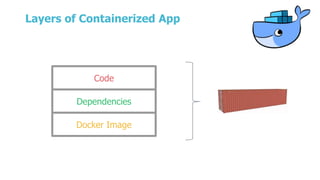
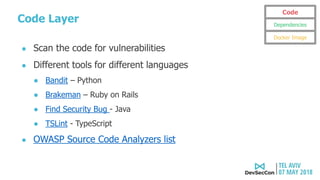
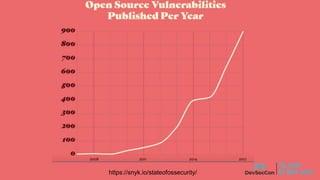
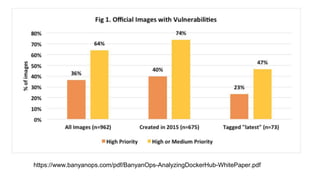
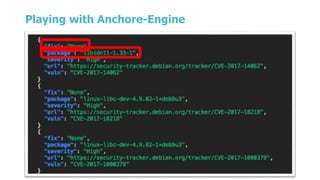
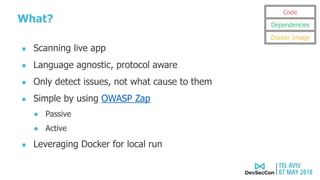
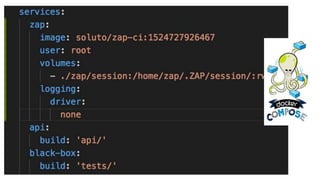
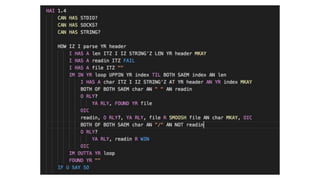
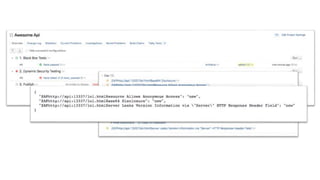
This document summarizes a presentation about security testing for containerized applications. It discusses performing static analysis on code, dependencies, and Docker images using open source tools like Bandit, Brakeman, Find Security Bugs, TSLint, OWASP Dependency Track, and Clair. It also covers dynamic analysis using passive and active scanning with OWASP Zap. The presentation demonstrates running these security tests on a sample Lolcode application and integrating the tests into a CI/CD pipeline using OWASP Glue. It provides resources for learning more about security testing of containerized apps.