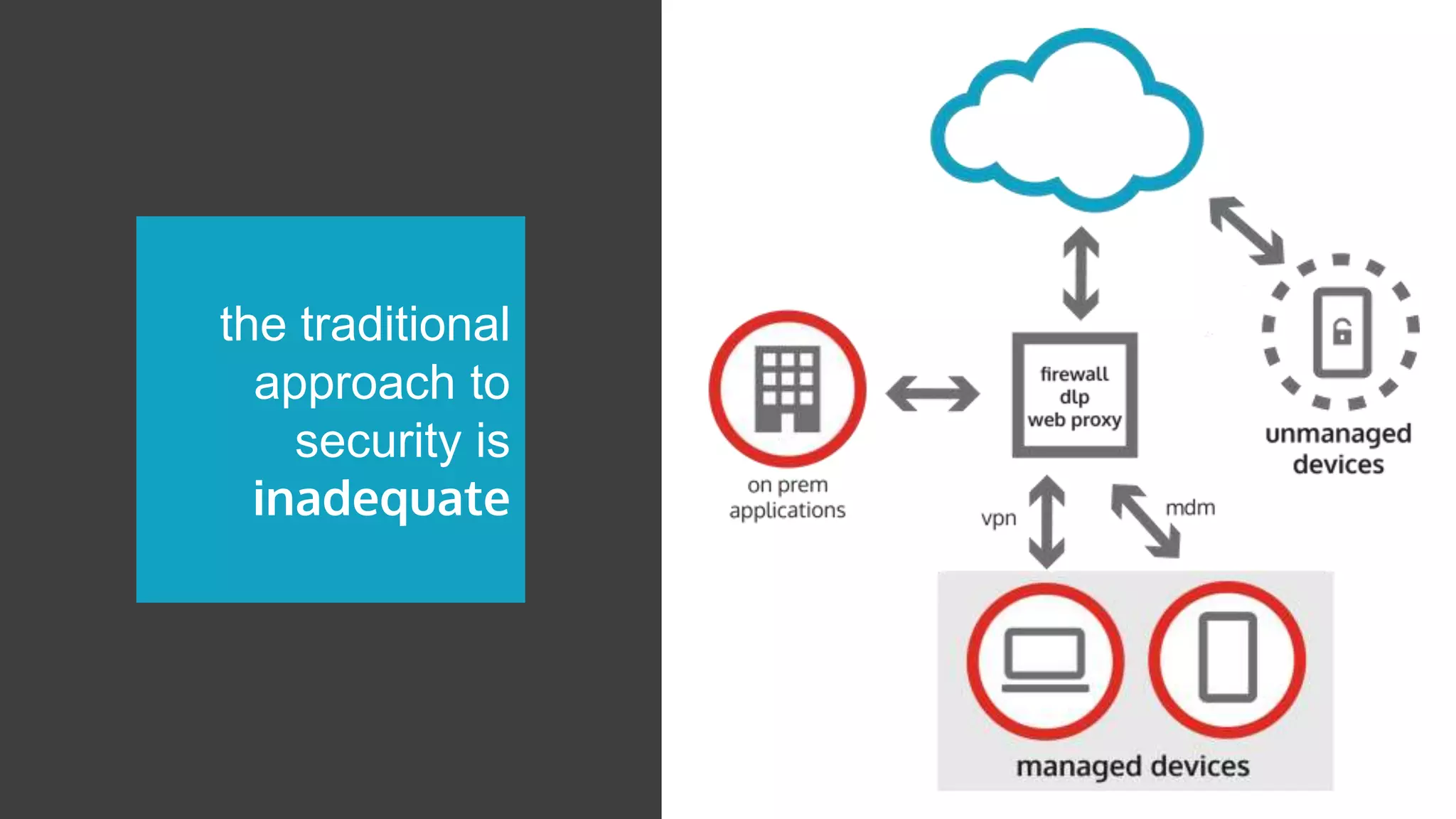
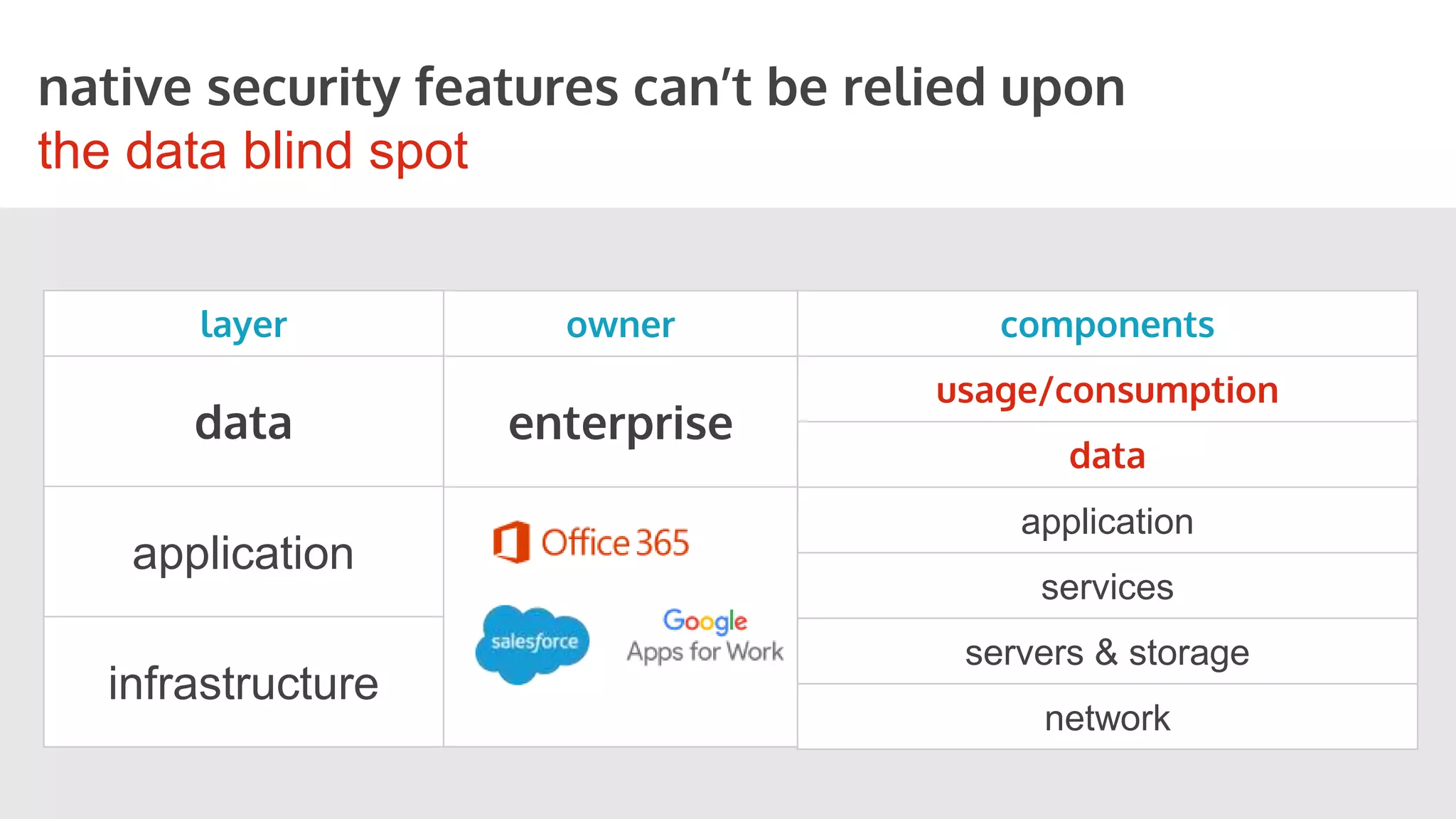
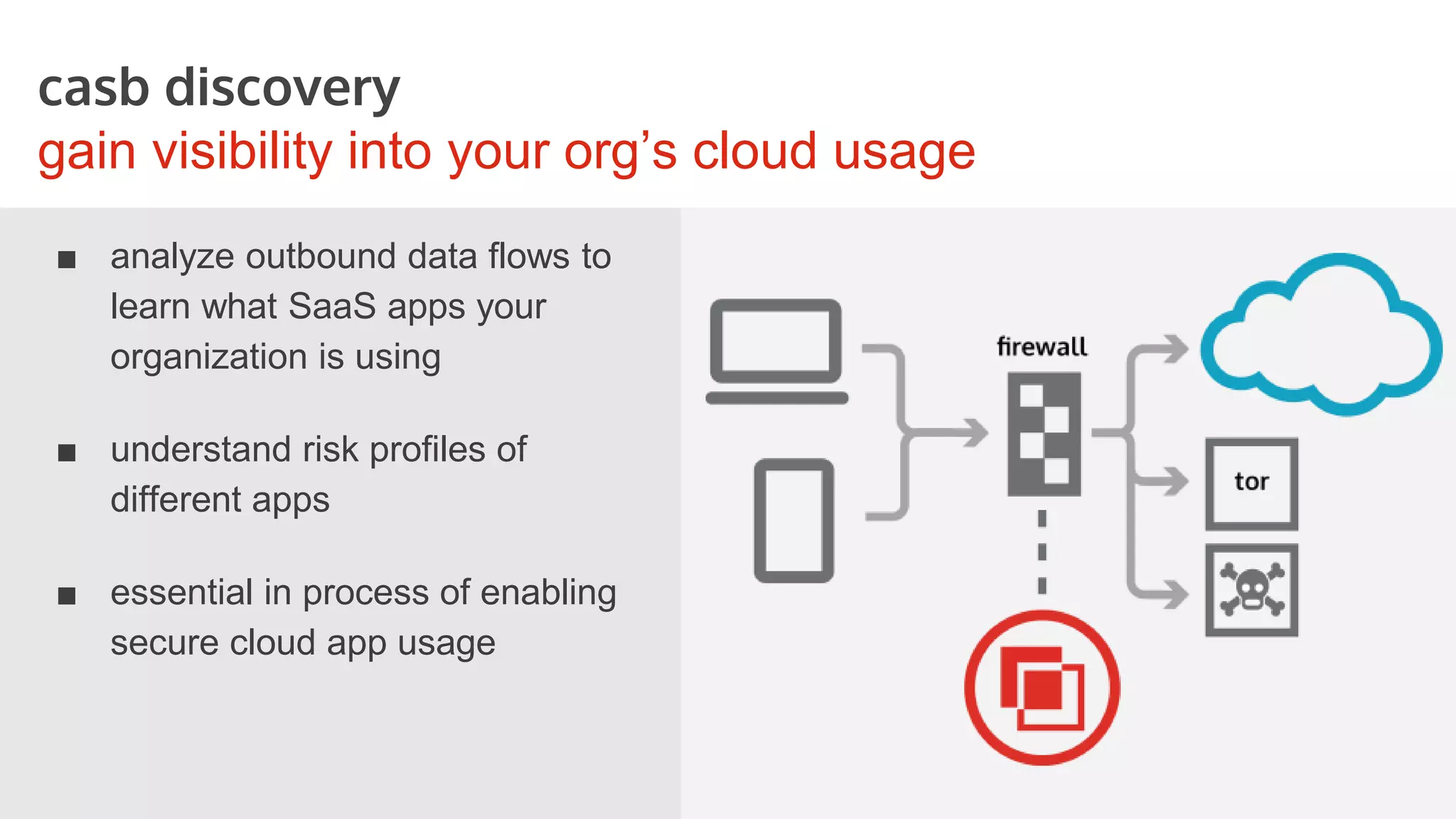
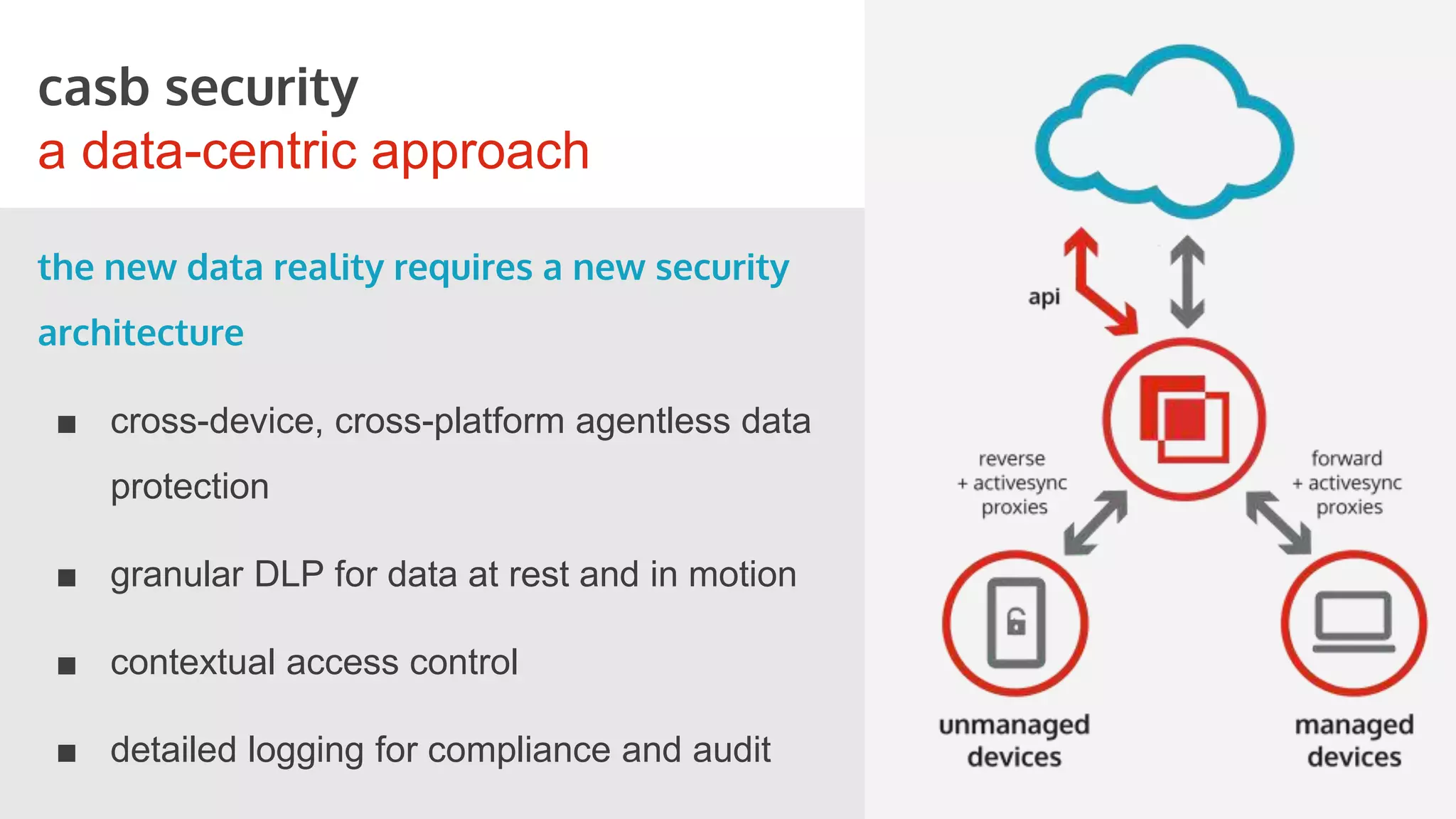
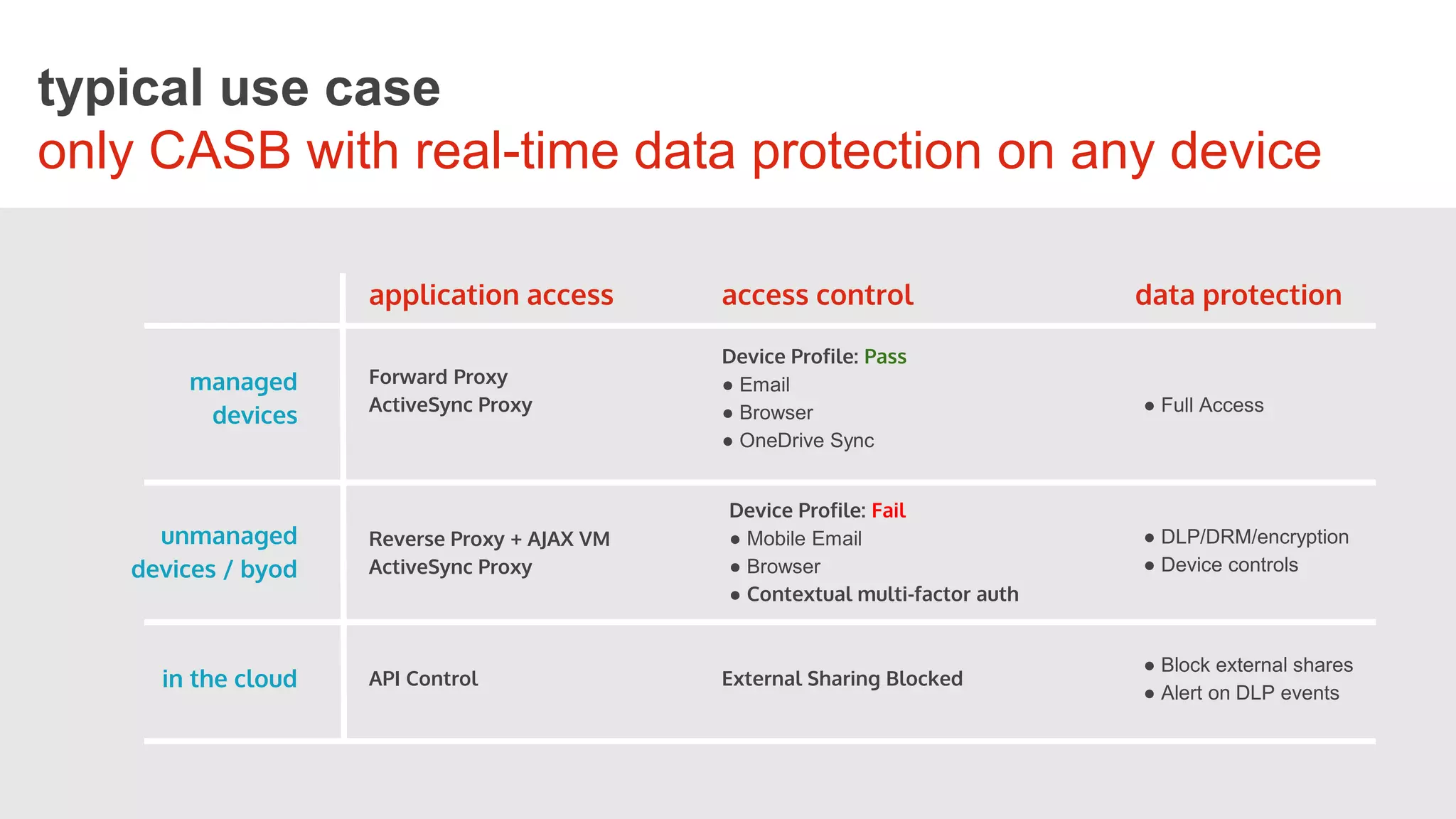
This document discusses securing cloud applications and data outside the traditional corporate firewall. It introduces Cloud Access Security Brokers (CASBs) as a better approach to cloud security compared to relying on native security features. CASBs provide identity management, discovery of cloud application usage, data-centric security, and mobile security. The document also shares examples of how CASBs help secure Office 365, Google Apps, and enable secure BYOD usage.