The document discusses honeypots, which are computer resources dedicated to being probed, attacked, or compromised. Honeypots can be used to detect internal attacks, identify scans and automated attacks, identify trends, keep attackers away from important systems, and collect signatures of attacks and malicious code. They work by emulating known vulnerabilities to collect information about attacks. Honeypots include low and high interaction varieties. Popular honeypot software includes Honeyd, which simulates virtual networks, and Nepenthes, which emulates vulnerabilities to capture binaries and commands executed by worms. Logs from honeypots can be analyzed to identify attack sources and collect malware samples.






![Detectando Máquinas Virtuais
/* VMM detector, based on SIDT trick written by joanna at invisiblethings.org
* should compile and run on any Intel based OS
* http://invisiblethings.org
*/
#include <stdio.h>
int main () {
unsigned char m[2+4], rpill[] = "x0fx01x0dx00x00x00x00xc3";
*((unsigned*)&rpill[3]) = (unsigned)m;
((void(*)())&rpill)();
printf ("idt base: %#xn", *((unsigned*)&m[2]));
if (m[5]>0xd0) printf ("Inside Matrix!n", m[5]);
else printf ("Not in Matrix.n");
return 0;
}](https://image.slidesharecdn.com/honeypots-12864130425193-phpapp01/85/Honeypots-Visao-Geral-11-320.jpg)


![Honeyd – Scripts
$> cat /var/honeyd/scripts/hello.sh $> telnet 10.0.0.1 23
Trying 10.0.0.1...
#!/usr/local/bin/bash Connected to 10.0.0.1.
echo "Hello world!" Escape character is '^]'.
while read data Hello world!
do
echo "$data" $> tail /var/honeyd/log/honeyd.log
done 2008-08-28-09:48:16.3539 tcp(6) S *.*.*.* 59255
10.0.0.1 23 [Linux 2.6 ]
$> cat /var/honey/conf/honeyd.conf
create test
add test tcp port 23
"/var/honeyd/scripts/hello.sh"
bind 10.0.0.1 test](https://image.slidesharecdn.com/honeypots-12864130425193-phpapp01/85/Honeypots-Visao-Geral-15-320.jpg)
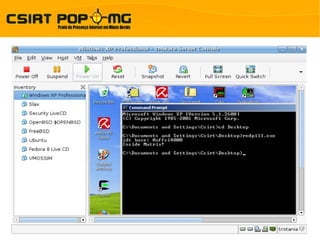
![Honeyd – Análise de Logs
$> cat /var/honeyd/log/honeyd.log
2008-08-28-00:39:00.0156 tcp(6) - 189.34.72.204 39367 *.*.*.* 22: 60 S [Linux 2.6 ]
2008-08-28-02:03:34.8542 tcp(6) - 124.64.123.69 64161 *.*.*.* 8080: 48 S [Windows XP SP1]
2008-08-28-02:17:44.3695 tcp(6) - 118.161.232.185 53063 *.*.*.* 3124: 48 S [Windows XP SP1]
2008-08-28-02:39:21.3643 tcp(6) - 201.160.39.176 4628 *.*.*.* 4899: 48 S [Windows XP SP1]
2008-08-28-03:15:22.0131 tcp(6) - 58.215.93.7 6000 *.*.*.* 2967: 40 S
2008-08-28-04:13:58.0860 icmp(1) - 222.124.175.222 *.*.*.*: 8(0): 61
2008-08-28-04:41:32.8131 tcp(6) - 148.204.175.200 35480 *.*.*.* 22: 60 S [Linux 2.6 ]
2008-08-28-04:55:34.4515 icmp(1) - 12.210.84.232 *.*.*.*: 8(0): 61
2008-08-28-05:09:05.3692 tcp(6) - 200.249.132.68 3353 *.*.*.* 135: 48 S [Windows XP SP1]
2008-08-28-06:39:50.9295 tcp(6) - 200.249.132.68 1300 *.*.*.* 135: 48 S [Windows XP SP1]
2008-08-28-07:16:31.3405 tcp(6) - 81.88.245.118 3559 *.*.*.* 445: 48 S [Windows XP SP1]
2008-08-28-07:36:45.1329 tcp(6) - 125.230.79.108 4512 *.*.*.* 25: 52 S [Windows 2000 RFC1323]
2008-08-28-07:45:31.4038 tcp(6) - 201.3.202.102 34215 *.*.*.* 22: 60 S [Linux 2.6 ]
2008-08-28-08:36:44.6540 tcp(6) - 84.60.254.245 4126 *.*.*.* 8080: 48 S [Windows 98 ]](https://image.slidesharecdn.com/honeypots-12864130425193-phpapp01/85/Honeypots-Visao-Geral-16-320.jpg)

![Nepenthes – Análise de Logs
$> cat /var/nepenthes/log/logged_downloads
[2008-08-27T04:24:58] 213.23.2.114 -> *.*.*.* tftp://192.168.168.199/mslaugh.exe
[2008-08-27T12:16:57] 88.156.57.191 -> *.*.*.* creceive://88.156.57.191:9988/0
[2008-08-27T13:02:57] 65.207.42.75 -> *.*.*.* tftp://129.12.19.71/msblast.exe
[2008-08-27T13:37:58] 83.92.20.178 -> *.*.*.* creceive://83.92.20.178:9988/0
[2008-08-27T14:10:51] 200.249.132.68 -> *.*.*.* link://200.249.132.68:42087/qFsh+A==
[2008-08-27T17:43:10] 200.249.132.68 -> *.*.*.* link://200.249.132.68:42087/qFsh+A==
[2008-08-27T18:03:06] 70.126.5.31 -> *.*.*.* creceive://70.126.5.31:9988/0
[2008-08-27T18:27:01] 170.51.137.180 -> *.*.*.* ftp://1:1@170.51.137.180:20864/directxx.exe
[2008-08-27T20:31:50] 200.13.254.183 -> *.*.*.* link://200.13.254.183:58382/eOkm/A==
[2008-08-27T21:37:29] 200.249.132.68 -> *.*.*.* link://200.249.132.68:42087/qFsh+A==
[2008-08-27T21:43:27] 208.28.150.10 -> *.*.*.* tftp://200.1.1.221/msblast.exe
[2008-08-27T23:18:42] 74.160.106.20 -> *.*.*.* creceive://74.160.106.20:9988/0
[2008-08-27T23:34:10] 24.98.111.69 -> *.*.*.* http://67.191.230.57/](https://image.slidesharecdn.com/honeypots-12864130425193-phpapp01/85/Honeypots-Visao-Geral-20-320.jpg)
![Nepenthes – Análise de Logs
$> cat /var/nepenthes/log/logged_submissions
[2008-08-27T12:17:15] 88.156.57.191 -> *.*.*.* creceive://88.156.57.191:18758
b1d52c56c5be86f927374870f1d62fb7
[2008-08-27T13:38:13] 83.92.20.178 -> *.*.*.* creceive://83.92.20.178:3947
32fc8b13d82583304d037859b7753c82
[2008-08-27T18:03:16] 70.126.5.31 -> *.*.*.* creceive://70.126.5.31:4450
3875b6257d4d21d51ec13247ee4c1cdb
[2008-08-27T18:27:23] 170.51.137.180 -> *.*.*.* ftp://1:1@170.51.137.180:20864/directxx.exe
382279b44f26c6d87ccaf5d8d4689738
[2008-08-27T20:31:53] 200.13.254.183 -> *.*.*.* link://200.13.254.183:58382/eOkm/A==
474312616dce04c03f13a20a6244b2bf
[2008-08-27T23:18:52] 74.160.106.20 -> *.*.*.* creceive://74.160.106.20:19673
3875b6257d4d21d51ec13247ee4c1cdb](https://image.slidesharecdn.com/honeypots-12864130425193-phpapp01/85/Honeypots-Visao-Geral-21-320.jpg)


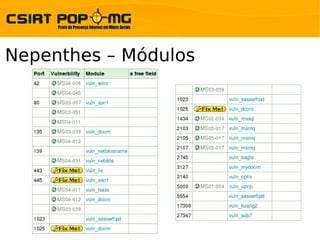
![Amun – Análise de Logs
$> cat /var/amun/vuln_modules/vuln-ftpd/ftpd_modul.py
import psyco ; psyco.full()
from psyco.classes import *
import struct
import random
import ftpd_shellcodes
import amun_logging
class vuln:
def __init__(self):
try:
self.vuln_name = "FTPD Vulnerability"
self.stage = "FTPD_STAGE1"
self.welcome_message = "220 Welcome to my FTP Server"
self.shellcode = []
except KeyboardInterrupt:
raise
...](https://image.slidesharecdn.com/honeypots-12864130425193-phpapp01/85/Honeypots-Visao-Geral-24-320.jpg)
![Amun – Análise de Logs
$> cat /var/amun/logs/exploits.log*
2008-08-23 04:45:06,861 INFO exploit 209.60.60.19:2354 -> *.*.*.*:445 (PNP Vulnerability:
bind://200.19.159.131:8594/)
2008-08-24 18:13:41,306 INFO exploit 122.160.202.148:33772 -> *.*.*.*:2967 (SYMANTEC
Vulnerability: cbacks://61.246.185.69:1235/)
2008-08-24 18:26:01,128 INFO exploit 200.149.108.192:3064 -> *.*.*.*:445 (ASN1 Vulnerability:
ftp://1:1@200.149.108.192:20579/['win.exe'])
2008-08-25 01:06:35,619 INFO exploit 200.249.132.68:3945 -> *.*.*.*:135 (DCOM Vulnerability:
cbackf://200.249.132.68:47683/6Fch+A==)
2008-08-25 02:32:57,851 INFO exploit 200.249.132.68:1580 -> *.*.*.*:135 (DCOM Vulnerability:
cbackf://200.249.132.68:47683/6Fch+A==)
2008-08-25 03:24:20,532 INFO exploit 24.87.32.159:3888 -> *.*.*.*:135 (DCOM Vulnerability:
cbackf://24.87.32.159:24536/YmNpLg==)
2008-08-25 08:34:58,236 INFO exploit 125.211.218.29:3887 -> *.*.*.*:443 (IIS Vulnerability:
http://thecric.free.fr:80/AZenv/azenv.php)](https://image.slidesharecdn.com/honeypots-12864130425193-phpapp01/85/Honeypots-Visao-Geral-25-320.jpg)
![Amun – Análise de Logs
$> cat /var/amun/logs/submissions.log*
2008-08-24 18:17:15,366 INFO [submit_md5] download (http://www.wuya1001.com:80/83.exe):
f16ba3d216853f6f5d40bae499f17c51 (size: 62046) - SYMANTEC
2008-08-24 18:31:55,985 INFO [submit_md5] download (ftp://1:1@200.149.108.192:20579/
['win.exe']): 8fcdb53b814d3155d232a149efaa40a8 (size: 132096) - ASN1
2008-08-24 18:44:21,365 INFO [submit_md5] download
(cbackf://200.13.254.183:46886/eOkW/A==): 474312616dce04c03f13a20a6244b2bf (size:
68608) - DCOM
2008-08-22 15:22:43,798 INFO [submit_md5] download (ftp://liubinbin:liubinbin@60.169.2.167:21/
['file/Ser1.exe']): aaaeaf9ab82f5cfe6738ca6cbed05085 (size: 61998) - SYMANTEC
2008-08-23 02:46:20,546 INFO [submit_md5] download
(cbackf://200.210.158.130:32636/eOmR/w==): 989a2dbd1df28b9165f510bec67ebb3c (size:
100864) - DCOM
2008-08-23 07:08:58,329 INFO [submit_md5] download (http://www.wuya1001.com:80/83.exe):
a6938c98d846767ac7bc616c64a9a106 (size: 62037) - SYMANTEC
2008-08-23 19:22:04,694 INFO [submit_md5] download (ftp://1:1@84.59.211.166:16083/
['directxx.exe']): 382279b44f26c6d87ccaf5d8d4689738 (size: 179200) - ASN1](https://image.slidesharecdn.com/honeypots-12864130425193-phpapp01/85/Honeypots-Visao-Geral-26-320.jpg)