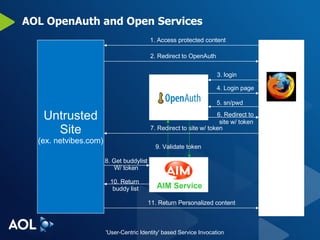
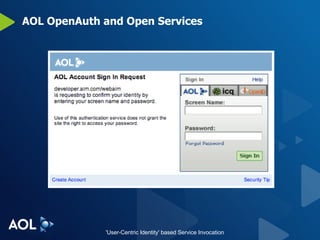
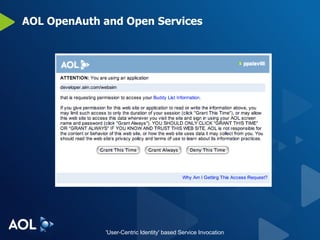
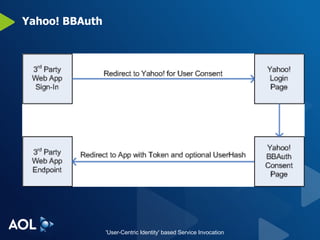
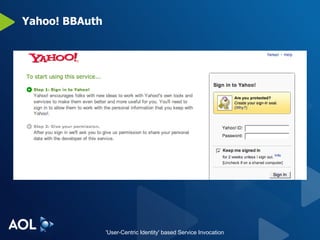
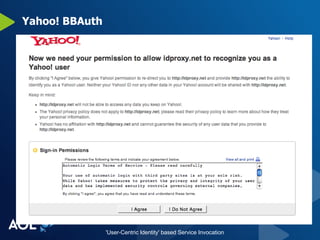
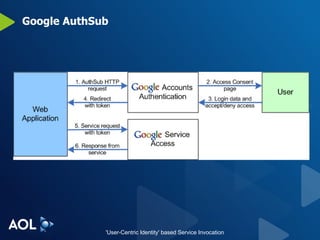
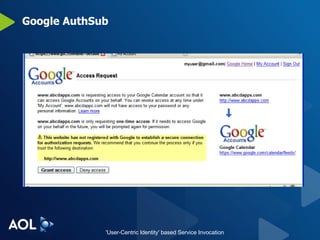
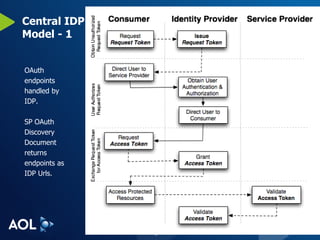
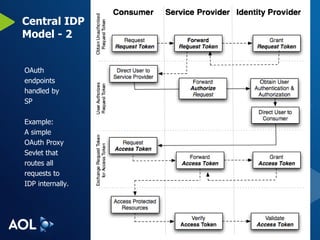
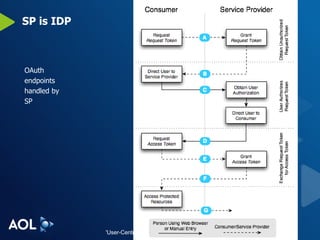
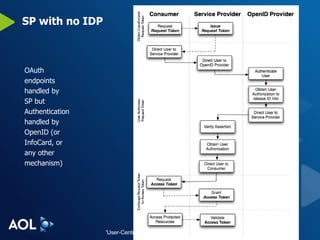
The document discusses user-centric identity and service invocation. It describes existing protocols like OpenID, SAML, and proprietary protocols from companies. It then introduces OAuth as an open standard for service invocation that is authentication method agnostic, easy for users and developers to implement, and provides security and privacy. OAuth defines a process for requesting user authorization for third-party access to protected services and resources in a standardized way.