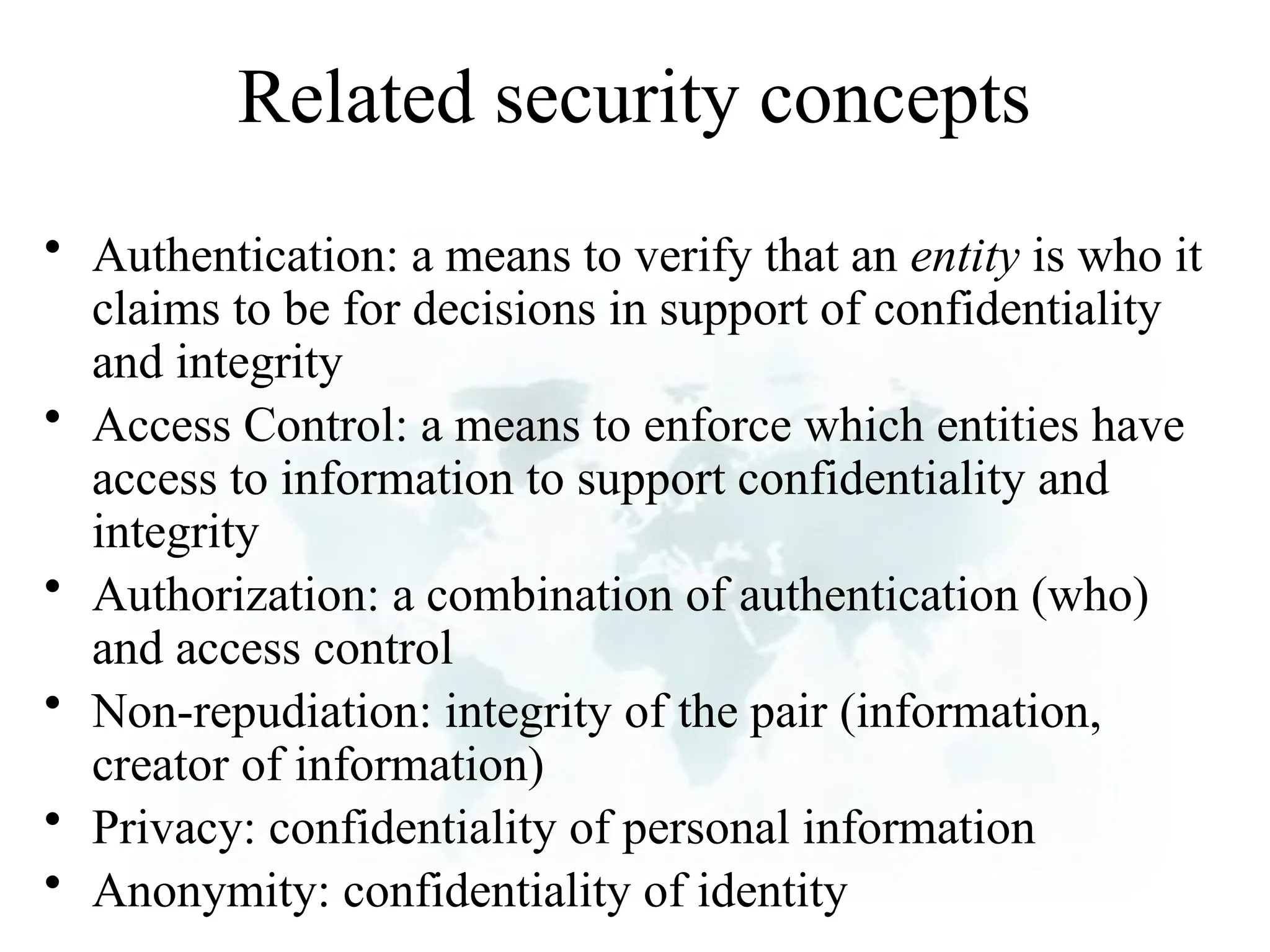
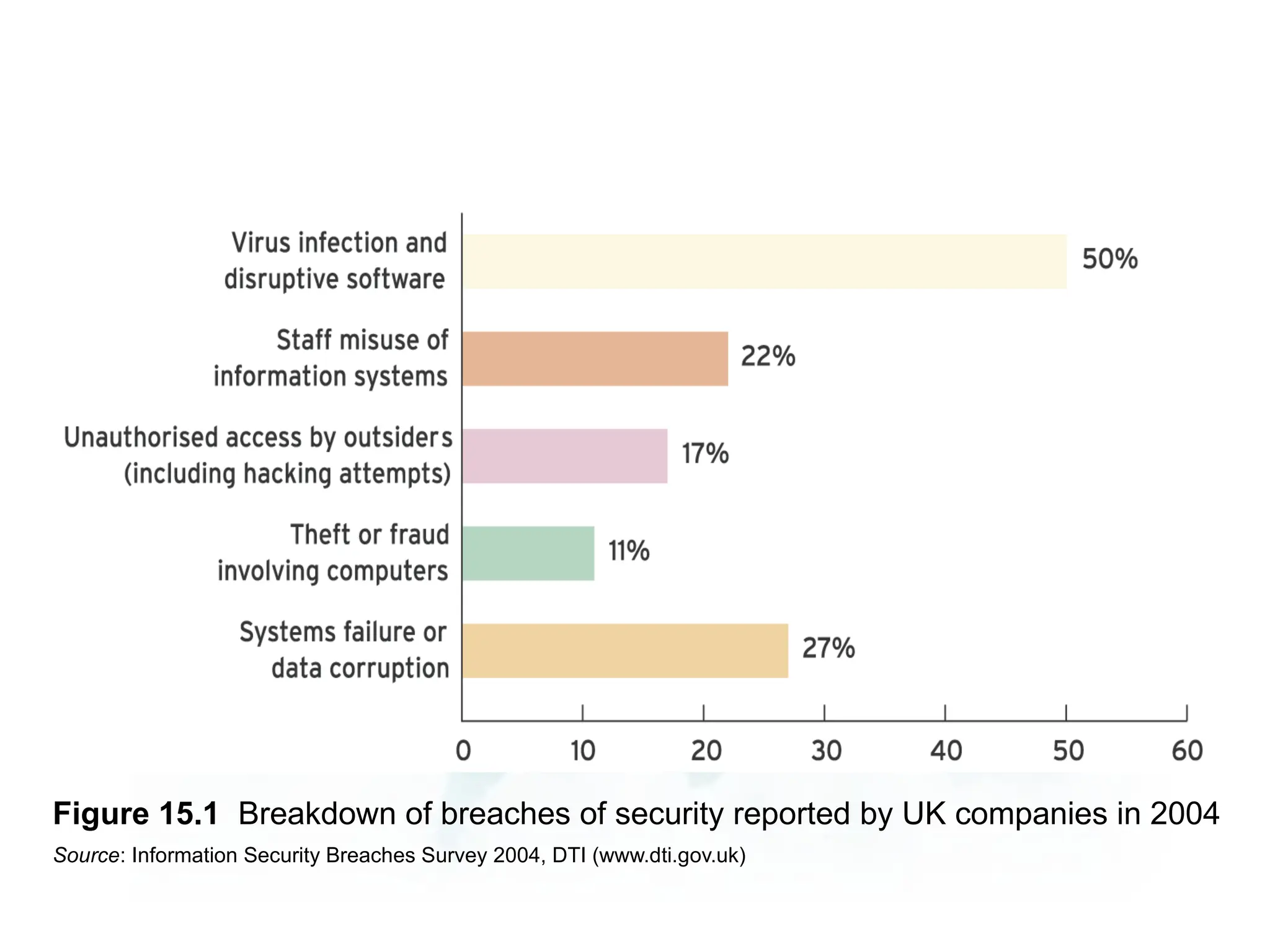
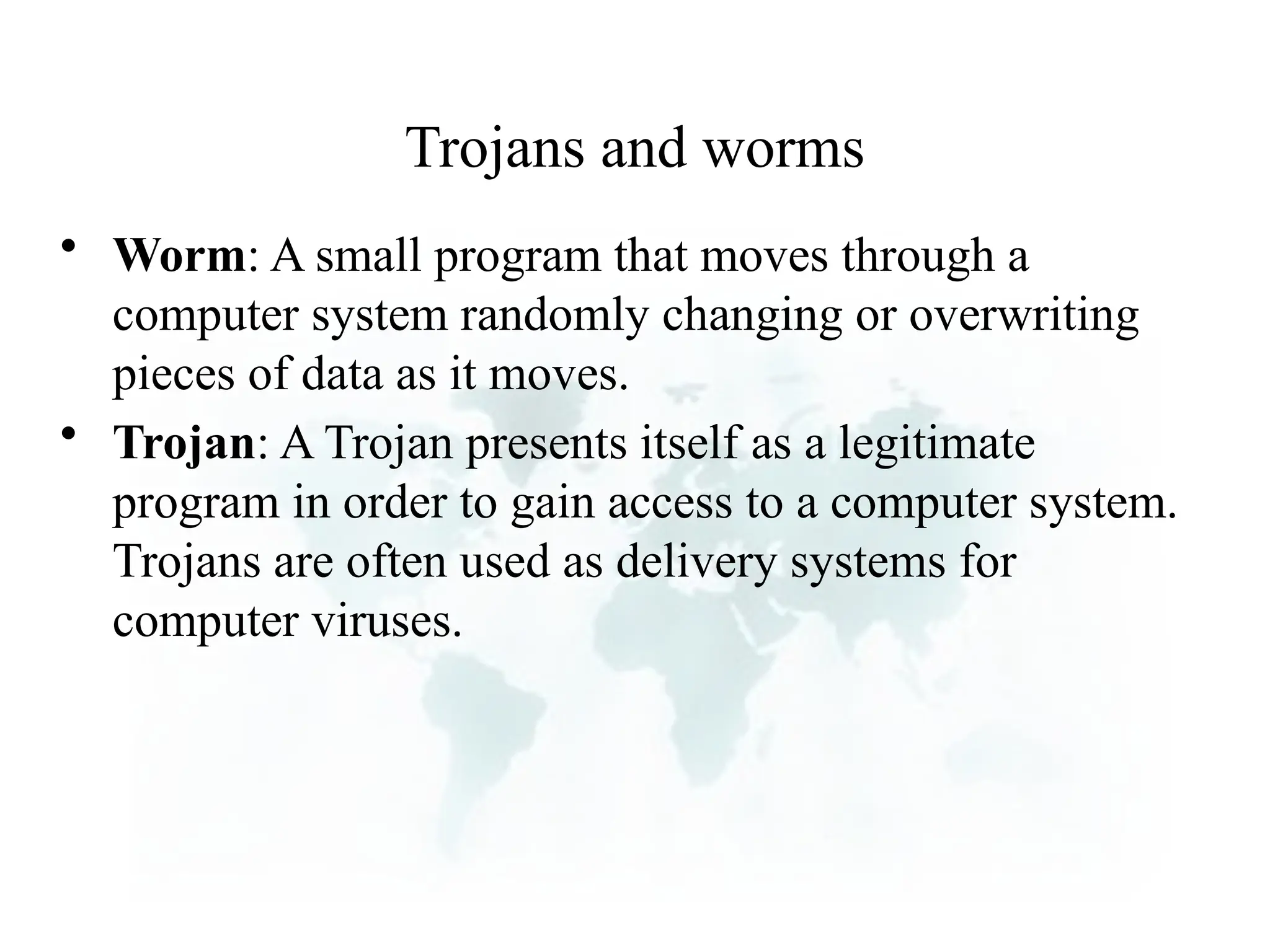
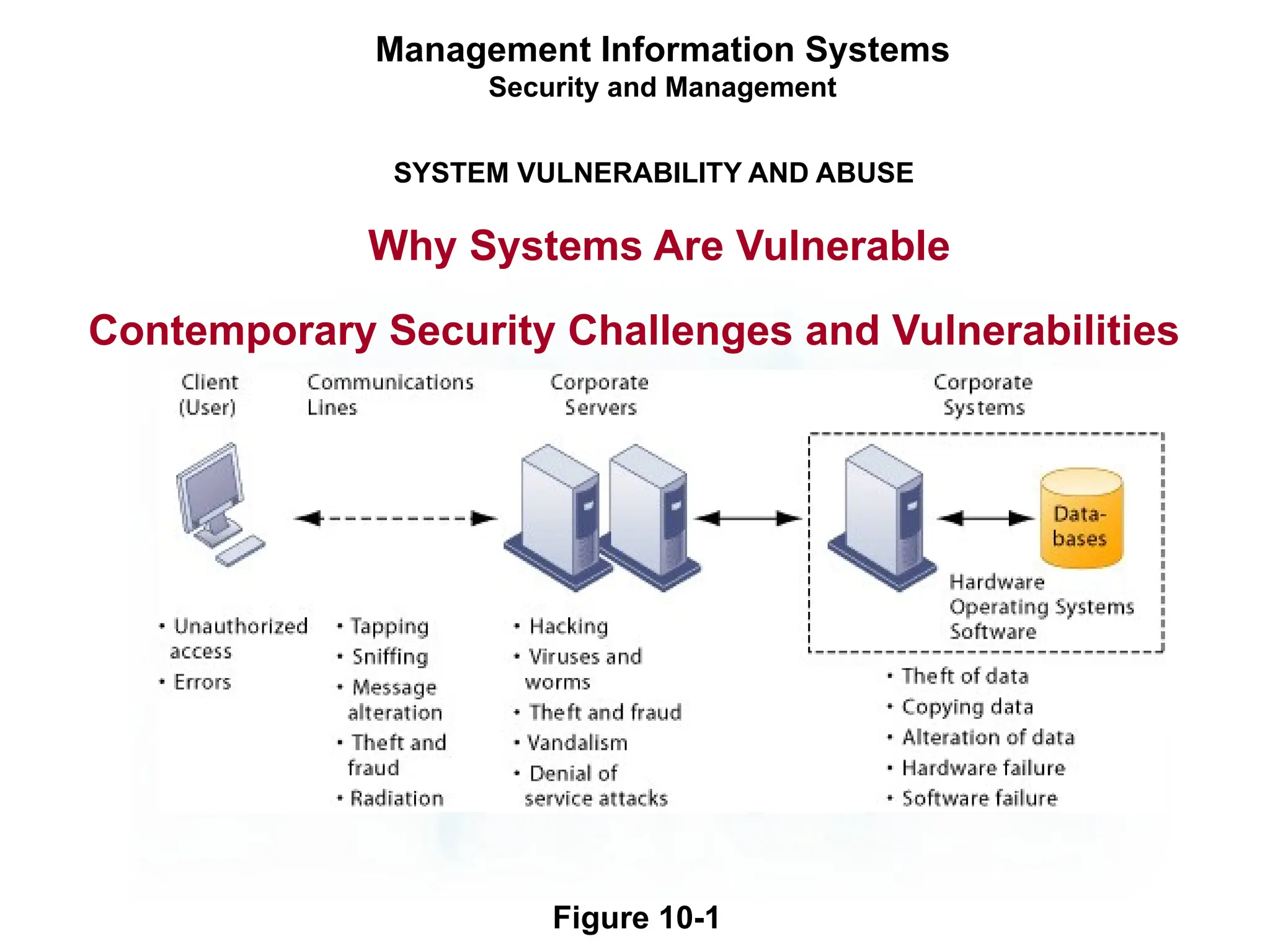
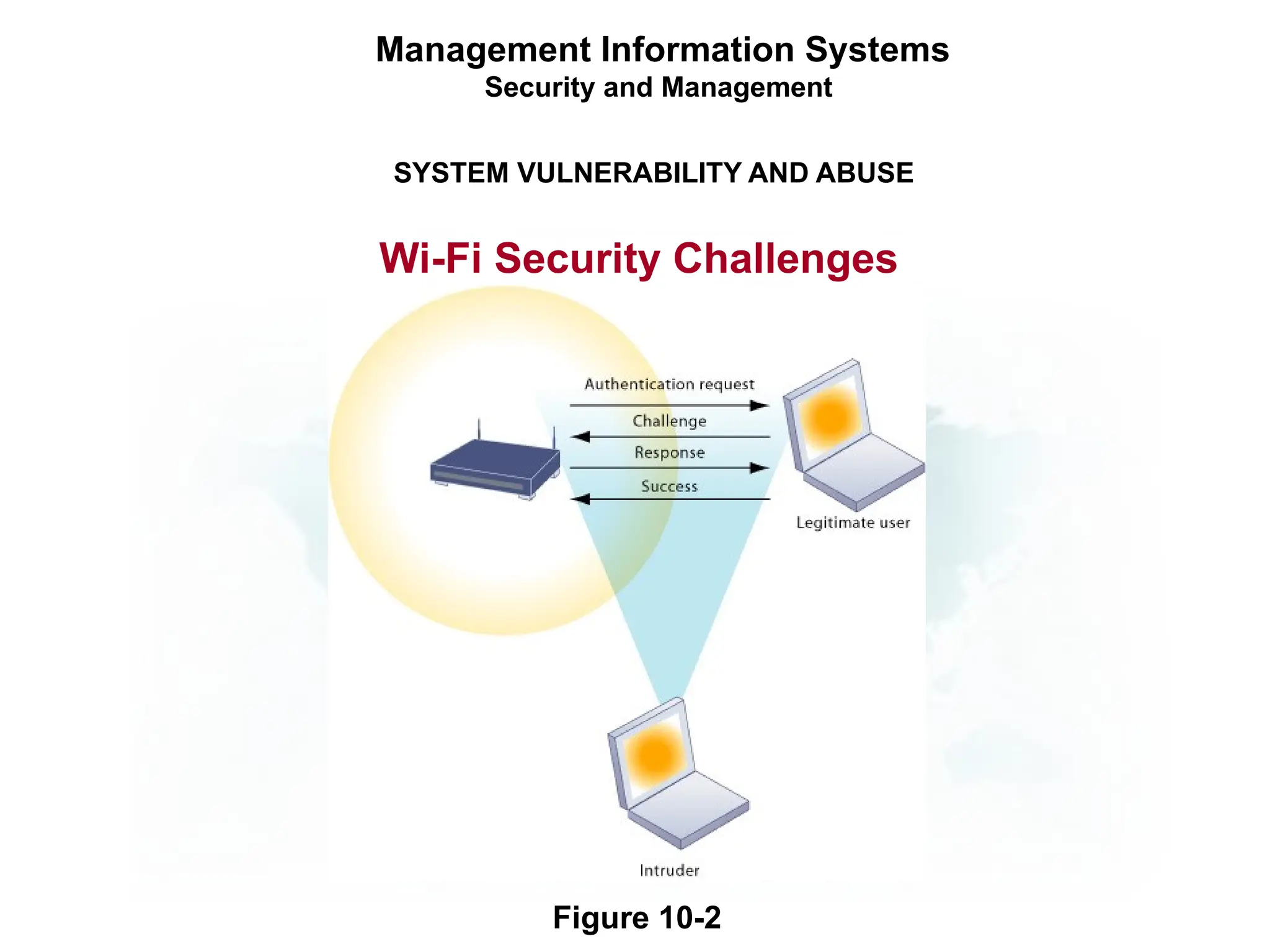
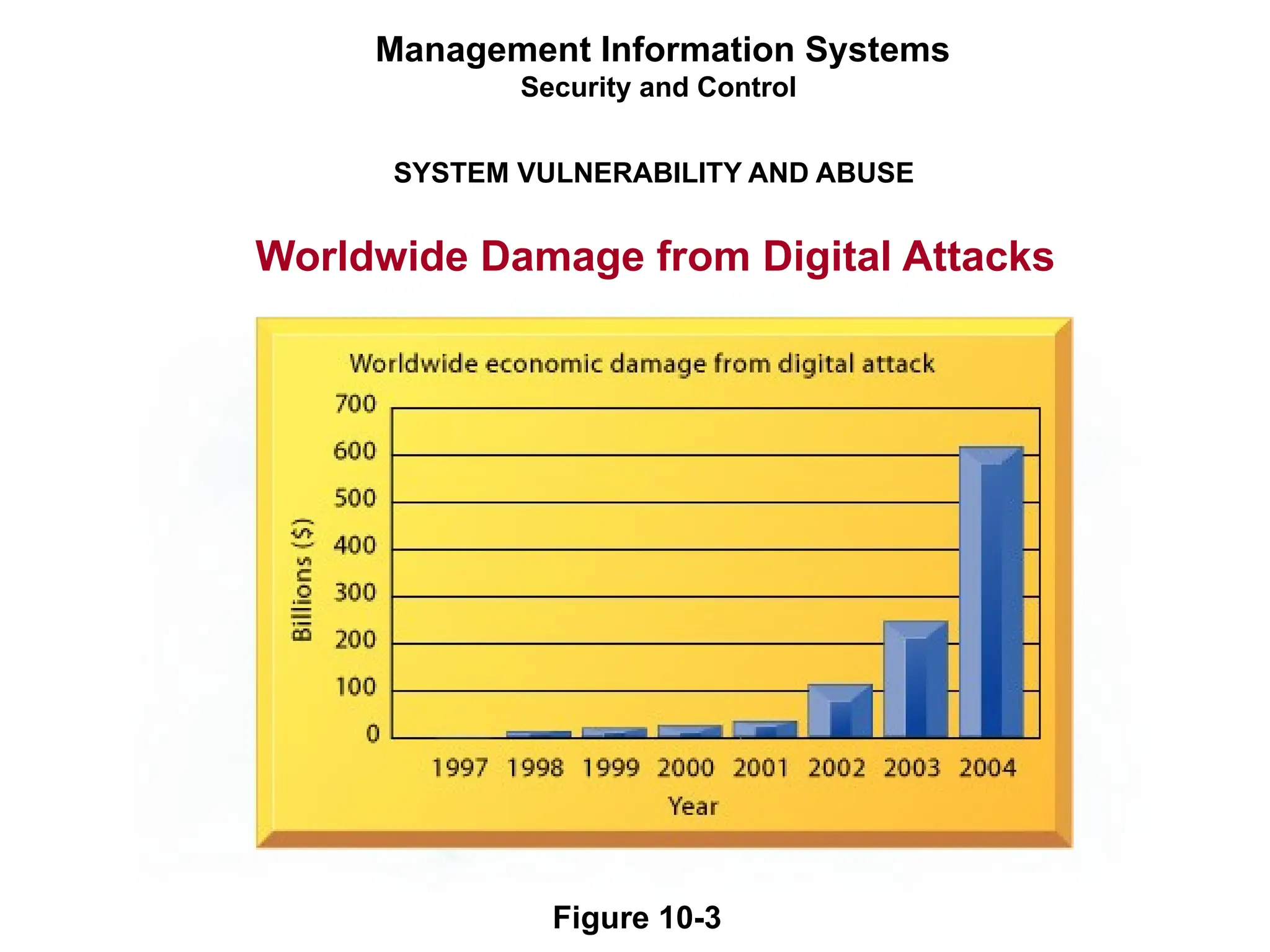
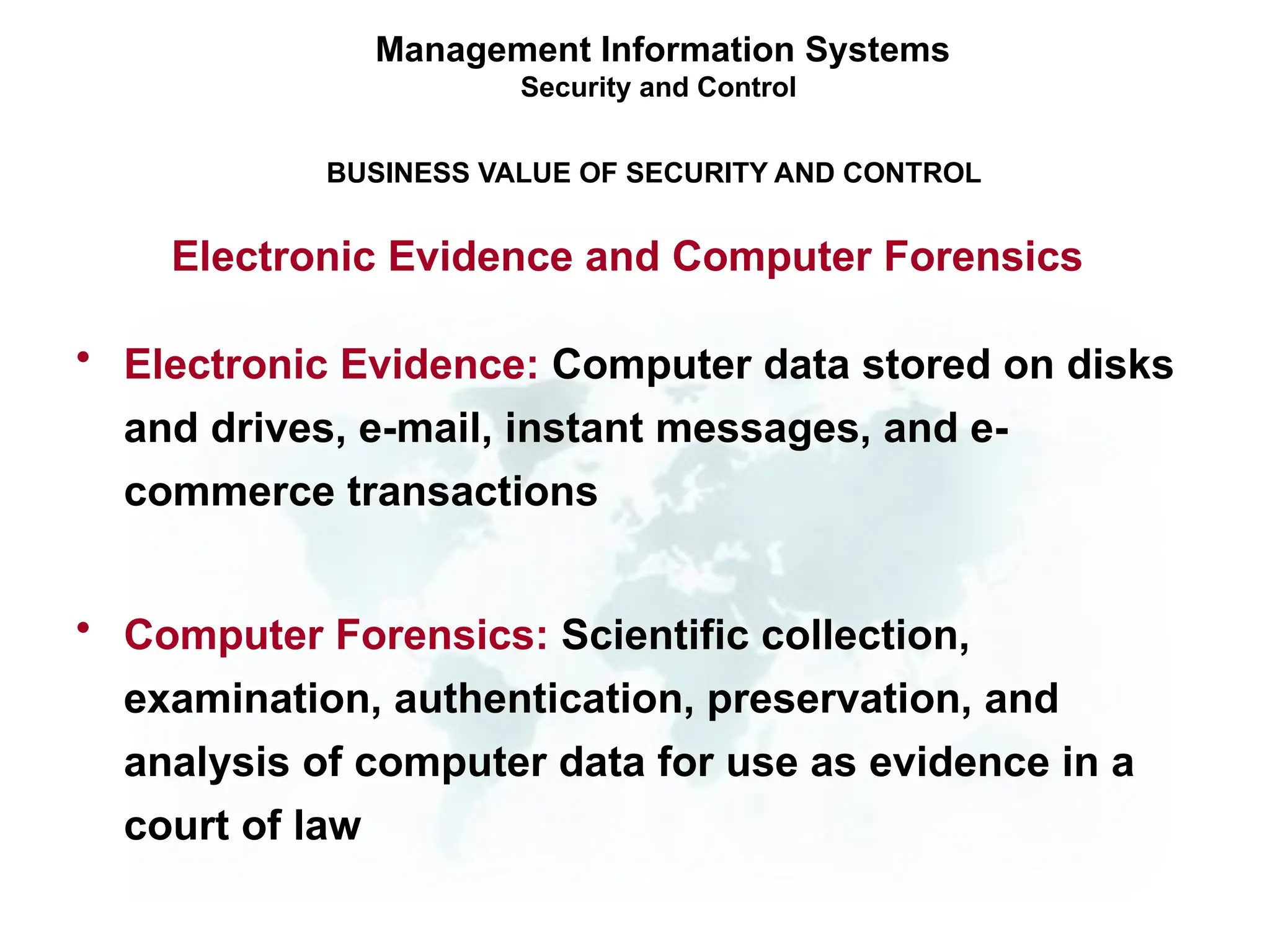
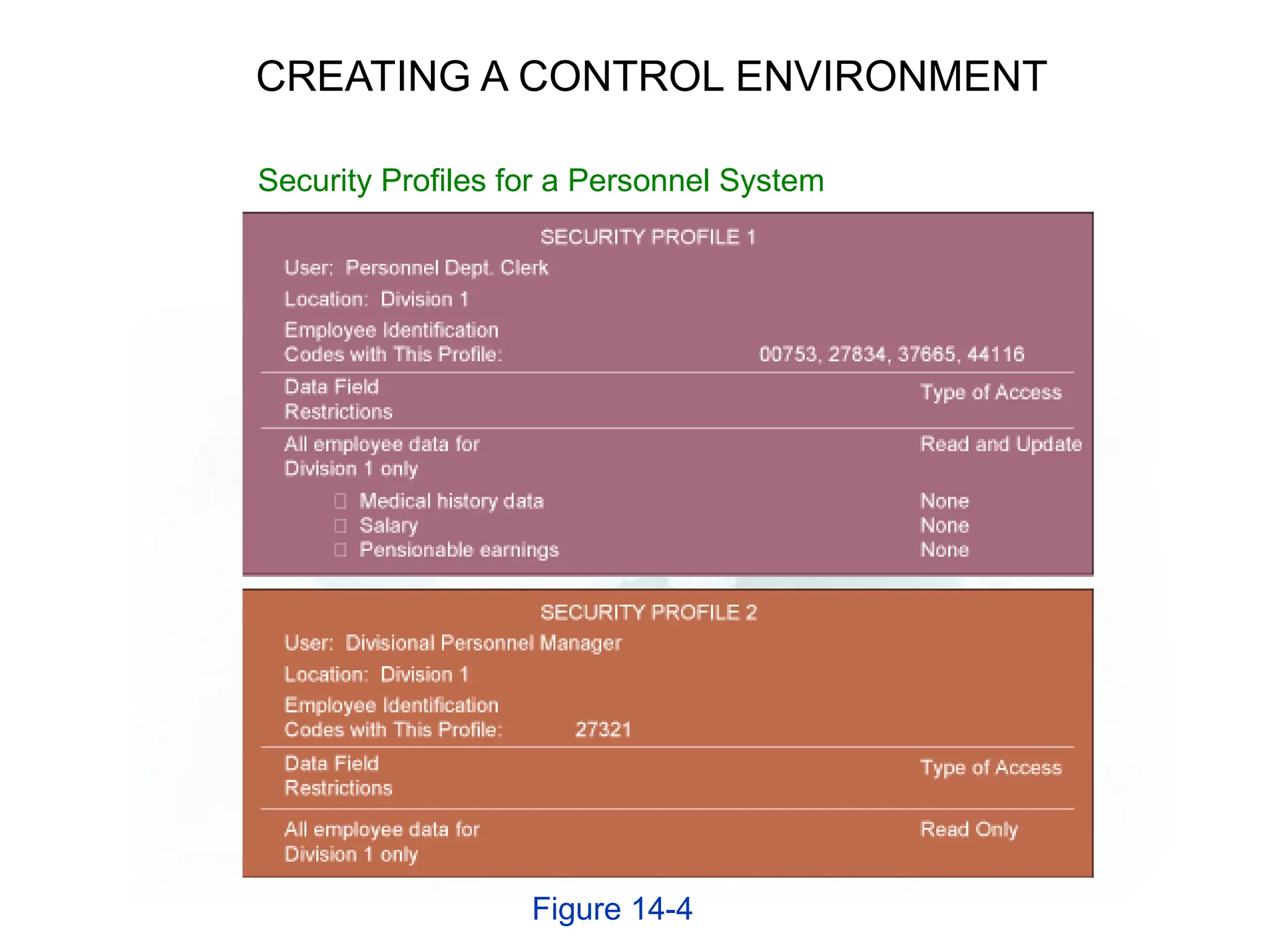
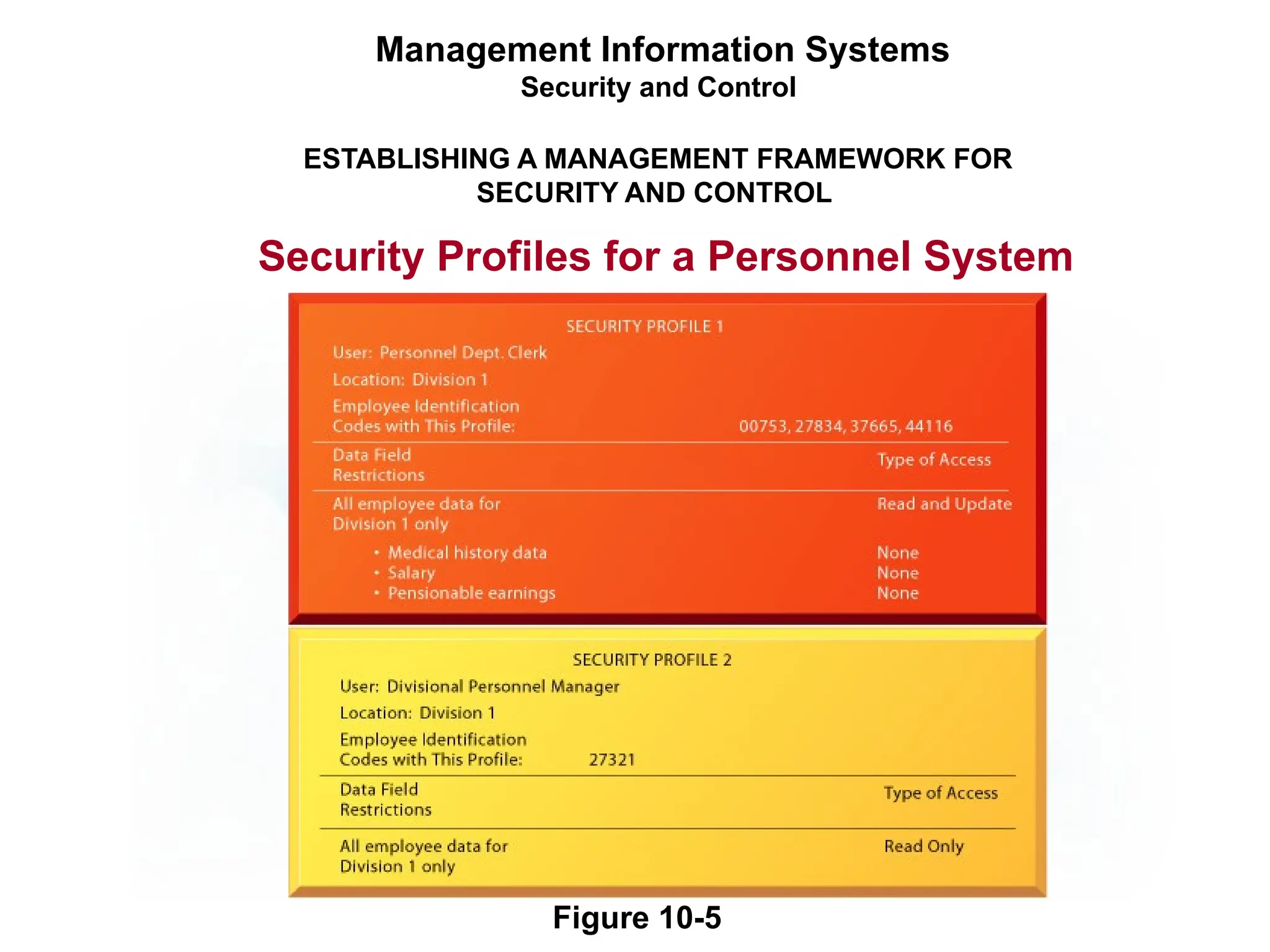
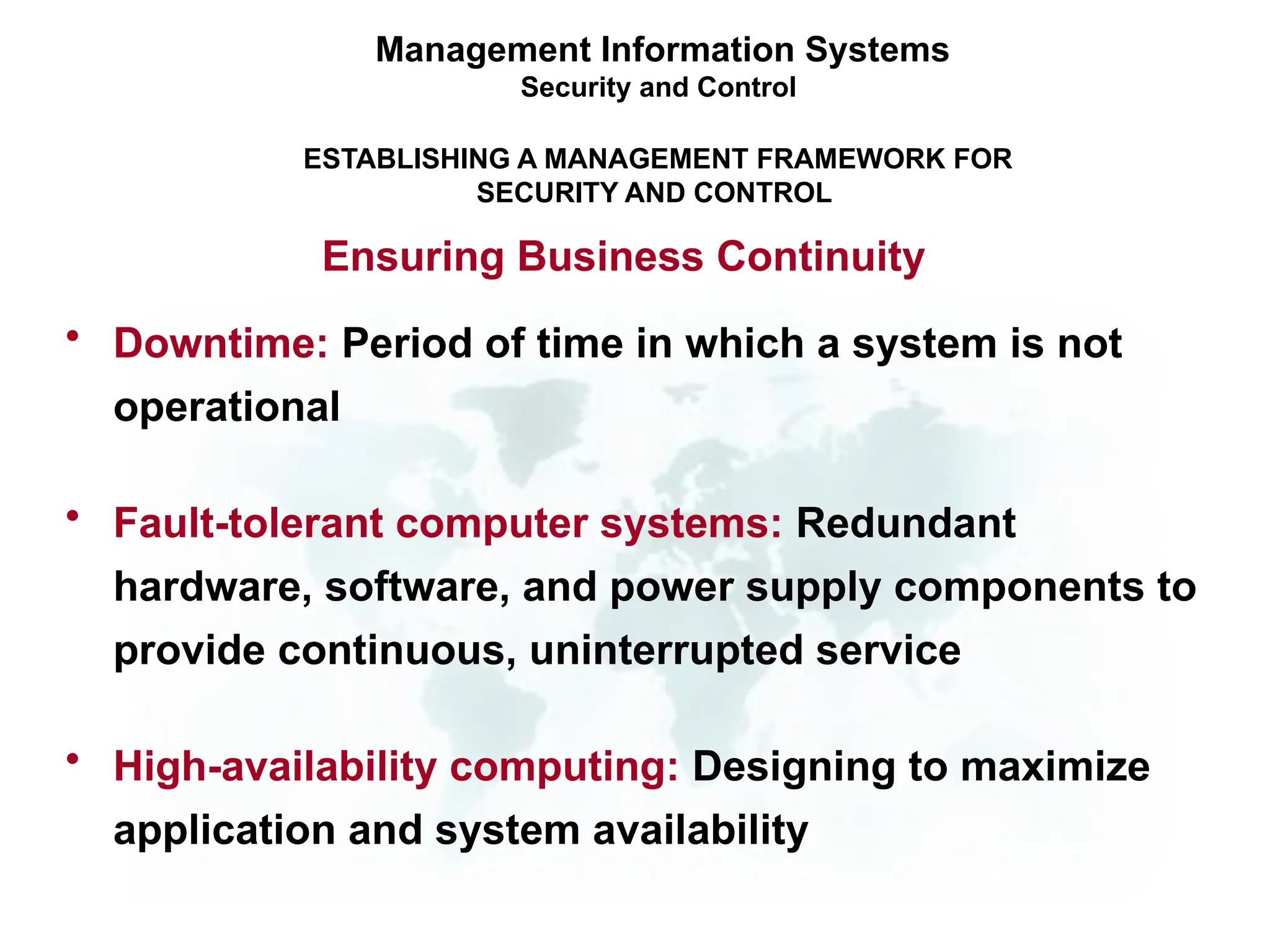
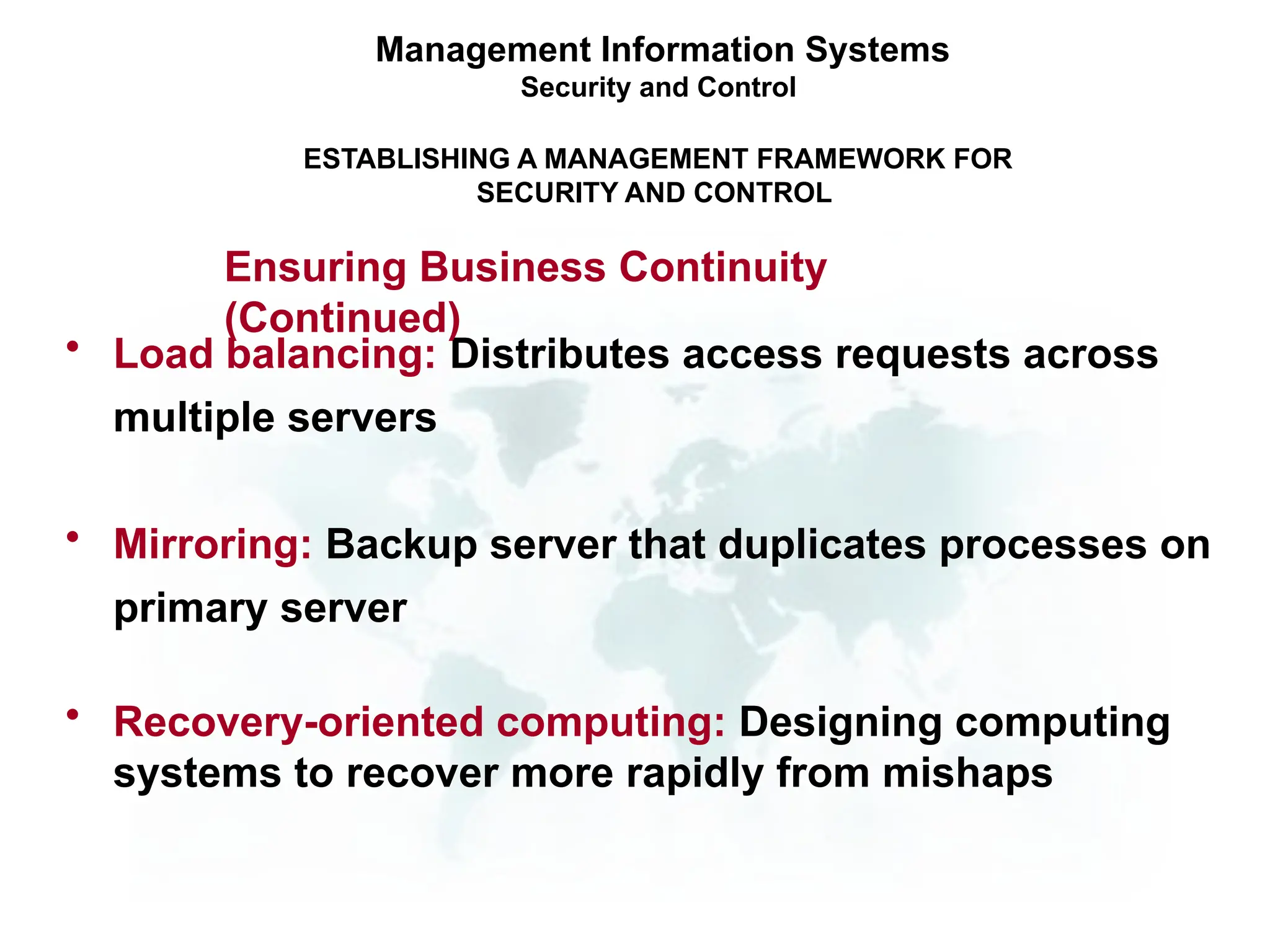
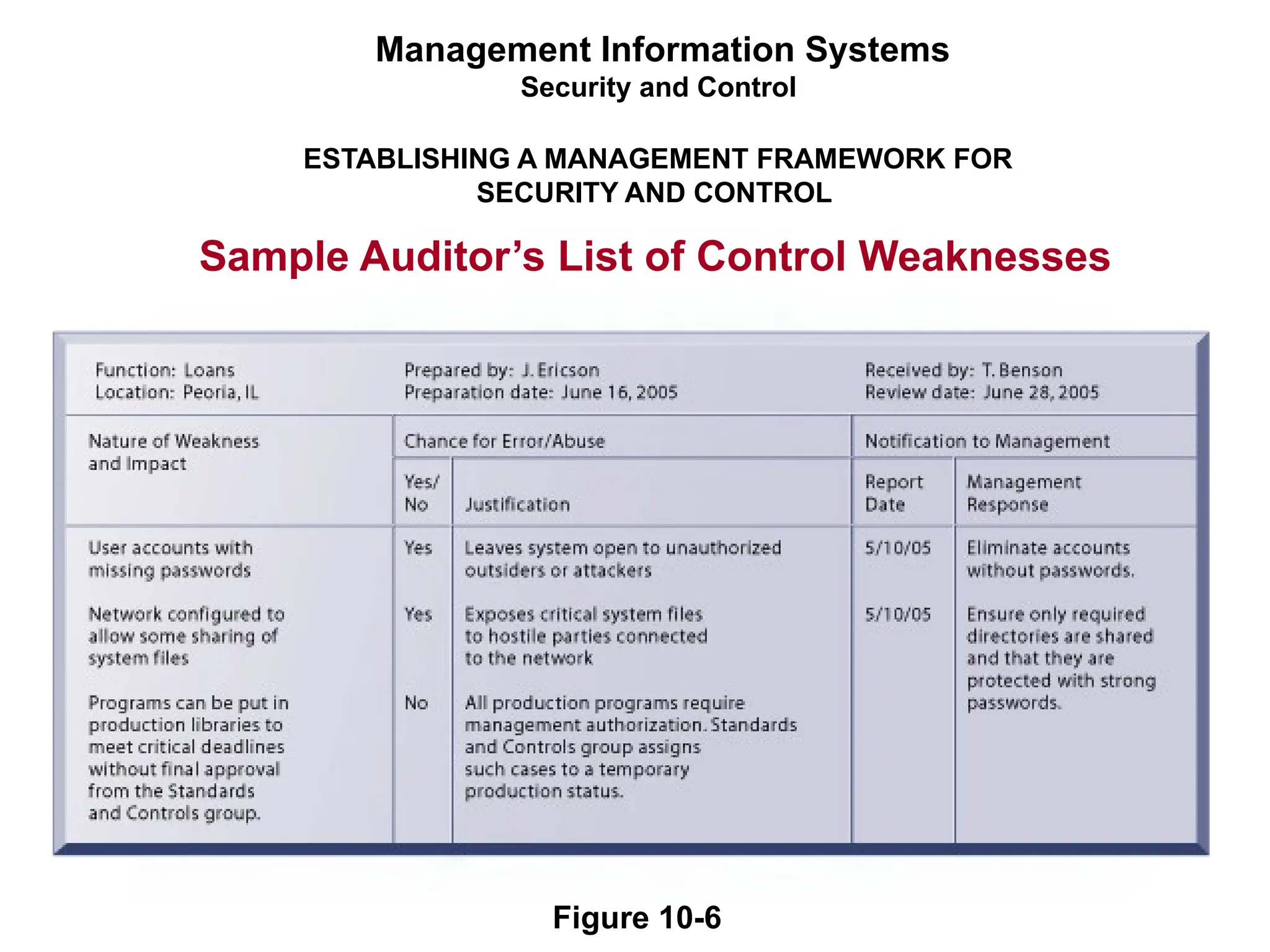
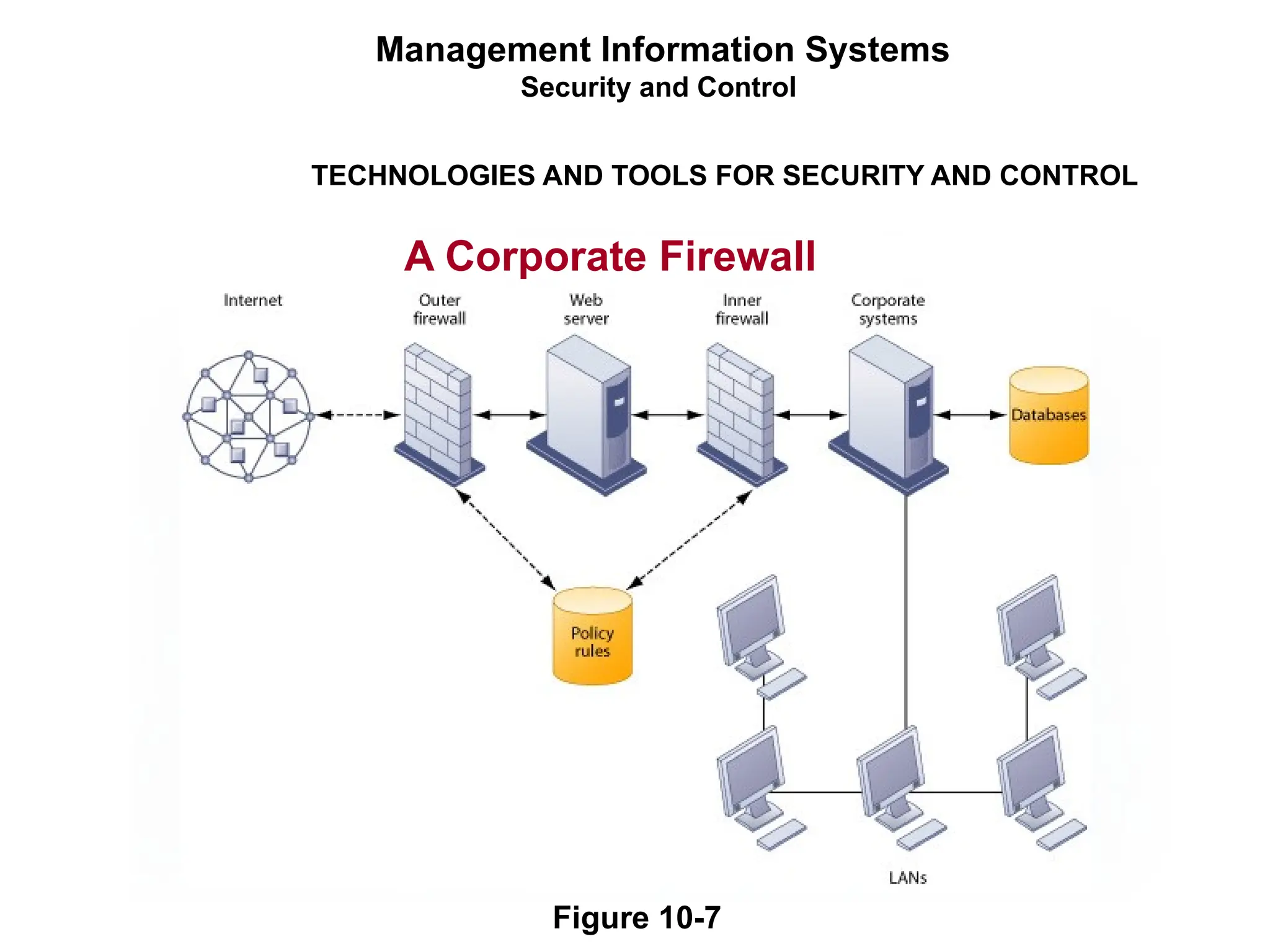
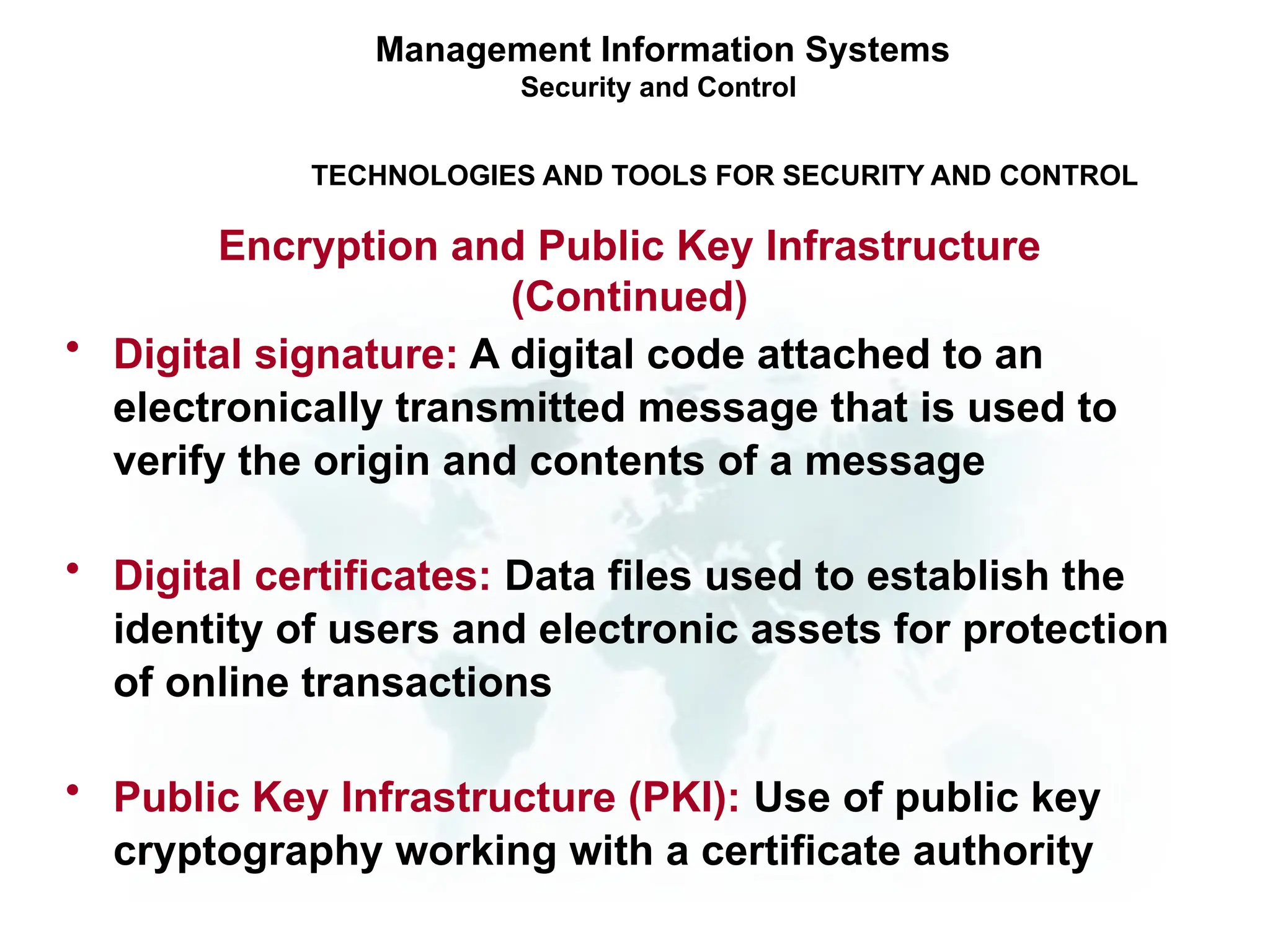
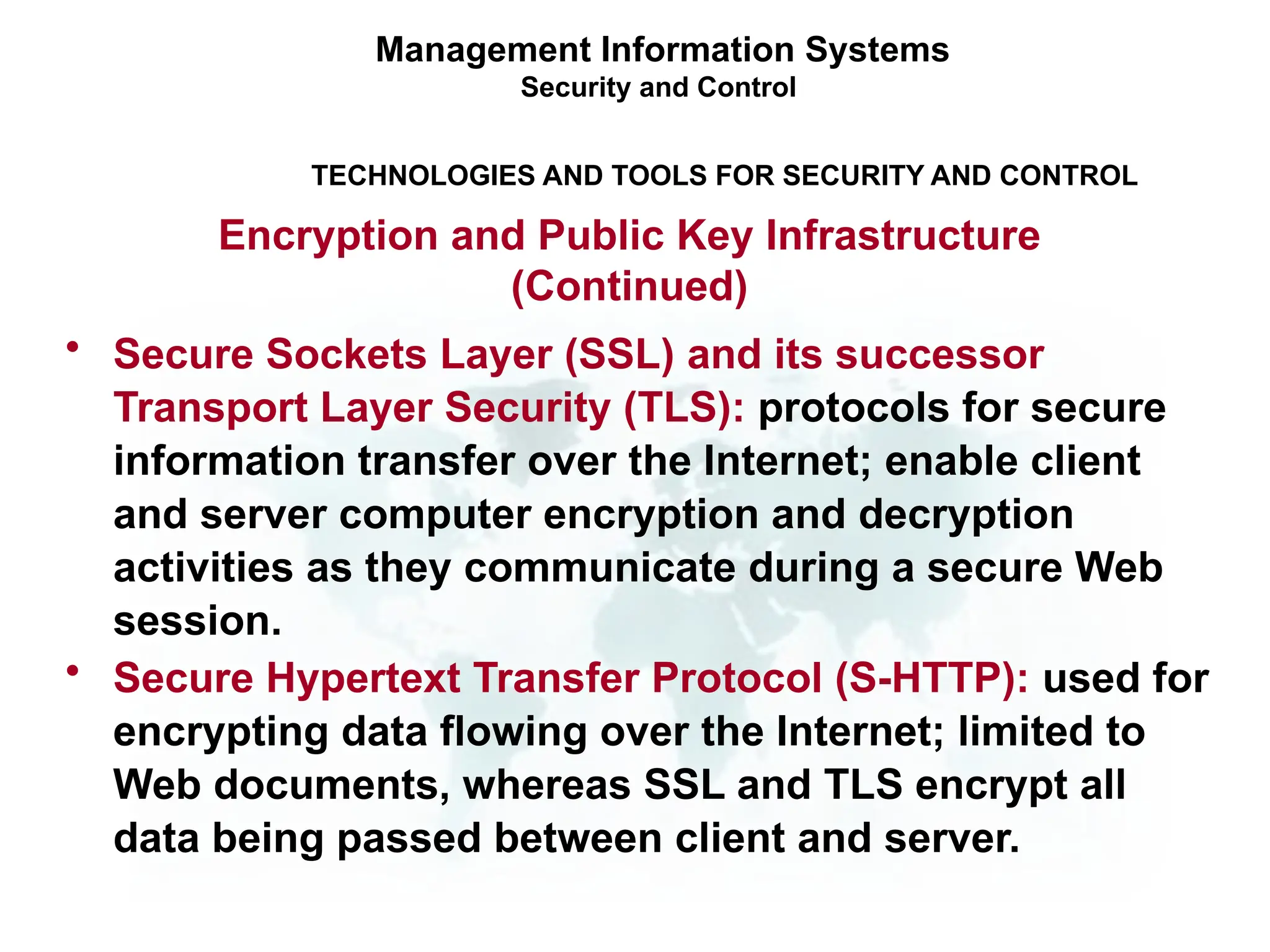
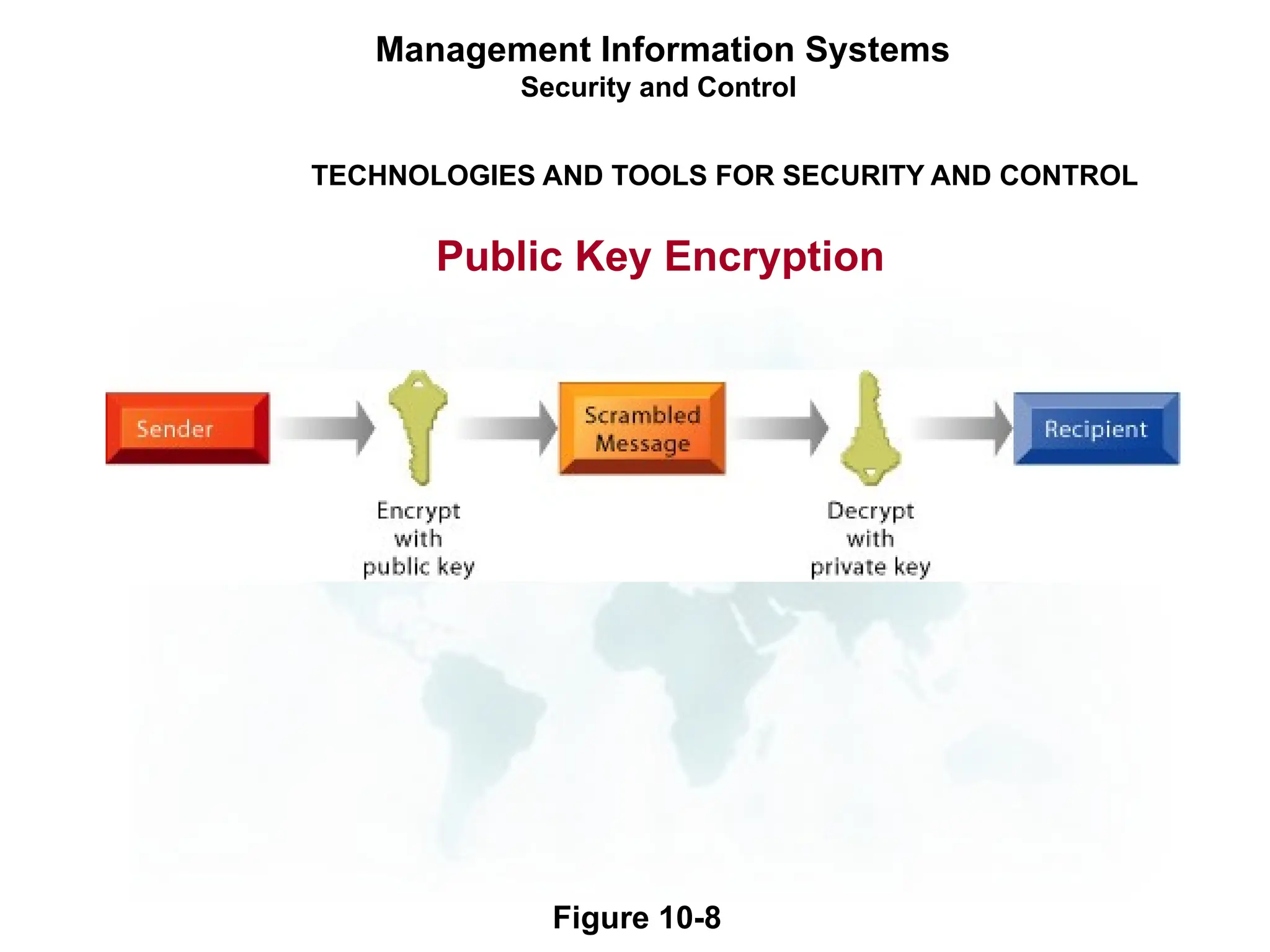
The document outlines the objectives and importance of information systems security management, emphasizing the need to understand potential threats and develop effective strategies for protection. It discusses various common threats, including accidents, natural disasters, and cyberattacks, while also addressing management approaches to enhance data integrity and confidentiality. Additionally, it highlights the significance of legal compliance, risk assessment, and the implementation of controls to safeguard organizational assets in the digital environment.