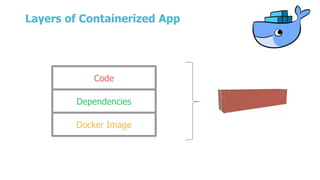
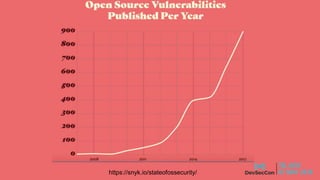
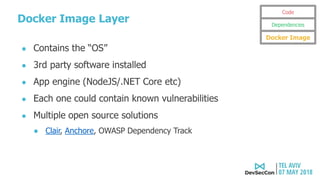
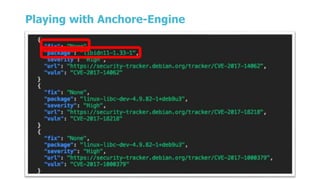
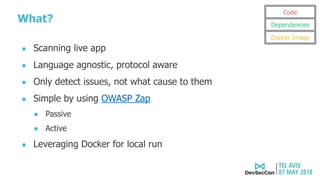
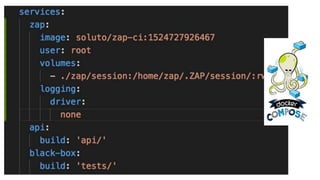
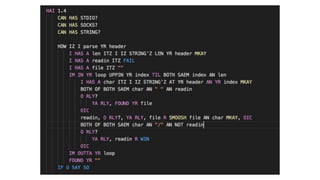
The document discusses security testing for containerized applications. It outlines different layers of containerized apps including code, dependencies, and Docker images. It then describes various security testing techniques that can be applied to each layer, including static analysis tools for code scanning, dependency scanning, and Docker image scanning. It also covers dynamic/runtime testing using passive and active scanning with tools like OWASP Zap. The document advocates building these security tests into the CI/CD pipeline and only deploying container images that pass all tests through a process of image certification. It demonstrates some of these techniques on a sample Lolcode application.