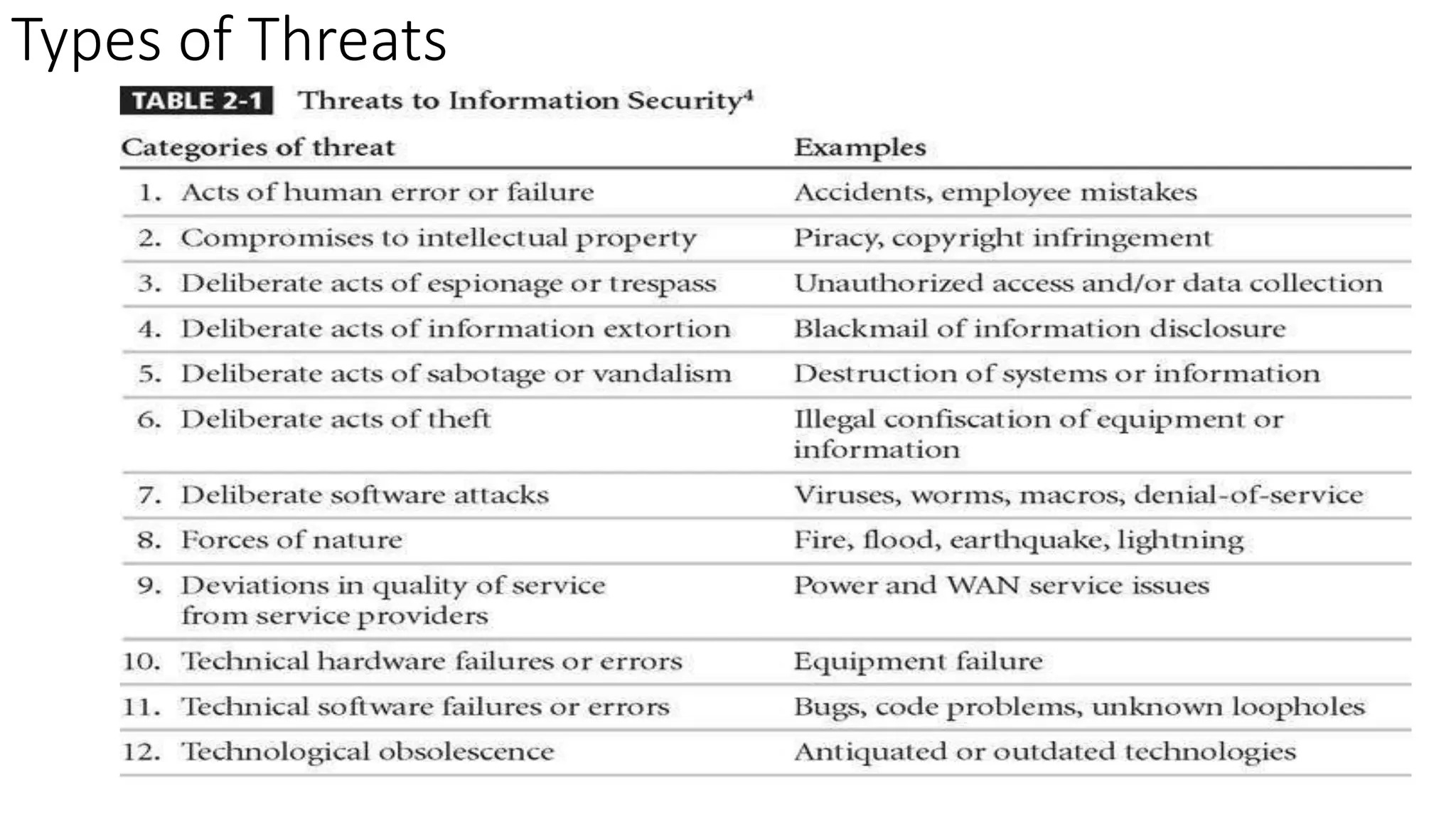
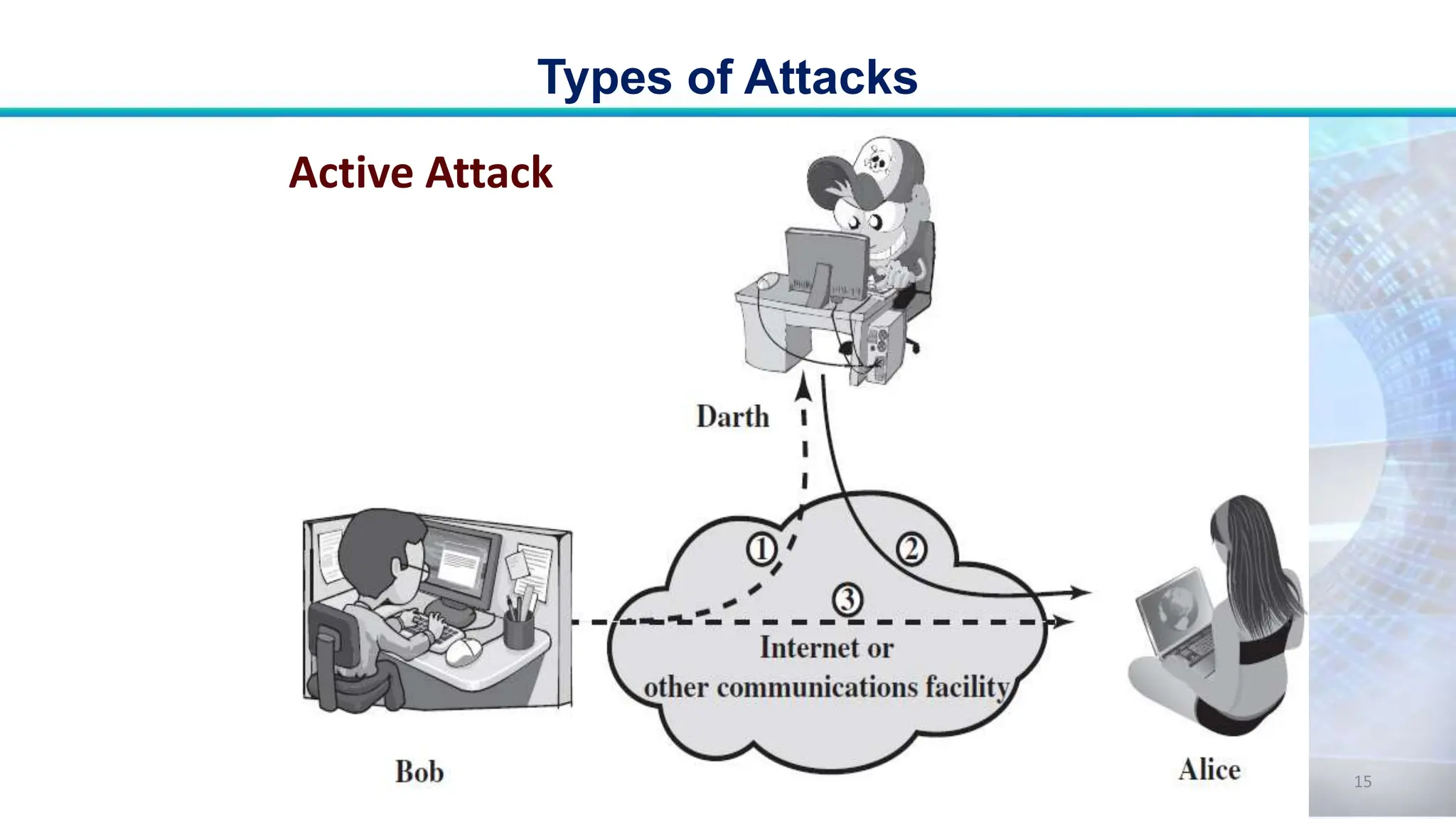
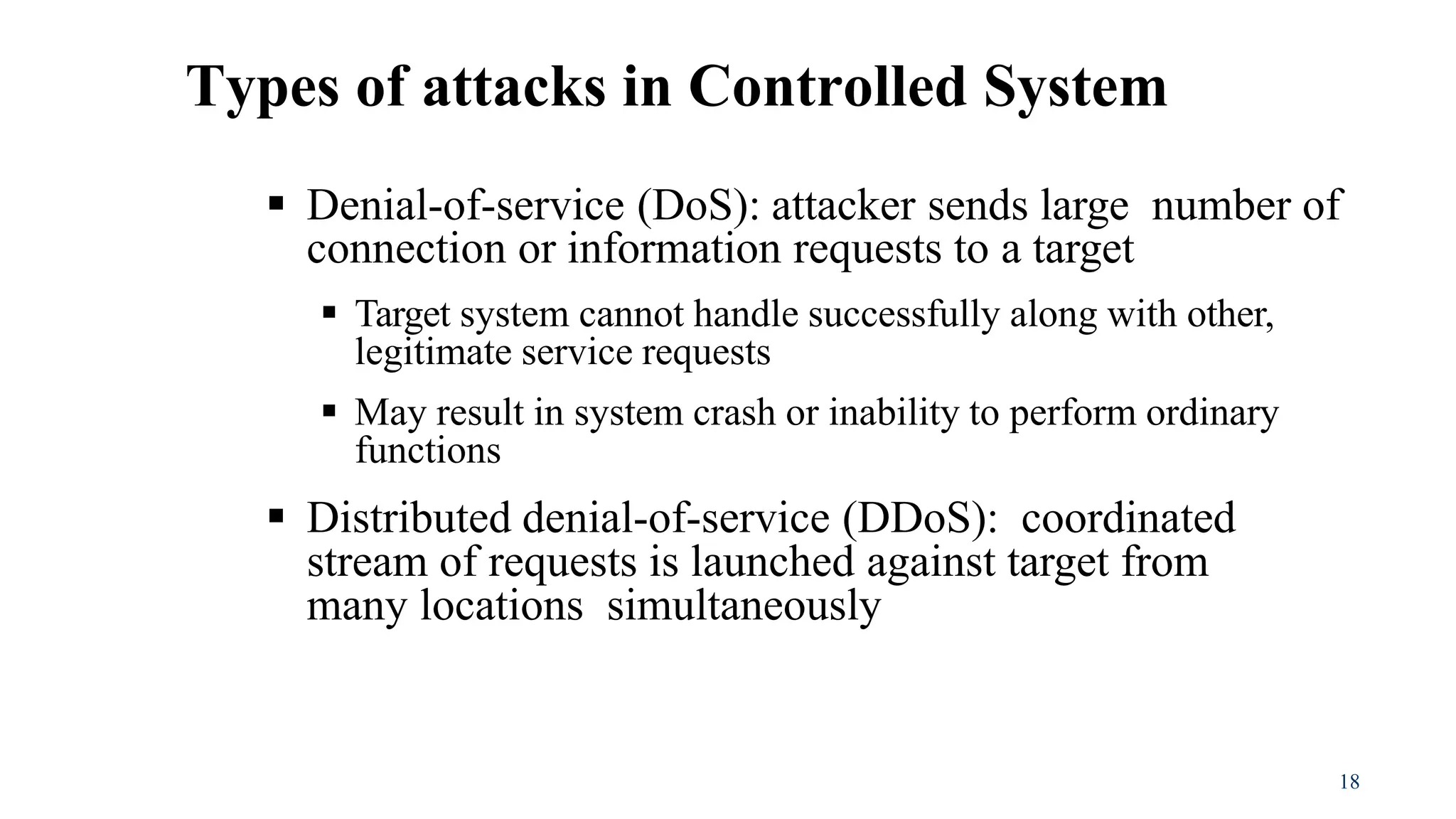
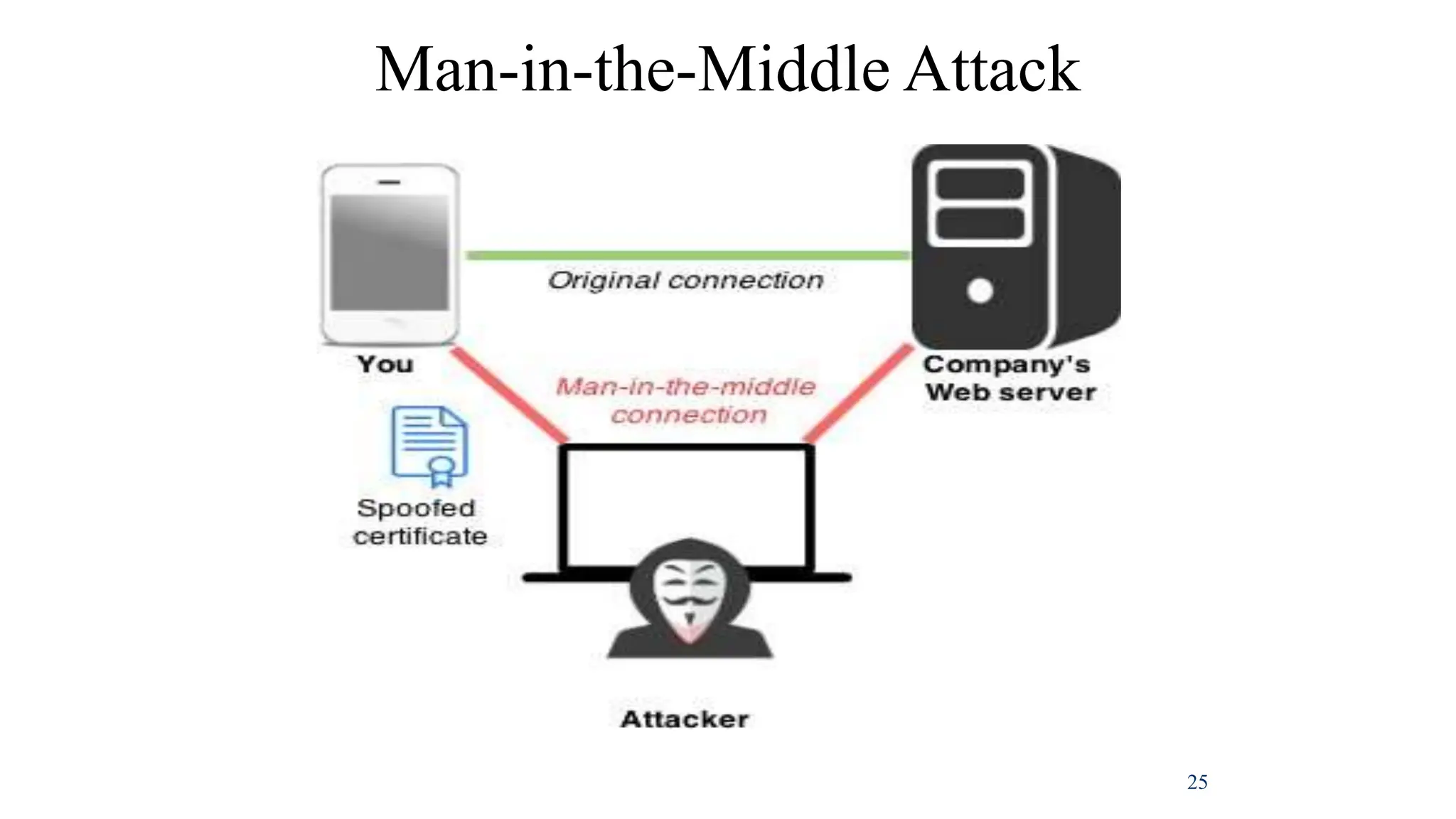
This document discusses various security concepts including business needs for information security, threats, and types of attacks. It explains that information security performs four key functions for organizations: protecting the ability to function, enabling safe application operation, protecting data, and safeguarding technology assets. Several types of threats are outlined including natural threats, human threats, and environmental threats. Passive and active attacks are defined, and examples of different types of attacks on controlled systems are provided such as malware, backdoors, password cracking, denial of service attacks, spoofing, and social engineering.