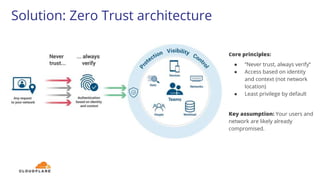
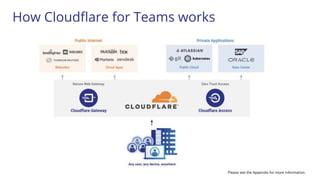
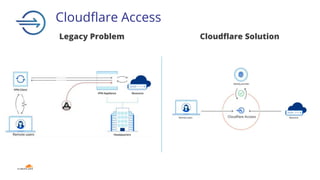
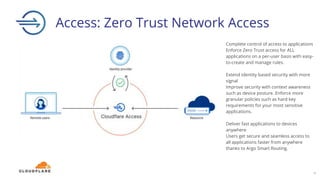
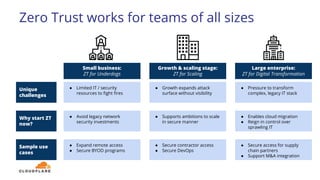
The document discusses the zero trust security framework, emphasizing the necessity for organizations to adopt a model that assumes users and networks are potentially compromised. It describes the challenges posed by traditional security measures, including increasing complexity and insufficient visibility, and presents Cloudflare's zero trust solutions designed to enhance security for organizations of all sizes. Case studies are provided to illustrate the successful implementation of zero trust strategies by various companies, leading to improved access control and reduced operational burdens.












![“[Access has] been amazing.
[Our previous solution] was
like trying to use a computer
that froze every 10 seconds.
Right now, support
departments don’t notice
any difference between
accessing customer
environments on-prem or
through Access.”
- Sybren van Wijk, Technical
Product Owner, TOPdesk
TOPdesk: Enabling 24x7 customer
support
26
CHALLENGES
● Dutch service management SaaS with expanding workforce across 11 countries
● Customer support engineers needed 24x7 remote access to an on-premise remote
support app; application was configured for office-only access due to GDPR
● Existing on-prem solution was slow, unresponsive, and designed when TOPDesk
had 100 employees, not 750+
SOLUTION
TOPDesk put Cloudflare Access in front of internal support apps to ensure technicians
could address pressing customer needs at any time, from anywhere. Access integrates
with Workers to ensures engineers can connect to only the customer environments they
have specific permission to reach, in compliance with GDPR.
VALUE
● Allowed TopDesk to supply true 24x7x365 support to customers
● Preparedness for remote work: Expanding Access usage in the weeks prior to the
pandemic helped prevent interruptions in customer support
● Replaced slower, less secure VPN access with Zero Trust access to key dashboards](https://image.slidesharecdn.com/zerotrustforeveryonewebinar-copy-200918005720/85/Zero-trust-for-everybody-3-ways-to-get-there-fast-26-320.jpg)