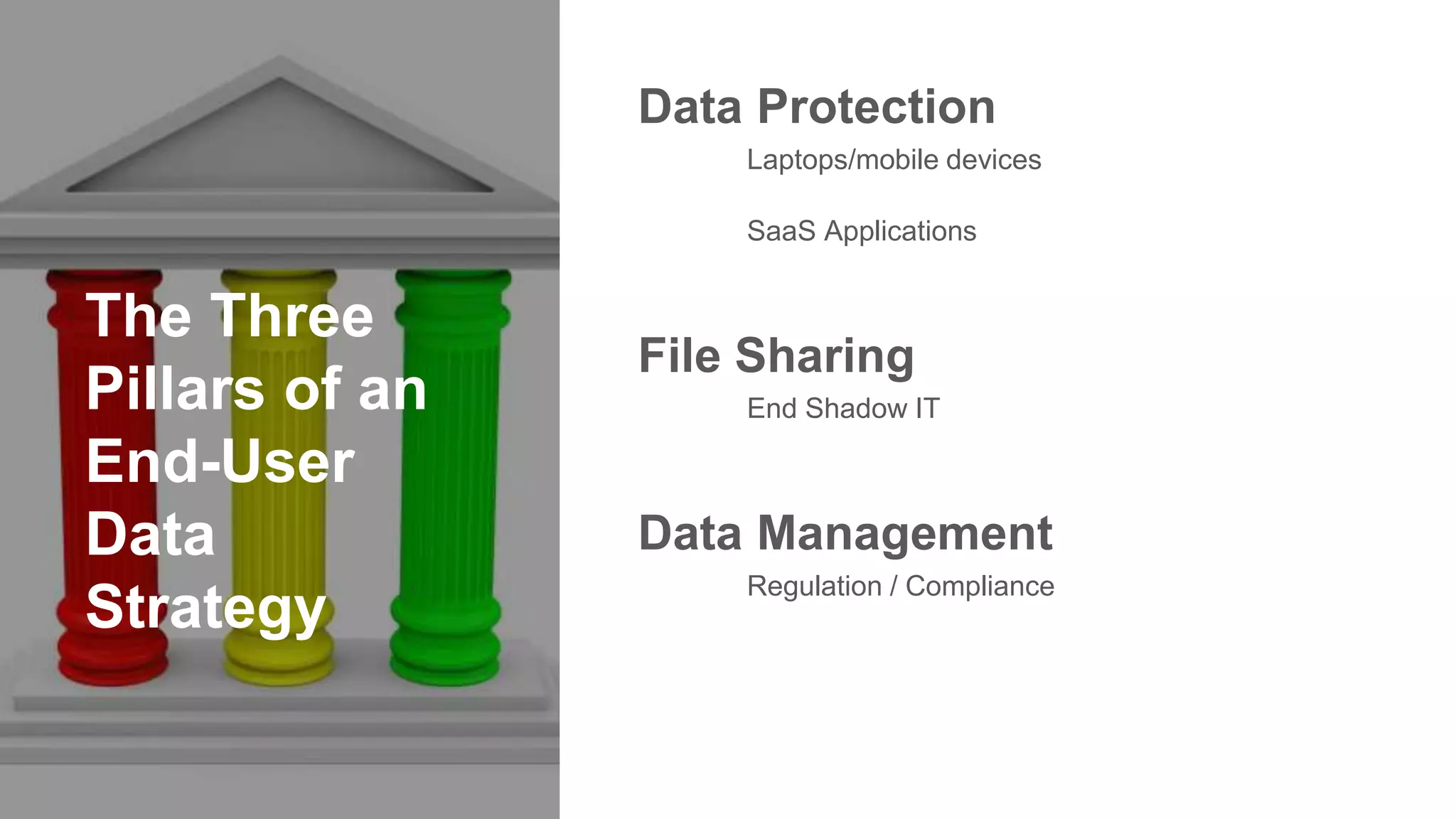
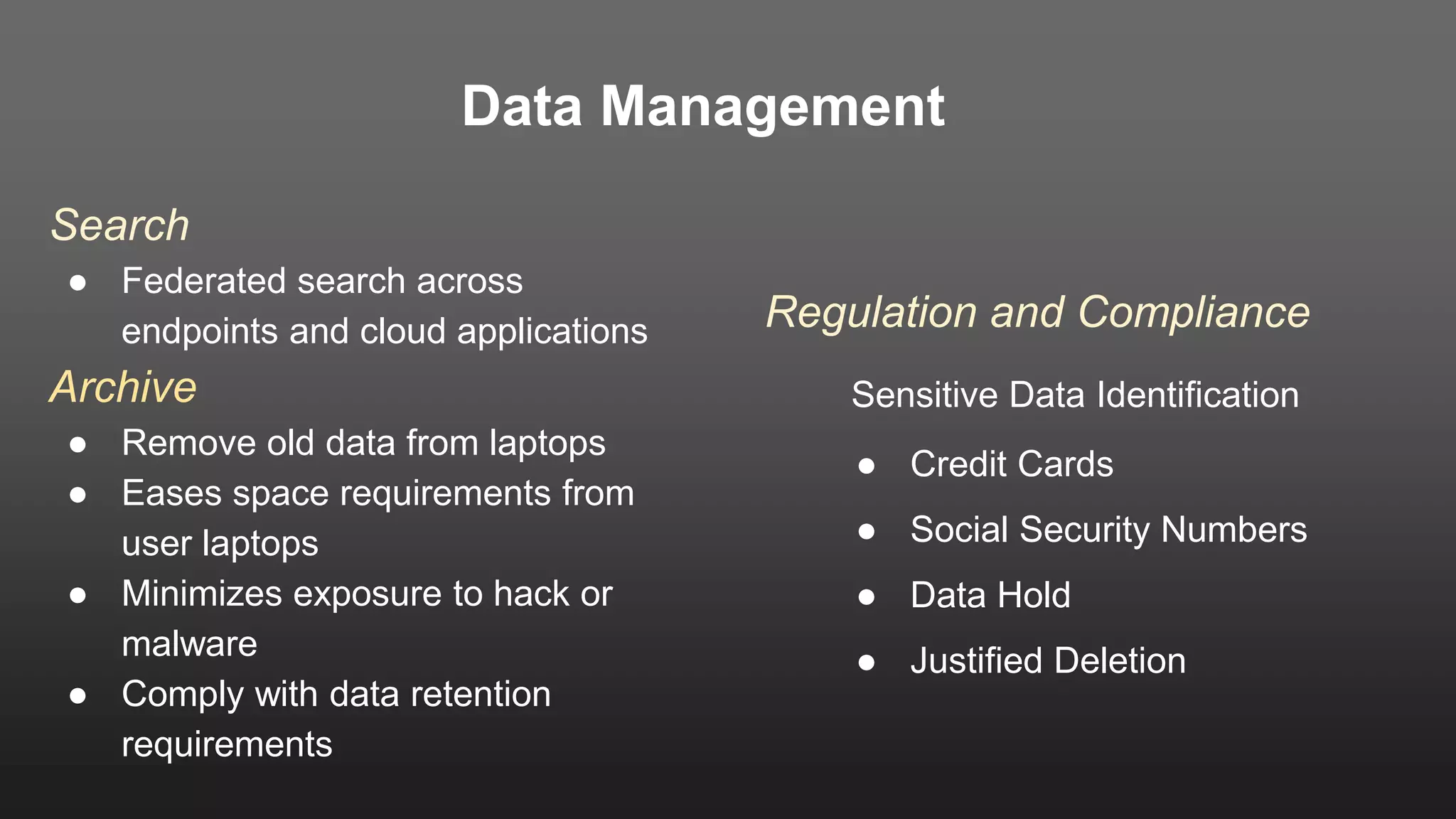
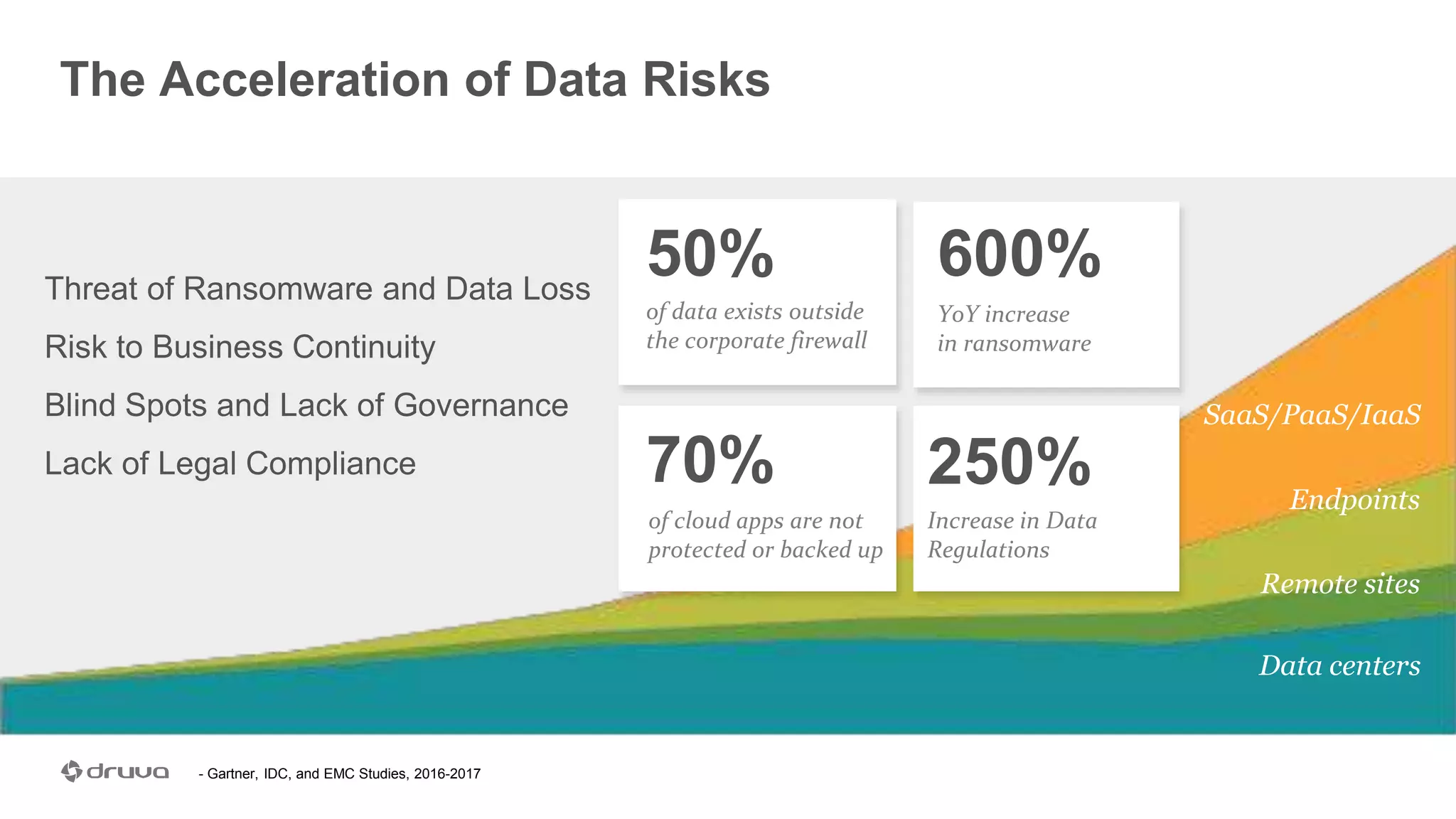
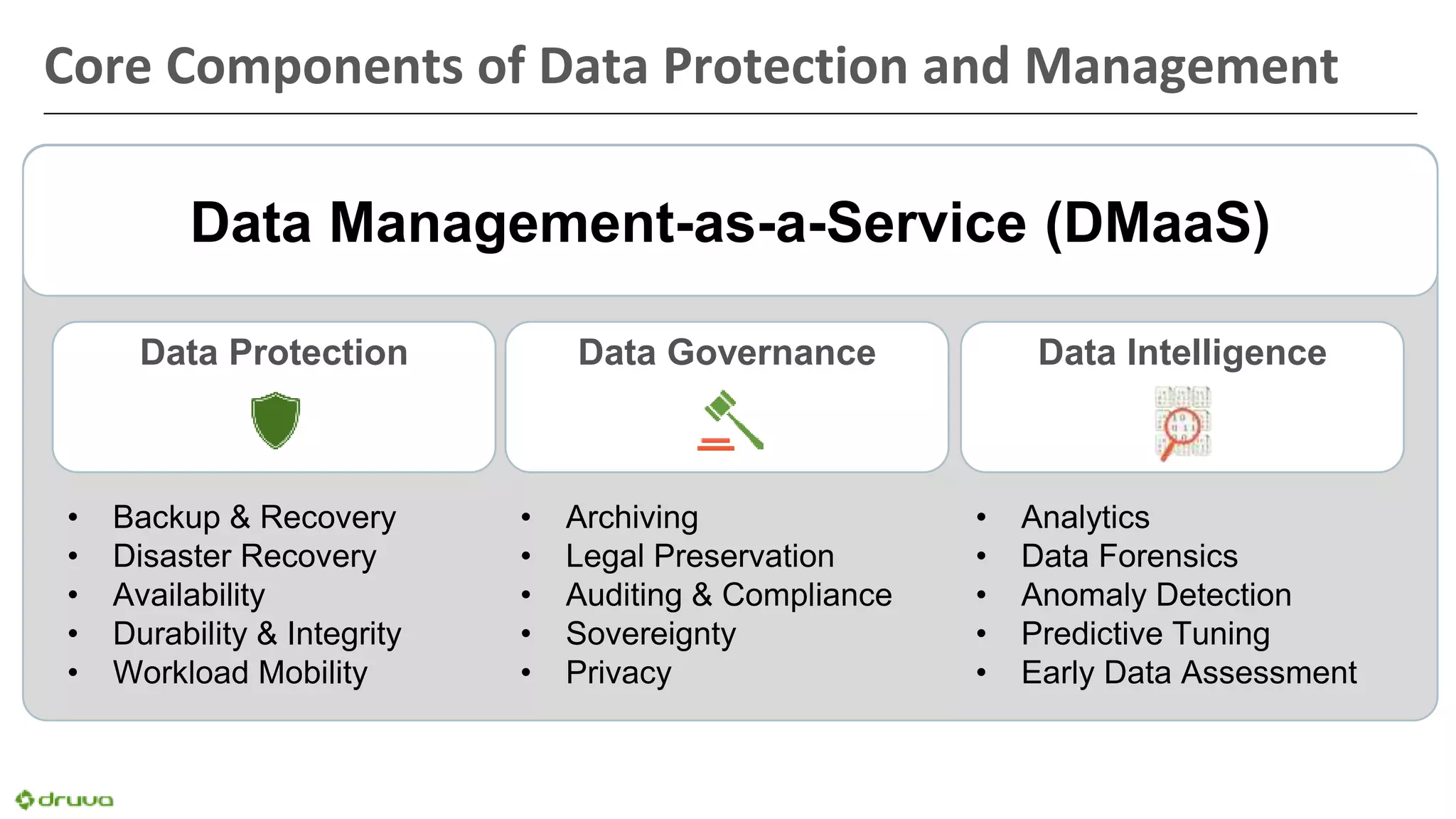
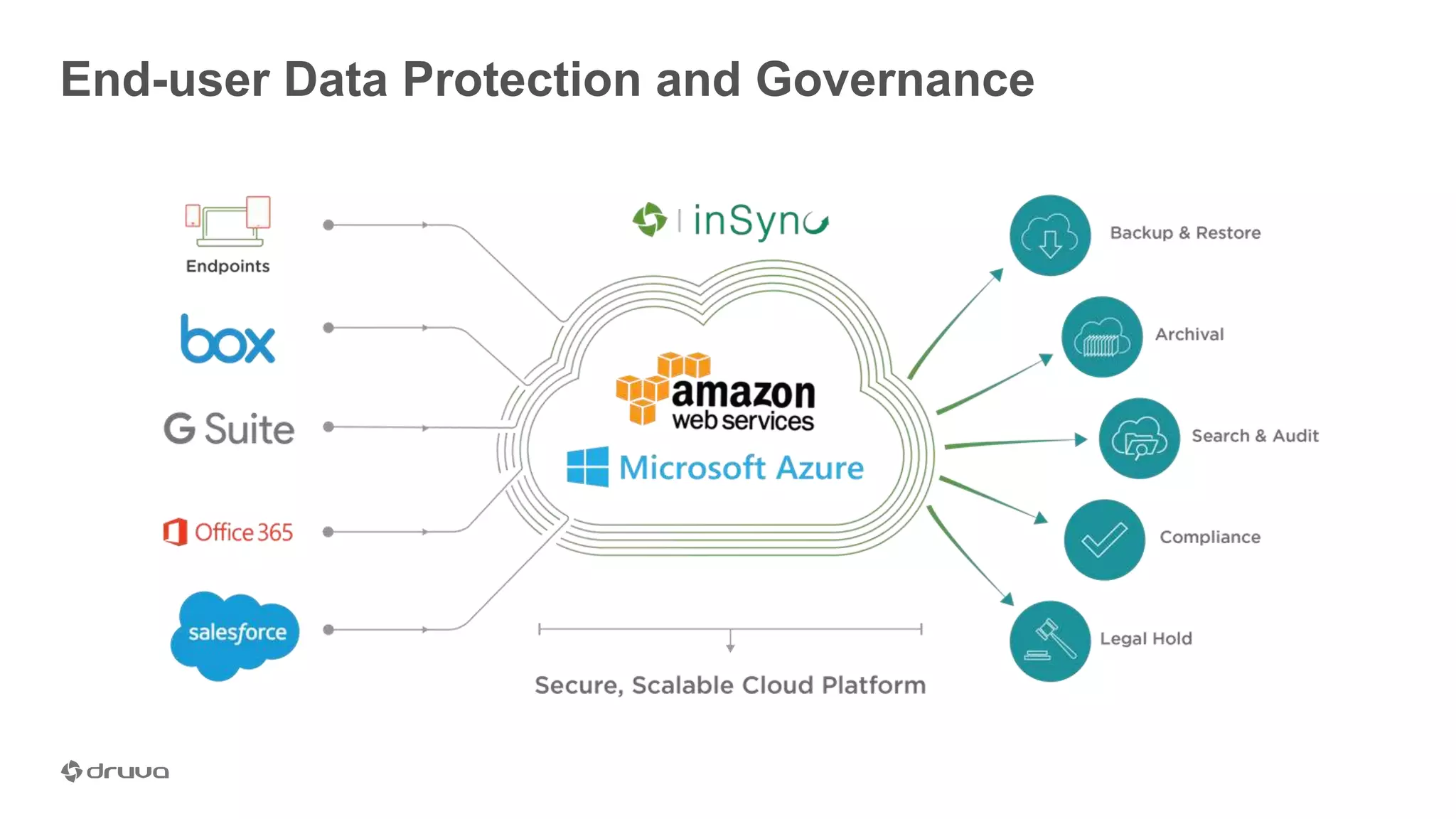
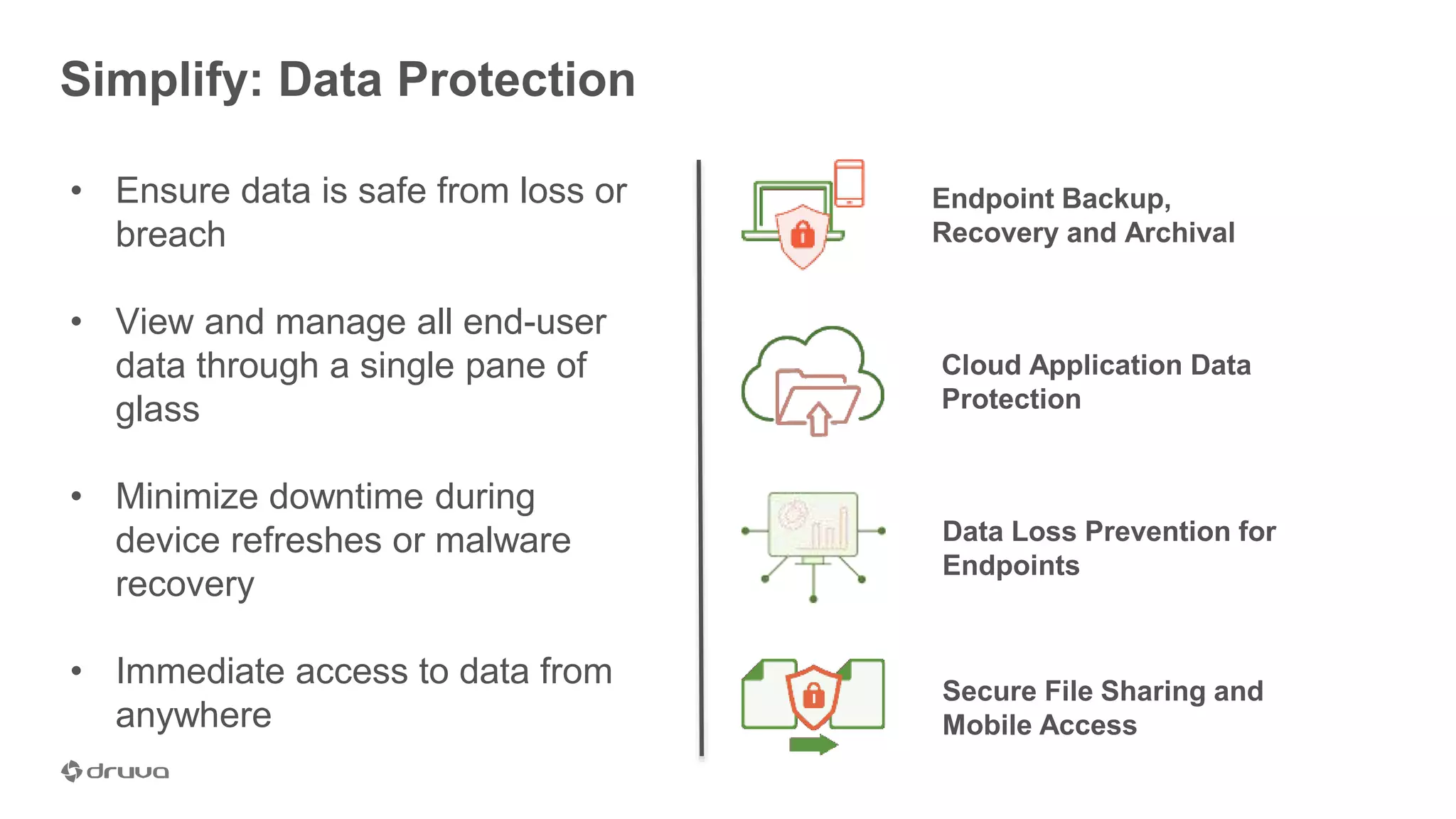
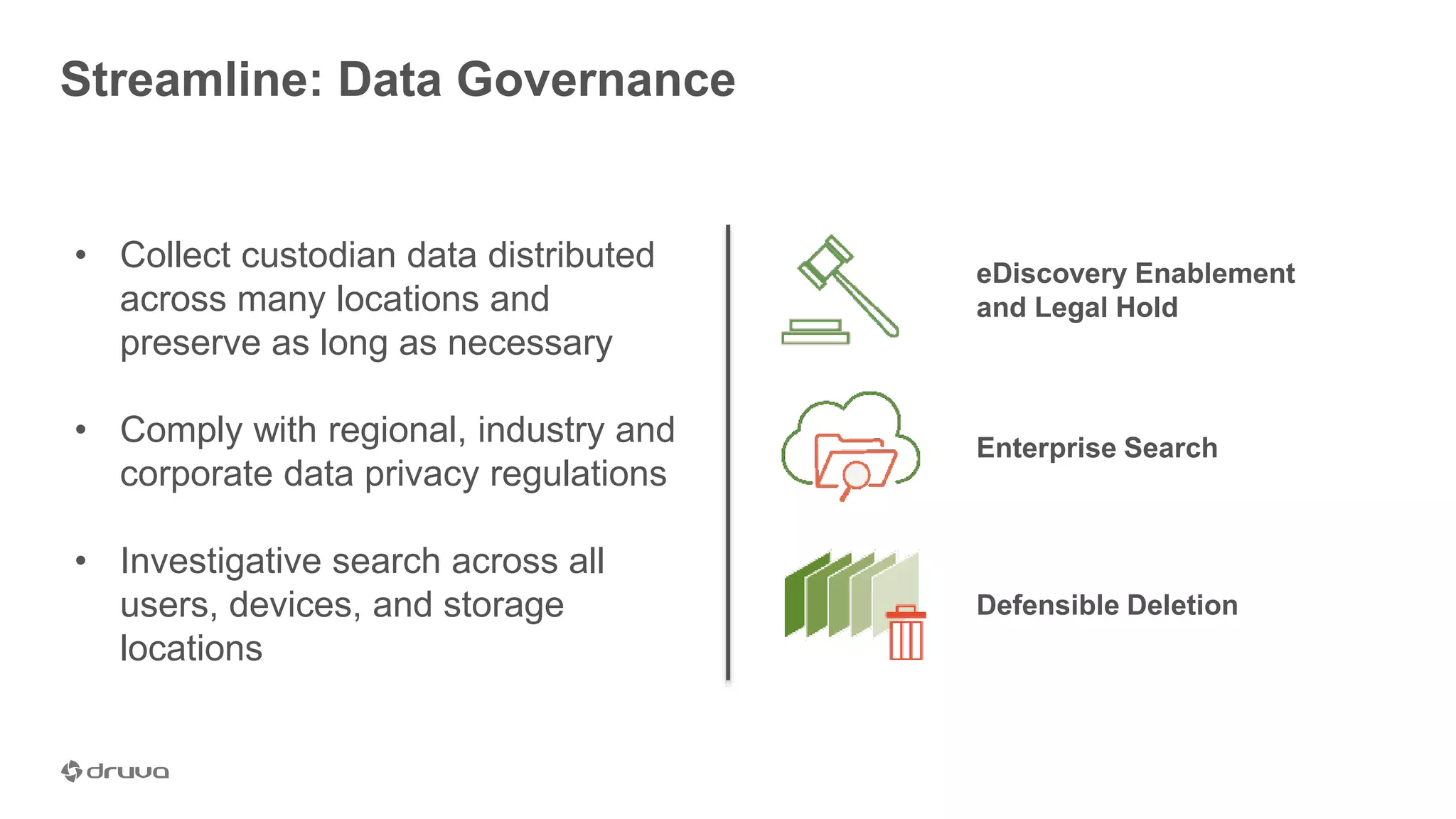
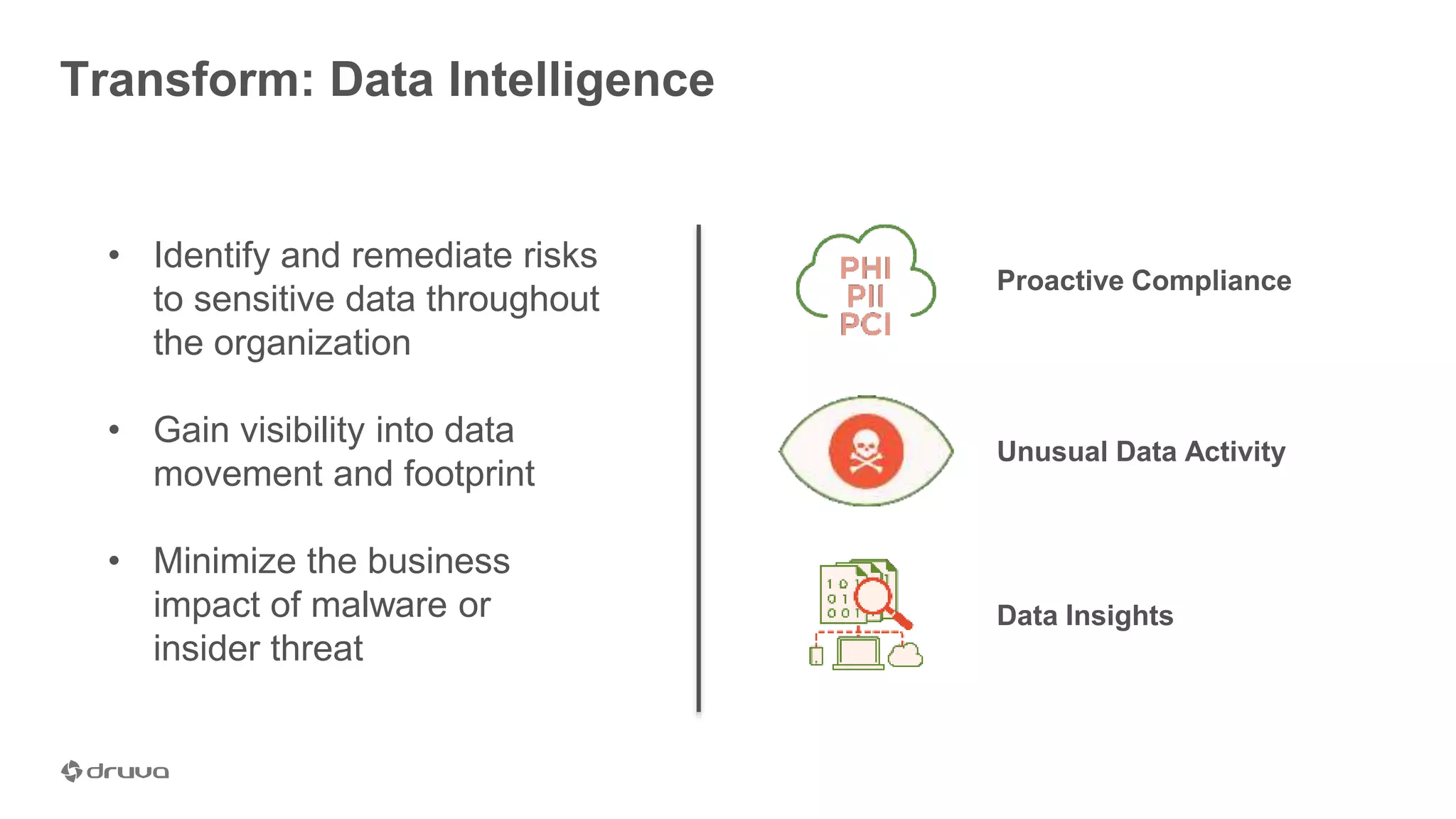
The document outlines the importance of developing a comprehensive end-user data strategy, which goes beyond mere endpoint backup to encompass data protection, sharing, and management. It identifies three key pillars: protection of laptops and SaaS applications, management of data regulation and compliance, and sharing capabilities to mitigate risks associated with shadow IT and data leakage. With increasing data risks, compliance demands, and ransomware threats, organizations are urged to adopt holistic data governance and protection strategies to safeguard sensitive information.