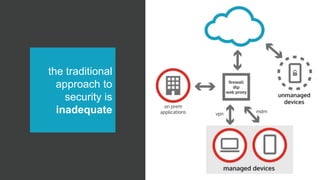
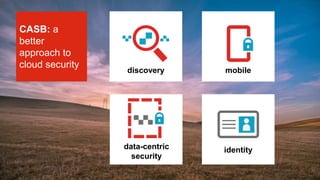
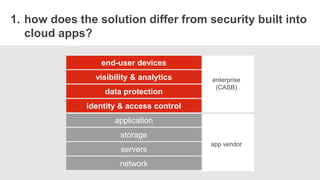
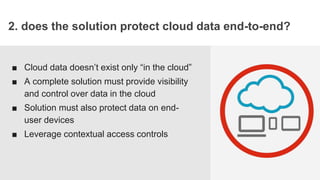
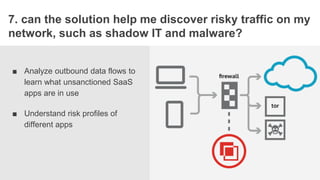
The document outlines essential considerations for evaluating cloud access security brokers (CASBs), emphasizing the need for enhanced security beyond traditional methods to protect sensitive data in various cloud environments. It presents eight critical questions to assess CASB solutions regarding data protection, visibility, access control, and risk mitigation. Specific use cases demonstrate how organizations can implement effective CASB solutions to manage security threats in cloud services like Office 365 and Google Apps.