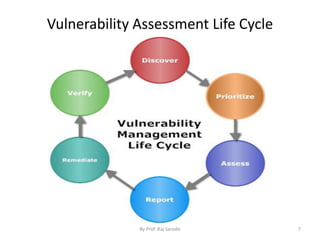
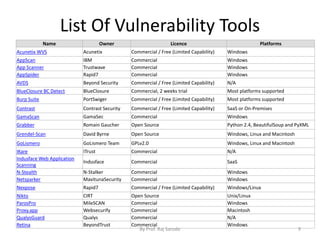
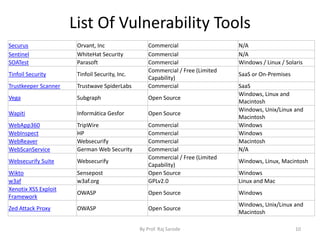
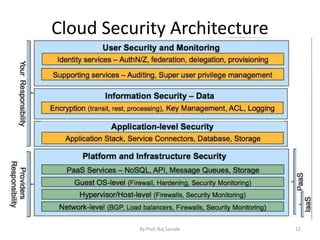
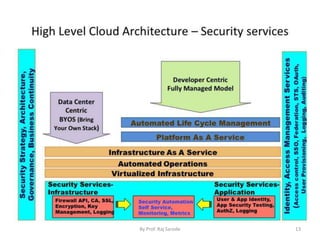
The document discusses cloud security fundamentals, emphasizing that responsibility for security and compliance rests with the business, regardless of whether they use cloud services or private infrastructure. It counters myths about cloud security, stating that data encryption and security depend on the cloud service provider and the specific cloud model used. Additionally, it covers various aspects of vulnerability management tools and the importance of understanding identity management and access control within cloud services.