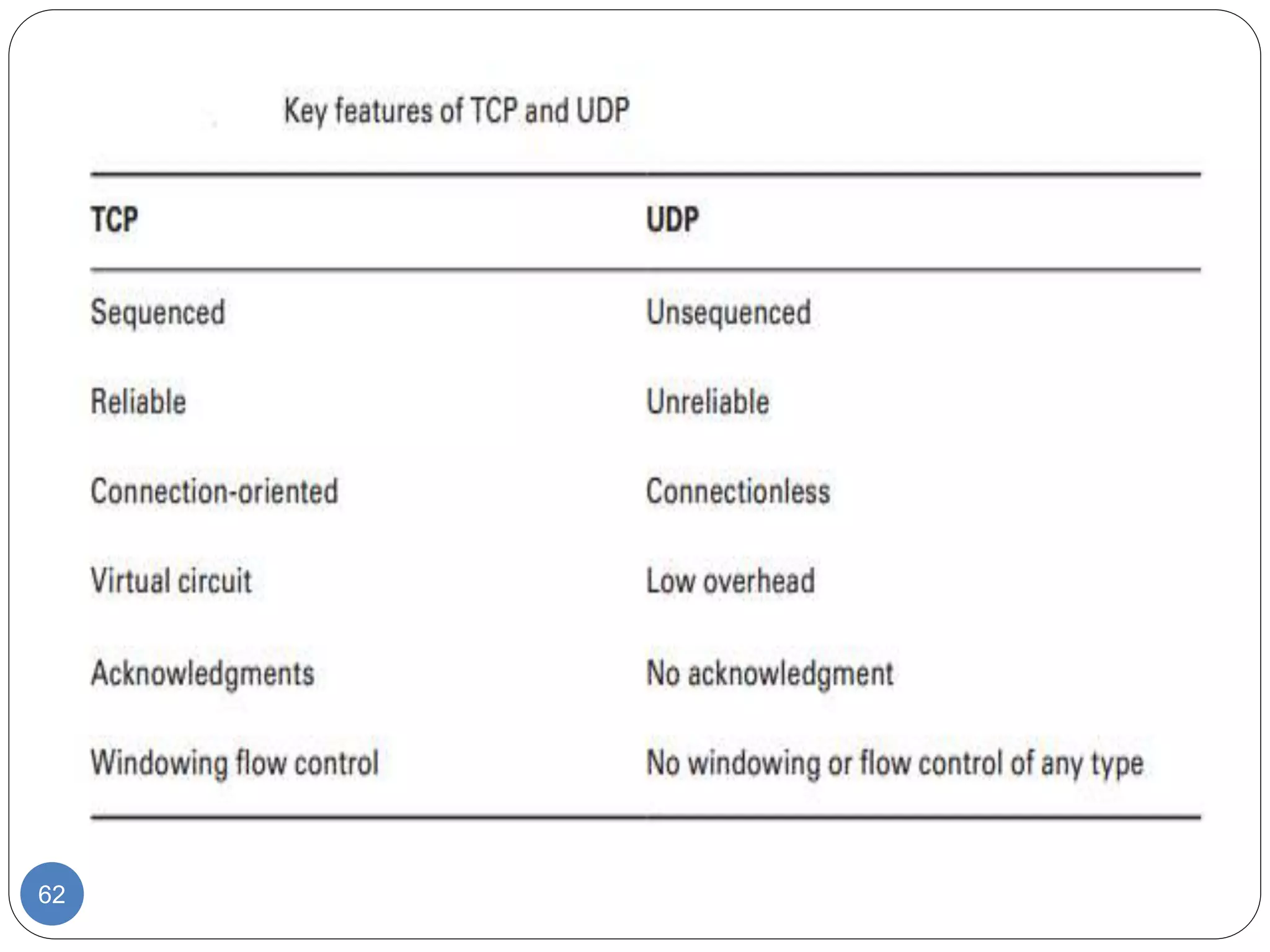
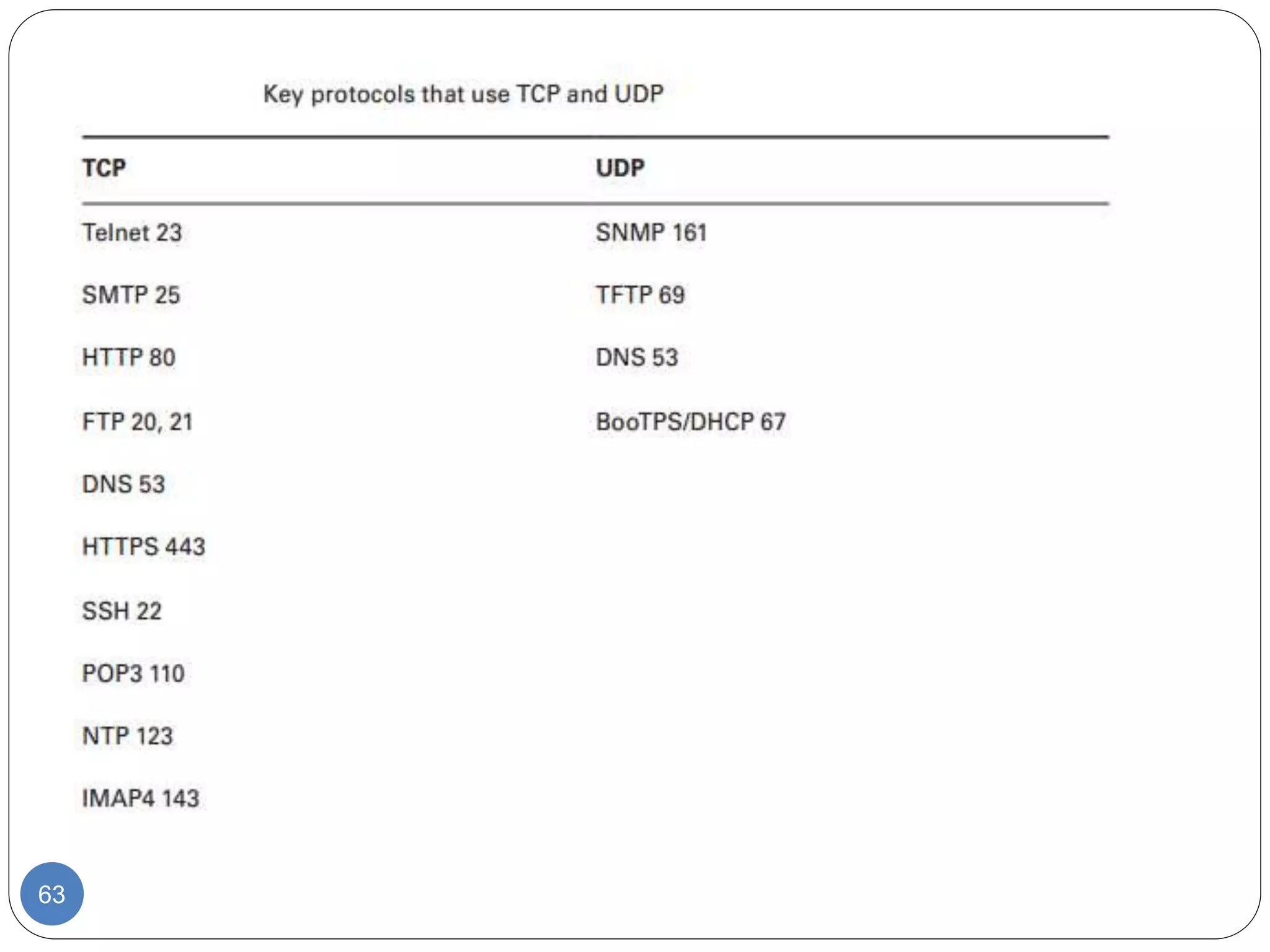
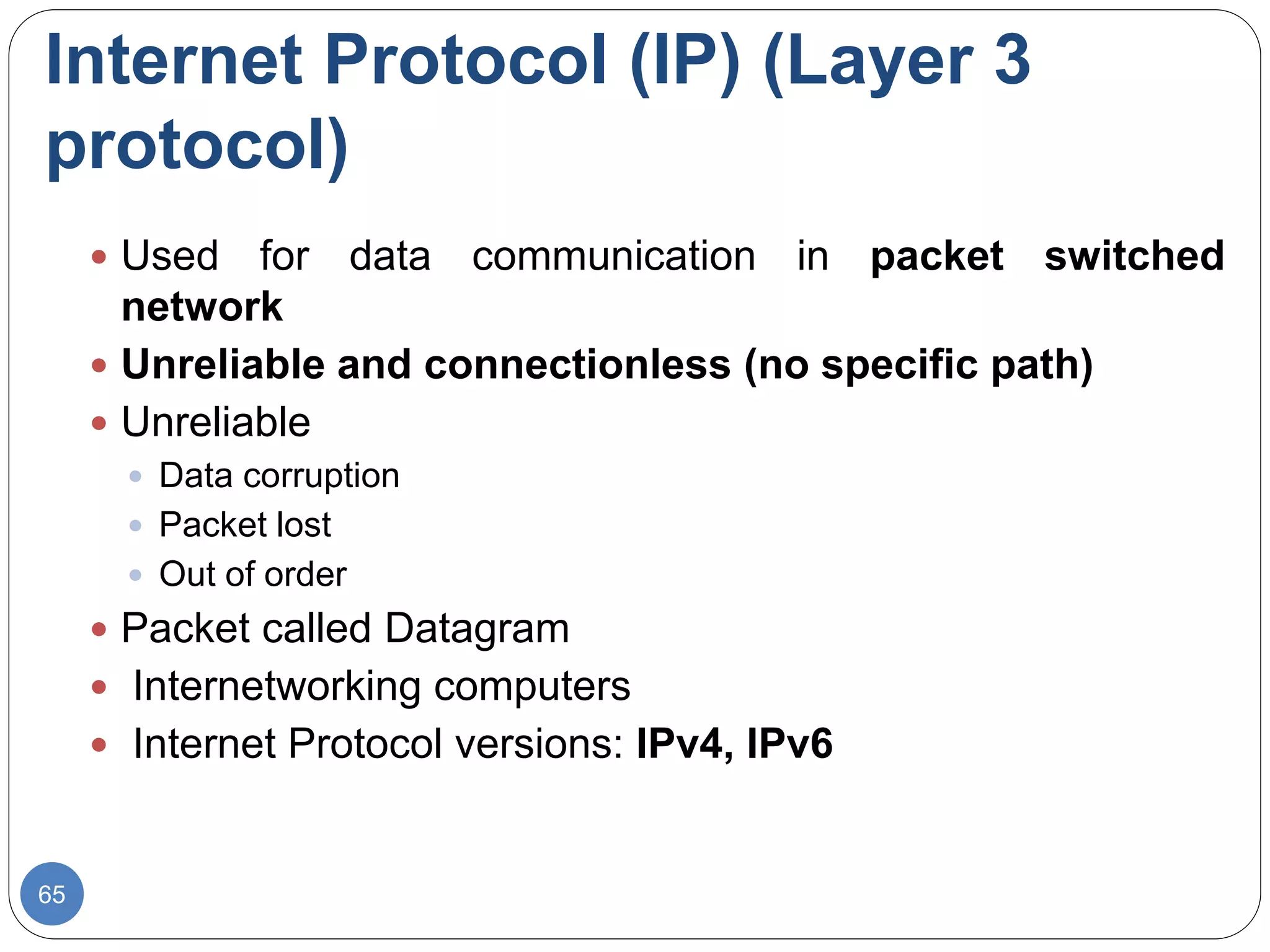
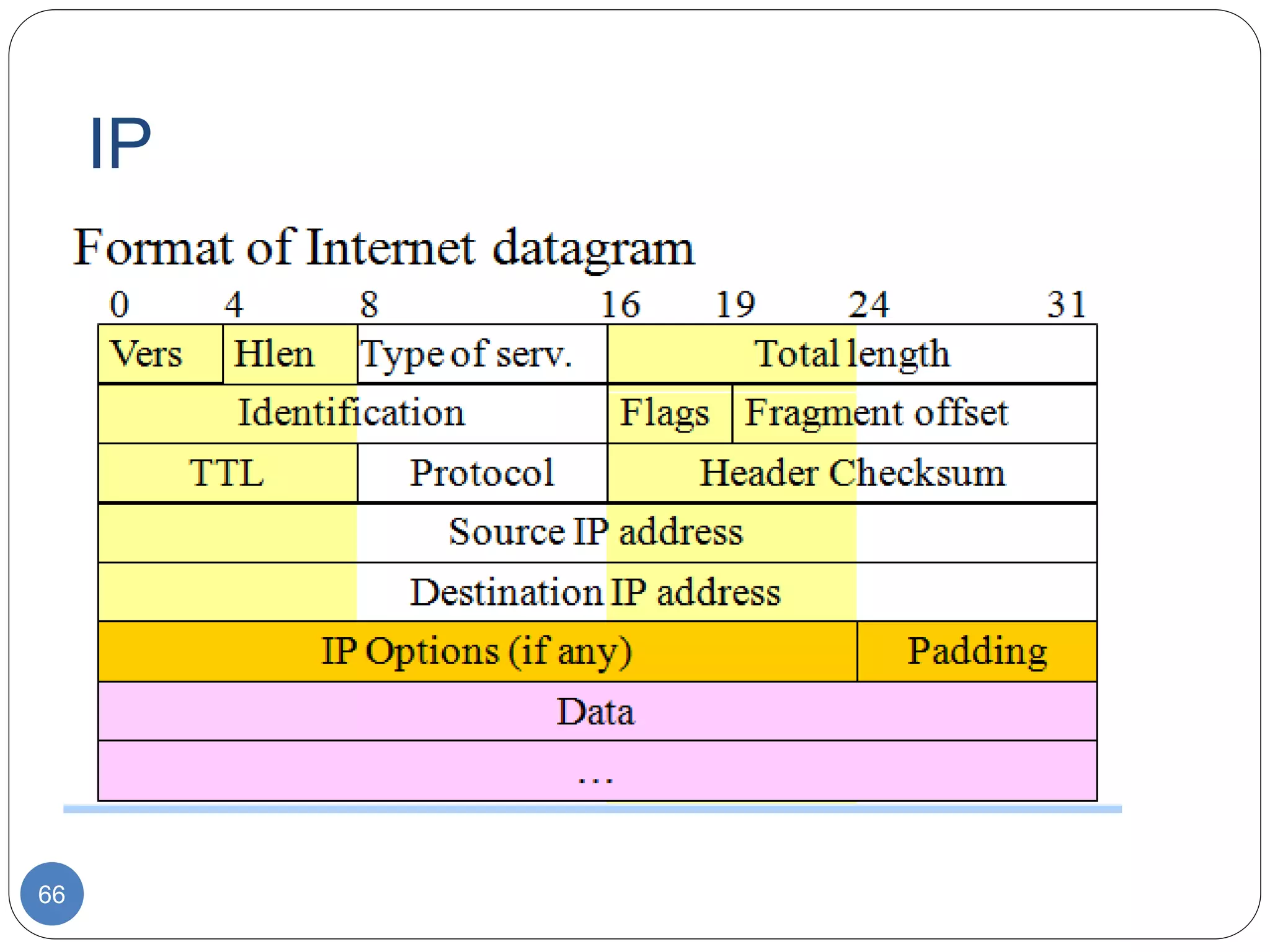
The document discusses network models and compares the OSI model and TCP/IP model. It provides details on the layers of the OSI model including the 7 layers from physical to application layer. It describes the functions of each layer such as physical dealing with raw bit transmission, data link framing bits into frames, network routing packets, transport ensuring reliable data delivery, session controlling connections, presentation translating between systems, and application providing user interfaces. It also summarizes the similarities and differences between the OSI and TCP/IP models.