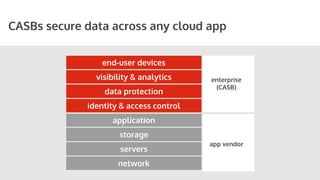
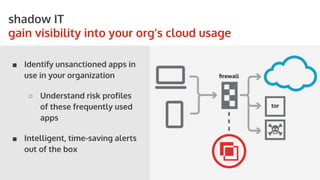
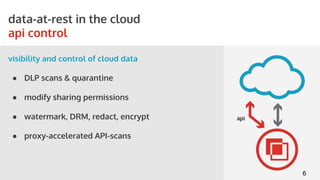
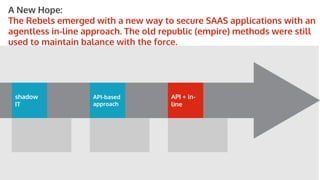
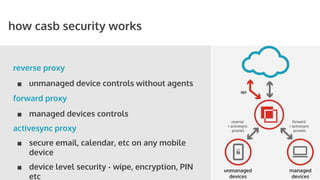
The document outlines the role of Cloud Access Security Brokers (CASBs) in securing cloud applications and managing shadow IT by providing visibility, data protection, and identity management across various cloud platforms. It highlights the inadequacies of existing Office 365 security measures and presents CASBs as an effective solution with an agentless, data-centric approach to enhance security across all devices. Additionally, the document includes case studies demonstrating the successful implementation of CASBs in organizations to mitigate data risks associated with cloud adoption.