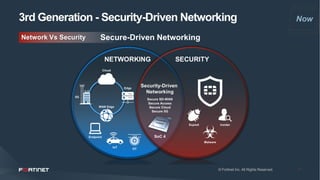
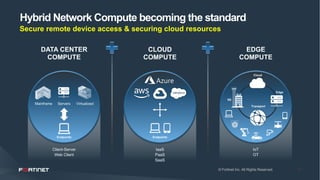
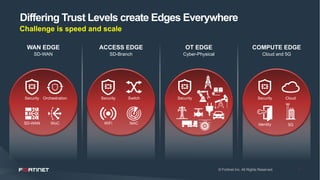
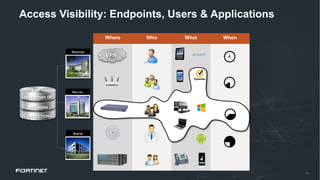
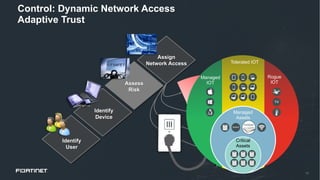
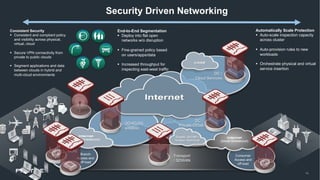
This document discusses moving beyond zero trust security models to a more comprehensive security driven networking approach. It advocates for integrating security across network, cloud, and edge infrastructure to gain visibility and control over all access and data flows. A security fabric is proposed that uses automation, open APIs, and behavioral analytics to consistently enforce security policies and rapidly respond to threats across hybrid digital environments. This is argued to provide organizations with a reasonable level of due care to prevent breaches and meet compliance standards.