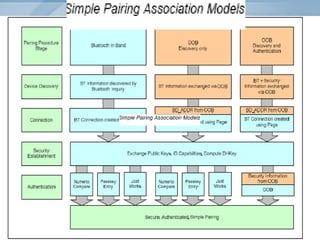
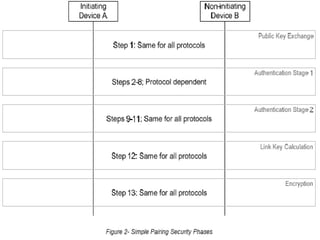
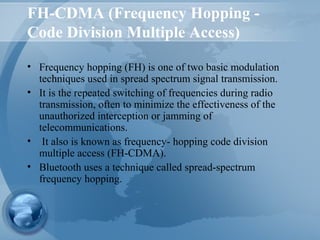
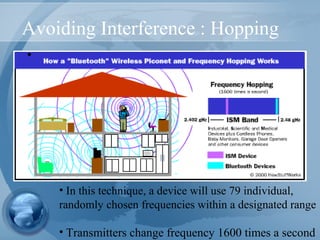
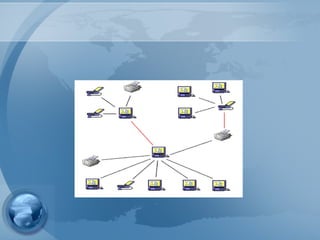
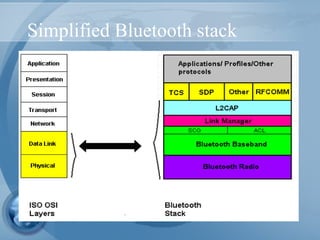
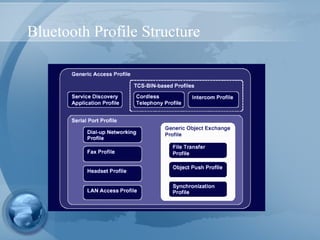
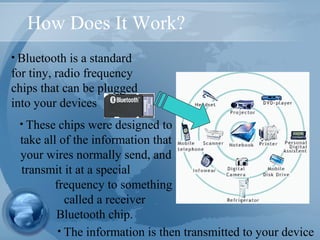
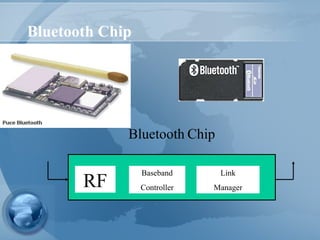
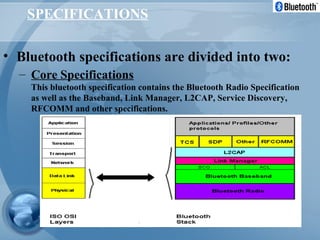
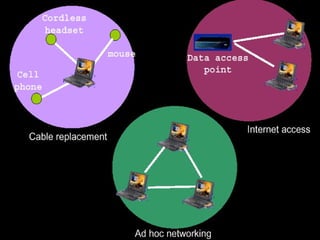
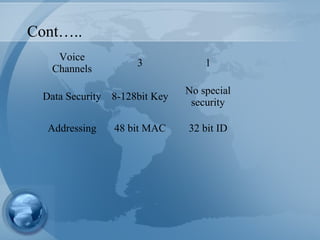
Bluetooth technology allows for wireless connections between various devices like phones, computers, and other electronics. The document discusses Bluetooth's history, specifications, security features and weaknesses. It provides technical details on how Bluetooth works, including defining piconets and scatternets, frequency hopping, encryption, and authentication processes. However, Bluetooth security has some vulnerabilities like short PINs, attacks on its encryption algorithms, and lack of location privacy.