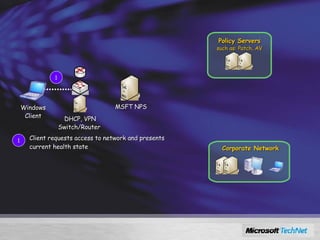
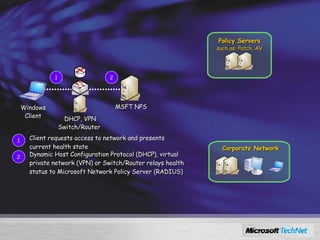
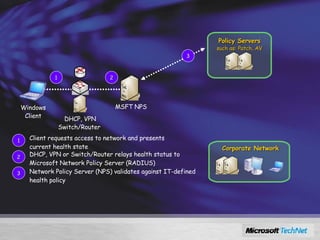
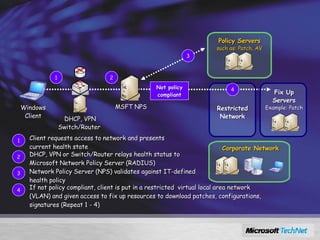
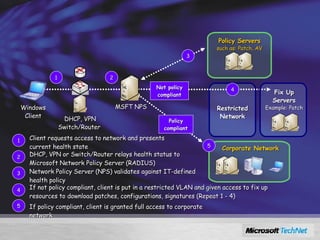
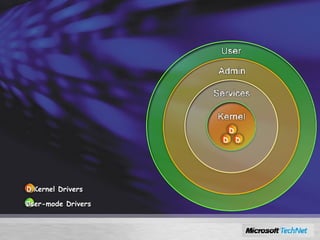
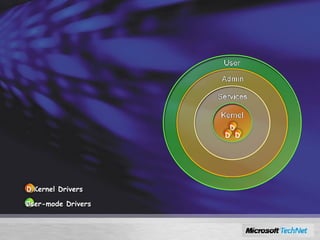
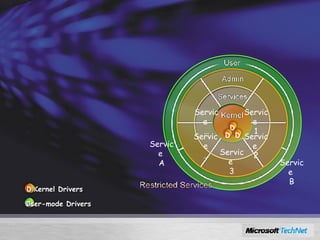
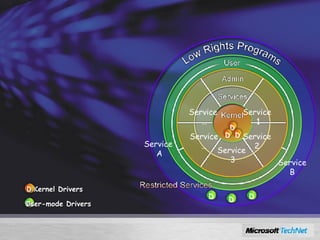
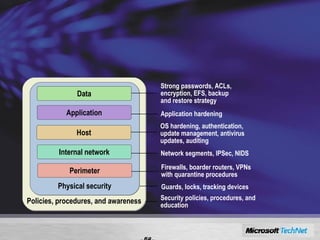
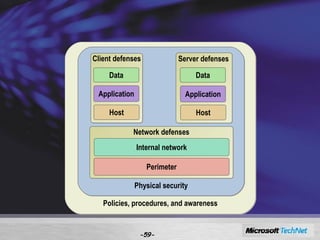
Windows Server 2008 includes several new security features to protect the operating system and applications. These include code integrity validation to prevent unauthorized code from loading, user access control to limit applications to standard user privileges, and network access protection to control network access based on the health status of client machines. The document also discusses improvements to application hardening, encryption technologies like BitLocker, and additional auditing capabilities in Windows Server 2008.