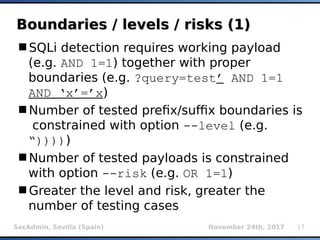
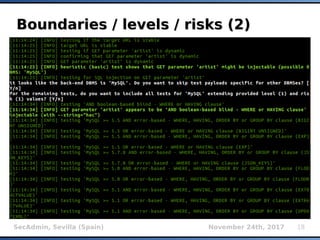
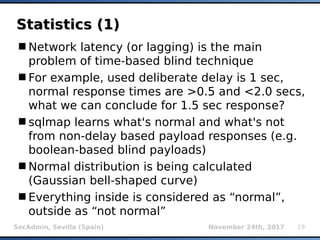
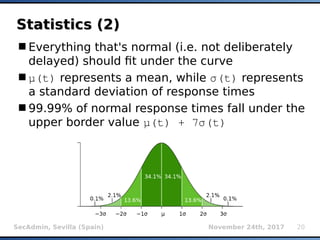
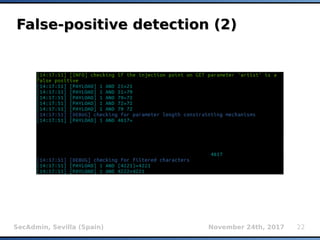
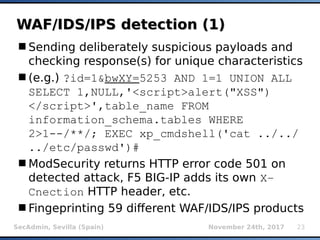
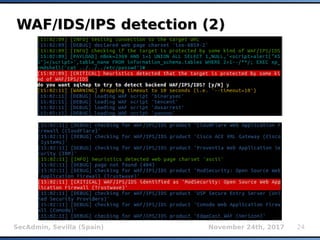
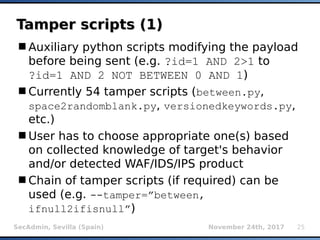
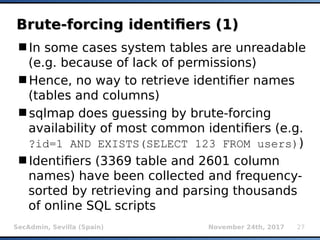
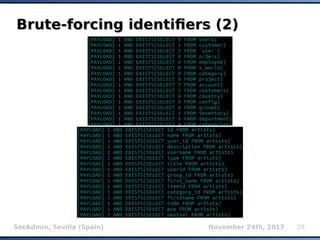
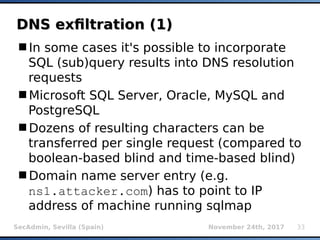
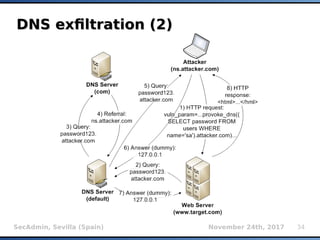
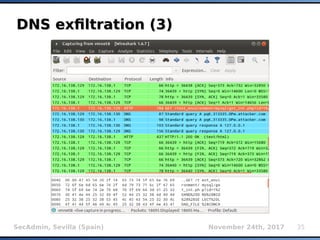
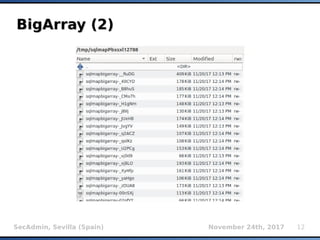
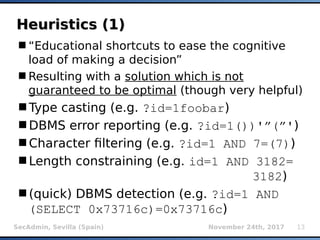
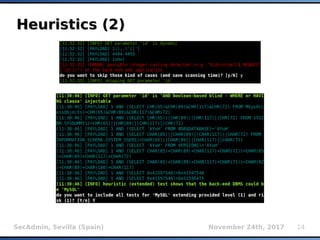
The document provides an overview of sqlmap, a free and open-source penetration testing tool designed to detect and exploit SQL injection flaws in databases. It covers its capabilities, including support for various database management systems and multiple SQL injection techniques, as well as advanced features like session data storage, big data handling, heuristic methods for effective exploitation, and techniques for bypassing web application firewalls. Additionally, the document discusses performance enhancements, false-positive detection mechanisms, and functionalities for hash cracking and data exfiltration.



![SecAdmin, Sevilla (Spain) November 24th, 2017 9
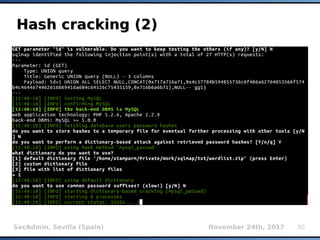
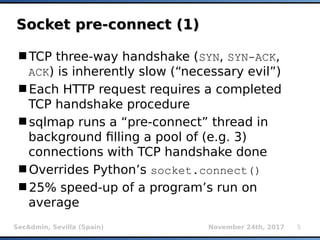
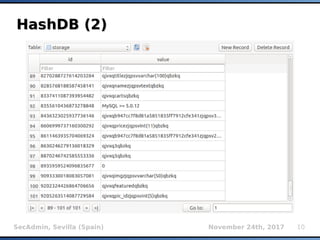
HashDB (1)HashDB (1)
Storage of resumable session data at
centralized place (local SQLite3 database)
Non-ASCII values are being automatically
serialized/deserialized (pickle)
INSERT INTO storage VALUES
(INT(MD5(target_url, uid, MILESTONE_SALT)
[:8]), stored_value)
uid uniquely describes stored_value for a
given target_url (e.g.: KB_INJECTIONS, SELECT
VERSION(), etc.)
MILESTONE_SALT changed whenever there is an
incompatible update of HashDB mechanism](https://image.slidesharecdn.com/secadmin-2017-miroslavstampar-sqlmapinternals-171219013111/85/sqlmap-internals-9-320.jpg)

![SecAdmin, Sevilla (Spain) November 24th, 2017 15
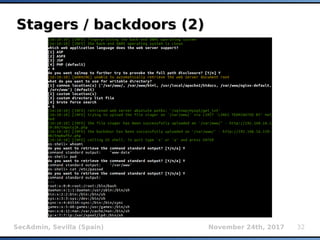
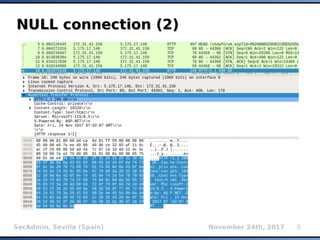
Boolean inference (1)Boolean inference (1)
Binary search using greater-than operator
O(Log2n) complexity compared to sequential
search with O(n)
Faster than bit-by-bit extraction (on average 6
requests compared to 8 requests)
For example:
Sample initial table ['A','B',...'Z']
AND (...) > 'M' → TRUE → ['N',...'Z']
AND (...) > 'S' → FALSE → ['N',...'S']
AND (...) > 'O' → TRUE → ['P', 'R', 'S']
AND (...) > 'R' → FALSE → ['P', 'R']
AND (...) > 'P' → FALSE → 'P' (result)](https://image.slidesharecdn.com/secadmin-2017-miroslavstampar-sqlmapinternals-171219013111/85/sqlmap-internals-15-320.jpg)