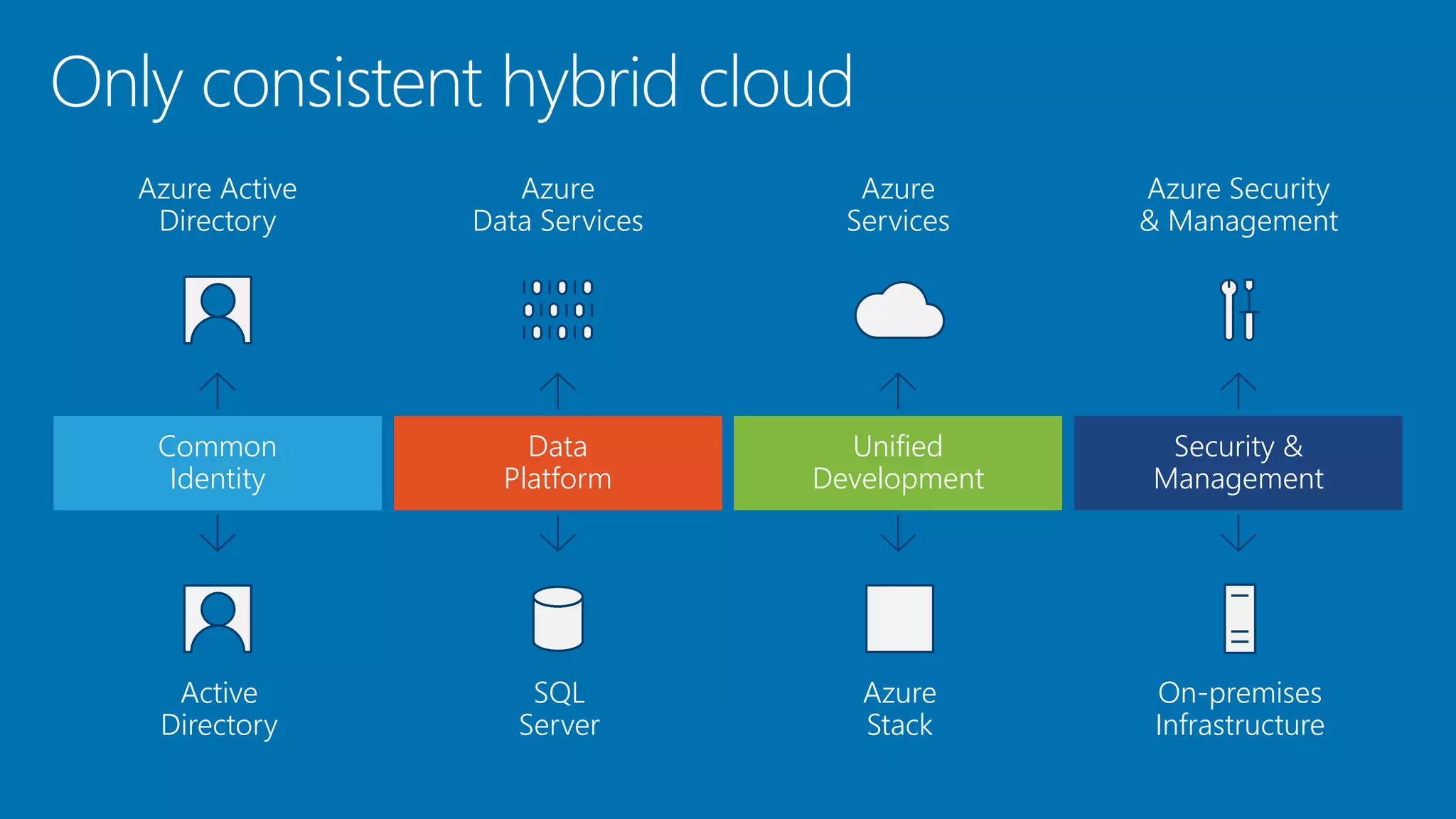
- Azure provides a unified platform for modern business with compute, data, storage, networking and application services across global Azure regions and a consistent hybrid cloud.
- Azure focuses on security and privacy with an emphasis on detection, response, and protection across infrastructure, platforms and applications.
- Security is a shared responsibility between Microsoft and customers, with Microsoft providing security controls and capabilities to help protect customer data and applications.






![• Secure Development Lifecycle -
https://www.microsoft.com/en-us/sdl/
• Tools to enable writing and releasing secure code
Empowering You
Secure Code Analysis VSTS Extension (Private Preview)
Contact: sdt-vsts@microsoft.com
Static Analysis for .NET
Roslyn, Security Analyzers
Binary Static Analysis Tool [GitHub]
provides security and correctness results for Windows portable executables
CREDSCAN
Detecting creds in
source & more
Credential Scanner
GitHub, VS-IDE Integration
Threat Modelling Tool
TMT2016
Secure Development Lifecycle](https://image.slidesharecdn.com/azuresecurityandcompliance-brazilfinancialcustomers-190301120627/75/Azure-security-and-Compliance-8-2048.jpg)

![Natural Disasters
Intrusion & DDoS
Administration Console and
Identity Management
Hardware
Management
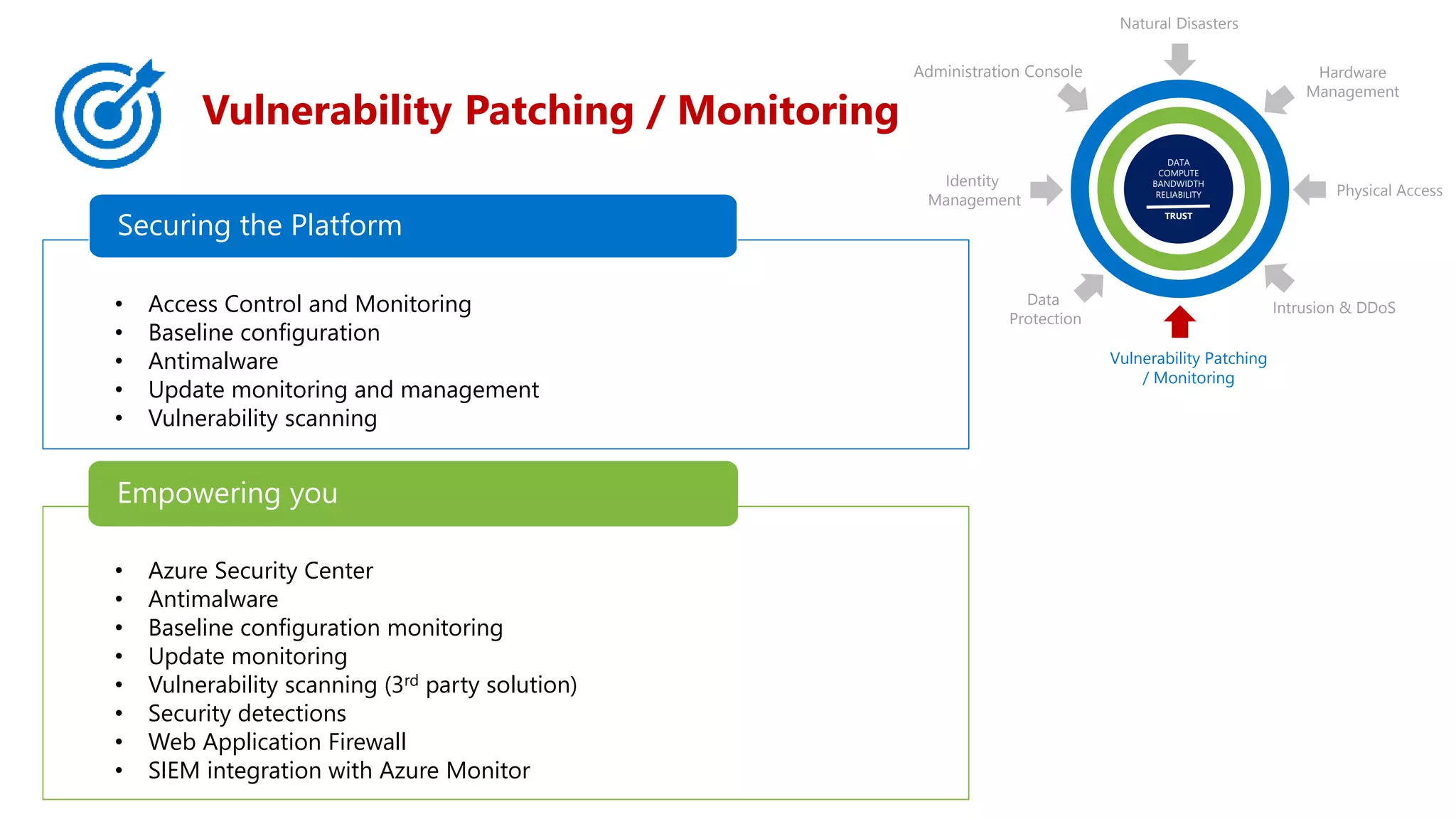
Vulnerability Patching
/ Monitoring
Data
Protection
Physical Access
DATA
COMPUTE
BANDWIDTH
RELIABILITY
TRUST
• Locked down Secure Admin Workstation
• Secure Boot, HW security, no admin, restricted browsing,
• AppLocker & Device Guard, Software Center, App security review
• Dedicated identity and resource forests
• Multi-factor authentication with physical or virtual smartcard
• Least and Temporarily Privilege, Just in Time elevation
• Access Control and Monitoring
Securing the Platform
• Privileged Access Workstation guidance on TechNet [link]
• Multi-factor authentication
• AAD Conditional Access (Location, Compliant devices)
• Just in Time access to IaaS
• AAD Monitoring
Empowering You
Identity
Management
Administration Console](https://image.slidesharecdn.com/azuresecurityandcompliance-brazilfinancialcustomers-190301120627/75/Azure-security-and-Compliance-10-2048.jpg)